CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 16
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 16
-
After significant vulnerabilities and misconfigurations were found in numerous production web applications, a security manager identified the need to implement better development controls.
Which of the following controls should be verified? (Choose two.)
- Input validation routines are enforced on the server side.
- Operating systems do not permit null sessions.
- Systems administrators receive application security training.
- VPN connections are terminated after a defined period of time.
- Error-handling logic fails securely.
- OCSP calls are handled effectively.
-
An organization wants to arm its cybersecurity defensive suite automatically with intelligence on zero-day threats shortly after they emerge. Acquiring tools and services that support which of the following data standards would BEST enable the organization to meet this objective?
- XCCDF
- OVAL
- STIX
- CWE
- CVE
-
A financial institution’s information security officer is working with the risk management officer to determine what to do with the institution’s residual risk after all security controls have been implemented. Considering the institution’s very low risk tolerance, which of the following strategies would be BEST?
- Transfer the risk.
- Avoid the risk
- Mitigate the risk.
- Accept the risk.
-
A large, public university has recently been experiencing an increase in ransomware attacks against computers connected to its network. Security engineers have discovered various staff members receiving seemingly innocuous files in their email that are being run. Which of the following would BEST mitigate this attack method?
- Improving organizations email filtering
- Conducting user awareness training
- Upgrading endpoint anti-malware software
- Enabling application whitelisting
-
A security architect is reviewing the code for a company’s financial website. The architect suggests adding the following HTML element, along with a server-side function, to generate a random number on the page used to initiate a funds transfer:
<input type=”hidden” name=”token” value=generateRandomNumber()>
Which of the following attacks is the security architect attempting to prevent?
- SQL injection
- XSRF
- XSS
- Clickjacking
-
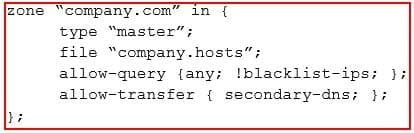
A security engineer is assessing the controls that are in place to secure the corporate-Internet-facing DNS server. The engineer notices that security ACLs exist but are not being used properly. The DNS server should respond to any source but only provide information about domains it has authority over. Additionally, the DNS administrator have identified some problematic IP addresses that should not be able to make DNS requests. Given the ACLs below:
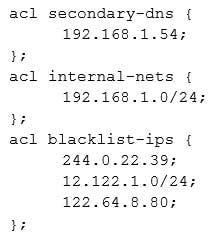
CAS-003 Part 16 Q06 085 Which of the following should the security administrator configure to meet the DNS security needs?
-
Following a recent and very large corporate merger, the number of log files an SOC needs to review has approximately tripled. The Chief Information Security Officer (CISO) has not been allowed to hire any more staff for the SOC, but is looking for other ways to automate the log review process so the SOC receives less noise. Which of the following would BEST reduce log noise for the SOC?
- SIEM filtering
- Machine learning
- Outsourcing
- Centralized IPS
-
An organization is deploying IoT locks, sensors, and cameras, which operate over 802.11, to replace legacy building access control systems. These devices are capable of triggering physical access changes, including locking and unlocking doors and gates. Unfortunately, the devices have known vulnerabilities for which the vendor has yet to provide firmware updates.
Which of the following would BEST mitigate this risk?
- Direct wire the IoT devices into physical switches and place them on an exclusive VLAN.
- Require sensors to sign all transmitted unlock control messages digitally.
- Associate the devices with an isolated wireless network configured for WPA2 and EAP-TLS.
- Implement an out-of-band monitoring solution to detect message injections and attempts.
-
A security administrator is updating corporate policies to respond to an incident involving collusion between two systems administrators that went undetected for more than six months.
Which of the following policies would have MOST likely uncovered the collusion sooner? (Choose two.)
- Mandatory vacation
- Separation of duties
- Continuous monitoring
- Incident response
- Time-of-day restrictions
- Job rotation
-
A core router was manipulated by a credentialed bypass to send all network traffic through a secondary router under the control of an unauthorized user connected to the network by WiFi.
Which of the following would BEST reduce the risk of this attack type occurring?
- Implement a strong, complex password policy for user accounts that have access to the core router.
- Deploy 802.1X as the NAC system for the WiFi infrastructure.
- Add additional port security settings for the switching environment connected to the core router.
- Allow access to the core router management interface only through an out-of-band channel.
-
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiation, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability.
2. The data will be hosted and managed outside of the company’s geographical location.The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant of the project, which of the following should the project’s security consultant recommend as the NEXT step?
- Develop a security exemption, as it does not meet the security policies.
- Require the solution owner to accept the identified risks and consequences.
- Mitigate the risk by asking the vendor to accept the in-country privacy principles.
- Review the procurement process to determine the lessons learned.
-
A security analyst works for a defense contractor that produces classified research on drones. The contractor faces nearly constant attacks from sophisticated nation-state actors and other APIs.
Which of the following would help protect the confidentiality of the research data?
- Use diverse components in layers throughout the architecture
- Implement non-heterogeneous components at the network perimeter
- Purge all data remnants from client devices’ volatile memory at regularly scheduled intervals
- Use only in-house developed applications that adhere to strict SDLC security requirements
-
A company recently implemented a variety of security services to detect various types of traffic that pose a threat to the company. The following services were enabled within the network:
• Scan of specific subsets for vulnerabilities
• Categorizing and logging of website traffic
• Enabling specific ACLs based on application traffic
• Sending suspicious files to a third-party site for validationA report was sent to the security team that identified multiple incidents of users sharing large amounts of data from an on-premise server to a public site. A small percentage of that data also contained malware and spyware
Which of the following services MOST likely identified the behavior and sent the report?
- Content filter
- User behavioral analytics
- Application sandbox
- Web application firewall
- Endpoint protection
- Cloud security broker
-
An external red team member conducts a penetration test, attempting to gain physical access to a large organization’s server room in a branch office. During reconnaissance, the red team member sees a clearly marked door to the server room, located next to the lobby, with a tumbler lock.
Which of the following is BEST for the red team member to bring on site to open the locked door as quickly as possible without causing significant damage?
- Screwdriver set
- Bump key
- RFID duplicator
- Rake picking
-
A company relies on an ICS to perform equipment monitoring functions that are federally mandated for operation of the facility. Fines for non-compliance could be costly. The ICS has known vulnerabilities and can no longer be patched or updated. Cyber-liability insurance cannot be obtained because insurance companies will not insure this equipment.
Which of the following would be the BEST option to manage this risk to the company’s production environment?
- Avoid the risk by removing the ICS from production
- Transfer the risk associated with the ICS vulnerabilities
- Mitigate the risk by restricting access to the ICS
- Accept the risk and upgrade the ICS when possible
-
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead. Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
- Risk assessment
- Regression testing
- User story development
- Data abstraction
- Business impact assessment
-
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data? (Choose two.)
- Data aggregation
- Data sovereignty
- Data isolation
- Data volume
- Data analytics
- Data precision
-
A company recently implemented a new cloud storage solution and installed the required synchronization client on all company devices. A few months later, a breach of sensitive data was discovered. Root cause analysis shows the data breach happened from a lost personal mobile device.
Which of the following controls can the organization implement to reduce the risk of similar breaches?
- Biometric authentication
- Cloud storage encryption
- Application containerization
- Hardware anti-tamper
-
A vendor develops a mobile application for global customers. The mobile application supports advanced encryption of data between the source (the mobile device) and the destination (the organization’s ERP system).
As part of the vendor’s compliance program, which of the following would be important to take into account?
- Mobile tokenization
- Export controls
- Device containerization
- Privacy policies
-
A security engineer is working to secure an organization’s VMs. While reviewing the workflow for creating VMs on demand, the engineer raises a concern about the integrity of the secure boot process of the VM guest.
Which of the following would BEST address this concern?
- Configure file integrity monitoring of the guest OS.
- Enable the vTPM on a Type 2 hypervisor.
- Only deploy servers that are based on a hardened image.
- Protect the memory allocation of a Type 1 hypervisor.