CCNPv8 ENCOR (Version 8.0) – Chapters 17 – 19: Wireless Essentials Exam Answers Full 100% 2024
CCNPv8 ENCOR (Version 8.0) – Chapters 17 – 19: Wireless Essentials Exam Answers Full 100% 2024
-
When comparing two absolute power values, what can a wireless engineer conclude after calculating a result of -3 dB?
- The value of the two power levels is the same.
- The power level of interest is double the reference value.
- The power level of interest is half the reference value.
- The power level of interest is ten times the reference value.
- The power level of interest is one tenth of the reference value.
Explanation & Hint: According to the dB laws:
- Law of 0: If two power levels are the same, one is 0 dB greater than the other.
- Law of 3s: A value of 3 dB means that the power value of interest is double the reference value. A value of -3 dB means that the power value of interest is half the reference value.
- Law of 10s: A value of 10 dB means that the power level of interest is 10 times the reference value. A value of -10 dB means that the power level of interest is 1/10th of the reference value.
-
While reviewing wireless survey reports, an intern asks a wireless engineer about the term noise floor. What is the definition of noise floor?
- Noise floor is the decreasing of the signal amplitude as it travels through free space.
- Noise floor is the average signal strength of the noise being received by a receiver.
- Noise floor is the maximum signal strength of the recorded noise received by a receiver.
- Noise floor is the smallest signal strength of the recorded noise received by a receiver.
Explanation & Hint: Noise is any other signal that is received on the same frequency as a signal of interest and noise floor is the average signal strength of that received noise.
-
Refer to the exhibit. It displays the sources of A, B, and C and the corresponding absolute power of each. In comparing source A and B , how much greater is the signal strength of source B than the signal strength of source A?
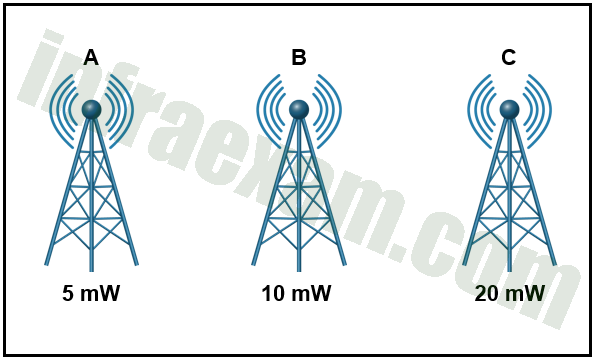
CCNPv8 ENCOR (Version 8.0) – Chapters 17 – 19 Wireless Essentials Exam Answers 01 - 0 dB
- 2 dB
- 3 dB
- 5 dB
- 10 dB
Explanation & Hint: Source B is double the value of source A. Each time you double a value, simply add 3 dB. Because 10 mW is double 5 mW, source B is 3 dB greater than the strength of source A.
-
What is a simple solution to overcome the negative effects of free space path loss?
- decrease the transmitter output power
- increase the transmitter output power
- decrease the antenna gain
- increase the cable length of the antenna
Explanation & Hint: Increasing the antenna gain or increasing the transmitter output power can be simple ways to overcome free space path loss.
-
What technological factor limits the number of unique spatial streams that can be supported by a MIMO device?
- the number of transmitters
- the number of receivers
- the processing capacity
- the number of radios
Explanation & Hint: A MIMO device can distribute spatial streams across multiple radio chains and does not have to assign a unique spatial stream to an individual transmitter/receiver. The number of possible spatial streams depends on the processing capacity and the transmitter feature set of the wireless device.
-
Which wireless technology allows data to be distributed across two or more radio chains in order to increase data throughput while operating on the same channel?
- spatial multiplexing
- dynamic rate shifting
- direct sequence spread spectrum
- narrowband
Explanation & Hint: Spatial multiplexing allows faster data throughput by multiplexing or distributing data across two or more radio chains operating on the same channel but separated through spatial diversity.
-
Which term describes the decrease in signal strength of an RF even though there are no obstacles in the path between a transmitter and a receiver?
- link budget
- transmit beamforming
- free space path loss
- spatial multiplexing
Explanation & Hint: Whenever an RF signal is transmitted from an antenna, the signal amplitude decreases as it travels through free space. Even if there are no obstacles in the path between the transmitter and receiver, the signal strength will weaken. This is known as free space path loss.
-
How does the 802.11ax amendment (Wi-Fi 6) differ from any other 802.11 wireless standard created before it?
- Wi-Fi 6 can allow multiple devices simultaneous access to the wireless medium.
- Wi-Fi 6 can support both the 2.4 GHz and 5 GHz band.
- Wi-Fi 6 can support data rates in excess of 150 Mbps per spatial stream.
- Wi-Fi 6 can utilize channel widths of 20, 40, 80, or 160 MHz.
Explanation & Hint: In comparing 802.11ax (Wi-Fi 6) to previous 802.11 implementations, one of the key differences is that 802.11ax can use OFDMA to allocate air time for transmission by multiple devices simultaneously.
-
Which IEEE standard operates at wireless frequencies in both the 5 GHz and 2.4 GHz ranges?
- 802.11n
- 802.11g
- 802.11b
- 802.11a
Explanation & Hint: The 802.11n standard is backwards compatible with both the 802.11a and 802.11b standards and therefore operates at both 5 GHz and 2.4 GHz.
-
An engineer has identified two signals that are 180 degrees out of phase . What can be determined about these two signals?
- These two RF signals will add together as they are received.
- These two RF signals will tend to cancel each other out as they are received.
- These two RF signals will have matching cycles and identical signals.
- These two RF signals were produced at exactly the same time.
Explanation & Hint: Signals designated as out of phase do not have matching cycles and are not identical. These signals may cancel each other out as they are received.
-
How does a change in frequency or cycles affect the wavelength of a wireless LAN signal?
- As the cycles of a wave become larger, the wavelength will cover less distance.
- As the frequency decreases, the wavelength will also decrease.
- As the frequency increases, the wavelength will also increase.
- As the number of cycles decreases, the wavelength will increase.
Explanation & Hint: In measuring an RF signal, there is a correlation between frequency and wavelength. As the frequency increases, the wavelength decreases. When there are fewer cycles per second, the wavelength will cover a greater distance.
-
Which wireless network topology requires that all of the access points be located within a 100 meter radius of an access switch?
- centralized wireless network
- embedded wireless network
- unified wireless network
- Mobility Express wireless network
Explanation & Hint: The embedded wireless network topology employs an embedded WLC within each access layer switch. Each AP would be connected to the access switch via twisted-pair cable and is subject to the 100 meter distance limitation.
-
What are two benefits of deploying a centralized wireless LAN topology? (Choose two.)
- decreasing the RTT between two wireless clients on a single access point
- maximizing the number of APs that can join a single WLC
- lowering the investment cost when utilizing lightweight access points in a Mobility Express topology
- decreasing the cable length requirement when utilizing lightweight access points in an embedded wireless network topology
- convenience of enforcing security policies for all wireless users
Explanation & Hint: A centralized or unified wireless LAN topology utilizes a centralized WLC location that provides easy enforcement of security policies and the ability to maximize the number of APs that can join to it. The centralized topology also supports user mobility because all of the APs associate to the same WLC no matter how many APs the user device associates with while roaming.
-
What is a difference between autonomous APs that operate in a home environment and controller-based APs that operate in a corporate environment?
- Autonomous APs incorporate the functions of a router, switch, and AP into one device.
- Autonomous APs do not support PoE.
- Controller-based APs can be automatically configured and managed by a WLAN controller.
- Controller-based APs are known as lightweight APs and require an initial configuration to operate.
Explanation & Hint: Autonomous APs are standalone devices that are configured via Cisco CLI or a GUI. Controller-based APs are server-dependent devices that require no initial configuration to operate, because they are automatically configured and managed by a WLAN controller. Most autonomous and controller-based APs support PoE.
-
Which protocol and port number are used when an AP sends a unicast CAPWAP Discovery Request packet to the IP address of a controller? (Choose two.)
- TCP
- 5246
- IP
- UDP
- 43
- 1812
- 1645
Explanation & Hint: When attempting to discover a WLC, an access point can send a unicast CAPWAP Discovery Request to the IP address of a controller over UDP port 5246 or can send a broadcast over the local subnet.
-
Which type of topology supports the use of CAPWAP tunnels without the investment of a dedicated wireless LAN controller?
- Mobility Express
- embedded wireless network
- centralized wireless network
- unified wireless network
Explanation & Hint: A Mobility Express topology uses a fully functional Cisco AP with software acting as a WLC instead of investing in a dedicated WLC device.
-
What information is needed by an AP for stateful switchover (SSO) using high availability with a standby WLC?
- the IP address of both the primary and standby WLC
- the group name of the SSO pair
- the active primary WLC
- the standby WLC
Explanation & Hint: The AP will have a single CAPWAP tunnel to the active controller. The active unit keeps CAPWAP tunnels, AP states, client states, configurations, and image files all in sync with the hot standby unit. The active controller also synchronizes the state of each associated client that is in the RUN state with the hot standby controller.
-
Why would an AP that successfully discovers a WLAN controller be denied from joining that WLC?
- The WLC has a software release downloaded on it that is different from the lightweight AP software.
- The WLC already has the maximum number of APs joined to it.
- The name of the WLC is different from the pre-configured name on the Cisco lightweight AP.
- The WLC is configured to be the standby WLC in an SSO group.
Explanation & Hint: A WLC will deny an AP from joining it if the maximum number of lightweight APs already joined to it has already been reached.
-
What type of wireless antenna is best suited for providing coverage in large open spaces, such as hallways or large conference rooms?
- omnidirectional
- directional
- Yagi
- dish
Explanation & Hint: Omnidirectional antennas send the radio signals in a 360 degree pattern around the antenna. This provides coverage to devices situated anywhere around the access point. Dishes, directional, and Yagi antennas focus the radio signals in a single direction, making them less suitable for covering large, open areas.
-
A wireless engineer accesses the WLC and configures a lightweight access point to function as a sniffer. Which two functions will be performed by the lightweight access point in this mode? (Choose two.)
- The lightweight AP will forward captured traffic to a PC running network analyzer software.
- The lightweight AP will offer one or more functioning BSSs on a specific channel.
- The lightweight AP will check for IDS events and determine the position of stations through location-based services.
- The lightweight AP will dedicate all of the physical radios to receiving 802.11 traffic from other sources.
- The lightweight AP will correlate MAC addresses heard on the wired network with those heard over the air to detect rogue devices.
Explanation & Hint: Once a special mode is activated on a lightweight AP, local mode and the corresponding BSSs will be disabled. A lightweight AP acting as a sniffer will dedicate all of the radios to receiving 802.11 traffic from other sources and forwarding that traffic to a PC that has network analyzer software installed.
-
How is the beamwidth of a wireless antenna measured on a plot?
- The beamwidth is determined by finding the weakest point on the plot and following it in either direction until the signal increases by 3 dB.
- The beamwidth is determined by finding the weakest point on the plot and following it in either direction until the signal decreases by 10 dB.
- The beamwidth is determined by finding the strongest point on the plot and following it in either direction until the signal decreases by 3 dB.
- The beamwidth is determined by finding the strongest point on the plot and following it in either direction until the signal decreases by 10 dB.
Explanation & Hint: Beamwidth is viewed as a measure of focus for a particular antenna. Beamwidth is determined by finding the strongest point on the plot and following it in either direction until the signal is one-half of the strongest power or 3 dB less.
-
A wireless engineer is troubleshooting signal degradation between two wireless antennas connecting over a distance. If no physical obstructions are found to be blocking the wireless signal, what is most likely the issue?
- The polarization of the transmitting antenna does not match the polarization of the receiving antenna.
- The gain of the transmitting antenna does not match the gain of the receiving antenna.
- The polarization of the transmitting antenna is 3 dB less than the receiving antenna.
- The transmitting and receiving antennas are mismatched and not providing a compatible radiation pattern.
Explanation & Hint: In order for two wireless antennas to not suffer from signal degradation, the polarization of the transmitting antenna should match the polarization of the receiving antenna.
-
What is the purpose of a wireless client sending a reassociation request to an AP?
- to find the SSID of the AP
- to form a new association with the AP
- to roam from current AP to another AP
- to respond to the beacon signal sent by the AP
Explanation & Hint: When a client wants to join the BSS of an AP, it actively scans channels and sends probe requests to discover candidate APs. The client then selects one and tries to associate with it. A wireless client can send association request and reassociation request frames to the AP selected. Association requests are used to form a new association, while reassociation requests are used to roam from one AP to another, preserving the original association status of the client.
-
For its customers, a shopping center is deploying a wireless network that consists of 20 lightweight APs that are bound to a single WLC. Which type of roaming occurs when clients roam between APs on the shopping center network?
- Layer 2 roaming
- autonomous roaming
- intracontroller roaming
- intercontroller roaming
Explanation & Hint: When a wireless client is roaming among APs that are bound to the same WLC controller, the roam occurs entirely within the controller. This is known as intracontroller roaming. Intercontroller roaming occurs when a client is roaming among APs that are bound to different WLC controllers. Layer 2 roaming is a type of the intercontroller roaming.
-
A company deploys a Cisco wireless network over a large campus. The wireless network uses lightweight APs and multiple WLCs. A network technician walks around the campus to verify that wireless clients can roam smoothly between APs bound to different WLCs and assigned different VLANs and IP subnets. The technician verifies that while the client roams around campus, the client retains the same VLAN and IP address assigned. Which roaming scenario is the technician verifying?
- Layer 2 roaming
- Layer 3 roaming
- local-to-local roaming
- intracontroller roaming
Explanation & Hint: In a Cisco wireless network, when a client initiates an intercontroller roam, the two controllers involved can compare the VLAN numbers that are assigned to the respective WLAN interfaces. If the VLAN IDs are the same, the client undergoes a Layer 2 intercontroller roam (also called local-to-local roam) and can continue to use the original IP address on the new controller. If the two VLAN IDs differ, the controllers arrange a Layer 3 roam that will allow the client to keep using the same IP address.
-
A company deploys a Cisco wireless network over the campus. Wireless network access is needed for visitors to access the internet while on campus. What are two best practices in setting up APs and WLCs for secure wireless connections for visitors? (Choose two.)
- deploying autonomous APs for visitors
- only using private IP addresses for APs and clients
- putting the anchor controller specific for visitors behind firewall
- using static IP addressing for clients to better locate visitor clients
- configuring a WLC to be a static anchor controller specific for visitors to associate
Explanation & Hint: In Layer 3 roaming, anchor and foreign controllers are normally determined automatically. When a client first associates with an AP and a controller, that controller becomes its anchor controller. When the client roams to a different controller, that controller can take on the foreign role. However, sometimes it is desirable to control which WLC to be the anchor controller. For example, guest users should not be allowed to associate with just any controller in the network. Guests might be forced onto a specific controller that is situated behind a firewall or contained in a protected environment. This objective can be achieved by configuring one controller to be a static anchor for a WLAN so that other controllers will direct clients toward it through Layer 3 roaming tunnels.
-
What is a difficulty in locating a wireless client based on the RSS value when received by only one AP?
- The RSS value is affected by moisture in the air.
- The RSS value is affected by the air temperature.
- The distance from the client to the AP cannot be accurately determined.
- The orientation where the client is situated in relation to the AP cannot be determined.
Explanation & Hint: To improve the accuracy of locating a device, an AP can use the received signal strength (RSS) of a client device as a measure of the distance between the two. However, if the distance is measured from a single AP only, it is difficult to determine where the client is situated in relation to the AP. In the case of an indoor AP with an omnidirectional antenna, the client could be located anywhere along a circular path of fixed distance because the received signal strength would be consistent at all points on the circle.
-
Which two Cisco location solutions can work with Cisco management platforms to provide real-time location services for a wireless network? (Choose two.)
- DNA Space
- DNA Center
- Prime Infrastructure
- Identity Services Engine
- Mobility Services Engine
Explanation & Hint: Cisco APs and WLCs can integrate with management platforms like Cisco Prime Infrastructure or DNA Center, along with location servers like Cisco Mobility Services Engine (MSE), Cisco Connected Mobile Experiences (CMX), or Cisco DNA Spaces to gather location information in real time and present that information in a relevant way.
-
What is a Cisco solution developed to improve the results of wireless device location based on RSS values received by multiple APs?
- integrating customized GPS service on campus
- using DNA Center to provide secondary location parameters
- optimizing the algorithm to use 7 APs for determining the location
- developing RF fingerprinting where each mapped area is compensated with a calibration template
Explanation & Hint: The Cisco approach to improve the results of wireless device location based on RSS values received by multiple APs is to implement RF fingerprinting, where each mapped area is influenced by an RF calibration template that more closely resembles the actual signal attenuation experienced by the APs and clients.
-
Which tunneling technology is used to facilitate data exchange between a lightweight AP and a WLAN controller?
- GRE tunnel
- IPsec tunnel
- overlay tunnel
- CAPWAP tunnel
Explanation & Hint: In a lightweight AP topology, APs are bound to wireless LAN controllers through CAPWAP tunnels.
-
Which technique is used by Cisco WLCs to minimize the time required on key exchanges during roaming by maintaining a database of clients and keys on behalf of bound APs, and providing those clients and keys to other controllers and bound APs as needed during roaming?
- key caching
- 802.11r support
- intercontroller roaming
- Cisco Centralized Key Management (CCKM)
Explanation & Hint: Cisco controllers offer three techniques to minimize the time and effort spent on key exchanges during roams:
- Cisco Centralized Key Management ( CCKM ): One controller maintains a database of clients and keys on behalf of bound APs and provides the clients and keys to other controllers and bound APs as needed during client roams.
- Key caching : Each client maintains a list of keys used with prior AP associations and presents the keys as it roams.
- 802.11r : This 802.11 amendment addresses fast roaming or fast BSS transition. A client can cache a portion of the key of the authentication server and present that to future APs as it roams.
-
How is wireless client location determined based on RSS values when using three or more APs?
- correlating the RSS values received by multiple APs to determine where they intersect
- comparing the RSS values received by multiple APs to choose the shortest straight distance
- comparing the RSS values to choose the location of the AP with the highest RSS received
- correlating the RSS values received by multiple APs to determine where the LAN switches that are connected to the APs intersect
Explanation & Hint: To locate a device more accurately, an AP can use the received signal strength (RSS) of a client device as a measure of the distance between the two. However, if the distance is measured from a single AP only, it is difficult to determine where the client is situated in relation to the AP. A better solution is to obtain the same measurement from three or more APs, then correlate the results and determine where they intersect.
-
What technology does a Cisco WLC use to provide Layer 3 roaming to a wireless client?
- an IPsec tunnel to connect the client to the original AP
- a CAPWAP tunnel that tethers the client to the original anchor controller
- a GRE tunnel to relay the data between the original AP and the roamed AP
- a NAT translation to match the IP address in the roamed AP to the original AP
Explanation & Hint: A Layer 3 intercontroller roam consists of an extra CAPWAP tunnel that is built between the original controller with which the client associated (called the anchor controller) and the controller it has roamed to (called the foreign controller). The tunnel carries data to and from the client as if it is still associated with the original controller and IP subnet.