CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 04
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 04
-
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
- Application whitelisting
- NX/XN bit
- ASLR
- TrustZone
- SCP
-
A software development team has spent the last 18 months developing a new web-based front-end that will allow clients to check the status of their orders as they proceed through manufacturing. The marketing team schedules a launch party to present the new application to the client base in two weeks. Before the launch, the security team discovers numerous flaws that may introduce dangerous vulnerabilities, allowing direct access to a database used by manufacturing. The development team did not plan to remediate these vulnerabilities during development. Which of the following SDLC best practices should the development team have followed?
- Implementing regression testing
- Completing user acceptance testing
- Verifying system design documentation
- Using a SRTM
-
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing using corporate-owned resources be monitored. Which of the following would allow the organization to meet its requirement? (Choose two.)
- Exempt mobile devices from the requirement, as this will lead to privacy violations
- Configure the devices to use an always-on IPSec VPN
- Configure all management traffic to be tunneled into the enterprise via TLS
- Implement a VDI solution and deploy supporting client apps to devices
- Restrict application permissions to establish only HTTPS connections outside of the enterprise boundary
-
After multiple service interruptions caused by an older datacenter design, a company decided to migrate away from its datacenter. The company has successfully completed the migration of all datacenter servers and services to a cloud provider. The migration project includes the following phases:
– Selection of a cloud provider
– Architectural design
– Microservice segmentation
– Virtual private cloud
– Geographic service redundancy
– Service migrationThe Chief Information Security Officer (CISO) is still concerned with the availability requirements of critical company applications. Which of the following should the company implement NEXT?
- Multicloud solution
- Single-tenancy private cloud
- Hybrid cloud solution
- Cloud access security broker
-
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The assessor has been handed a package of definitions provided in XML format, and many of the files have two common tags within them: “<object object_ref=… />” and “<state state_ref=… />”. Which of the following tools BEST supports the use of these definitions?
- HTTP interceptor
- Static code analyzer
- SCAP scanner
- XML fuzzer
-
Legal authorities notify a company that its network has been compromised for the second time in two years. The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks. Which of the following would have allowed the security team to use historical information to protect against the second attack?
- Key risk indicators
- Lessons learned
- Recovery point objectives
- Tabletop exercise
-
A web developer has implemented HTML5 optimizations into a legacy web application. One of the modifications the web developer made was the following client side optimization:
localStorage.setItem(“session-cookie”, document.cookie);
Which of the following should the security engineer recommend?
- SessionStorage should be used so authorized cookies expire after the session ends
- Cookies should be marked as “secure” and “HttpOnly”
- Cookies should be scoped to a relevant domain/path
- Client-side cookies should be replaced by server-side mechanisms
-
A hospital’s security team recently determined its network was breached and patient data was accessed by an external entity. The Chief Information Security Officer (CISO) of the hospital approaches the executive management team with this information, reports the vulnerability that led to the breach has already been remediated, and explains the team is continuing to follow the appropriate incident response plan. The executive team is concerned about the hospital’s brand reputation and asks the CISO when the incident should be disclosed to the affected patients. Which of the following is the MOST appropriate response?
- When it is mandated by their legal and regulatory requirements
- As soon as possible in the interest of the patients
- As soon as the public relations department is ready to be interviewed
- When all steps related to the incident response plan are completed
- Upon the approval of the Chief Executive Officer (CEO) to release information to the public
-
A deployment manager is working with a software development group to assess the security of a new version of the organization’s internally developed ERP tool. The organization prefers to not perform assessment activities following deployment, instead focusing on assessing security throughout the life cycle. Which of the following methods would BEST assess the security of the product?
- Static code analysis in the IDE environment
- Penetration testing of the UAT environment
- Vulnerability scanning of the production environment
- Penetration testing of the production environment
- Peer review prior to unit testing
-
During a security event investigation, a junior analyst fails to create an image of a server’s hard drive before removing the drive and sending it to the forensics analyst. Later, the evidence from the analysis is not usable in the prosecution of the attackers due to the uncertainty of tampering. Which of the following should the junior analyst have followed?
- Continuity of operations
- Chain of custody
- Order of volatility
- Data recovery
-
A team is at the beginning stages of designing a new enterprise-wide application. The new application will have a large database and require a capital investment in hardware. The Chief Information Officer (СIO) has directed the team to save money and reduce the reliance on the datacenter, and the vendor must specialize in hosting large databases in the cloud. Which of the following cloud-hosting options would BEST meet these needs?
- Multi-tenancy SaaS
- Hybrid IaaS
- Single-tenancy PaaS
- Community IaaS
-
A company wants to extend its help desk availability beyond business hours. The Chief Information Officer (CIO) decides to augment the help desk with a third-party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance. The security administrator implements the following firewall change:
CAS-003 Part 04 Q12 020 The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
- LDAP
- WAYF
- OpenID
- RADIUS
- SAML
-
An architect was recently hired by a power utility to increase the security posture of the company’s power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
- Isolate the systems on their own network
- Install a firewall and IDS between systems and the LAN
- Employ own stratum-0 and stratum-1 NTP servers
- Upgrade the software on critical systems
- Configure the systems to use government-hosted NTP servers
-
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office:
– Store taxation-related documents for five years
– Store customer addresses in an encrypted format
– Destroy customer information after one year
– Keep data only in the customer’s home countryWhich of the following should the CISO implement to BEST meet these requirements? (Choose three.)
- Capacity planning policy
- Data retention policy
- Data classification standard
- Legal compliance policy
- Data sovereignty policy
- Backup policy
- Acceptable use policy
- Encryption standard
-
A company contracts a security engineer to perform a penetration test of its client-facing web portal. Which of the following activities would be MOST appropriate?
- Use a protocol analyzer against the site to see if data input can be replayed from the browser
- Scan the website through an interception proxy and identify areas for the code injection
- Scan the site with a port scanner to identify vulnerable services running on the web server
- Use network enumeration tools to identify if the server is running behind a load balancer
-
A large enterprise with thousands of users is experiencing a relatively high frequency of malicious activity from the insider threats. Much of the activity appears to involve internal reconnaissance that results in targeted attacks against privileged users and network file shares. Given this scenario, which of the following would MOST likely prevent or deter these attacks? (Choose two.)
- Conduct role-based training for privileged users that highlights common threats against them and covers best practices to thwart attacks
- Increase the frequency at which host operating systems are scanned for vulnerabilities, and decrease the amount of time permitted between vulnerability identification and the application of corresponding patches
- Enforce command shell restrictions via group policies for all workstations by default to limit which native operating system tools are available for use
- Modify the existing rules of behavior to include an explicit statement prohibiting users from enumerating user and file directories using available tools and/or accessing visible resources that do not directly pertain to their job functions
- For all workstations, implement full-disk encryption and configure UEFI instances to require complex passwords for authentication
- Implement application blacklisting enforced by the operating systems of all machines in the enterprise
-
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
- Data aggregation
- Data sovereignty
- Data isolation
- Data volume
- Data analytics
-
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, “criticalValue” indicates if an emergency is underway:

CAS-003 Part 04 Q18 021 Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
- Rewrite the software to implement fine-grained, conditions-based testing
- Add additional exception handling logic to the main program to prevent doors from being opened
- Apply for a life-safety-based risk exception allowing secure doors to fail open
- Rewrite the software’s exception handling routine to fail in a secure state
-
SIMULATION
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.4.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250Instructions:
To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
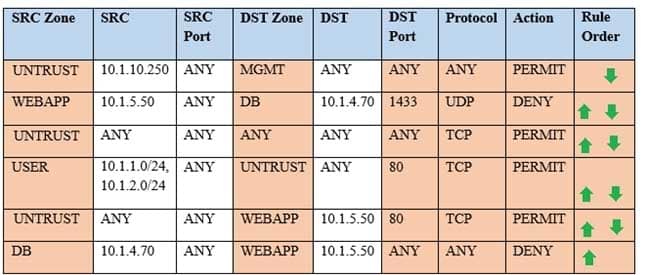
CAS-003 Part 04 Q19 022 Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.- For correct answers: see the explanation below
Explanation:
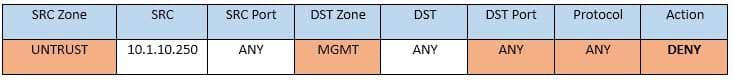
Task 1: A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
In Rule no. 1 edit the Action to Deny to block internet access from the management platform.
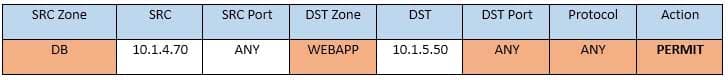
CAS-003 Part 04 Q19 023 Task 2: The firewall must be configured so that the SQL server can only receive requests from the web server.
In Rule no. 6 from top, edit the Action to be Permit.
CAS-003 Part 04 Q19 024 Task 3: The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
In rule no. 5 from top, change the DST port to Any from 80 to allow all unencrypted traffic.
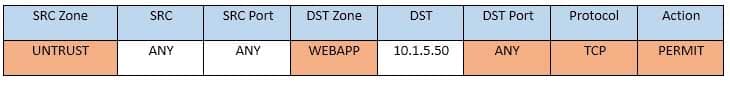
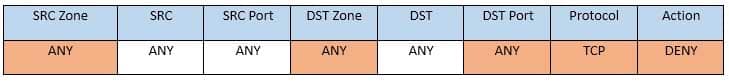
CAS-003 Part 04 Q19 025 Task 4: Ensure the final rule is an explicit deny
Enter this at the bottom of the access list i.e. the line at the bottom of the rule:
CAS-003 Part 04 Q19 026 Task 5: Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
In Rule number 4 from top, edit the DST port to 443 from 80
-
A software development manager is running a project using agile development methods. The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project.
Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?
- Conduct a penetration test on each function as it is developed
- Develop a set of basic checks for common coding errors
- Adopt a waterfall method of software development
- Implement unit tests that incorporate static code analyzers
