CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 15
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 15
-
An organization’s network security administrator has been using an SSH connection to manage switches and routers for several years. After attempting to connect to a router, an alert appears on the terminal emulation software, warning that the SSH key has changed.
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.)
- The SSH keys were given to another department.
- A MITM attack is being performed by an APT.
- The terminal emulator does not support SHA-256.
- An incorrect username or password was entered.
- A key rotation has occurred as a result of an incident.
- The workstation is not syncing with the correct NTP server.
-
Following a recent outage, a systems administrator is conducting a study to determine a suitable bench stock on server hard drives.
Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep-on hand?
- TTR
- ALE
- MTBF
- SLE
- RPO
-
A school contracts with a vendor to devise a solution that will enable the school library to lend out tablet computers to students while on site. The tablets must adhere to string security and privacy practices. The school’s key requirements are to:
– Maintain privacy of students in case of loss
– Have a theft detection control in place
– Be compliant with defined disability requirements
– Have a four-hour minimum battery lifeWhich of the following should be configured to BEST meet the requirements? (Choose two.)
- Remote wiping
- Geofencing
- Antivirus software
- TPM
- FDE
- Tokenization
-
A project manager is working with a software development group to collect and evaluate user scenarios related to the organization’s internally designed data analytics tool. While reviewing stakeholder input, the project manager would like to formally document the needs of the various stakeholders and the associated organizational compliance objectives supported by the project.
Which of the following would be MOST appropriate to use?
- Roles matrix
- Peer review
- BIA
- SRTM
-
A laptop is recovered a few days after it was stolen.
Which of the following should be verified during incident response activities to determine the possible impact of the incident?
- Full disk encryption status
- TPM PCR values
- File system integrity
- Presence of UEFI vulnerabilities
-
Ann, a security administrator, is conducting an assessment on a new firewall, which was placed at the perimeter of a network containing PII. Ann runs the following commands on a server (10.0.1.19) behind the firewall:

CAS-003 Part 15 Q06 080 From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:
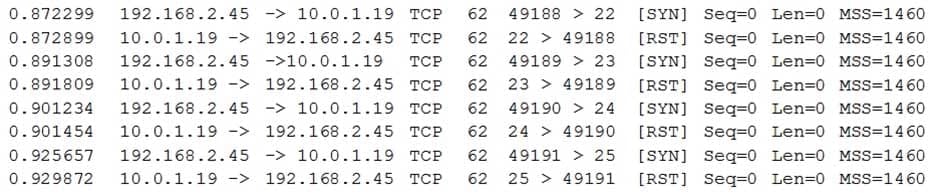
CAS-003 Part 15 Q06 081 Connectivity to the server from outside the firewall worked as expected prior to executing these commands.
Which of the following can be said about the new firewall?
- It is correctly dropping all packets destined for the server.
- It is not blocking or filtering any traffic to the server.
- Iptables needs to be restarted.
- The IDS functionality of the firewall is currently disabled.
-
A new database application was added to a company’s hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company’s cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security team do to help mitigate future attacks within the VM environment? (Choose two.)
- Install the appropriate patches.
- Install perimeter NGFW.
- Configure VM isolation.
- Deprovision database VM.
- Change the user’s access privileges.
- Update virus definitions on all endpoints.
-
A penetration testing manager is contributing to an RFP for the purchase of a new platform. The manager has provided the following requirements:
– Must be able to MITM web-based protocols
– Must be able to find common misconfigurations and security holesWhich of the following types of testing should be included in the testing platform? (Choose two.)
- Reverse engineering tool
- HTTP intercepting proxy
- Vulnerability scanner
- File integrity monitor
- Password cracker
- Fuzzer
-
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS.
Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
- Run the memdump utility with the -k flag.
- Use a loadable kernel module capture utility, such as LiME.
- Run dd on/dev/mem.
- Employ a stand-alone utility, such as FTK Imager.
-
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.
CAS-003 Part 15 Q10 082 Below is a snippet from the firewall related to that server (access is provided in a top-down model):

CAS-003 Part 15 Q10 083 Which of the following lines should be configured to allow the proper access? (Choose two.)
- Move line 3 below line 4 and change port 80 to 443 on line 4.
- Move line 3 below line 4 and add port 443 to line.
- Move line 4 below line 5 and add port 80 to 8080 on line 2.
- Add port 22 to line 2.
- Add port 22 to line 5.
- Add port 443 to line 2.
- Add port 443 to line 5.
-
A firewall specialist has been newly assigned to participate in red team exercises and needs to ensure the skills represent real-world threats.
Which of the following would be the BEST choice to help the new team member learn bleeding-edge techniques?
- Attend hacking conventions.
- Research methods while using Tor.
- Interview current red team members.
- Attend web-based training.
-
An organization is implementing a virtualized thin-client solution for normal user computing and access. During a review of the architecture, concerns were raised that an attacker could gain access to multiple user environments by simply gaining a foothold on a single one with malware. Which of the following reasons BEST explains this?
- Malware on one virtual environment could enable pivoting to others by leveraging vulnerabilities in the hypervisor.
- A worm on one virtual environment could spread to others by taking advantage of guest OS networking services vulnerabilities.
- One virtual environment may have one or more application-layer vulnerabilities, which could allow an attacker to escape that environment.
- Malware on one virtual user environment could be copied to all others by the attached network storage controller.
-
An online bank has contracted with a consultant to perform a security assessment of the bank’s web portal. The consultant notices the login page is linked from the main page with HTTPS, but when the URL is changed to HTTP, the browser is automatically redirected back to the HTTPS site. Which of the following is a concern for the consultant, and how can it be mitigated?
- XSS could be used to inject code into the login page during the redirect to the HTTPS site. The consultant should implement a WAF to prevent this.
- The consultant is concerned the site is using an older version of the SSL 3.0 protocol that is vulnerable to a variety of attacks. Upgrading the site to TLS 1.0 would mitigate this issue.
- The HTTP traffic is vulnerable to network sniffing, which could disclose usernames and passwords to an attacker. The consultant should recommend disabling HTTP on the web server.
- A successful MITM attack Could intercept the redirect and use sslstrip to decrypt further HTTPS traffic. Implementing HSTS on the web server would prevent this.
-
A security administrator wants to implement controls to harden company-owned mobile devices. Company policy specifies the following requirements:
– Mandatory access control must be enforced by the OS.
– Devices must only use the mobile carrier data transport.Which of the following controls should the security administrator implement? (Choose three.)
- Enable DLP
- Enable SEAndroid
- Enable EDR
- Enable secure boot
- Enable remote wipe
- Disable Bluetooth
- Disable 802.11
- Disable geotagging
-
While conducting online research about a company to prepare for an upcoming penetration test, a security analyst discovers detailed financial information on an investor website the company did not make public. The analyst shares this information with the Chief Financial Officer (CFO), who confirms the information is accurate, as it was recently discussed at a board of directors meeting. Many of the details are verbatim discussion comments captured by the board secretary for purposes of transcription on a mobile device. Which of the following would MOST likely prevent a similar breach in the future?
- Remote wipe
- FDE
- Geolocation
- eFuse
- VPN
-
An organization wants to allow its employees to receive corporate email on their own smartphones. A security analyst is reviewing the following information contained within the file system of an employee’s smartphone:
FamilyPix.jpg
Taxreturn.tax
paystub.pdf
employeesinfo.xls
SoccerSchedule.doc
RecruitmentPlan.xlsBased on the above findings, which of the following should the organization implement to prevent further exposure? (Choose two.)
- Remote wiping
- Side loading
- VPN
- Containerization
- Rooting
- Geofencing
- Jailbreaking
-
An infrastructure team within an energy organization is at the end of a procurement process and has selected a vendor’s SaaS platform to deliver services. As part of the legal negotiation, there are a number of outstanding risks, including:
1. There are clauses that confirm a data retention period in line with what is in the energy organization’s security policy.
2. The data will be hosted and managed outside of the energy organization’s geographical location.The number of users accessing the system will be small, and no sensitive data will be hosted in the SaaS platform. Which of the following should the project’s security consultant recommend as the NEXT step?
- Develop a security exemption, as the solution does not meet the security policies of the energy organization.
- Require a solution owner within the energy organization to accept the identified risks and consequences.
- Mititgate the risks by asking the vendor to accept the in-country privacy principles and modify the retention period.
- Review the procurement process to determine the lessons learned in relation to discovering risks toward the end of the process.
-
A developer emails the following output to a security administrator for review:
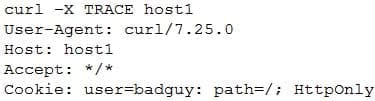
CAS-003 Part 15 Q18 084 Which of the following tools might the security administrator use to perform further security assessment of this issue?
- Port scanner
- Vulnerability scanner
- Fuzzer
- HTTP interceptor
-
A software development company lost customers recently because of a large number of software issues. These issues were related to integrity and availability defects, including buffer overflows, pointer dereferences, and others. Which of the following should the company implement to improve code quality? (Choose two.)
- Development environment access controls
- Continuous integration
- Code comments and documentation
- Static analysis tools
- Application containerization
- Code obfuscation
-
An enterprise is trying to secure a specific web-based application by forcing the use of multifactor authentication. Currently, the enterprise cannot change the application’s sign-in page to include an extra field. However, the web-based application supports SAML. Which of the following would BEST secure the application?
- Using an SSO application that supports mutlifactor authentication
- Enabling the web application to support LDAP integration
- Forcing higher-complexity passwords and frequent changes
- Deploying Shibboleth to all web-based applications in the enterprise