300-410 : Implementing Cisco Enterprise Advanced Routing and Services (ENARSI) : Part 08
-
You are troubleshooting an issue with the configuration of mGRE on the hub router in a hub-and-spoke configuration. Examine the output of the configuration of the tunnel interface on the hub router:
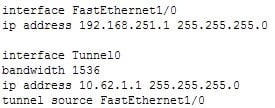
300-410 Part 08 Q01 094 Which of the following statements is true?
- The tunnel destination must be specified on the tunnel interface
- the tunnel mode gre multipoint command must be executed on the tunnel interface
- the tunnel mode gre multipoint command must be executed on the physical interface
- The tunnel destination must be specified on the physical interface
Explanation:
The tunnel mode gre multipoint command must be executed on the tunnel interface. An mGRE configuration is one in which the tunnel is allowed to have multiple destinations. The distinguishing feature between an mGRE interface and a point-to-point GRE interface is the tunnel destination. While it is specified on a point-to-point GRE interface, it is not on an mGRE interface. Instead the command tunnel mode gre multipoint is executed on the tunnel interface. This allows the interface to use the Next Hop Routing protocol (NHRP) to discover the IP addresses of the other tunnel endpoints.The tunnel destination is not specified on the tunnel interface using mGRE. Instead the command tunnel mode gre multipoint is executed on the tunnel interface.
The tunnel mode gre multipoint command must be executed on the tunnel interface, not the physical interface.
The tunnel destination is neither specified on the tunnel interface nor on the physical interface when using mGRE.
Objective:
VPN Technologies
Sub-Objective:
Configure and verify GRE -
You are planning the configuration of Easy Virtual Networking (EVN).
Which of the following statements is true of an interface that will be an EVN trunk?
- It must support 802.1q encapsulation
- The interface can also be configured for VRF-Lite
- The interface will support OSPFv3
- The interface can support RIP
Explanation:
The interface must be able to support 802.1q encapsulation. The EVN trunk carries the traffic of multiple virtual routing and forwarding (VRF) instances, with the traffic of each instance tagged with an ID called the virtual network tag. Since the VLAN ID field of an 802.1q encapsulated packet is used for this ID, the link must be one that supports 802.1q.Easy Virtual networking is a technology that allows for the creation of separate networks with separate routing tables and routing instances using the same physical topology. The IP addressing for the networks can even overlap with no problem. The networks are kept separate using the network ID tags in a similar fashion to the way switches keep VLANs separate by using VLAN tags.
An EVN trunk interface cannot also be configured for VRF-Lite. VRF-Lite is an earlier technology that accomplishes the same goal, but lacks the simplicity of EVN.
Neither RIP nor OSPFv3 is supported in Easy Virtual Networking EVN at all.
Objective:
VPN Technologies
Sub-Objective:
Describe Easy Virtual Networking (EVN) -
After an associate configured a DMVPN hub, you execute the following command on the hub router:

300-410 Part 08 Q03 095 Which of the following statements is true of this output?
- The NMBA address was statically configured
- The NHRP information did not come from the NHS
- The mapping was created through an NHRP registration request
- The device at 10.1.1.2 is behind a NAT router
Explanation:
The mapping was created through an NHRP registration request, as indicated by the flag setting registered. Next Hop Resolution Protocol (NHRP) can be used in place of static IP address to NBMA address mappings to allow the spoke routers in an mGRE hub-and-spoke configuration to discover one another’s physical IP addresses.When the output of the show nhrp detail command shows the registered flag listed, it means that the mapping was created dynamically and was learned through a registration request to the next hop server (NHS).
The mapping was not created statically. Had it been created statically, the Type field would not be listed as dynamic. It would say static.
The NHRP information DID come from the next hop server (NHS). That is indicated by the presence of the authoritative flag. The NHS is the next hop to the destination as indicated by the routing table.
The device at 10.1.1.2 is not necessarily behind a NAT router. The presence of the nat flag in the output indicates that the device at 10.1.1.2 supports the NHRP NAT extension type for supporting dynamic spoke-to-spoke tunnels to or from spokes behind a NAT router. This flag does not mean that the spoke (NHS client) is behind a NAT router.
Objective:
VPN Technologies
Sub-Objective:
Describe DMVPN (single hub) -
The following commands were executed on the perimeter router. The Fa1/0 interface in the router is the external interface.
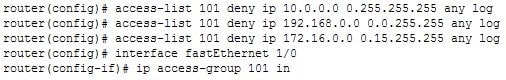
300-410 Part 08 Q04 096 What will be the effect of these commands?
- all traffic will be blocked incoming
- traffic sourced from private IP addresses will be blocked incoming
- traffic destined for private IP addresses will be allowed incoming
- no traffic will be blocked incoming
Explanation:
All traffic will be blocked incoming. While it appears on the surface that this list was designed to block incoming traffic sourced from private IP addresses, it is lacking a single permit statement. Due to the implied deny all at the end of the list, no traffic will be allowed incoming.Blocking incoming traffic from private IP addresses is a way to prevent IP spoofing, since there should be no reason for traffic from private IP addresses to be incoming from the Internet. However, you need to include a permit statement at the end to allow all other traffic types.
Traffic destined for private IP addresses is not all that will be blocked by this command set. In fact, no traffic would be allowed. If there were a permit ip any any at the end of the list, then incoming traffic destined for private IP addresses would be allowed. This is probably not a great idea either, but if it a permit IP any were added at the end of the command set in the scenario, it would allow incoming traffic destined for private IP addresses.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Examine the following access list:
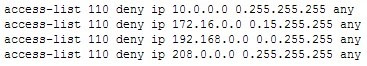
300-410 Part 08 Q05 097 Which statement is NOT designed to prevent IP spoofing attacks from packets that appear to be sourced from inside the network, but are actually sourced from outside the network?
- access-list 110 deny ip 10.0.0.0 0.255.255.255 any
- access-list 110 deny ip 172.16.0.0 0.15.255.255 any
- access-list 110 deny ip 192.168.0.0 0.0.255.255 any
- access-list 110 deny ip 208.0.0.0 0.255.255.255 any
Explanation:
Infrastructure access control lists are designed to prevent spoofing attacks from packets that appear to be sourced from inside the network when they are in fact sourced from outside the network. There are two groups of address that should be blocked at the edge of the network:
The private address space, which are called RFC 1918 addresses
Certain “special use addresses” as defined in RFC 3330The address 208.0.0.0 0.255.255.255 falls into neither of those categories.
The RFC 1918 addresses that should be blocked are:
10.0.0.0/24
172.16.0.0/16
192.168.0.0/16The RFC 3330 addresses that should be blocked are:
0.0.0.0
127.0.0.0/8
192.0.2.0/24
224.0.0.0/4For more information about these special use addresses, see RFC 3330.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Examine the following output of the show ip route command and the partial output of the show run command from the router R63:

300-410 Part 08 Q06 098 What will the router do with a packet with a source address of 192.168.5.5/24 and a destination address of 10.11.11.20/ 24 that arrives on the Serial0/0 interface?
- forward it out the Ethernet0/0 interface
- forward it out the Tunnel0 interface
- drop the packet
- forward it out the Ethernet0/1 interface
Explanation:
It will drop the packet. The partial output of the show run command shows that the ip verify unicast source reachable via rx command has been executed on the Serial 0/0 interface. This enables the Unicast Reverse Path Forwarding (Unicast RPF) feature. This feature prevents IP spoofing by verifying from the routing table that there is a valid return path to the source IP address. If there is not valid return path, you can assume the IP address has been spoofed. When the command ends in the keyword rx, it means that there must be a return path through the interface where the command was executed. This is called strict mode.The packet arrived on the Serial0/0 interface. The routing table shows that there is no routing entry for the 192.168.5.0/24 network that leads back through the entry interface of Serial0/0. In fact, in this instance there is no routing table entry for that network leading to any interface. When this occurs, the router will drop the packet.
The router will not send the packet to either the Ethernet0/0 or the Tunnel0 interfaces because the destination network, 10.11.11.0/24, is not a reachable destination on those interfaces. Even if it were reachable, the Unicast Reverse Path Forwarding (Unicast RPF) feature will drop the packet because it has been spoofed.
It will not send the packet to the Ethernet0/1 interface. The Unicast Reverse Path Forwarding (Unicast RPF) feature will drop the packet because it has been spoofed. If the packet were not spoofed, it would be sent to the Ethernet0/1 interface because that is the interface used by the default route. Because there is no route in the table to the 10.11.11.0/24 network, it would be sent to the default route.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
An associate creates the following access list that she plans to apply to an interface on a router:access-list 100 permit ip any any log
What type of traffic could cause this ACL to place a heavy load on the CPU of the router, and what command could be used to reduce the impact of the ACL? (Choose two.)
- traffic that is CEF switched
- traffic that is process switched
- traffic that is fast switched
- ip access-list log-update threshold
- ip access-list logging interval
- logging rate limi
Explanation:
There are two contributors to the CPU load increase from ACL logging: process switching of packets that match log-enabled access control entries (ACEs), and the generation and transmission of the log messages. To reduce the impact of process switched traffic, the ip access-list logging interval command can be used. The interval is specified in milliseconds and represents how often a single packet is process switched. While the messages in the generated log entries may not be as comprehensive after this command is executed, the counter values that are generated by the show access-list and show ip-access list commands will still be accurate.Packets that are not process switched (CEF switched and fast switched) will examined or accounted for in the logging, so they are not the source of the problem.
The ip access-list log-update threshold command is used to configure how often syslog messages are generated and sent after the initial packet match. While this would be a beneficial command to run, as it addresses the second source of CPU congestion that is the sending of the syslog messages, that was not listed as a traffic type option. Therefore, this would not be a solution to the issue presented by packet switched traffic.
The logging rate limit command also will reduce the impact of log generation and transmission on the CPU, but again, it does not address the issue presented by process switched traffic.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Which of the following commands enables Unicast Reverse Path forwarding in loose mode?
- ip verify unicast source reachable-via rx
- ip verify unicast source reachable-via any
- ip verify unicast source reachable-via rx allow default
- ip verify unicast source reachable-via allow default
Explanation:
The command ip verify unicast source reachable-via any enables Unicast Reverse Path Forwarding (RPF) in loose mode. In loose mode, traffic is allowed if the source address is reachable via any interface on the router as indicted in the routing table. Unicast Reverse Path forwarding uses the source IP address when it validates the packet. Packets are validated when the source address is contained in the routing table and is reachable either via the ingress interface (strict mode) or via any interface (loose mode).The command ip verify unicast source reachable-via rx enables Unicast RPF in strict mode, not loose mode. The rx keyword indicates the source must be reachable on the interface where the packet arrived.
The command ip verify unicast source reachable-via rx allow default enables Unicast RPF in strict mode. The inclusion of the allow default keyword indicates the source can be reachable via a default route to be accepted.
The command ip verify unicast source reachable-via allow default is syntactically incorrect. The allow default keyword cannot be present by itself. It must follow either the rx or any keywords.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
The following access lists are applied to an interface connecting two OSPF routers:

300-410 Part 08 Q09 099 What is the result?
- the DR on the link will begin updating
- the OSPF adjacency will go down
- the last deny statement will fail to log traffic
- the list will only permit IPv6 neighbor advertisements
Explanation:
If this list is applied to the interface connecting two OSPF routers, the OSPF adjacency would go down. The deny ip any any log statement will deny the IPv6 link local addresses, which are used for the neighbor discovery process and by OSPF routers to establish neighbor adjacencies when directly connected.By default, IPv6 access lists have a deny all at the end that does NOT include those addresses. However, when you set an explicit deny all as shown in the scenario, you will block all traffic that is not specified by an earlier statement in the list.
The DR on the link, if present, will not begin updating because the adjacency will fail. It will then have no neighbor to update.
The last deny statement in the scenario will log any traffic it blocks, as indicated by the inclusion of the log keyword.
The list will NOT permit neighbor advertisements. These are always done in terms of link local addresses, which the explicit deny ip any any log statement at the end will block.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Which of the following IPv6 access list statements would permit SSH traffic from 2001:DB8:0:4::32 when applied to the VTY lines?
- permit ipv6 2001:DB3:0:5::/48 any eq ssh
- permit ipv6 2001:DB8:0:4::/64 any eq ssh
- permit ipv6 host 2001:DB8:0:4::32 any eq 23
- permit ipv6 2001:DE8:0:4:::/48 any eq 22
Explanation:
The only statement that would allow SSH traffic from 2001:DB8:0:4::32 is permit ipv6 2001:DB8:0:4::/64 any eq ssh. It would match because it specifies the 2001:DB8:0:4:: subnet as a result of the /64 prefix. With that prefix, traffic must match in the first four hextets. Since the address 2001:DB8:0:5::32 matches in the first four hextets, it is allowed.The statement permit ipv6 2001:DB3:0:5::/48 any eq ssh will not permit traffic from 2001:DB8:0:4::32. With a /48 subnet mask, the address must match in the first three hextets, and it does not do
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Examine the following output of the show ip route command and the partial output of the show run command from the router R64:
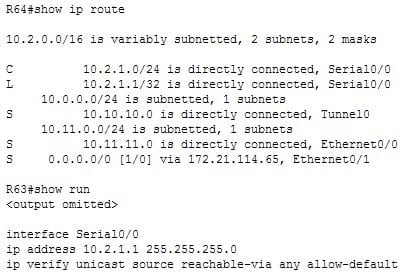
300-410 Part 08 Q11 100 What will the router do with a packet with a source address of 10.2.1.7/24 and a destination address of 10.11.11.50/ 24 that arrives on the Serial0 interface?
- forward it out the Serial0/0 interface
- forward it out the Tunnel0 interface
- drop the packet
- forward it out the Ethernet0/0 interface
Explanation:
It will forward the packet out the Ethernet 0/0 interface. The partial output of the show run command shows that the ip verify unicast source reachable via any command has been executed on the Serial 0/0 interface. This enables the Unicast Reverse Path Forwarding (Unicast RPF) feature. This feature prevents IP spoofing by verifying from the routing table that there is a valid return path to the source IP address. If there is not valid return path, you can assume the IP has been spoofed.When the ip verify unicast source reachable via command ends with the key word any , it means the return path can be through any interface, not just the one where the command was executed. This is called loose mode. It also includes the parameter allow-default which removes the requirement that the network be specifically mentioned in the routing table.
Since there is a routing table entry for the source network leading to the Serial0/0 interface, the packet will be forwarded to the destination network reachable using the route via the E0/0 interface.
The router will not send the packet to either the Serial0/0 or the Tunnel0 interfaces because the destination network, 10.11.11.0/24, is not a reachable destination on those interfaces.
It will not send the packet to the Ethernet0/1 interface because that is the interface used by the default route. Because there is a route in the table to the 10.11.11.0/24 network, it would be sent to the Ethernet 0/0 interface.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
When the log keyword is added to an access list statement, CPU utilization increases.
What is the source of the increased CPU utilization? (Choose all that apply.)
- the process switching of packets that match the ACE
- the incrementing of the match counter every 60 seconds
- the generation and transmission of log messages
- the CEF switching of packets that match the ACE
Explanation:
The source of the increased CPU utilization will have two sources. First is the process switching of each packet that matches the ACE, which is a slower switching method than CEF switching. The second is the generation and transmission of the log messages. Both effects can be mitigated by adjusting the logging interval and the message interval.The CPU utilization does NOT increase from the incrementing of the match counter every 60 seconds. The match counter increments every 5 minutes by default.
The CPU utilization does NOT increase from the CEF switching of packets that match the ACE. Those packets will be process switched, which is a much slower process than CEF switching.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Earlier today you created and applied an access list designed to restrict remote access to the router R62 ONLY from the device at 2001:DB8:0:4:: 32. During testing, you discover that it is not having the desired effect.You execute the show run command and see the following partial output that is relevant to the issue:
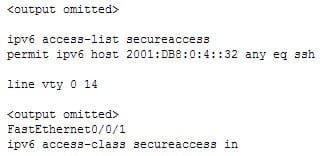
300-410 Part 08 Q13 101 Why is the access list not functioning correctly?
- the IPv6 address in the list is not formatted correctly
- the list is not applied to the proper interface
- the list is missing a deny statement
- the ipv6 access-group command should be used to apply the list
Explanation:
The list is applied to the wrong interface. An access list that is designed to control remote access should be applied to the VTY lines, not to one of the physical interfaces. If the command were formatted correctly, the show run output would appear as follows:
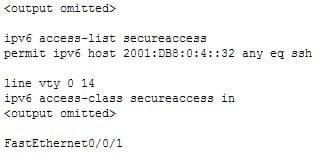
300-410 Part 08 Q13 102 The IPv6 address is formatted correctly. Although it has been shortened in format, it follows all of the shortening rules. It omits only leading zeros and it utilizes the double colon only once.
The access list does not require a deny statement. There is an implicit deny all at the end of the list.
The ipv6 access-group command should not be used to apply the list. This command is used when an access list is applied to a physical interface, not the VTY lines.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
The following command was executed on the router R61.R61#debug ip packet detail 105
What type of information will this debug command generate?
- all information on packets that are not fast switched by the router named 105
- all information on packets that are not fast switched by the local router
- information on packets that are not fast switched as filtered by the access list 105
- information on packets sent from router 105
Explanation:
This debug command will generate information on packets that are not fast switched as filtered by the access list 105. The output of certain debug commands can generate a tremendous amount of output, and in most cases a lot of information you don’t need. It can even impact the performance of the router while the debug command is in effect. The best way to reduce this output is to filter it through an extended access list.To do this, you create the access list as you would any other access list and then reference the access list number when you execute the debug command. For example, to restrict the output of the debug ip packet detail command to the traffic generate between the devices with the IP addresses 10.10.10.2 and 13.1.1.1, you would create the following extended access list:
access-list 105 permit icmp host 10.10.10.2 host 13.1.1.1
access-list 105 permit icmp host 13.1.1.1 host 10.10.10.2When you then execute the debug ip packet detail command and reference the list number of 105, it will only display debug output concerning communications between these IP addresses.
The number 105 in the command does not reference a router name or number. It references an access list number.
The command will not display all information on packets that are not fast switched by the local router. It will be limited to information as filtered in the access list 105.
The command will not list information on packets sent from router 105. The number 105 refers to an access list number, not a router.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
Which of the following commands must be present in the configuration to support Unicast RFP?
- bandwidth
- ip cef
- ip route 0.0.0.0 0.0.0.0
- log
Explanation:
The command ip cef must be present in the configuration to support Unicast Reverse Path Forwarding (RPF). If the router is set to its defaults, it will be present. Unicasts RPF uses the tables created by CEF to validate packet source addresses. Therefore, it must be enabled. Unicast RPF can be enabled in three modes:
Strict mode – The source address must be must be reachable on the interface where the packet arrived.
Loose mode – Traffic is allowed if the source address is reachable via any interface on the router as indicted in the routing table.
VRF mode – Evaluates an incoming packet’s source IP address against the VRF table configured for an eBGP neighbor.The bandwidth command, while desirable to ensure proper cost calculation of the interface for routing purposes, is not a requirement for Unicast RPF.
The ip route 0.0.0.0 0.0.0 command creates a default route. A default route does not need to be present for Unicast RPF to function.
The log command is not required. This command should be used with caution with any access list, as it causes an increase in CPU usage in the router.
Objective:
Infrastructure Security
Sub-Objective:
Configure and verify router security features -
When the auth keyword is used in the snmp-server host command, which of the flowing must be configured with an authentication mechanism?
- the interface
- the host
- the user
- the group
Explanation:
The auth keyword specifies that the user should be authenticated using either the HMAC-MD5 or HMAC-SHA algorithms. These algorithms are specified during the creation of the SNMP user.For example, the following command creates a user named V3User that will be a member of the SNMP group V3Group and will use HMAC-MD5 with a password of MyPassword:
snmp-server user V3User V3Group v3 auth md5 MyPassword
The authentication mechanism is not configured on the interface. All SNMP commands are executed at the global configuration prompt.
The authentication mechanism is not configured at the host level. The version and security model (authentication, authentication and encryption, or neither) are set at the host level.
The authentication mechanism is not configured at the SNMP group level. The group level is where access permissions like read and write are set. This is why a user account must be a member of a group to derive an access level, even if it is a group of one.
Objective:
Infrastructure Services
Sub-Objective:
Configure and verify SNMP -
You recently implemented SNMPv3 to increase the security of your network management system. A partial output of the show run command displays the following output that relates to SNMP.<output omitted>snmp-server group NORMAL v3 noauth read NORMAL write NORMAL
Which of the following statements is true of this configuration?
- it provides encryption, but it does not provide authentication
- it provides neither authentication nor encryption
- it provides authentication, but it does not provide encryption
- it provides both authentication and encryption
Explanation:
It provides neither authentication nor encryption. In SNMPv3 there are three combinations of security that can be used:
noAuthNoPriv- no authentication and no encryption noauth keyword in the configuration
AuthNoPriv – messages are authenticated but not encrypted auth keyword in the configuration
AuthPriv – messages are authenticated and encrypted priv keyword in the configuration
In this case, the keyword noauth in the configuration indicates that no authentication and no encryption are provided. This makes the implementation no more secure than SNMPv1 or SNMPv2.In SNMPv1 and SNMPv2, authentication is performed using a community string. When you implement SNMP using the noauth keyword, it does not use community strings for authentication. Instead it uses the configured user or group name (in this case NORMAL). Regardless, it does not provide either authentication or encryption.
Objective:
Infrastructure Services
Sub-Objective:
Configure and verify SNMP -
You execute the following command.router(config-if)#ip helper-address 172.20.14.225
Which of the following traffic types will NOT be forwarded to the IP address 172.20.14.225?
- TFTP
- SMTP
- DNS
- TACACS
Explanation:
While the ip helper address command is typically used to forward DHCP broadcasts to a DHCP server located in a remote subnet, it will also forward the following broadcast packets by default as well:
TFTP – UDP port 69
Domain Name System (DNS) UDP port 53
Time service – port 37
NetBIOS Name Server – port137
NetBIOS Datagram Server – port 138
Bootstrap Protocol (BOOTP) – port 67
TACACS UDP port 49Objective:
Infrastructure Services
Sub-Objective:
Configure and verify IPv4 and IPv6 DHCP -
You execute the debug ip packet command and find that you receive no output.
Which of the following is the MOST likely reason?
- someone executed the no ip route-cache command
- someone executed the no ip mroute cache command
- someone attached an extended access list to the debug process
- someone executed the ip cef command
Explanation:
When the ip cef command is executed, it enables Cisco Express Forwarding. When CEF is enabled, packets are no longer switched to the processor, so the output shows nothing. You must disable CEF and fast switching on the interface while you are running the debug ip packet command.Executing the no ip route-cache command would disable fast switching and would enable the gathering of packets rather than disable the operation.
Executing the no ip-mroute cache command would disable fast switching of multicast packets and would enable the gathering of multicast packets.
While it is possible that that an overly restrictive access list could result in NO output, this is only a possibility. On the other hand, it is certain that no output will be produced if the ip cef command was executed. Access lists SHOULD be used in conjunction with the debug ip packet command to reduce the significant amount of information generated and the system resources required to do so.
Objective:
Infrastructure Services
Sub-Objective:
Configure and verify logging -
You have implemented SNMP v3 in your network. You find after making the configuration changes that technicians in the RESTRICTED group cannot access the MIB. You execute the show run command and receive the following output that relates to SNMP:
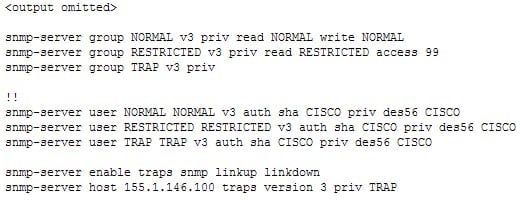
300-410 Part 08 Q20 103 What is preventing the RESTRICTED group from viewing the MIB?
- the presence of the keyword priv in the command creating the RESTRICTED group
- a mismatch between the authentication mechanism and the encryption type in the command creating the RESTRICTED user
- the absence of an access list defining the stations that can used by the RESTRICTED group
- the presence of the keyword auth in the command creating the RESTRICTED user
Explanation:
At the end of the command creating the RESTRICTED group is the parameter access 99. This indicates that an access list number 99 is being used to specify the allowed IP addresses of the stations that can be used to connect to the MIB for the group. Since the access list is missing from the configuration, no IP addresses will be allowed, and no connections can be made by the group.The presence of the keyword priv in the command creating the RESTRICTED group is not causing the issue. This keyword indicates that encryption (privacy) and authentication should both be used on all transmissions by the group.
In SMNPv3, there are three combinations of security that can be used:
noAuthNoPriv- no authentication and no encryption noauth keyword in the configuration
AuthNoPriv – messages are authenticated but not encrypted auth keyword in the configuration
AuthPriv – messages are authenticated and encrypted priv keyword in the configuration
There is no mismatch between the authentication mechanism and the encryption type in the command creating the RESTRICTED user.snmp-server user RESTRICTED RESTRICTED v3 auth sha CISCO priv des56 CISCO
In the preceding command, the section auth sha CISCO specified that messages are authenticated using SHA with a key of CISCO. It does not need to the match the section priv des56 CISCO, which indicates that encryption (priv) will be provided using DES56 with a key of CISCO.
The presence of the keyword auth in the command creating the RESTRICTED user is not causing the issue. This line indicates that that messages are authenticated using SHA with a key of CISCO.
Objective:
Infrastructure Services
Sub-Objective:
Configure and verify SNMP