CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 13
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 13
-
A security analyst is classifying data based on input from data owners and other stakeholders. The analyst has identified three data types:
1. Financially sensitive data
2. Project data
3. Sensitive project dataThe analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
- Conduct a quantitative evaluation of the risks associated with commingling the data and reject or accept the concerns raised by the stakeholders.
- Meet with the affected stakeholders and determine which security controls would be sufficient to address the newly raised risks.
- Use qualitative methods to determine aggregate risk scores for each project and use the derived scores to more finely segregate the data.
- Increase the number of available data storage devices to provide enough capacity for physical separation of non-sensitive project data.
-
A government contractor was the victim of a malicious attack that resulted in the theft of sensitive information. An analyst’s subsequent investigation of sensitive systems led to the following discoveries:
– There was no indication of the data owner’s or user’s accounts being compromised.
– No database activity outside of previous baselines was discovered.
– All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
– It was likely not an insider threat, as all employees passed polygraph tests.Given this scenario, which of the following is the MOST likely attack that occurred?
- The attacker harvested the hashed credentials of an account within the database administrators group after dumping the memory of a compromised machine. With these credentials, the attacker was able to access the database containing sensitive information directly.
- An account, which belongs to an administrator of virtualization infrastructure, was compromised with a successful phishing attack. The attacker used these credentials to access the virtual machine manager and made a copy of the target virtual machine image. The attacker later accessed the image offline to obtain sensitive information.
- A shared workstation was physically accessible in a common area of the contractor’s office space and was compromised by an attacker using a USB exploit, which resulted in gaining a local administrator account. Using the local administrator credentials, the attacker was able to move laterally to the server hosting the database with sensitive information.
- After successfully using a watering hole attack to deliver an exploit to a machine, which belongs to an employee of the contractor, an attacker gained access to a corporate laptop. With this access, the attacker then established a remote session over a VPN connection with the server hosting the database of sensitive information.
-
A networking administrator was recently promoted to security administrator in an organization that handles highly sensitive data. The Chief Information Security Officer (CISO) has just asked for all IT security personnel to review a zero-day vulnerability and exploit for specific application servers to help mitigate the organization’s exposure to that risk. Which of the following should the new security administrator review to gain more information? (Choose three.)
- CVE database
- Recent security industry conferences
- Security vendor pages
- Known vendor threat models
- Secure routing metrics
- Server’s vendor documentation
- Verified security forums
- NetFlow analytics
-
A company has decided to replace all the T-1 uplinks at each regional office and move away from using the existing MPLS network. All regional sites will use high-speed connections and VPNs to connect back to the main campus. Which of the following devices would MOST likely be added at each location?
- SIEM
- IDS/IPS
- Proxy server
- Firewall
- Router
-
An external red team is brought into an organization to perform a penetration test of a new network-based application. The organization deploying the network application wants the red team to act like remote, external attackers, and instructs the team to use a black-box approach. Which of the following is the BEST methodology for the red team to follow?
- Run a protocol analyzer to determine what traffic is flowing in and out of the server, and look for ways to alter the data stream that will result in information leakage or a system failure.
- Send out spear-phishing emails against users who are known to have access to the network-based application, so the red team can go on-site with valid credentials and use the software.
- Examine the application using a port scanner, then run a vulnerability scanner against open ports looking for known, exploitable weaknesses the application and related services may have.
- Ask for more details regarding the engagement using social engineering tactics in an attempt to get the organization to disclose more information about the network application to make attacks easier.
-
First responders, who are part of a core incident response team, have been working to contain an outbreak of ransomware that also led to data loss. In a rush to isolate the three hosts that were calling out to the NAS to encrypt whole directories, the hosts were shut down immediately without investigation and then isolated. Which of the following were missed? (Choose two.)
- CPU, process state tables, and main memory dumps
- Essential information needed to perform data restoration to a known clean state
- Temporary file system and swap space
- Indicators of compromise to determine ransomware encryption
- Chain of custody information needed for investigation
-
A regional business is expecting a severe winter storm next week. The IT staff has been reviewing corporate policies on how to handle various situations and found some are missing or incomplete. After reporting this gap in documentation to the information security manager, a document is immediately drafted to move various personnel to other locations to avoid downtime in operations. This is an example of:
- a disaster recovery plan
- an incident response plan
- a business continuity plan
- a risk avoidance plan
-
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot.
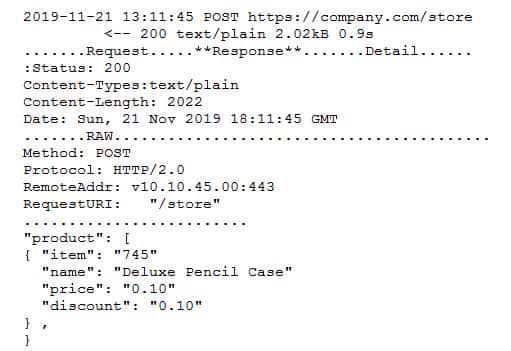
CAS-003 Part 13 Q08 076 Which of the following tools was MOST likely used to exploit the application?
- The engineer captured the data with a protocol analyzer, and then utilized Python to edit the data
- The engineer queried the server and edited the data using an HTTP proxy interceptor
- The engineer used a cross-site script sent via curl to edit the data
- The engineer captured the HTTP headers, and then replaced the JSON data with a banner-grabbing tool
-
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below:
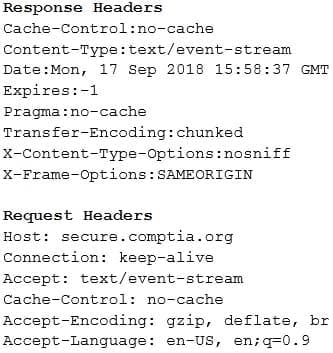
CAS-003 Part 13 Q09 077 Which of the following tools did the security engineer MOST likely use to generate this output?
- Application fingerprinter
- Fuzzer
- HTTP interceptor
- Vulnerability scanner
-
The Chief Financial Officer (CFO) of a major hospital system has received a ransom letter that demands a large sum of cryptocurrency be transferred to an anonymous account. If the transfer does not take place within ten hours, the letter states that patient information will be released on the dark web. A partial listing of recent patients is included in the letter. This is the first indication that a breach took place. Which of the following steps should be done FIRST?
- Review audit logs to determine the extent of the breach
- Pay the hacker under the condition that all information is destroyed
- Engage a counter-hacking team to retrieve the data
- Notify the appropriate legal authorities and legal counsel
-
A project manager is working with system owners to develop maintenance windows for system patching and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
- MOU
- SOW
- SRTM
- SLA
-
A Chief Information Security Officer (CISO) is working with a consultant to perform a gap assessment prior to an upcoming audit. It is determined during the assessment that the organization lacks controls to effectively assess regulatory compliance by third-party service providers. Which of the following should be revised to address this gap?
- Privacy policy
- Work breakdown structure
- Interconnection security agreement
- Vendor management plan
- Audit report
-
Joe, a penetration tester, is assessing the security of an application binary provided to him by his client. Which of the following methods would be the MOST effective in reaching this objective?
- Employ a fuzzing utility
- Use a static code analyzer
- Run the binary in an application sandbox
- Manually review the binary in a text editor
-
A security administrator is advocating for enforcement of a new policy that would require employers with privileged access accounts to undergo periodic inspections and review of certain job performance data. To which of the following policies is the security administrator MOST likely referring?
- Background investigation
- Mandatory vacation
- Least privilege
- Separation of duties
-
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements:
1. Support server, laptop, and desktop infrastructure
2. Due to limited security resources, implement active protection capabilities
3. Provide users with the ability to self-service classify information and apply policies
4. Protect data-at-rest and data-in-useWhich of the following endpoint capabilities would BEST meet the above requirements? (Choose two.)
- Data loss prevention
- Application whitelisting
- Endpoint detect and respond
- Rights management
- Log monitoring
- Antivirus
-
A company is migrating systems from an on-premises facility to a third-party managed datacenter. For continuity of operations and business agility, remote access to all hardware platforms must be available at all times. Access controls need to be very robust and provide an audit trail. Which of the following security controls will meet the company’s objectives? (Choose two.)
- Integrated platform management interfaces are configured to allow access only via SSH
- Access to hardware platforms is restricted to the systems administrator’s IP address
- Access is captured in event logs that include source address, time stamp, and outcome
- The IP addresses of server management interfaces are located within the company’s extranet
- Access is limited to interactive logins on the VDi
- Application logs are hashed cryptographically and sent to the SIEM
-
A Chief Information Security Officer (CISO) implemented MFA for all accounts in parallel with the BYOD policy. After the implementation, employees report the increased authentication method is causing increased time to tasks. This applies both to accessing the email client on the workstation and the online collaboration portal. Which of the following should be the CISO implement to address the employees’ concerns?
- Create an exception for the company’s IPs.
- Implement always-on VPN.
- Configure the use of employee PKI authentication for email.
- Allow the use of SSO.
-
A Chief Information Security Officer (CISO) of a large financial institution undergoing an IT transformation program wants to embed security across the business rapidly and across as many layers of the business as possible to achieve quick wins and reduce risk to the organization. Which of the following business areas should the CISO target FIRST to best meet the objective?
- Programmers and developers should be targeted to ensure secure coding practices, including automated code reviews with remediation processes, are implemented immediately.
- Human resources should be targeted to ensure all new employees undertake security awareness and compliance training to reduce the impact of phishing and ransomware attacks.
- The project management office should be targeted to ensure security is managed and included at all levels of the project management cycle for new and in-flight projects.
- Risk assurance teams should be targeted to help identify key business unit security risks that can be aggregated across the organization to produce a risk posture dashboard for executive management.
-
A security administrator is concerned about the increasing number of users who click on malicious links contained within phishing emails. Although the company has implemented a process to block these links at the network perimeter, many accounts are still becoming compromised. Which of the following should be implemented for further reduce the number of account compromises caused by remote users who click these links?
- Anti-spam gateways
- Security awareness training
- URL rewriting
- Internal phishing campaign
-
A university’s help desk is receiving reports that Internet access on campus is not functioning. The network administrator looks at the management tools and sees the 1Gbps Internet is completely saturated with ingress traffic. The administrator sees the following output on the Internet router:

CAS-003 Part 13 Q20 078 The administrator calls the university’s ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?
- The ISP engineer should null route traffic to the web server immediately to restore Internet connectivity. The university should implement a remotely triggered black hole with the ISP to resolve this more quickly in the future.
- A university web server is under increased load during enrollment. The ISP engineer should immediately increase bandwidth to 2Gbps to restore Internet connectivity. In the future, the university should pay for more bandwidth to handle spikes in web server traffic.
- The ISP engineer should immediately begin blocking IP addresses that are attacking the web server to restore Internet connectivity. In the future, the university should install a WAF to prevent this attack from happening again.
- The ISP engineer should begin refusing network connections to the web server immediately to restore Internet connectivity on campus. The university should purchase an IPS device to stop DDoS attacks in the future.