CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 14
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 14
-
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO’s first task is to write a new, relevant risk assessment for the organization. Which of the following would BEST help the CISO find relevant risks to the organization? (Choose two.)
- Perform a penetration test.
- Conduct a regulatory audit.
- Hire a third-party consultant.
- Define the threat model.
- Review the existing BIA.
- Perform an attack path analysis.
-
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
- Install network taps at the edge of the network.
- Send syslog from the IDS into the SIEM.
- Install HIDS on each computer.
- SPAN traffic form the network core into the IDS.
-
As part of incident response, a technician is taking an image of a compromised system and copying the image to a remote image server (192.168.45.82). The system drive is very large but does not contain the sensitive data. The technician has limited time to complete this task. Which of the following is the BEST command for the technician to run?
- tar cvf – / | ssh 192.168.45.82 “cat – > /images/image.tar”
- dd if=/dev/mem | scp – 192.168.45.82:/images/image.dd
- memdump /dev/sda1 | nc 192.168.45.82 3000
- dd if=/dev/sda | nc 192.168.45.82 3000
-
A network administrator is concerned about a particular server that is attacked occasionally from hosts on the Internet. The server is not critical; however, the attacks impact the rest of the network.
While the company’s current ISP is cost effective, the ISP is slow to respond to reported issues. The administrator needs to be able to mitigate the effects of an attack immediately without opening a trouble ticket with the ISP. The ISP is willing to accept a very small network route advertised with a particular BGP community string. Which of the following is the BEST way for the administrator to mitigate the effects of these attacks?
- Use the route protection offered by the ISP to accept only BGP routes from trusted hosts on the Internet, which will discard traffic from attacking hosts.
- Work with the ISP and subscribe to an IPS filter that can recognize the attack patterns of the attacking hosts, and block those hosts at the local IPS device.
- Advertise a /32 route to the ISP to initiate a remotely triggered black hole, which will discard traffic destined to the problem server at the upstream provider.
- Add a redundant connection to a second local ISP, so a redundant connection is available for use if the server is being attacked on one connection.
-
A Chief Information Security Officer (CISO) needs to establish a KRI for a particular system. The system holds archives of contracts that are no longer in use. The contracts contain intellectual property and have a data classification of non-public. Which of the following be the BEST risk indicator for this system?
- Average minutes of downtime per quarter
- Percent of patches applied in the past 30 days
- Count of login failures per week
- Number of accounts accessing the system per day
-
Staff members are reporting an unusual number of device thefts associated with time out of the office. Thefts increased soon after the company deployed a new social networking application. Which of the following should the Chief Information Security Officer (CISO) recommend implementing?
- Automatic location check-ins
- Geolocated presence privacy
- Integrity controls
- NAC checks to quarantine devices
-
A security engineer is assessing a new IoT product. The product interfaces with the ODBII port of a vehicle and uses a Bluetooth connection to relay data to an onboard data logger located in the vehicle. The data logger can only transfer data over a custom USB cable. The engineer suspects a relay attack is possible against the cryptographic implementation used to secure messages between segments of the system. Which of the following tools should the engineer use to confirm the analysis?
- Vulnerability scanner
- Wireless protocol analyzer
- Log analysis and reduction tools
- Network-based fuzzer
-
A recent security assessment revealed a web application may be vulnerable to clickjacking. According to the application developers, a fix may be months away. Which of the following should a security engineer configure on the web server to help mitigate the issue?
- File upload size limits
- HttpOnly cookie field
- X-Frame-Options header
- Input validation
-
A developer is reviewing the following transaction logs from a web application:
Username: John Doe
Street name: Main St.
Street number: <script>alert(‘test’)</alert>Which of the following code snippets should the developer implement given the above transaction logs?
- if ($input != strcmp($var1, “<>”)) {die();}
- <form name =”form1” action=”/submit.php” onsubmit=”return validate()” action=POST>
- $input=strip_tags(trim($_POST[‘var1’]));
- <html><form name=”myform” action=”www.server.com/php/submit.php action=GET”
-
A manufacturing company recently recovered from an attack on its ICS devices. It has since reduced the attack surface by isolating the affected components. The company now wants to implement detection capabilities. It is considering a system that is based on machine learning. Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
- Trains on normal behavior and identifies deviations therefrom
- Identifies and triggers upon known bad signatures and behaviors
- Classifies traffic based on logical protocols and messaging formats
- Automatically reconfigures ICS devices based on observed behavior
-
An engineer is reviewing the security architecture for an enterprise network. During the review, the engineer notices an undocumented node on the network. Which of the following approaches can be utilized to determine how this node operates? (Choose two.)
- Use reverse engineering and techniques
- Assess the node within a continuous integration environment
- Employ a static code analyzer
- Review network and traffic logs
- Use a penetration testing framework to analyze the node
- Analyze the output of a ping sweep
-
A security administrator is reviewing the following output from an offline password audit:
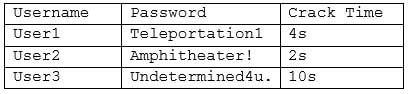
CAS-003 Part 14 Q12 079 Which of the following should the systems administrator implement to BEST address this audit finding? (Choose two.)
- Cryptoprocessor
- Bcrypt
- SHA-256
- PBKDF2
- Message authentication
-
A corporate forensic investigator has been asked to acquire five forensic images of an employee database application. There are three images to capture in the United States, one in the United Kingdom, and one in Germany. Upon completing the work, the forensics investigator saves the images to a local workstation. Which of the following types of concerns should the forensic investigator have about this work assignment?
- Environmental
- Privacy
- Ethical
- Criminal
-
A security consultant is performing a penetration test on www.comptia.org and wants to discover the DNS administrator’s email address to use in a later social engineering attack. The information listed with the DNS registrar is private. Which of the following commands will also disclose the email address?
- dig –h comptia.org
- whois –f comptia.org
- nslookup –type=SOA comptia.org
- dnsrecon –i comptia.org –t hostmaster
-
Ann, a corporate executive, has been the recent target of increasing attempts to obtain corporate secrets by competitors through advanced, well-funded means. Ann frequently leaves her laptop unattended and physically unsecure in hotel rooms during travel. A security engineer must find a practical solution for Ann that minimizes the need for user training. Which of the following is the BEST solution in this scenario?
- Full disk encryption
- Biometric authentication
- An eFuse-based solution
- Two-factor authentication
-
An internal application has been developed to increase the efficiency of an operational process of a global manufacturer. New code was implemented to fix a security bug, but it has caused operations to halt. The executive team has decided fixing the security bug is less important than continuing operations.
Which of the following would BEST support immediate rollback of the failed fix? (Choose two.)
- Version control
- Agile development
- Waterfall development
- Change management
- Continuous integration
-
An analyst is investigating anomalous behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the “compose” window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
- Reverse engineer the application binary.
- Perform static code analysis on the source code.
- Analyze the device firmware via the JTAG interface.
- Change to a whitelist that uses cryptographic hashing.
- Penetration test the mobile application.
-
A security appliance vendor is reviewing an RFP that is requesting solutions for the defense of a set of web-based applications. This RFP is from a financial institution with very strict performance requirements. The vendor would like to respond with its solutions.
Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor’s qualifications?
- The solution employs threat information-sharing capabilities using a proprietary data model.
- The RFP is issued by a financial institution that is headquartered outside of the vendor’s own country.
- The overall solution proposed by the vendor comes in less that the TCO parameter in the RFP.
- The vendor’s proposed solution operates below the KPPs indicated in the RFP.
-
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
- Single-tenant private cloud
- Multitenant SaaS cloud
- Single-tenant hybrid cloud
- Multitenant IaaS cloud
- Multitenant PaaS cloud
- Single-tenant public cloud
-
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses “Number of successful phishing attacks” as a KRI, but it does not show an increase.
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
- The ratio of phishing emails to non-phishing emails
- The number of phishing attacks per employee
- The number of unsuccessful phishing attacks
- The percent of successful phishing attacks