CCSK Module 3 Unit 2 Answers – Governance Knowledge Check Quiz
CCSK Module 3 Unit 2 Answers – Governance Knowledge Check Quiz Full 100% 2023 2024
This is CCSK Module 3 Unit 2 Answers – Governance Knowledge Check Quiz. Our expert team has verified questions and answers with clear explanations to get a full score of 100%. You can review all these questions before taking the exam.
-
Select the governance tool that is most affected by the transition to cloud computing:
- Mission statement
- Compliance reporting
- Board of Directors reporting
- Chart of accounts
-
Answers Explanation & Hint:
Compliance reporting is the governance tool that is most affected by the transition to cloud computing. As organizations move their operations and data to the cloud, they often need to adapt their compliance reporting processes to ensure that they continue to meet regulatory and industry standards.
The transition to cloud computing introduces new challenges and considerations for compliance reporting, including:
- Data Security and Privacy: Cloud computing involves storing and processing data on third-party servers. Organizations must ensure that the cloud service provider (CSP) adheres to the necessary security and privacy requirements to protect sensitive information.
- Data Residency and Jurisdiction: Cloud data may be stored in data centers located in different countries or regions. This can complicate compliance with data residency and jurisdictional regulations that dictate where certain types of data can be stored and processed.
- Auditing and Transparency: Traditional on-premises systems might have been audited differently than cloud-based systems. Cloud services may require different methods of tracking and reporting access to data and system activities to maintain transparency and accountability.
- Service Level Agreements (SLAs): Compliance reporting might need to account for the terms and conditions outlined in cloud service level agreements, which detail the uptime, availability, and performance of the cloud services being used.
- Access Control and Identity Management: Cloud environments often rely on different access control mechanisms and identity management solutions. Ensuring that access is appropriately restricted to authorized personnel becomes crucial for compliance.
- Vendor Management: Organizations need to perform due diligence on their cloud service providers to ensure they comply with relevant standards and regulations. This involves assessing the CSP’s security practices, certifications, and compliance efforts.
- Data Handling and Retention: Cloud computing can change how data is handled, archived, and retained. Compliance reporting must reflect these changes and ensure that data is managed in accordance with applicable regulations.
- Data Backup and Recovery: Cloud services may offer various backup and recovery mechanisms. Compliance reporting needs to account for these mechanisms and verify that data can be restored in accordance with regulatory requirements.
All these considerations make compliance reporting a governance tool that is significantly impacted by the transition to cloud computing. Organizations need to carefully assess their compliance needs, adapt their reporting processes, and work closely with their cloud service providers to ensure that they continue to meet all relevant regulations and standards.
-
In terms of cloud computing and security… what is the primary governance role of a contract?
- To define the data custodian
- Cost management
- Defines how you extend internal controls to the cloud provider
- Regulatory requirements
-
Answers Explanation & Hint:
In terms of cloud computing and security, the primary governance role of a contract is to define how you extend internal controls to the cloud provider.
When an organization decides to use cloud services, they enter into a contractual agreement with the cloud service provider (CSP). This contract is a critical governance tool for ensuring the security of data and systems in the cloud environment. One of the key aspects of this contract is to outline how the organization’s internal controls and security requirements will be extended and enforced within the cloud environment. This includes:
- Security Responsibilities: The contract should clearly define the roles and responsibilities of both the organization and the cloud provider regarding security measures and controls. It should specify who is responsible for what aspects of security, such as data protection, access controls, encryption, and vulnerability management.
- Compliance with Regulations: The contract should ensure that the cloud provider adheres to relevant regulatory requirements that the organization must comply with. This includes specifying how data will be handled to meet data protection regulations, industry standards, and any other applicable laws.
- Data Protection and Privacy: The contract should outline how the organization’s data will be protected within the cloud environment. This includes details about data encryption, access controls, data segregation, and incident response procedures.
- Auditing and Monitoring: The contract should establish the organization’s right to audit and monitor the cloud provider’s infrastructure and services to ensure that security controls are being implemented effectively. It should detail how and when audits will be conducted.
- Incident Response and Reporting: The contract should outline the procedures for handling security incidents, breaches, and data breaches. It should specify how the cloud provider will report incidents to the organization and the actions that will be taken to mitigate and address them.
- Termination and Data Retrieval: The contract should include provisions for data retrieval and transition in case the organization decides to terminate the services or switch to a different provider. This ensures that data is securely transferred back to the organization and that no data is left behind.
By defining how internal controls are extended to the cloud provider, the contract plays a crucial role in maintaining a secure and compliant cloud computing environment. It establishes the terms and expectations for security measures, risk management, and data protection, providing a framework for both parties to uphold their respective responsibilities and obligations.
-
Does the shared responsibilities model define the contract or the contract define the shared responsibilities model?
- The contract defines the shared responsibilities model
- The shared responsibilities model defines the contract
-
Answers Explanation & Hint:
The correct statement is:
The contract defines the shared responsibilities model.
The contract between a cloud service provider (CSP) and a customer outlines the terms, conditions, and expectations for the services being provided. Within this contract, the shared responsibilities model is defined. This model clarifies the respective roles and responsibilities of both the CSP and the customer when it comes to various aspects of security, compliance, data management, and other operational considerations in the cloud environment. The shared responsibilities model helps set expectations and ensure that both parties understand their roles in maintaining a secure and compliant cloud deployment.
-
Select the layer where you evaluate your providers in the diagram:
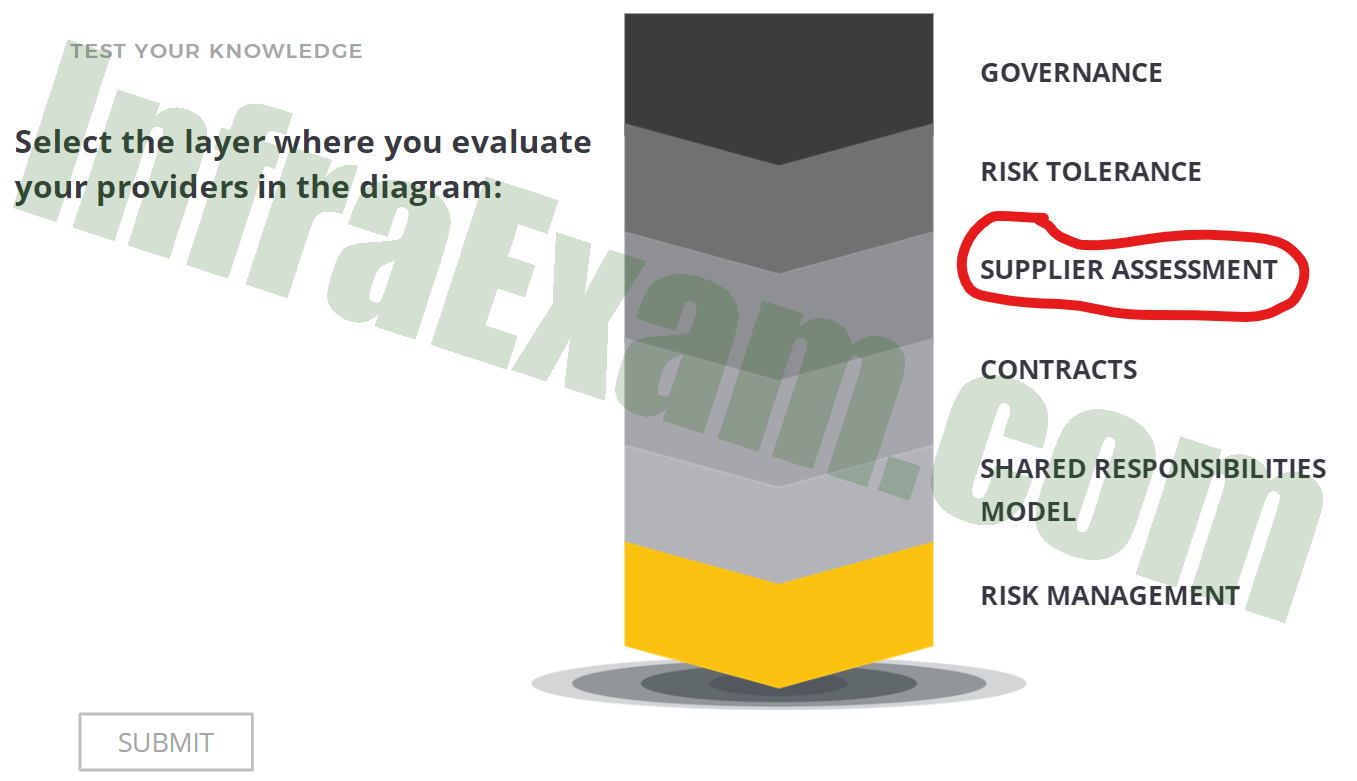
CCSK Module 3 Unit 2 Answers – Governance Knowledge Check Quiz 01 Answers Explanation & Hint:
You evaluate your providers in the “Supplier Assessment” layer in the diagram.
The “Supplier Assessment” layer involves evaluating potential or existing suppliers, such as cloud service providers, to ensure they meet your organization’s requirements, standards, and expectations. This evaluation process includes assessing factors such as security practices, compliance with regulations, performance, reliability, and more. This layer helps organizations make informed decisions about which providers to engage with and how to manage the risks associated with third-party partnerships.