CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 05
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 05
-
SIMULATION
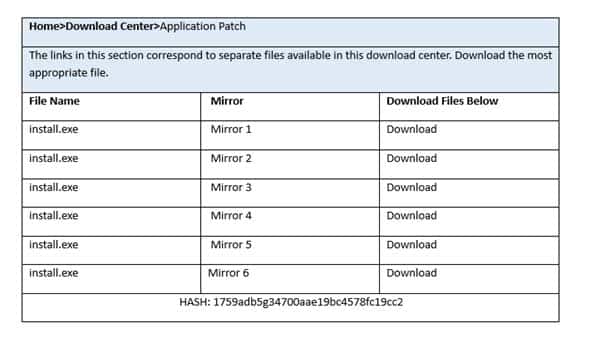
CAS-003 Part 05 Q01 028 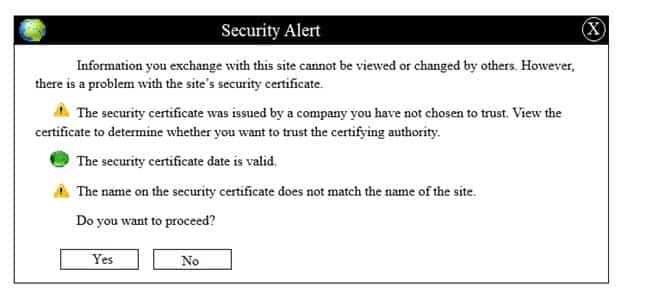
CAS-003 Part 05 Q01 029 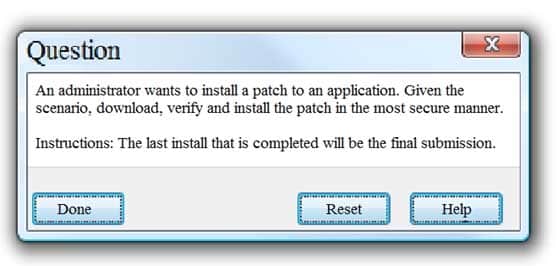
CAS-003 Part 05 Q01 030 - For correct answers: see the explanation below
Step 1: Verify that the certificate is valid or not. In case of any warning message, cancel the download.
Step 2: If certificate issue is not there then, download the file in your system.
Step 3: Calculate the hash value of the downloaded file.
Step 4: Match the hash value of the downloaded file with the one which you selected on the website.
Step 5: Install the file if the hash value matches. -
Given the code snippet below:

CAS-003 Part 05 Q02 031 Which of the following vulnerability types in the MOST concerning?
- Only short usernames are supported, which could result in brute forcing of credentials.
- Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
- Hardcoded usernames with different code paths taken depend on which user is entered.
- Format string vulnerability is present for admin users but not for standard users.
-
To meet an SLA, which of the following document should be drafted, defining the company’s internal interdependent unit responsibilities and delivery timelines.
- BPA
- OLA
- MSA
- MOU
Explanation:
OLA is an agreement between the internal support groups of an institution that supports SLA. According to the Operational Level Agreement, each internal support group has certain responsibilities to the other group. The OLA clearly depicts the performance and relationship of the internal service groups. The main objective of OLA is to ensure that all the support groups provide the intended Service Level Agreement.
-
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company’s products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:

CAS-003 Part 05 Q04 032 Which of the following is the MOST likely type of activity occurring?
- SQL injection
- XSS scanning
- Fuzzing
- Brute forcing
-
An organization has established the following controls matrix:
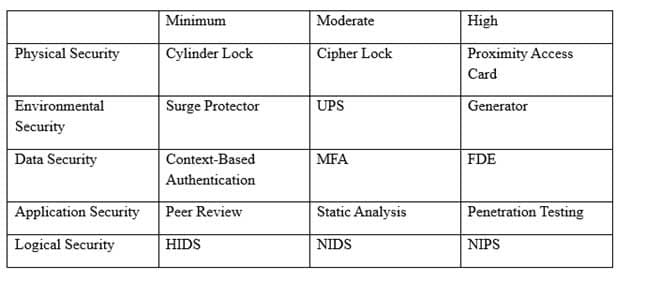
CAS-003 Part 05 Q05 033 The following control sets have been defined by the organization and are applied in aggregate fashion:
– Systems containing PII are protected with the minimum control set.
– Systems containing medical data are protected at the moderate level.
– Systems containing cardholder data are protected at the high level.The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
- Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
- Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
- Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
- Intrusion detection capabilities, network-based IPS, generator, and context-based authentication.
-
A company’s existing forward proxies support software-based TLS decryption, but are currently at 60% load just dealing with AV scanning and content analysis for HTTP traffic. More than 70% outbound web traffic is currently encrypted. The switching and routing network infrastructure precludes adding capacity, preventing the installation of a dedicated TLS decryption system. The network firewall infrastructure is currently at 30% load and has software decryption modules that can be activated by purchasing additional license keys. An existing project is rolling out agent updates to end-user desktops as part of an endpoint security refresh.
Which of the following is the BEST way to address these issues and mitigate risks to the organization?
- Purchase the SSL, decryption license for the firewalls and route traffic back to the proxies for end-user categorization and malware analysis.
- Roll out application whitelisting to end-user desktops and decommission the existing proxies, freeing up network ports.
- Use an EDP solution to address the malware issue and accept the diminishing role of the proxy for URL categorization in the short team.
- Accept the current risk and seek possible funding approval in the next budget cycle to replace the existing proxies with ones with more capacity.
-
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded.
Which of the following should be used to identify weak processes and other vulnerabilities?
- Gap analysis
- Benchmarks and baseline results
- Risk assessment
- Lessons learned report
-
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix.
Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Choose two.)
- Antivirus
- HIPS
- Application whitelisting
- Patch management
- Group policy implementation
- Firmware updates
-
A network engineer is attempting to design-in resiliency characteristics for an enterprise network’s VPN services.
If the engineer wants to help ensure some resilience against zero-day vulnerabilities exploited against the VPN implementation, which of the following decisions would BEST support this objective?
- Implement a reverse proxy for VPN traffic that is defended and monitored by the organization’s SOC with near-real-time alerting to administrators.
- Subscribe to a managed service provider capable of supporting the mitigation of advanced DDoS attacks on the enterprise’s pool of VPN concentrators.
- Distribute the VPN concentrators across multiple systems at different physical sites to ensure some backup services are available in the event of primary site loss.
- Employ a second VPN layer concurrently where the other layer’s cryptographic implementation is sourced from a different vendor.
-
An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data:

CAS-003 Part 05 Q10 034 Which of the following tools was used to gather this information from the hashed values in the file?
- Vulnerability scanner
- Fuzzer
- MD5 generator
- Password cracker
- Protocol analyzer
-
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that were developed internally and have been used several years to secure the organization’s systems. The CISO knows improvements can be made to the guides.
Which of the following would be the BEST source of reference during the revision process?
- CVE database
- Internal security assessment reports
- Industry-accepted standards
- External vulnerability scan reports
- Vendor-specific implementation guides
-
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization’s file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system.
Which of the following is MOST likely to be reviewed during the assessment? (Choose two.)
- Access control list
- Security requirements traceability matrix
- Data owner matrix
- Roles matrix
- Data design document
- Data access policies
-
Security policies that are in place at an organization prohibit USB drives from being utilized across the entire enterprise, with adequate technical controls in place to block them. As a way to still be able to work from various locations on different computing resources, several sales staff members have signed up for a web-based storage solution without the consent of the IT department. However, the operations department is required to use the same service to transmit certain business partner documents.
Which of the following would BEST allow the IT department to monitor and control this behavior?
- Enabling AAA
- Deploying a CASB
- Configuring an NGFW
- Installing a WAF
- Utilizing a vTPM
-
Legal counsel has notified the information security manager of a legal matter that will require the preservation of electronic records for 2000 sales force employees. Source records will be email, PC, network shares, and applications.
After all restrictions have been lifted, which of the following should the information manager review?
- Data retention policy
- Legal hold
- Chain of custody
- Scope statement
-
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
CAS-003 Part 05 Q15 035 
CAS-003 Part 05 Q15 036 - For correct answers: see the explanation below
Explanation:
Step 1:
The ps command is the “process status” command. By using ps -A, you can list all currently running services, including their Process Identifiers (PID).You can disable services using the kill command, such as, for example, kill -9 1125, which would stop whichever process is PID 1125.
Step 2:
The chkconfig –list command displays a list of system services and whether they are started (on) or stopped (off) in runlevels 0-6.Step 3:
Importantly, chkconfig –list will allow you to see what services are running at level 3 (which means they will re-enable at restart) and you can use chkconfig –level 3 off to turn off the services you just killed. Once you do this, the sim is done and you can move on. -
The legal department has required that all traffic to and from a company’s cloud-based word processing and email system is logged. To meet this requirement, the Chief Information Security Officer (CISO) has implemented a next-generation firewall to perform inspection of the secure traffic and has decided to use a cloud-based log aggregation solution for all traffic that is logged.
Which of the following presents a long-term risk to user privacy in this scenario?
- Confidential or sensitive documents are inspected by the firewall before being logged.
- Latency when viewing videos and other online content may increase.
- Reports generated from the firewall will take longer to produce due to more information from inspected traffic.
- Stored logs may contain non-encrypted usernames and passwords for personal websites.
-
A consultant is hired to perform a passive vulnerability assessment of a company to determine what information might be collected about the company and its employees. The assessment will be considered successful if the consultant can discover the name of one of the IT administrators.
Which of the following is MOST likely to produce the needed information?
- Whois
- DNS enumeration
- Vulnerability scanner
- Fingerprinting
-
A breach was caused by an insider threat in which customer PII was compromised. Following the breach, a lead security analyst is asked to determine which vulnerabilities the attacker used to access company resources.
Which of the following should the analyst use to remediate the vulnerabilities?
- Protocol analyzer
- Root cause analysis
- Behavioral analytics
- Data leak prevention
-
A security analyst has requested network engineers integrate sFlow into the SOC’s overall monitoring picture. For this to be a useful addition to the monitoring capabilities, which of the following must be considered by the engineering team?
- Effective deployment of network taps
- Overall bandwidth available at Internet PoP
- Optimal placement of log aggregators
- Availability of application layer visualizers
-
Ann, a member of the finance department at a large corporation, has submitted a suspicious email she received to the information security team. The team was not expecting an email from Ann, and it contains a PDF file inside a ZIP compressed archive. The information security team is not sure which files were opened. A security team member uses an air-gapped PC to open the ZIP and PDF, and it appears to be a social engineering attempt to deliver an exploit.
Which of the following would provide greater insight on the potential impact of this attempted attack?
- Run an antivirus scan on the finance PC.
- Use a protocol analyzer on the air-gapped PC.
- Perform reverse engineering on the document.
- Analyze network logs for unusual traffic.
- Run a baseline analyzer against the user’s computer.