CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 07
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 07
-
An organization is considering the use of a thin client architecture as it moves to a cloud-hosted environment. A security analyst is asked to provide thoughts on the security advantages of using thin clients and virtual workstations.
Which of the following are security advantages of the use of this combination of thin clients and virtual workstations?
- Malicious insiders will not have the opportunity to tamper with data at rest and affect the integrity of the system.
- Thin client workstations require much less security because they lack storage and peripherals that can be easily compromised, and the virtual workstations are protected in the cloud where security is outsourced.
- All thin clients use TPM for core protection, and virtual workstations use vTPM for core protection with both equally ensuring a greater security advantage for a cloud-hosted environment.
- Malicious users will have reduced opportunities for data extractions from their physical thin client workstations, this reducing the effectiveness of local attacks.
-
A security analyst is attempting to break into a client’s secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use.
After network enumeration, the analyst’s NEXT step is to perform:
- a gray-box penetration test
- a risk analysis
- a vulnerability assessment
- an external security audit
- a red team exercise
-
A security architect is determining the best solution for a new project. The project is developing a new intranet with advanced authentication capabilities, SSO for users, and automated provisioning to streamline Day 1 access to systems. The security architect has identified the following requirements:
1. Information should be sourced from the trusted master data source.
2. There must be future requirements for identity proofing of devices and users.
3. A generic identity connector that can be reused must be developed.
4. The current project scope is for internally hosted applications only.Which of the following solution building blocks should the security architect use to BEST meet the requirements?
- LDAP, multifactor authentication, OAuth, XACML
- AD, certificate-based authentication, Kerberos, SPML
- SAML, context-aware authentication, OAuth, WAYF
- NAC, radius, 802.1x, centralized active directory
-
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?
- Lack of adequate in-house testing skills.
- Requirements for geographically based assessments
- Cost reduction measures
- Regulatory insistence on independent reviews.
-
Engineers at a company believe a certain type of data should be protected from competitors, but the data owner insists the information is not sensitive. An information security engineer is implementing controls to secure the corporate SAN. The controls require dividing data into four groups: non-sensitive, sensitive but accessible, sensitive but export-controlled, and extremely sensitive.
Which of the following actions should the engineer take regarding the data?
- Label the data as extremely sensitive.
- Label the data as sensitive but accessible.
- Label the data as non-sensitive.
- Label the data as sensitive but export-controlled.
-
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review:

CAS-003 Part 07 Q06 042 Which of the following tools is the engineer utilizing to perform this assessment?
- Vulnerability scanner
- SCAP scanner
- Port scanner
- Interception proxy
-
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues.
Which of the following is the MOST important information to reference in the letter?
- After-action reports from prior incidents.
- Social engineering techniques
- Company policies and employee NDAs
- Data classification processes
-
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization’s systems to the greatest extent possible.
Which of the following principles is being demonstrated?
- Administrator accountability
- PII security
- Record transparency
- Data minimization
-
A newly hired security analyst has joined an established SOC team. Not long after going through corporate orientation, a new attack method on web-based applications was publicly revealed. The security analyst immediately brings this new information to the team lead, but the team lead is not concerned about it.
Which of the following is the MOST likely reason for the team lead’s position?
- The organization has accepted the risks associated with web-based threats.
- The attack type does not meet the organization’s threat model.
- Web-based applications are on isolated network segments.
- Corporate policy states that NIPS signatures must be updated every hour.
-
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

CAS-003 Part 07 Q10 043 Which of the following should be included in the auditor’s report based on the above findings?
- The hard disk contains bad sectors
- The disk has been degaussed.
- The data represents part of the disk BIOS.
- Sensitive data might still be present on the hard drives.
-
The Chief Information Officer (CISO) is concerned that certain systems administrators will privileged access may be reading other users’ emails. Review of a tool’s output shows the administrators have used web mail to log into other users’ inboxes.
Which of the following tools would show this type of output?
- Log analysis tool
- Password cracker
- Command-line tool
- File integrity monitoring tool
-
A security analyst is troubleshooting a scenario in which an operator should only be allowed to reboot remote hosts but not perform other activities. The analyst inspects the following portions of different configuration files:
Configuration file 1: Operator ALL=/sbin/reboot Configuration file 2: Command=”/sbin/shutdown now”, no-x11-forwarding, no-pty, ssh-dss Configuration file 3: Operator:x:1000:1000::/home/operator:/bin/bash
Which of the following explains why an intended operator cannot perform the intended action?
- The sudoers file is locked down to an incorrect command
- SSH command shell restrictions are misconfigured
- The passwd file is misconfigured
- The SSH command is not allowing a pty session
-
The director of sales asked the development team for some small changes to increase the usability of an application used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now show numerous flaws that were not present in the previous versions of the code.
Which of the following is an SDLC best practice that should have been followed?
- Versioning
- Regression testing
- Continuous integration
- Integration testing
-
An organization is engaged in international business operations and is required to comply with various legal frameworks. In addition to changes in legal frameworks, which of the following is a primary purpose of a compliance management program?
- Following new requirements that result from contractual obligations
- Answering requests from auditors that relate to e-discovery
- Responding to changes in regulatory requirements
- Developing organizational policies that relate to hiring and termination procedures
-
Company.org has requested a black-box security assessment be performed on key cyber terrain. One area of concern is the company’s SMTP services. The security assessor wants to run reconnaissance before taking any additional action and wishes to determine which SMTP server is Internet-facing.
Which of the following commands should the assessor use to determine this information?
-
dnsrecon –d company.org –t SOA -
dig company.org mx
-
nc –v company.org
-
whois company.org
-
-
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software.
Which of the following would BEST ensure the software and instruments are working as designed?
- System design documentation
- User acceptance testing
- Peer review
- Static code analysis testing
- Change control documentation
-
A company has gone through a round of phishing attacks. More than 200 users have had their workstation infected because they clicked on a link in an email. An incident analysis has determined an executable ran and compromised the administrator account on each workstation. Management is demanding the information security team prevent this from happening again.
Which of the following would BEST prevent this from happening again?
- Antivirus
- Patch management
- Log monitoring
- Application whitelisting
- Awareness training
-
An internal staff member logs into an ERP platform and clicks on a record. The browser URL changes to:
URL: http://192.168.0.100/ERP/accountId=5&action=SELECT
Which of the following is the MOST likely vulnerability in this ERP platform?
- Brute forcing of account credentials
- Plain-text credentials transmitted over the Internet
- Insecure direct object reference
- SQL injection of ERP back end
-
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
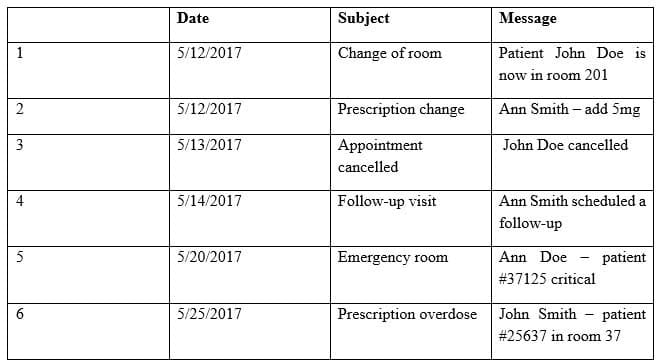
CAS-003 Part 07 Q19 044 Which of the following represents the BEST solution for preventing future fines?
- Implement a secure text-messaging application for mobile devices and workstations.
- Write a policy requiring this information to be given over the phone only.
- Provide a courier service to deliver sealed documents containing public health informatics.
- Implement FTP services between clinics to transmit text documents with the information.
- Implement a system that will tokenize patient numbers.
-
An information security manager is concerned that connectivity used to configure and troubleshoot critical network devices could be attacked. The manager has tasked a network security engineer with meeting the following requirements:
– Encrypt all traffic between the network engineer and critical devices.
– Segregate the different networking planes as much as possible.
– Do not let access ports impact configuration tasks.Which of the following would be the BEST recommendation for the network security engineer to present?
- Deploy control plane protections.
- Use SSH over out-of-band management.
- Force only TACACS to be allowed.
- Require the use of certificates for AAA.