CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 09
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 09
-
The Chief Executive Officer (CEO) of a small startup company has an urgent need for a security policy and assessment to address governance, risk management, and compliance. The company has a resource-constrained IT department, but has no information security staff. The CEO has asked for this to be completed in three months.
Which of the following would be the MOST cost-effective solution to meet the company’s needs?
- Select one of the IT personnel to obtain information security training, and then develop all necessary policies and documents in-house.
- Accept all risks associated with information security, and then bring up the issue again at next year’s annual board meeting.
- Release an RFP to consultancy firms, and then select the most appropriate consultant who can fulfill the requirements.
- Hire an experienced, full-time information security team to run the startup company’s information security department.
-
As part of an organization’s compliance program, administrators must complete a hardening checklist and note any potential improvements. The process of noting improvements in the checklist is MOST likely driven by:
- the collection of data as part of the continuous monitoring program.
- adherence to policies associated with incident response.
- the organization’s software development life cycle.
- changes in operating systems or industry trends.
-
A security engineer has been hired to design a device that will enable the exfiltration of data from within a well-defended network perimeter during an authorized test. The device must bypass all firewalls and NIDS in place, as well as allow for the upload of commands from a centralized command and control server . The total cost of the device must be kept to a minimum in case the device is discovered during an assessment.
Which of the following tools should the engineer load onto the device being designed?
- Custom firmware with rotating key generation
- Automatic MITM proxy
- TCP beacon broadcast software
- Reverse shell endpoint listener
-
A security consultant is improving the physical security of a sensitive site and takes pictures of the unbranded building to include in the report. Two weeks later, the security consultant misplaces the phone, which only has one hour of charge left on it. The person who finds the phone removes the MicroSD card in an attempt to discover the owner to return it.
The person extracts the following data from the phone and EXIF data from some files:
DCIM Images folder
Audio books folder
Torrentz
My TAX.xls
Consultancy HR Manual.doc
Camera: SM-G950F
Exposure time: 1/60s
Location: 3500 Lacey Road USAWhich of the following BEST describes the security problem?
- MicroSD in not encrypted and also contains personal data.
- MicroSD contains a mixture of personal and work data.
- MicroSD in not encrypted and contains geotagging information.
- MicroSD contains pirated software and is not encrypted.
-
An engineer needs to provide access to company resources for several offshore contractors. The contractors require:
– Access to a number of applications, including internal websites
– Access to database data and the ability to manipulate it
– The ability to log into Linux and Windows servers remotelyWhich of the following remote access technologies are the BEST choices to provide all of this access securely? (Choose two.)
- VTC
- VRRP
- VLAN
- VDI
- VPN
- Telnet
-
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor’s cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
- SaaS
- PaaS
- IaaS
- Hybrid cloud
- Network virtualization
-
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly. Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems. Which of the following should the project manager use to determine the source of the defined algorithm in use?
- Code repositories
- Security requirements traceability matrix
- Software development lifecycle
- Roles matrix
- Implementation guide
-
An administrator has noticed mobile devices from an adjacent company on the corporate wireless network. Malicious activity is being reported from those devices. To add another layer of security in an enterprise environment, an administrator wants to add contextual authentication to allow users to access enterprise resources only while present in corporate buildings. Which of the following technologies would accomplish this?
- Port security
- Rogue device detection
- Bluetooth
- GPS
-
A network engineer is upgrading the network perimeter and installing a new firewall, IDS, and external edge router. The IDS is reporting elevated UDP traffic, and the internal routers are reporting high utilization. Which of the following is the BEST solution?
- Reconfigure the firewall to block external UDP traffic.
- Establish a security baseline on the IDS.
- Block echo reply traffic at the firewall.
- Modify the edge router to not forward broadcast traffic.
-
An administrator is working with management to develop policies related to the use of the cloud-based resources that contain corporate data. Management plans to require some control over organizational data stored on personal devices, such as tablets. Which of the following controls would BEST support management’s policy?
- MDM
- Sandboxing
- Mobile tokenization
- FDE
- MFA
-
Users have been reporting unusual automated phone calls, including names and phone numbers, that appear to come from devices internal to the company. Which of the following should the systems administrator do to BEST address this problem?
- Add an ACL to the firewall to block VoIP.
- Change the settings on the phone system to use SIP-TLS.
- Have the phones download new configurations over TFTP.
- Enable QoS configuration on the phone VLAN.
-
A consulting firm was hired to conduct assessment for a company. During the first stage, a penetration tester used a tool that provided the following output:
TCP 80 open
TCP 443 open
TCP 1434 filteredThe penetration tester then used a different tool to make the following requests:
GET / script/login.php?token=45$MHT000MND876
GET / script/login.php?token=@#984DCSPQ%091DFWhich of the following tools did the penetration tester use?
- Protocol analyzer
- Port scanner
- Fuzzer
- Brute forcer
- Log analyzer
- HTTP interceptor
-
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage.
Which of the following exercise types should the analyst perform?
- Summarize the most recently disclosed vulnerabilities.
- Research industry best practices and the latest RFCs.
- Undertake an external vulnerability scan and penetration test.
- Conduct a threat modeling exercise.
-
In the past, the risk committee at Company A has shown an aversion to even minimal amounts of risk acceptance. A security engineer is preparing recommendations regarding the risk of a proposed introducing legacy ICS equipment. The project will introduce a minor vulnerability into the enterprise. This vulnerability does not significantly expose the enterprise to risk and would be expensive against.
Which of the following strategies should the engineer recommended be approved FIRST?
- Avoid
- Mitigate
- Transfer
- Accept
-
A company has adopted and established a continuous-monitoring capability, which has proven to be effective in vulnerability management, diagnostics, and mitigation. The company wants to increase the likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle.
Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
- Install and configure an IPS.
- Enforce routine GPO reviews.
- Form and deploy a hunt team.
- Institute heuristic anomaly detection.
- Use a protocol analyzer with appropriate connectors.
-
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure. The organization’s server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
- Contain the server.
- Initiate a legal hold.
- Perform a risk assessment.
- Determine the data handling standard.
- Disclose the breach to customers.
- Perform an IOC sweep to determine the impact.
-
SIMULATION
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
CAS-003 Part 09 Q17 051 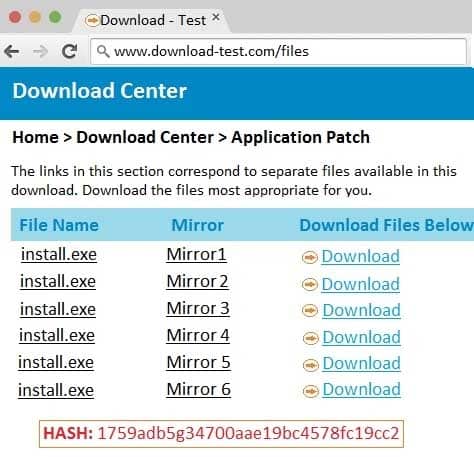
CAS-003 Part 09 Q17 052 
CAS-003 Part 09 Q17 053 
CAS-003 Part 09 Q17 054 
CAS-003 Part 09 Q17 055 
CAS-003 Part 09 Q17 056 
CAS-003 Part 09 Q17 057 - For correct answers: see the explanation below
Explanation:
In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
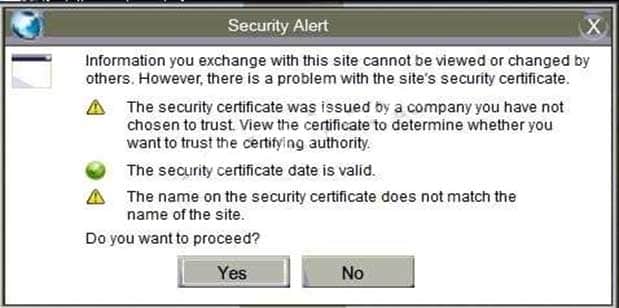
CAS-003 Part 09 Q17 058 Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
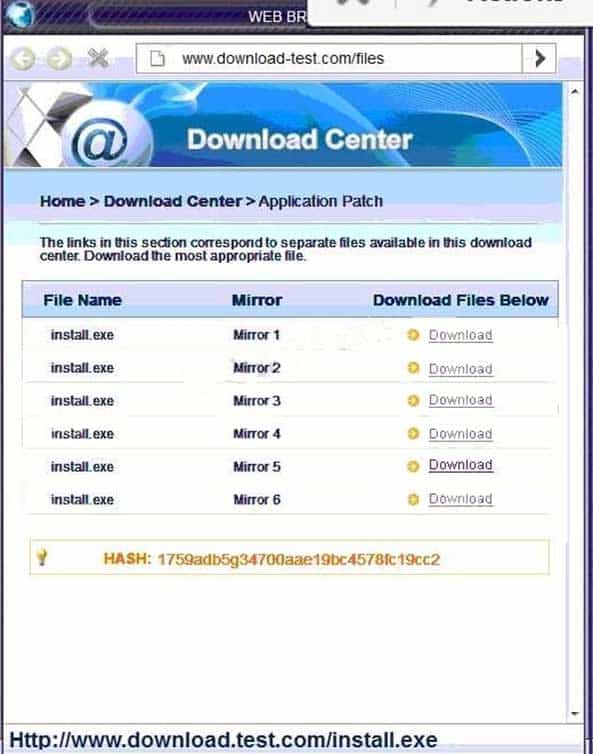
CAS-003 Part 09 Q17 059 Since we need to do this in the most secure manner possible, they should not be used.
Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as shown. Make sure that the hash matches.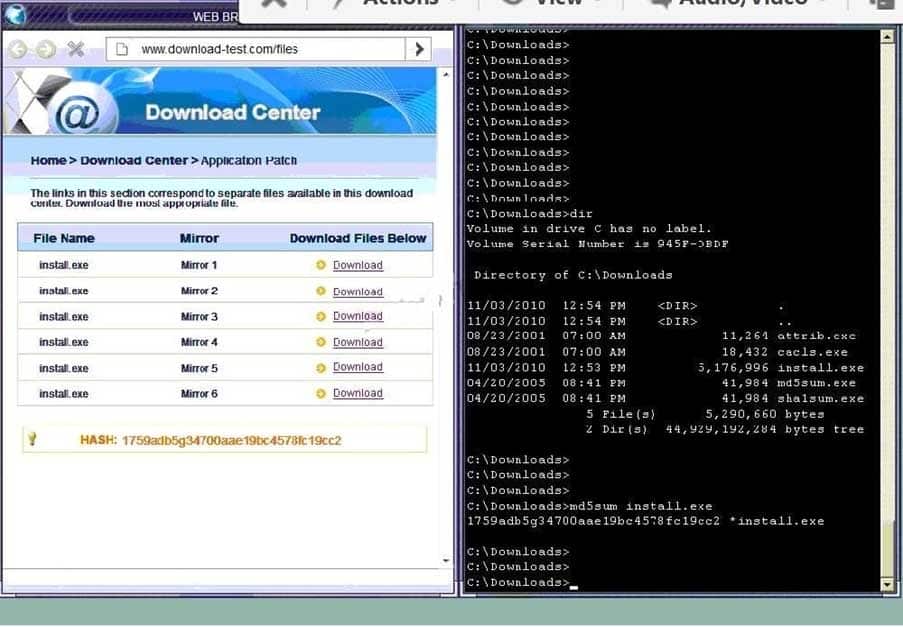
CAS-003 Part 09 Q17 060 Finally, type in install.exe to install it and make sure there are no signature verification errors.
-
An organization, which handles large volumes of PII, allows mobile devices that can process, store, and transmit PII and other sensitive data to be issued to employees. Security assessors can demonstrate recovery and decryption of remnant sensitive data from device storage after MDM issues a successful wipe command. Assuming availability of the controls, which of the following would BEST protect against the loss of sensitive data in the future?
- Implement a container that wraps PII data and stores keying material directly in the container’s encrypted application space.
- Use encryption keys for sensitive data stored in an eFuse-backed memory space that is blown during remote wipe.
- Issue devices that employ a stronger algorithm for the authentication of sensitive data stored on them.
- Procure devices that remove the bootloader binaries upon receipt of an MDM-issued remote wipe command.
-
A large company with a very complex IT environment is considering a move from an on-premises, internally managed proxy to a cloud-based proxy solution managed by an external vendor. The current proxy provides caching, content filtering, malware analysis, and URL categorization for all staff connected behind the proxy. Staff members connect directly to the Internet outside of the corporate network. The cloud-based version of the solution would provide content filtering, TLS decryption, malware analysis, and URL categorization. After migrating to the cloud solution, all internal proxies would be decommissioned. Which of the following would MOST likely change the company’s risk profile?
- 1. There would be a loss of internal intellectual knowledge regarding proxy configurations and application data flows.
2. There would be a greater likelihood of Internet access outages due to lower resilience of cloud gateways.
3. There would be data sovereignty concerns due to changes required in routing and proxy PAC files. - 1. The external vendor would have access to inbound and outbound gateway traffic.
2. The service would provide some level of protection for staff working from home.
3. Outages would be likely to occur for systems or applications with hard-coded proxy information. - 1. The loss of local caching would dramatically increase ISP charges and impact existing bandwidth.
2. There would be a greater likelihood of Internet access outages due to lower resilience of cloud gateways.
3. There would be a loss of internal intellectual knowledge regarding proxy configurations and application data flows. - 1. Outages would be likely to occur for systems or applications with hard-coded proxy information.
2. The service would provide some level of protection for staff members working from home.
3. Malware detection times would decrease due to third-party management of the service.
- 1. There would be a loss of internal intellectual knowledge regarding proxy configurations and application data flows.
-
A security engineer is deploying an IdP to broker authentication between applications. These applications all utilize SAML 2.0 for authentication. Users log into the IdP with their credentials and are given a list of applications they may access. One of the application’s authentications is not functional when a user initiates an authentication attempt from the IdP. The engineer modifies the configuration so users browse to the application first, which corrects the issue. Which of the following BEST describes the root cause?
- The application only supports SP-initiated authentication.
- The IdP only supports SAML 1.0
- There is an SSL certificate mismatch between the IdP and the SaaS application.
- The user is not provisioned correctly on the IdP.