DVA-C01 : AWS Certified Developer Associate : Part 18
DVA-C01 : AWS Certified Developer Associate : Part 18
-
Which techniques will help mitigate this exception? (Choose two.)
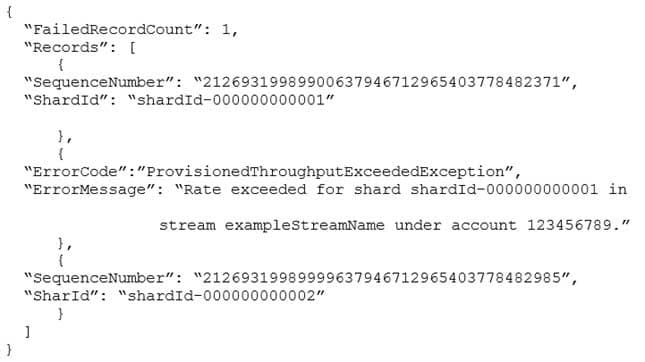
DVA-C01 AWS Certified Developer Associate Part 18 Q01 019 - Implement retries with exponential backoff
- Use a PutRecord API instead of PutRecords
- Reduce the frequency and/or size of the requests
- Use Amazon SNS instead of Kinesis
- Reduce the number of KCL consumers
-
A developer is building an application integrating an Amazon API Gateway with an AWS Lambda function. When calling the API, the developer receives the following error:
Wed Nov 08 01:13:00 UTC 2017 : Method completed with status: 502
What should the developer do to resolve the error?
- Change the HTTP endpoint of the API to an HTTPS endpoint
- Change the format of the payload sent to the API Gateway
- Change the format of the Lambda function response to the API call
- Change the authorization header in the API call to access the Lambda function
-
How does Envelope Encryption work in AWS KMS?
- The Customer Master Key is used to encrypt/decrypt a data key. The Plaintext Data Key is used to encrypt customer data.
- Two encryption keys are used. The Customer Master Key encrypts customer data. The Data Key is used to re-encrypt the encrypted data.
- Two encryption keys are used. The Data Key encrypts customer data. The Сustomer Master Key is used to re-encrypt the encrypted data.
- The Customer Master Key is used to encrypt/decrypt a data key. The Encrypted Data Key is used to encrypt customer data.
-
A developer must build a mobile application that allows users to read and write data from an Amazon DynamoDB table to store user state for each unique user. The solution needs to limit data access to allow users access only to their own data.
Which solution below is the most secure?
- Embed AWS access credentials into the application and create DynamoDB queries that limit user access.
- Use Amazon Cognito identity pools to assign unique identifiers and provide user access.
- Modify the DynamoDB table to allow public read and writes, then add client-side filtering.
- Create a web portal for users to create an account on AWS Directory Service.
-
A developer is building an application on Amazon EC2. The developer encountered an “Access Denied” error on some of the API calls to AWS services while testing. The developer needs to modify permissions that have been already given to the instance.
How can these requirements be met with minimal changes and minimum downtime?
- Make a new IAM role with the needed permissions. Stop the instance. Attach the new IAM role to the instance. Start the instance.
- Delete the existing IAM role. Attach a new IAM role with the needed permissions.
- Stop the instance. Update the attached IAM role adding the needed permissions. Start the instance.
- Update the attached IAM role adding the needed permissions.
-
A developer is building an application that will run on Amazon EC2 instances. The application needs to connect to an Amazon DynamoDB table to read and write records. The security team must periodically rotate access keys.
Which approach will satisfy these requirements?
- Create an IAM role with read and write access to the DynamoDB table. Generate access keys for the user and store the access keys in the application as environment variables.
- Create an IAM user with read and write access to the DynamoDB table. Store the user name and password in the application and generate access keys using an AWS SDK.
- Create an IAM role, configure read and write access for the DynamoDB table, and attach to the EC2 instances.
- Create an IAM user with read and write access to the DynamoDB table. Generate access keys for the user and store the access keys in the application as a credentials file.
-
A video-hosting website has two types of members: those who pay a fee, and those who do not. Each video upload places a message in Amazon SQS. A fleet of Amazon EC2 instances polls Amazon SQS and processes each video.
The developer needs to ensure that the videos uploaded by the paying members are processed first.
How can the developer meet this requirement?
- Create two SQS queues: one for paying members, and one for non-paying members. Poll the paying member queue first and then poll the non-paying member queue.
- Use SQS to set priorities on individual items within a single queue; give the paying members’ videos the highest priority.
- Use SQS to set priorities on individual items within a single queue and use Amazon SNS to encode the videos.
- Create two Amazon SNS topics: one for paying members and one for non-paying members. Use SNS topic subscription priorities to differentiate between the two types of members.
-
A developer is monitoring an application running on an Amazon EC2 instance. The application accesses an Amazon DynamoDB table and the developer has configured a custom Amazon CloudWatch metric with data granularity of 1 second. If there are any issues, the developer wants to be notified within 30 seconds using Amazon SNS.
Which CloudWatch mechanism will satisfy this requirement?
- Configure a high-resolution CloudWatch alarm.
- Set up a custom AWS Lambda CloudWatch log.
- Use a Cloud Watch stream.
- Change to a default CloudWatch metric.
-
A developer is designing a distributed application built using a microservices architecture spanning multiple AWS accounts. The company’s operations team wants to analyze and debug application issues from a centralized account.
How can the developer meet these requirements?
- Use an Amazon X-Ray agent with role assumption to publish data into the centralized account.
- Use Amazon X-Ray and create a new IAM user to publish the access keys into the centralized account.
- Use VPC Flow Logs to collect applications logs across different accounts.
- Enable AWS CloudTrail to publish the trails in an Amazon S3 bucket in the centralized account.
-
A developer is implementing authentication and authorization for an application. The developer needs to ensure that the user credentials are never exposed.
Which approach should the developer take to meet this requirement?
- Store the user credentials in Amazon DynamoDB. Build an AWS Lambda function to validate the credentials and authorize users.
- Deploy a custom authentication and authorization API on an Amazon EC2 instance. Store the user credentials in Amazon S3 and encrypt the credentials using Amazon S3 server-side encryption.
- Use Amazon Cognito to configure a user pool, and user the Cognito API to authenticate and authorize the user.
- Store the user credentials in Amazon RDS. Enable the encryption option for the Amazon RDS DB instances. Build an API using AWS Lambda to validate the credentials and authorize users.
-
A developer is building a new complex application on AWS. The application consists of multiple microservices hosted on Amazon EC2. The developer wants to determine which microservice adds the most latency while handling a request.
Which method should the developer use to make this determination?
- Instrument each microservice request using the AWS X-Ray SDK. Examine the annotations associated with the requests.
- Instrument each microservice request using the AWS X-Ray SDK. Examine the subsegments associated with the requests.
- Instrument each microservice request using the AWS X-Ray SDK. Examine the Amazon CloudWatch EC2 instance metrics associated with the requests.
- Instrument each microservice request using the Amazon CloudWatch SDK. Examine the CloudWatch EC2 instance metrics associated with the requests.
-
A company has a two-tier application running on an Amazon EC2 server that handles all of its AWS based e-commerce activity. During peak times, the backend servers that process orders are overloaded with requests. This results in some orders failing to process. A developer needs to create a solution that will re-factor the application.
Which steps will allow for more flexibility during peak times, while still remaining cost-effective? (Choose two.)
- Increase the backend T2 EC2 instance sizes to x1 to handle the largest possible load throughout the year.
- Implement an Amazon SQS queue to decouple the front-end and backend servers.
- Use an Amazon SNS queue to decouple the front-end and backend servers.
- Migrate the backend servers to on-premises and pull from an Amazon SNS queue.
- Modify the backend servers to pull from an Amazon SQS queue.
-
A developer is asked to integrate Amazon CloudWatch into an on-premises application.
How should the application access CloudWatch, according to AWS security best practices?
- Configure AWS credentials in the application server with an AWS SDK
- Implement and proxy API-calls through an EC2 instance
- Store IAM credentials in the source code to enable access
- Add the application server SSH-key to AWS
-
A developer is trying to get data from an Amazon DynamoDB table called demoman-table. The developer configured the AWS CLI to use a specific IAM user’s credentials and executed the following command:

DVA-C01 AWS Certified Developer Associate Part 18 Q14 020 The command returned errors and no rows were returned.
What is the MOST likely cause of these issues?
- The command is incorrect; it should be rewritten to use put-item with a string argument.
- The developer needs to log a ticket with AWS Support to enable access to the demoman-table.
- Amazon DynamoDB cannot be accessed from the AWS CLI and needs to be called via the REST API.
- The IAM user needs an associated policy with read access to demoman-table.
-
A company’s new mobile app uses Amazon API Gateway. As the development team completes a new release of its APIs, a developer must safely and transparently roll out the API change.
What is the SIMPLEST solution for the developer to use for rolling out the new API version to a limited number of users through API Gateway?
- Create a new API in API Gateway. Direct a portion of the traffic to the new API using an Amazon Route 53 weighted routing policy.
- Validate the new API version and promote it to production during the window of lowest expected utilization.
- Implement an Amazon CloudWatch alarm to trigger a rollback if the observed HTTP 500 status code rate exceeds a predetermined threshold.
- Use the canary release deployment option in API Gateway. Direct a percentage of the API traffic using the canarySettings setting.
-
A developer must increase read performance from an unencrypted Amazon S3 bucket. The application requires 100,000 read requests each second. Cost-effectiveness is a priority.
What would be the SIMPLEST approach to implement these requirements?
- Create 20 or more prefixes in Amazon S3. Place files by prefixes. Read in parallel by prefixes.
- Create 20 or more AWS accounts. Create a bucket in each account. Read in parallel by bucket.
- Deploy Memcached on Amazon EC2. Cache the files in memory. Retrieve from the Memcached cache.
- Copy all files to Amazon DynamoDB. Index the files with S3 metadata. Retrieve from DynamoDB.
-
A developer must modify an Alexa skill backed by an AWS Lambda function to access an Amazon DynamoDB table in a second account. A role in the second account has been created with permissions to access the table.
How should the table be accessed?
- Modify the Lambda function execution role’s permissions to include the new role.
- Change the Lambda function execution role to be the new role.
- Assume the new role in the Lambda function when accessing the table.
- Store the access key and the secret key for the new role and use then when accessing the table.
-
A developer is creating a new application that will be accessed by users through an API created using Amazon API Gateway. The users need to be authenticated by a third-party Security Assertion Markup Language (SAML) identity provider. Once authenticated, users will need access to other AWS services, such as Amazon S3 and Amazon DynamoDB.
How can these requirements be met?
- Use an Amazon Cognito user pool with SAML as the resource server.
- Use Amazon Cognito identity pools with a SAML identity provider as one of the authentication providers.
- Use the AWS IAM service to provide the sign-up and sign-in functionality.
- Use Amazon CloudFront signed URLs to connect with the SAML identity provider.
-
An application development team decides to use AWS X-Ray to monitor application code to analyze performance and perform root cause analysis.
What does the team need to do to begin using X-Ray? (Choose two.)
- Log instrumentation output into an Amazon SQS queue.
- Use a visualization tool to view application traces.
- Instrument application code using the AWS SDK.
- Install the X-Ray agent on the application servers.
- Create an Amazon DynamoDB table to store the trace logs.
-
A developer has code stored in an Amazon S3 bucket. The code must be deployed as an AWS Lambda function across multiple accounts in the same Region as the S3 bucket. The Lambda function will be deployed using an AWS CloudFormation template that is run for each account.
What is the MOST secure approach to allow access to the Lambda code in the S3 bucket?
- Grant the CloudFormation execution role S3 list and get permissions. Add a bucket policy to Amazon S3 with the Principal of “AWS”: [account numbers].
- Grant the CloudFormation execution role S3 get permissions. Add a bucket policy to Amazon S3 with the Principal of “*”.
- Use a service-based link to grant the Lambda function S3 list and get permissions by explicitly adding the S3 bucket’s account number in the resource.
- Use a service-based link to grant the Lambda function S3 get permissions and add a Resource of “*” to allow access to the S3 bucket.