CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26: Access Control and Infrastructure Security Exam Answers Full 100% 2024
CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26: Access Control and Infrastructure Security Exam Answers Full 100% 2024
-
Which place in the network (PIN) is considered to be the highest-risk, as it is the ingress and egress point for internet traffic?
- edge
- cloud
- WAN
- data center
Explanation & Hint: The network edge is the ingress and egress point for traffic to and from the internet. It is the most important place in the network (PIN) for e-commerce and is also the highest-risk PIN.
-
What threat protection actions are involved in the “before” phase of the attack continuum?
- establishing policies and implementing prevention measures to reduce risks
- defining the abilities and actions that are required when an attack gets through
- detecting, containing, and remediating attacks
- conducting threat analysis and incident response
Explanation & Hint: Threat protection activities before a network attack include establishing the policies and implementing prevention solutions that can reduce risk.
-
Match the Cisco Safe security concepts to the description. (Not all options are used.)
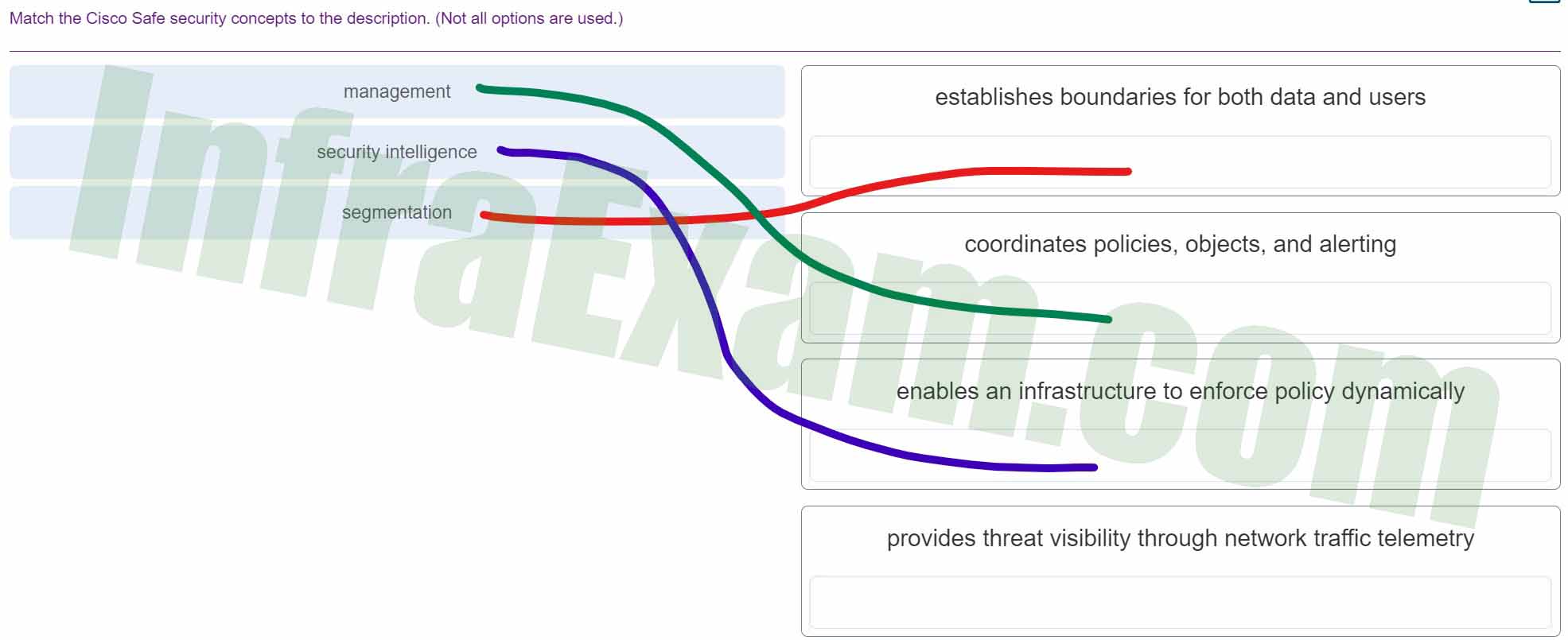
CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26 Access Control and Infrastructure Security Exam Answers 001 - management ==> coordinates policies, objects, and alerting
- security intelligence ==> enables an infrastructure to enforce policy dynamically
- segmentation ==> establishes boundaries for both data and users
- provides threat visibility through network traffic telemetry ==> Not matched
Explanation & Hint: The Cisco SAFE (Security Architecture for Enterprise) framework is a guide for designing network security. Here are explanations for the security concepts that are typically associated with the Cisco SAFE model, which might match the descriptions you have in your image:
- Management: This typically refers to the administration of security policies, the configuration of security solutions, and the ongoing management of the security infrastructure. In a broader sense, it could also include incident response, change management, and the operational aspects of security.
- Security Intelligence: This refers to the collection, analysis, and application of data to identify, categorize, and respond to threats. Security intelligence solutions might include threat intelligence feeds, security information and event management systems (SIEMs), and data from various security sensors.
- Segmentation: In the context of network security, segmentation is about creating boundaries within the network to control access and limit the scope of potential breaches. It involves dividing the network into segments or zones, each with its own security controls. Segmentation can help in establishing boundaries for both data and users, ensuring that users can only access the network segments that are relevant to their role.
-
Match the Cisco SAFE component with the description. (Not all options are used.)
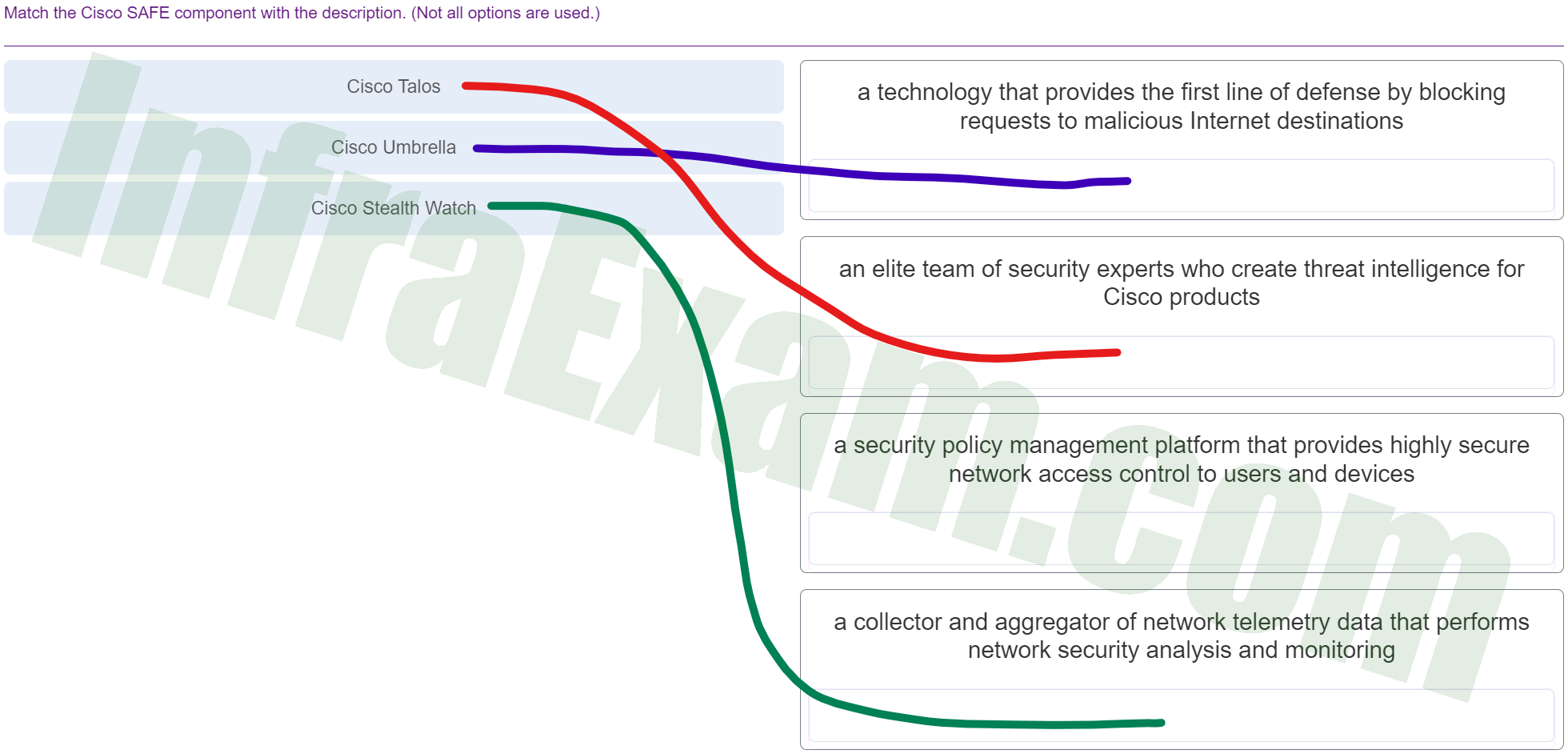
CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26 Access Control and Infrastructure Security Exam Answers 002 - Cisco Talos ==> an elite team of security experts who create threat intelligence for Cisco products
- Cisco Umbrella ==> a technology that provides the first line of defense by blocking requests to malicious Internet destinations
- Cisco Stealth Watch ==> a collector and aggregator of network telemetry data that performs network security analysis and monitoring
- a security policy management platform that provides highly secure network access control to users and devices ==> Not matched
Explanation & Hint: Cisco Talos: This is Cisco’s elite threat intelligence organization that is responsible for analyzing and managing cyber threats. The team of security experts in Talos detects, analyzes, and protects against both known and emerging threats while working to discover new vulnerabilities in software and hardware. So, the description “an elite team of security experts who create threat intelligence for Cisco products” matches with Cisco Talos.
Cisco Umbrella: Formerly known as OpenDNS, Cisco Umbrella is a cloud security platform that provides the first line of defense against threats on the internet by blocking requests to malicious destinations before a connection is established. It offers DNS-layer security, secure web gateway, firewall, and cloud access security broker (CASB) functionality. The description “a technology that provides the first line of defense by blocking requests to malicious Internet destinations” matches with Cisco Umbrella.
Cisco Stealthwatch: This is Cisco’s network telemetry-based security analytics solution. Stealthwatch collects and aggregates data from across the entire network, which enables it to perform security monitoring and behavioral modeling to detect anomalies and threats. The description “a collector and aggregator of network telemetry data that performs network security analysis and monitoring” matches with Cisco Stealthwatch.
-
Which solution provides comprehensive network and data protection for organizations before, during, and after a malware attack?
- Cisco AMP
- Cisco ISE
- Cisco Stealthwatch
- Cisco Umbrella
Explanation & Hint: Cisco Advanced Malware Protection (AMP) is a malware analysis and protection solution that provides comprehensive protection for organizations across the full attack continuum: before, during, and after.
-
Which solution provides VPN access for clients and performs an assessment of the VPN client security posture compliance?
- Cisco AnyConnect
- Cisco Umbrella
- Cisco AMP
- Cisco Talos
Explanation & Hint: Cisco AnyConnect is a client software product that provides VPN access to clients and also is capable of assessing endpoint compliance with antivirus, antispyware, and firewall software installed on the host.
-
Which type of threat defense is provided by Cisco Umbrella?
- blocking requests to malicious Internet destinations
- blocking hidden malware from both suspicious and legitimate websites
- identifying and blocking zero-day threats that manage to infiltrate the network
- monitoring and analyzing network traffic for potential network intrusion attacks
Explanation & Hint: Cisco Umbrella serves as a first line of defense for an organization by blocking requests to malicious internet destinations.
-
Which Cisco solution is used by Cisco Web Security Appliance to detect and correlate threats in real time?
- Cisco Talos
- Cisco Umbrella
- Cisco ISE
- Cisco Threat Grid
Explanation & Hint: Cisco Web Security Appliance (WSA) is a web gateway that offers a wide range of security protection. It leverages Cisco Talos for real-time intelligence so that is can stay ahead of the evolving threat landscape and protect against the latest exploits.
-
What security capability is provided by applying Cisco WSA web reputation filters before an attack?
- prevents client devices from accessing dangerous websites containing malware or phishing links
- provides administrators with granular control over web and mobile application usage behavior
- uses URL filtering to shut down access to websites known to host malware
- inspects the network continuously for instances of undetected malware and breaches
Explanation & Hint: Cisco Web Security Appliance (WSA) provides a variety of protections across the attack continuum before, during, and after an attack. Before an attack Cisco WSA uses web reputation filters to prevent client devices from accessing dangerous websites containing malware or phishing links and to block those that fall below a defined security threshold.
-
Which security appliance passively monitors and analyzes network traffic for potential network intrusion attacks and logs the attacks for analysis?
- intrusion detection system
- intrusion prevention system
- next-generation firewall
- web security appliance
Explanation & Hint: An intrusion detection system (IDS) is a system that passively monitors and analyzes network traffic for potential network intrusion attacks and logs the intrusion attack data for security analysis.
-
According to Gartner, Inc. what three capabilities must a next-generation firewall (NGFW) provide in addition to standard firewall features? (Choose three.)
- an integrated IPS
- the ability to perform application-level inspection
- the ability to leverage external security intelligence
- incident response and forensics
- real-time contextual awareness
- the ability to identify users who click malicious URLs
Explanation & Hint: In addition to IPS functionality, Gartner Inc. states a next-generation firewall (NGFW) should include the following capabilities:
An integrated IPS
Application-level inspection
The ability to leverage external security intelligence to address evolving security threats
-
Match the security platform to the description. (Not all options are used.)
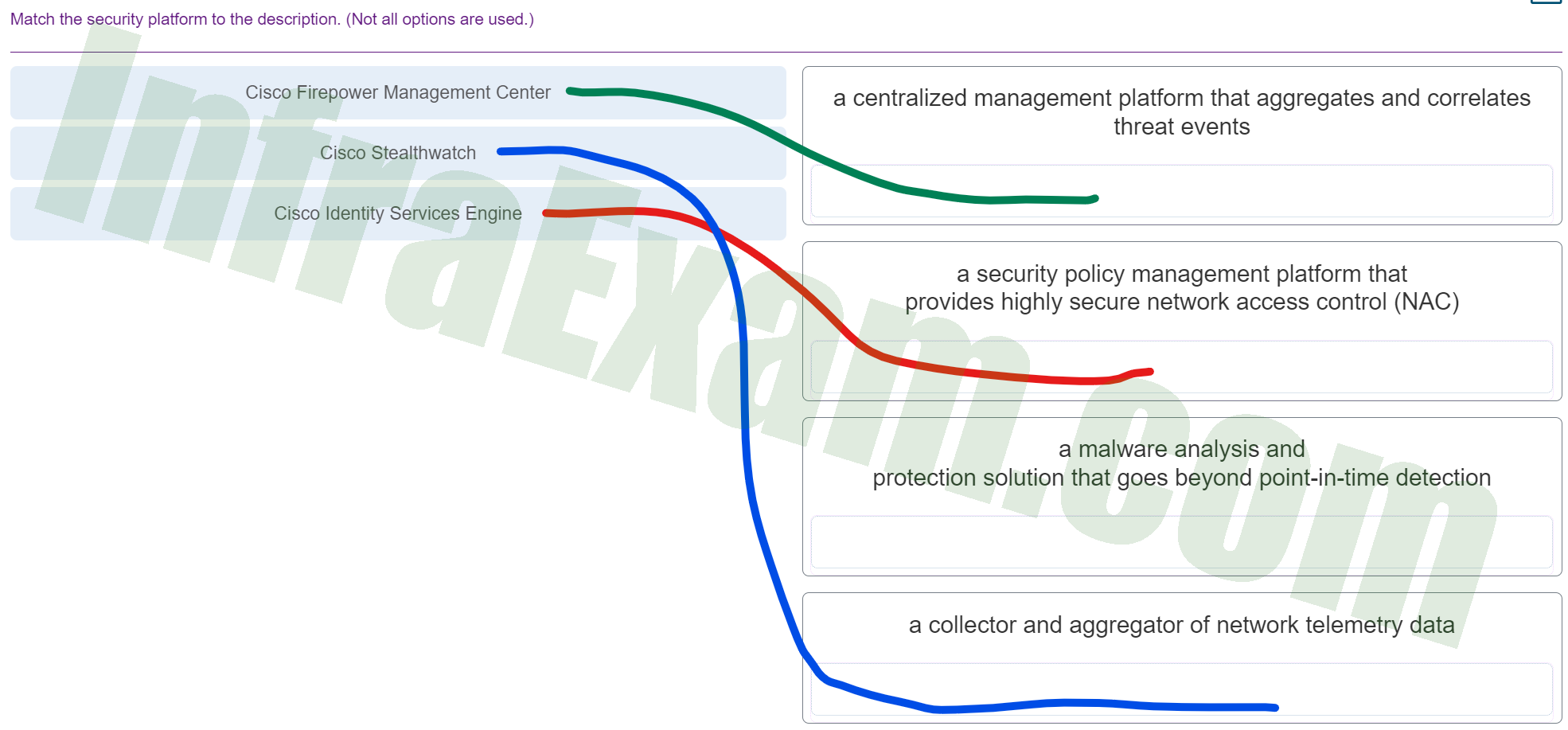
CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26 Access Control and Infrastructure Security Exam Answers 003 - Cisco Firepower Management Center ==> a centralized management platform that aggregates and correlates threat events
- Cisco Stealthwatch ==> a collector and aggregator of network telemetry data
- Cisco Identity Services Engine ==> a security policy management platform that provides highly secure network access control (NAC)
- a malware analysis and protection solution that goes beyond point-in-time detection ==> Not matched
Explanation & Hint: Cisco Firepower Management Center: This is a centralized security management tool that provides comprehensive management over firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection. It aggregates and correlates threat events to help manage and mitigate risks.
Cisco Stealthwatch: This is Cisco’s network telemetry-based security analytics solution. Stealthwatch collects and aggregates network telemetry data across the enterprise and uses it to detect advanced threats, respond to security incidents quickly, and simplify network segmentation and compliance.
Cisco Identity Services Engine (ISE): ISE is a security policy management platform that enables the creation and enforcement of security and access policies for endpoint devices connected to an organization’s network. It provides network access control (NAC) and is designed to deliver highly secure access control across wired and wireless multivendor networks.
-
Which secure access solution can be implemented to authenticate endpoints that do not support 802.1x or MAB?
- web authentication
- Enhanced Flexible Authentication
- Cisco Identity-Based Network Services
- Cisco TrustSec
Explanation & Hint: Some endpoints that need access to the network may not have 802.1x supplicants and may not know the MAC address to perform MAB. This can be a problem for contractors or visitors that need internet access. In such cases web authentication can be implemented to present a user with web portal requesting a username and password.
-
Which EAP method makes use of the Protected Extensible Authentication Protocol (PEAP)?
- EAP tunneled TLS authentication method
- EAP challenge-based authentication method
- EAP TLS authentication method
- EAP inner authentication method
Explanation & Hint: PEAP is used in EAP tunneled TLS authentication methods. PEAP forms an encrypted TLS tunnel between the supplicant and the authentication server and uses an EAP authentication inner method to authenticate the supplicant through the outer PEAP TLS tunnel.
-
What message is sent every 30 seconds by the 802.1x authenticator to an endpoint to initiate the MAB authentication process?
- EAPoL identity request
- RADIUS access-request
- RADIUS access-accept
- EAPoL start
-
Explanation & Hint: The authenticator initiates the 802.1x MAB authentication process by sending an EAPoL identity request message to the endpoint every 30 seconds to determine if it has a supplicant.
-
What are the three phases of TrustSec configuration? (Choose three.)
- ingress classification
- propagation
- egress enforcement
- access-request
- access-accept
- start
Explanation & Hint: TrustSec configuration occurs in three phases:
Ingress classification – where SGT tags are assigned to users and resources
Propagation – where mappings to the TrustSec devices are made based on SGT tags
Egress enforcement – where policies are enforced at the egress point of the TrustSec network
-
Which set of access control entries would allow all users on the 192.168.10.0/24 network to access a web server that is located at 172.17.80.1, but would not allow them to use Telnet?
- access-list 103 deny tcp host 192.168.10.0 any eq 23
access-list 103 permit tcp host 192.168.10.1 eq 80 - access-list 103 permit 192.168.10.0 0.0.0.255 host 172.17.80.1
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq telnet - access-list 103 permit tcp 192.168.10.0 0.0.0.255 host 172.17.80.1 eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23 - access-list 103 permit tcp 192.168.10.0 0.0.0.255 any eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23Explanation & Hint: For an extended ACL to meet these requirements the following need to be included in the access control entries:
identification number in the range 100-199 or 2000-2699
permit or deny parameter
protocol
source address and wildcard
destination address and wildcard
port number or name
- access-list 103 deny tcp host 192.168.10.0 any eq 23
-
Which three statements describe ACL processing of packets? (Choose three.)
- An implicit deny any rejects any packet that does not match any ACE.
- A packet can either be rejected or forwarded as directed by the ACE that is matched.
- A packet that has been denied by one ACE can be permitted by a subsequent ACE.
- A packet that does not match the conditions of any ACE will be forwarded by default.
- Each statement is checked only until a match is detected or until the end of the ACE list.
- Each packet is compared to the conditions of every ACE in the ACL before a forwarding decision is made.
Explanation & Hint: When packets are checked against an access list, each ACE in the access list is checked in sequence until a match is detected. At the end of all access lists is an implicit deny any ACE. Packets will be dropped or forwarded as directed by the matching ACE.
-
Refer to the exhibit. An ACL was configured on R1 with the intention of denying traffic from subnet 172.16.4.0/24 into subnet 172.16.3.0/24. All other traffic into subnet 172.16.3.0/24 should be permitted. This standard ACL was then applied outbound on interface G0/0/0. Which conclusion can be drawn from this configuration?
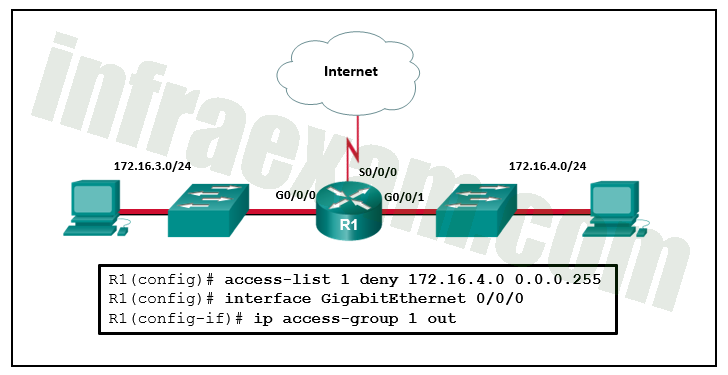
CCNPv8 ENCOR (Version 8.0) – Chapters 25 – 26 Access Control and Infrastructure Security Exam Answers 02 - Only traffic from the 172.16.4.0/24 subnet is blocked, and all other traffic is allowed.
- An extended ACL must be used in this situation.
- The ACL should be applied to the GigabitEthernet 0/0/0 interface of R1 inbound to accomplish the requirements.
- All traffic will be blocked, not just traffic from the 172.16.4.0/24 subnet.
- The ACL should be applied outbound on all interfaces of R1.
Explanation & Hint: Because of the implicit deny at the end of all ACLs, the access-list 1 permit any command must be included to ensure that only traffic from the 172.16.4.0/24 subnet is blocked and that all other traffic is allowed.
-
What are two limitations of PACLs? (Choose two.)
- no filtering of outbound traffic
- no support of ACLs that filter IPv6 packets
- can only filter Layer 2 traffic
- only support extended ACLs
- only support numbered ACLs
Explanation & Hint: PACLs have some limitations and restrictions. PACLs do not support filtering of outbound traffic on an interface and they do not support ACLs filtering IPv6. Also, PACLs do not support Layer 2 control packets like STP, CDP, or VTP and are only supported in hardware.
-
An administrator defined a local user account with a secret password on router R1 for use with SSH. Which three additional steps are required to configure R1 to accept only encrypted SSH connections? (Choose three.)
- Configure the IP domain name on the router.
- Enable inbound vty Telnet sessions.
- Generate crypto keys.
- Configure DNS on the router.
- Configure a host name other than “Router”.
- Generate two-way pre-shared keys.
Explanation & Hint: There are three steps to configure SSH support on a Cisco router:
Step 1: Configure a hostname.
Step 2: Configure a domain name.
Step 3: Generate crypto keys.
-
Which command produces an encrypted password that is easily reversible?
- service password-encryption
- enable secret {password}
- username {username} algorithm-type sha256 {password}
- username {username} secret {password}
Explanation & Hint: The service password-encryption command uses a Cisco proprietary Vignere cypher algorithm which is weak and easily reversible. The enable secret and the username secret commands encrypt passwords using the MD5 hashing algorithm and the username algorithm-type sha 256 command uses a SHA-256 hashed secret and is considered uncrackable.
-
Which is the preferred method for securing device terminal lines?
- AAA authentication
- a password configured directly on the terminal lines
- username-based authentication
- username-based authentication restricted with an ACL
Explanation & Hint: The preferred method for securing device terminal lines is to use an AAA server. Username-based authentication is recommended as a backup. Configuring a password directly on the line is not recommended.
-
What protocol is used to encapsulate the EAP data between the authenticator and authentication server performing 802.1X authentication?
- RADIUS
- TACACS+
- SSH
- MD5
Explanation & Hint: Encapsulation of EAP data between the authenticator and the authentication server is performed using RADIUS.
-
Which statement describes a difference between RADIUS and TACACS+?
- RADIUS uses TCP, whereas TACACS+ uses UDP.
- RADIUS does not support EAP for 802.1x, whereas TACACS+ does.
- RADIUS encrypts only the password, whereas TACACS+ encrypts all communication.
- RADIUS separates authentication and authorization, whereas TACACS+ combines them as one process.
Explanation & Hint: TACACS+ uses TCP, encrypts the entire packet (not just the password), and separates authentication and authorization into two distinct processes. Both protocols are supported by the Cisco Secure ACS software.
-
What is a feature of a Cisco IOS Zone-Based Policy Firewall?
- Router management interfaces must be manually assigned to the self zone.
- Service policies are applied in interface configuration mode.
- A router interface can belong to only one zone at a time.
- The pass action works in multiple directions.
Explanation & Hint: The pass action allows traffic in only one direction. Interfaces automatically become members of the self zone. Interfaces are assigned to a zone in interface configuration mode, but most configuration takes place in global configuration mode and associated submodes. An interface can belong to only one zone at a time.
-
Which statement describes Cisco IOS Zone-Based Policy Firewall operation?
- The pass action works in only one direction.
- A router interface can belong to multiple zones.
- Service policies are applied in interface configuration mode.
- Router management interfaces must be manually assigned to the self zone.
Explanation & Hint: The pass action allows traffic only in one direction. Interfaces automatically become members of the self zone. Interfaces are assigned to zones in interface configuration mode, but most configuration takes place in global configuration mode and associated submodes. Interfaces can belong to only one zone at any time.
-
What are two characteristics of the ZBFW default zone? (Choose two.)
- It is a system built zone.
- Interfaces that are not members of other zones are placed in this zone by default.
- By default, all IP addresses on a router are included in the default zone.
- All traffic is permitted by default to and from the default zone.
- By default, interfaces in the default zone are permitted to communicate with interfaces in other zones.
Explanation & Hint: The default zone is a system-level zone. If an interface is not configured as part of another security zone, it is placed in the default zone automatically. Interfaces in different zones are not permitted to communicate by default.
-
What is the Control Plane Policing (CoPP) feature designed to accomplish?
- manage services provided by the control plane
- prevent unnecessary traffic from overwhelming the route processor
- disable control plane services to reduce overall traffic
- direct all excess traffic away from the route processor
Explanation & Hint: Control Plane Policing (CoPP) does not manage or disable any services. It does not direct traffic away from the route processor, but rather it prevents unnecessary traffic from getting to the route processor.
-
Which command can be issued to protect a Cisco router from unauthorized automatic remote configuration?
- no service config
- no ip proxy-arp
- no cdp enable
- no service pad
Explanation & Hint: Service configuration allows Cisco devices to be configured automatically from remote devices using TFTP. By disabling this service with the no service config command, the threat of an unauthorized automatic device configuration can be mitigated.
-
Which vulnerability can be mitigated by disabling CDP and LLDP on a Cisco device?
- advertising detailed information about a device
- half-open or orphaned TCP connections
- answering APR requests intended for other devices
- automatic remote configuration
Explanation & Hint: Both CDP and LLDP are topology discovery tools and can advertise detailed information about a device. To prevent a Cisco device from sending CDP and LLDP packets onto the network, both protocols should be disabled.