CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 08
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 08
-
A penetration tester noticed special characters in a database table. The penetration tester configured the browser to use an HTTP interceptor to verify that the front-end user registration web form accepts invalid input in the user’s age field. The developer was notified and asked to fix the issue.
Which of the following is the MOST secure solution for the developer to implement?
- IF $AGE == “!@#$%^&*()_+<>?”:{}[]” THEN ERROR
- IF $AGE == [1234567890] {1,3} THEN CONTINUE
- IF $AGE != “a-bA-Z!@#$%^&*()_+<>?”:{}[]” THEN CONTINUE
- IF $AGE == [1-0] {0,2} THEN CONTINUE
-
A managed service provider is designing a log aggregation service for customers who no longer want to manage an internal SIEM infrastructure. The provider expects that customers will send all types of logs to them, and that log files could contain very sensitive entries. Customers have indicated they want on-premises and cloud-based infrastructure logs to be stored in this new service. An engineer, who is designing the new service, is deciding how to segment customers.
Which of the following is the BEST statement for the engineer to take into consideration?
- Single-tenancy is often more expensive and has less efficient resource utilization. Multitenancy may increase the risk of cross-customer exposure in the event of service vulnerabilities.
- The managed service provider should outsource security of the platform to an existing cloud company. This will allow the new log service to be launched faster and with well-tested security controls.
- Due to the likelihood of large log volumes, the service provider should use a multitenancy model for the data storage tier, enable data deduplication for storage cost efficiencies, and encrypt data at rest.
- The most secure design approach would be to give customers on-premises appliances, install agents on endpoints, and then remotely manage the service via a VPN.
-
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company’s web servers can be obtained publicly and is not proprietary in any way. The next day the company’s website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website.
Which of the following is the FIRST action the company should take?
- Refer to and follow procedures from the company’s incident response plan.
- Call a press conference to explain that the company has been hacked.
- Establish chain of custody for all systems to which the systems administrator has access.
- Conduct a detailed forensic analysis of the compromised system.
- Inform the communications and marketing department of the attack details.
-
Click on the exhibit buttons to view the four messages.

CAS-003 Part 08 Q04 045 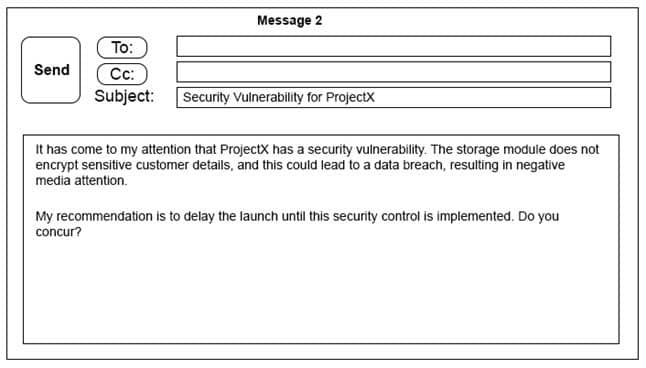
CAS-003 Part 08 Q04 046 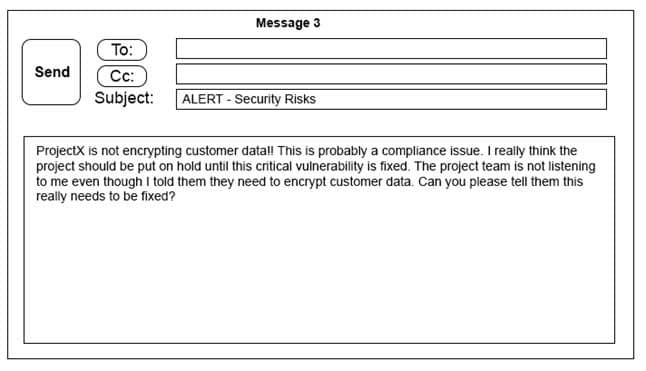
CAS-003 Part 08 Q04 047 
CAS-003 Part 08 Q04 048 A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?
- Message 1
- Message 2
- Message 3
- Message 4
-
As a result of an acquisition, a new development team is being integrated into the company. The development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize SaaS. To have the team up and running effectively, a separate Internet connection has been procured.
A stand up has identified the following additional requirements:
1. Reuse of the existing network infrastructure
2. Acceptable use policies to be enforced
3. Protection of sensitive files
4. Access to the corporate applicationsWhich of the following solution components should be deployed to BEST meet the requirements? (Choose three.)
- IPSec VPN
- HIDS
- Wireless controller
- Rights management
- SSL VPN
- NAC
- WAF
- Load balancer
-
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable.
Which of the following solutions BEST meets all of the architect’s objectives?
- An internal key infrastructure that allows users to digitally sign transaction logs
- An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
- A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
- An open distributed transaction ledger that requires proof of work to append entries.
-
A user asks a security practitioner for recommendations on securing a home network. The user recently purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some of the IoT devices are wearables, and other are installed in the user’s automobiles. The current home network is configured as a single flat network behind an ISP-supplied router. The router has a single IP address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user’s privacy concerns and provide the BEST level of security for the home network?
- Ensure all IoT devices are configured in a geofencing mode so the devices do not work when removed from the home network. Disable the home assistant unless actively using it, and segment the network so each IoT device has its own segment.
- Install a firewall capable of cryptographically separating network traffic, require strong authentication to access all IoT devices, and restrict network access for the home assistant based on time-of-day restrictions.
- Segment the home network to separate network traffic from users and the IoT devices, ensure security settings on the home assistant support no or limited recording capability, and install firewall rules on the router to restrict traffic to the home assistant as much as possible.
- Change all default passwords on the IoT devices, disable Internet access for the IoT devices and the home assistant, obtain routable IP addresses for all devices, and implement IPv6 and IPSec protections on all network traffic.
-
An enterprise with global sites processes and exchanges highly sensitive information that is protected under several countries’ arms trafficking laws. There is new information that malicious nation-state-sponsored activities are targeting the use of encryption between the geographically disparate sites. The organization currently employs ECDSA and ECDH with P-384, SHA-384, and AES-256-GCM on VPNs between sites.
Which of the following techniques would MOST likely improve the resilience of the enterprise to attack on cryptographic implementation?
- Add a second-layer VPN from a different vendor between sites.
- Upgrade the cipher suite to use an authenticated AES mode of operation.
- Use a stronger elliptic curve cryptography algorithm.
- Implement an IDS with sensors inside (clear-text) and outside (cipher-text) of each tunnel between sites.
- Ensure cryptography modules are kept up to date from vendor supplying them.
-
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
– End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families.
– Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
– A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
– The use of satellite communication to include multiple proxy servers to scramble the source IP addressWhich of the following is of MOST concern in this scenario?
- Malicious actors intercepting inbound and outbound communication to determine the scope of the mission
- Family members posting geotagged images on social media that were received via email from soldiers
- The effect of communication latency that may negatively impact real-time communication with mission control
- The use of centrally managed military network and computers by soldiers when communicating with external parties
-
Given the following code snippet:

CAS-003 Part 08 Q10 049 Of which of the following is this snippet an example?
- Data execution prevention
- Buffer overflow
- Failure to use standard libraries
- Improper filed usage
- Input validation
-
A company has created a policy to allow employees to use their personally owned devices. The Chief Information Security Officer (CISO) is getting reports of company data appearing on unapproved forums and an increase in theft of personal electronic devices.
Which of the following security controls would BEST reduce the risk of exposure?
- Disk encryption on the local drive
- Group policy to enforce failed login lockout
- Multifactor authentication
- Implementation of email digital signatures
-
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees’ devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees’ devices into the network securely?
- Distribute a NAC client and use the client to push the company’s private key to all the new devices.
- Distribute the device connection policy and a unique public/private key pair to each new employee’s device.
- Install a self-signed SSL certificate on the company’s RADIUS server and distribute the certificate’s public key to all new client devices.
- Install an 802.1X supplicant on all new devices and let each device generate a self-signed certificate to use for network access.
-
A forensic analyst suspects that a buffer overflow exists in a kernel module. The analyst executes the following command:

CAS-003 Part 08 Q13 050 However, the analyst is unable to find any evidence of the running shell.
Which of the following of the MOST likely reason the analyst cannot find a process ID for the shell?
- The NX bit is enabled
- The system uses ASLR
- The shell is obfuscated
- The code uses dynamic libraries
-
Ann, a terminated employee, left personal photos on a company-issued laptop and no longer has access to them. Ann emails her previous manager and asks to get her personal photos back.
Which of the following BEST describes how the manager should respond?
- Determine if the data still exists by inspecting to ascertain if the laptop has already been wiped and if the storage team has recent backups.
- Inform Ann that the laptop was for company data only and she should not have stored personal photos on a company asset.
- Report the email because it may have been a spoofed request coming from an attacker who is trying to exfiltrate data from the company laptop.
- Consult with the legal and/or human resources department and check company policies around employment and termination procedures.
-
During the decommissioning phase of a hardware project, a security administrator is tasked with ensuring no sensitive data is released inadvertently. All paper records are scheduled to be shredded in a crosscut shredder, and the waste will be burned. The system drives and removable media have been removed prior to e-cycling the hardware.
Which of the following would ensure no data is recovered from the system drives once they are disposed of?
- Overwriting all HDD blocks with an alternating series of data.
- Physically disabling the HDDs by removing the drive head.
- Demagnetizing the hard drive using a degausser.
- Deleting the UEFI boot loaders from each HDD.
-
A company has decided to lower costs by conducting an internal assessment on specific devices and various internal and external subnets. The assessment will be done during regular office hours, but it must not affect any production servers.
Which of the following would MOST likely be used to complete the assessment? (Choose two.)
- Agent-based vulnerability scan
- Black-box penetration testing
- Configuration review
- Social engineering
- Malware sandboxing
- Tabletop exercise
-
A security engineer is attempting to increase the randomness of numbers used in key generation in a system. The goal of the effort is to strengthen the keys against predictive analysis attacks.
Which of the following is the BEST solution?
- Use an entropy-as-a-service vendor to leverage larger entropy pools.
- Loop multiple pseudo-random number generators in a series to produce larger numbers.
- Increase key length by two orders of magnitude to detect brute forcing.
- Shift key generation algorithms to ECC algorithms.
-
A security engineer is attempting to convey the importance of including job rotation in a company’s standard security policies. Which of the following would be the BEST justification?
- Making employees rotate through jobs ensures succession plans can be implemented and prevents single points of failure.
- Forcing different people to perform the same job minimizes the amount of time malicious actions go undetected by forcing malicious actors to attempt collusion between two or more people.
- Administrators and engineers who perform multiple job functions throughout the day benefit from being cross-trained in new job areas.
- It eliminates the need to share administrative account passwords because employees gain administrative rights as they rotate into a new job area.
-
A company is transitioning to a new VDI environment, and a system engineer is responsible for developing a sustainable security strategy for the VDIs.
Which of the following is the MOST appropriate order of steps to be taken?
- Firmware update, OS patching, HIDS, antivirus, baseline, monitoring agent
- OS patching, baseline, HIDS, antivirus, monitoring agent, firmware update
- Firmware update, OS patching, HIDS, antivirus, monitoring agent, baseline
- Baseline, antivirus, OS patching, monitoring agent, HIDS, firmware update
-
The Chief Information Officer (CIO) has been asked to develop a security dashboard with the relevant metrics. The board of directors will use the dashboard to monitor and track the overall security posture of the organization. The CIO produces a basic report containing both KPI and KRI data in two separate sections for the board to review.
Which of the following BEST meets the needs of the board?
- KRI:
– Compliance with regulations
– Backlog of unresolved security investigations
– Severity of threats and vulnerabilities reported by sensors
– Time to patch critical issues on a monthly basis
KPI:
– Time to resolve open security items
– % of suppliers with approved security control frameworks
– EDR coverage across the fleet
– Threat landscape rating - KRI:
– EDR coverage across the fleet
– Backlog of unresolved security investigations
– Time to patch critical issues on a monthly basis
– Threat landscape rating
KPI:
– Time to resolve open security items
– Compliance with regulations
– % of suppliers with approved security control frameworks
– Severity of threats and vulnerabilities reported by sensors - KRI:
– EDR coverage across the fleet
– % of suppliers with approved security control framework
– Backlog of unresolved security investigations
– Threat landscape rating
KPI:
– Time to resolve open security items
– Compliance with regulations
– Time to patch critical issues on a monthly basis
– Severity of threats and vulnerabilities reported by sensors - KPI:
– Compliance with regulations
– % of suppliers with approved security control frameworks
– Severity of threats and vulnerabilities reported by sensors
– Threat landscape rating
KRI:
– Time to resolve open security items
– Backlog of unresolved security investigations
– EDR coverage across the fleet
– Time to patch critical issues on a monthly basis
- KRI: