DVA-C01 : AWS Certified Developer Associate : Part 07
DVA-C01 : AWS Certified Developer Associate : Part 07
-
What does an Amazon SQS delay queue accomplish?
- Messages are hidden for a configurable amount of time when they are first added to the queue.
- Messages are hidden for a configurable amount of time after they are consumed from the queue.
- The consumer can poll the queue for a configurable amount of time before retrieving a message.
- Message cannot be deleted for a configurable amount of time after they are consumed from the queue.
-
A company has multiple Developers located across the globe who are updating code incrementally for a development project. When Developers upload code concurrently, internet connectivity is slow, and it is taking a long time to upload code for deployment in AWS Elastic Beanstalk.
Which step will result in minimized upload and deployment time with the LEAST amount of administrative effort?
- Allow the Developers to upload the code to an Amazon S3 bucket, and deploy it directly to Elastic Beanstalk.
- Allow the Developers to upload the code to a central FTP server to deploy the application to Elastic Beanstalk.
- Create an AWS CodeCommit repository, allow the Developers to commit code to it, and then directly deploy the code to Elastic Beanstalk.
- Create a code repository on an Amazon EC2 instance so that all Developers can update the code, and deploy the application from the instance to Elastic Beanstalk.
-
A company recently migrated its web, application, and NoSQL database tiers to AWS. The company is using Auto Scaling to scale the web and application tiers. More than 95 percent of the Amazon DynamoDB requests are repeated read-requests.
How can the DynamoDB NoSQL tier be scaled up to cache these repeated requests?
- Amazon EMR
- Amazon DynamoDB Accelerator
- Amazon SQS
- Amazon CloudFront
-
A company is building an application to track athlete performance using an Amazon DynamoDB table. Each item in the table is identified by a partition key (user_id) and a sort key (sport_name). The table design is shown below:
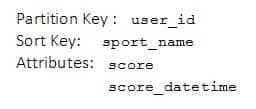
DVA-C01 AWS Certified Developer Associate Part 07 Q04 008 (Note: Not all table attributes are shown)
A Developer is asked to write a leaderboard application to display the top performers (user_id) based on the score for each sport_name.
What process will allow the Developer to extract results MOST efficiently from the DynamoDB table?
- Use a DynamoDB query operation with the key attributes of user_id and sport_name and order the results based on the score attribute.
- Create a global secondary index with a partition key of sport_name and a sort key of score, and get the results
- Use a DynamoDB scan operation to retrieve scores and user_id based on sport_name, and order the results based on the score attribute.
- Create a local secondary index with a primary key of sport_name and a sort key of score and get the results based on the score attribute.
-
A Developer is creating a mobile application that will not require users to log in.
What is the MOST efficient method to grant users access to AWS resources?
- Use an identity provider to securely authenticate with the application.
- Create an AWS Lambda function to create an IAM user when a user accesses the application.
- Create credentials using AWS KMS and apply these credentials to users when using the application.
- Use Amazon Cognito to associate unauthenticated users with an IAM role that has limited access to resources.
-
An application running on Amazon EC2 instances must access objects within an Amazon S3 bucket that are encrypted using server-side encryption using AWS KMS encryption keys (SSE-KMS). The application must have access to the customer master key (CMK) to decrypt the objects.
Which combination of steps will grant the application access? (Choose two.)
- Write an S3 bucket policy that grants the bucket access to the key.
- Grant access to the key in the IAM EC2 role attached to the application’s EC2 instances.
- Write a key policy that enables IAM policies to grant access to the key.
- Grant access to the key in the S3 bucket’s ACL
- Create a Systems Manager parameter that exposes the KMS key to the EC2 instances.
-
A company needs a fully-managed source control service that will work in AWS. The service must ensure that revision control synchronizes multiple distributed repositories by exchanging sets of changes peer-to-peer. All users need to work productively even when not connected to a network.
Which source control service should be used?
- Subversion
- AWS CodeBuild
- AWS CodeCommit
- AWS CodeStar
-
A Developer is writing a serverless application that requires that an AWS Lambda function be invoked every 10 minutes.
What is an automated and serverless way to trigger the function?
- Deploy an Amazon EC2 instance based on Linux, and edit its /etc/crontab file by adding a command to periodically invoke the Lambda function.
- Configure an environment variable named PERIOD for the Lambda function. Set the value to 600.
- Create an Amazon CloudWatch Events rule that triggers on a regular schedule to invoke the Lambda function.
- Create an Amazon SNS topic that has a subscription to the Lambda function with a 600-second timer.
-
A Developer is writing an imaging micro service on AWS Lambda. The service is dependent on several libraries that are not available in the Lambda runtime environment.
Which strategy should the Developer follow to create the Lambda deployment package?
- Create a ZIP file with the source code and all dependent libraries.
- Create a ZIP file with the source code and a script that installs the dependent libraries at runtime.
- Create a ZIP file with the source code. Stage the dependent libraries on an Amazon S3 bucket indicated by the Lambda environment variable LD_LIBRARY_PATH
- Create a ZIP file with the source code and a buildspec.yaml file that installs the dependent libraries on AWS Lambda.
-
A Developer is designing a fault-tolerant environment where client sessions will be saved.
How can the Developer ensure that no sessions are lost if an Amazon EC2 instance fails?
- Use sticky sessions with an Elastic Load Balancer target group.
- Use Amazon SQS to save session data.
- Use Amazon DynamoDB to perform scalable session handling.
- Use Elastic Load Balancer connection draining to stop sending requests to failing instances.
-
In a move toward using microservices, a company’s Management team has asked all Development teams to build their services so that API requests depend only on that service’s data store. One team is building a Payments service which has its own database; the service needs data that originates in the Accounts database. Both are using Amazon DynamoDB.
What approach will result in the simplest, decoupled, and reliable method to get near-real time updates from the Accounts database?
- Use Amazon Glue to perform frequent ETL updates from the Accounts database to the Payments database.
- Use Amazon ElastiCache in Payments, with the cache updated by triggers in the Accounts database.
- Use Amazon Kinesis Data Firehose to deliver all changes from the Accounts database to the Payments database.
- Use Amazon DynamoDB Streams to deliver all changes from the Accounts database to the Payments database.
-
How should custom libraries be utilized in AWS Lambda?
- Host the library on Amazon S3 and reference to it from the Lambda function.
- Install the library locally and upload a ZIP file of the Lambda function.
- Import the necessary Lambda blueprint when creating the function.
- Modify the function runtime to include the necessary library.
-
A company needs to secure its existing website running behind an Elastic Load Balancer. The website’s Amazon EC2 instances are CPU-constrained.
What should be done to secure the website while not increasing the CPU load on the EC2 web servers? (Choose two.)
- Configure an Elastic Load Balancer with SSL pass-through.
- Configure SSL certificates on an Elastic Load Balancer.
- Configure an Elastic Load Balancer with a Loadable Storage System.
- Install SSL certificates on the EC2 instances.
- Configure an Elastic Load Balancer with SSL termination.
-
An AWS Lambda function generates a 3MB JSON file and then uploads it to an Amazon S3 bucket daily. The file contains sensitive information, so the Developer must ensure that it is encrypted before uploading to the bucket.
Which of the following modifications should the Developer make to ensure that the data is encrypted before uploading it to the bucket?
- Use the default AWS KMS customer master key for S3 in the Lambda function code.
- Use the S3 managed key and call the GenerateDataKey API to encrypt the file.
- Use the GenerateDateKey API, then use that data key to encrypt the file in the Lambda function code.
- Use a custom KMS customer master key created for S3 in the Lambda function code.
-
A Developer wants to find a list of items in a global secondary index from an Amazon DynamoDB table.
Which DynamoDB API call can the Developer use in order to consume the LEAST number of read capacity units?
- Scan operation using eventually-consistent reads
- Query operation using strongly-consistent reads
- Query operation using eventually-consistent reads
- Scan operation using strongly-consistent reads
-
A Developer has published an update to an application that is served to a global user base using Amazon CloudFront. After deploying the application, users are not able to see the updated changes.
How can the Developer resolve this issue?
- Remove the origin from the CloudFront configuration and add it again.
- Disable forwarding of query strings and request headers from the CloudFront distribution configuration.
- Invalidate all the application objects from the edge caches.
- Disable the CloudFront distribution and enable it again to update all the edge locations.
-
A Developer must deploy a new AWS Lambda function using an AWS CloudFormation template.
Which procedures will deploy a Lambda function? (Choose two.)
- Upload the code to an AWS CodeCommit repository, then add a reference to it in an AWS::Lambda::Function resource in the template.
- Create an AWS::Lambda::Function resource in the template, then write the code directly inside the CloudFormation template.
- Upload a .ZIP file containing the function code to Amazon S3, then add a reference to it in an AWS::Lambda::Function resource in the template.
- Upload a .ZIP file to AWS CloudFormation containing the function code, then add a reference to it in an AWS::Lambda::Function resource in the template.
- Upload the function code to a private Git repository, then add a reference to it in an AWS::Lambda::Function resource in the template.
-
A Developer wants to enable AWS X-Ray for a secure application that runs in an Amazon ECS environment.
What combination of steps will enable X-Ray? (Choose three.)
- Create a Docker image that runs the X-Ray daemon.
- Add instrumentation to the application code for X-Ray.
- Install the X-Ray daemon on the underlying EC2 instance.
- Configure and use an IAM EC2 instance role.
- Register the application with X-Ray.
- Configure and use an IAM role for tasks.
-
A Developer is designing a new application that uses Amazon S3. To satisfy compliance requirements, the Developer must encrypt the data at rest.
How can the Developer accomplish this?
- Use s3:x-amz-acl as a condition in the S3 bucket policy.
- Use Amazon RDS with default encryption.
- Use aws:SecureTransport as a condition in the S3 bucket policy.
- Turn on S3 default encryption for the S3 bucket.
-
An AWS Elastic Beanstalk application needs to be deployed in multiple regions and requires a different Amazon Machine Image (AMI) in each region.
Which AWS CloudFormation template key can be used to specify the correct AMI for each region?
- Parameters
- Outputs
- Mappings
- Resources