CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 19
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 19
-
A security manager needed to protect a high-security data center, so the manager installed a mantrap that can detect an employee’s heartbeat, weight, and badge. Which of the following did the security manager implement?
- A physical control
- A corrective control
- A compensating control
- A managerial control
-
An organization is concerned that its hosted web servers are not running the most updated version of software. Which of the following would work BEST to help identify potential vulnerabilities?
-
hping3 –S comptia.org –p 80
-
nc –1 –v comptia.org –p 80
-
nmap comptia.org –p 80 –sV -
nslookup –port=80 comptia.org
-
-
A security administrator adding a NAC requirement for all VPN users to ensure the connecting devices are compliant with company policy. Which of the following items provides the HIGHEST assurance to meet this requirement?
- Implement a permanent agent.
- Install antivirus software.
- Use an agentless implementation.
- Implement PKI.
-
A company wants to configure its wireless network to require username and password authentication. Which of the following should the system administrator implement?
- WPS
- PEAP
- TKIP
- PKI
-
Ann, a security manager, is reviewing a threat feed that provides information about attacks that allow a malicious user to gain access to private contact lists. Ann receives a notification that the vulnerability can be exploited within her environment. Given this information, Ann can anticipate an increase in:
- vishing attacks
- SQL injections attacks
- web application attacks
- brute-force attacks
-
A security analyst is reviewing the following pseudo-output snippet after running the command less /tmp/file.tmp.
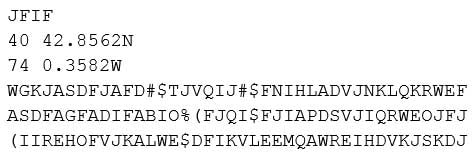
CAS-003 Part 19 Q06 094 The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
- Deploy a solution to sanitize geotagging information
- Install software to wipe data remnants on servers
- Enforce proper input validation on mission-critical software
- Implement a digital watermarking solution
-
An international e-commerce company has identified attack traffic originating from a whitelisted third party’s IP address used to mask the third party’s internal network. The security team needs to block the attack traffic without impacting the vendor’s services. Which of the following is the BEST approach to identify the threat?
- Ask the third-party vendor to block the attack traffic
- Configure the third party’s proxy to begin sending X-Forwarded-For headers
- Configure the e-commerce company’s IPS to inspect HTTP traffic
- Perform a vulnerability scan against the network perimeter and remediate any issues identified
-
An organization is in the process of evaluating service providers for an upcoming migration to cloud-based services for the organization’s ERP system. As part of the requirements defined by the project team, regulatory requirements specify segmentation and isolation of the organization’s data. Which of the following should the vendor management team identify as a requirement during the procurement process?
- Public cloud services with single-tenancy IaaS architectures
- Private cloud services with single-tenancy PaaS services
- Private cloud services with multitenancy in place for private SaaS environments
- Public cloud services with private SaaS environments supported by private IaaS backbones
-
DRAG DROP
A vulnerability scan with the latest definitions was performed across Sites A and B.
INSTRUCTIONS
Match each relevant finding to the affected host.
After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
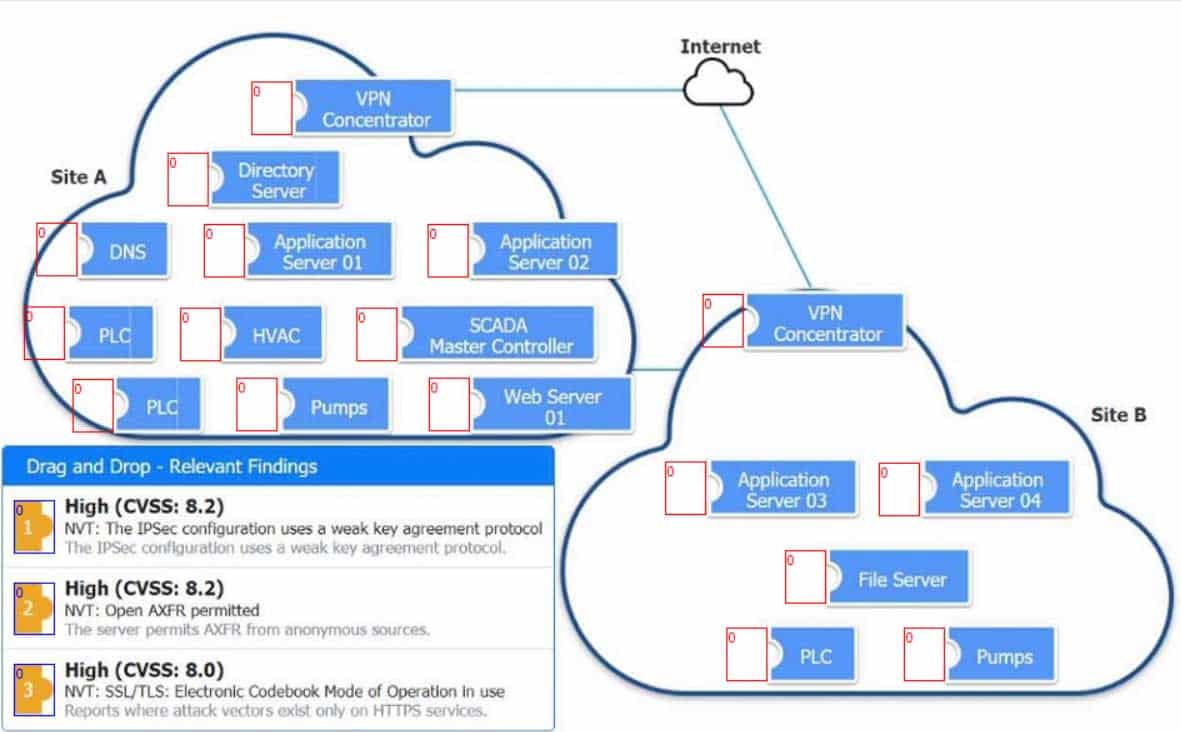
CAS-003 Part 19 Q09 095 Question 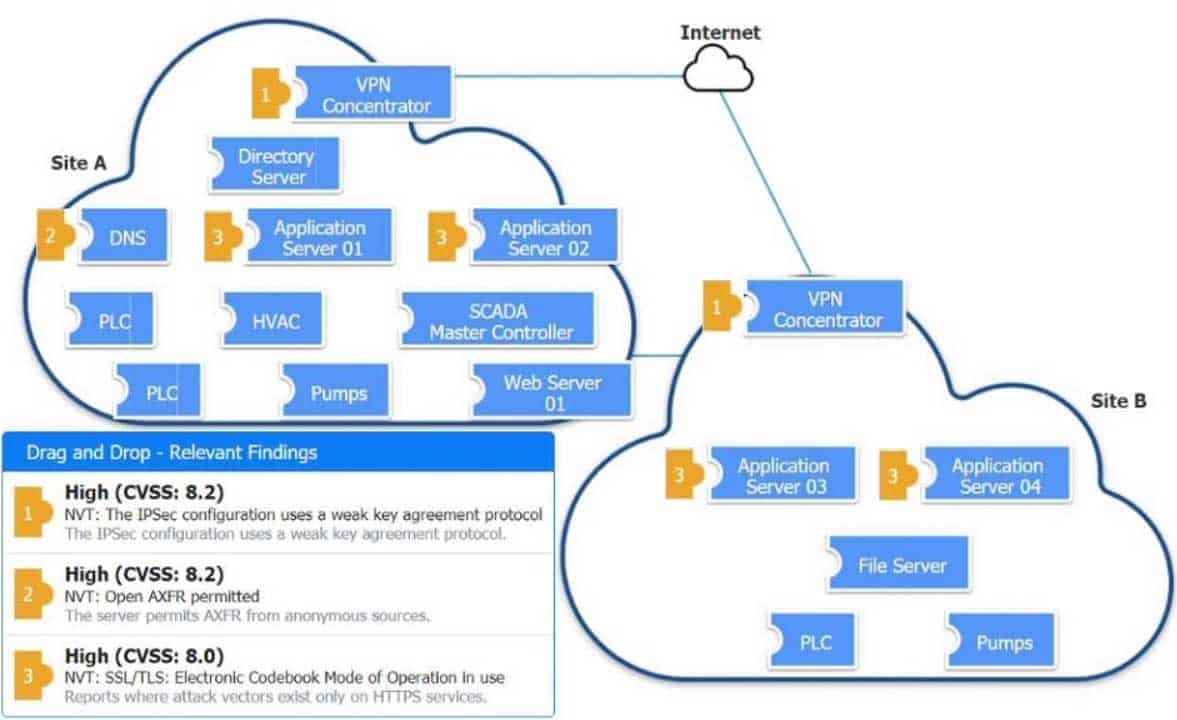
CAS-003 Part 19 Q09 095 Answer -
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from Company A’s privileged network.
The company’s hardening guidelines indicate the following:
– There should be one primary server or service per device.
– Only default ports should be used.
– Non-secure protocols should be disabled.INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
– The IP address of the device
– The primary server or service of the device
– The protocol(s) that should be disabled based on the hardening guidelinesTo select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
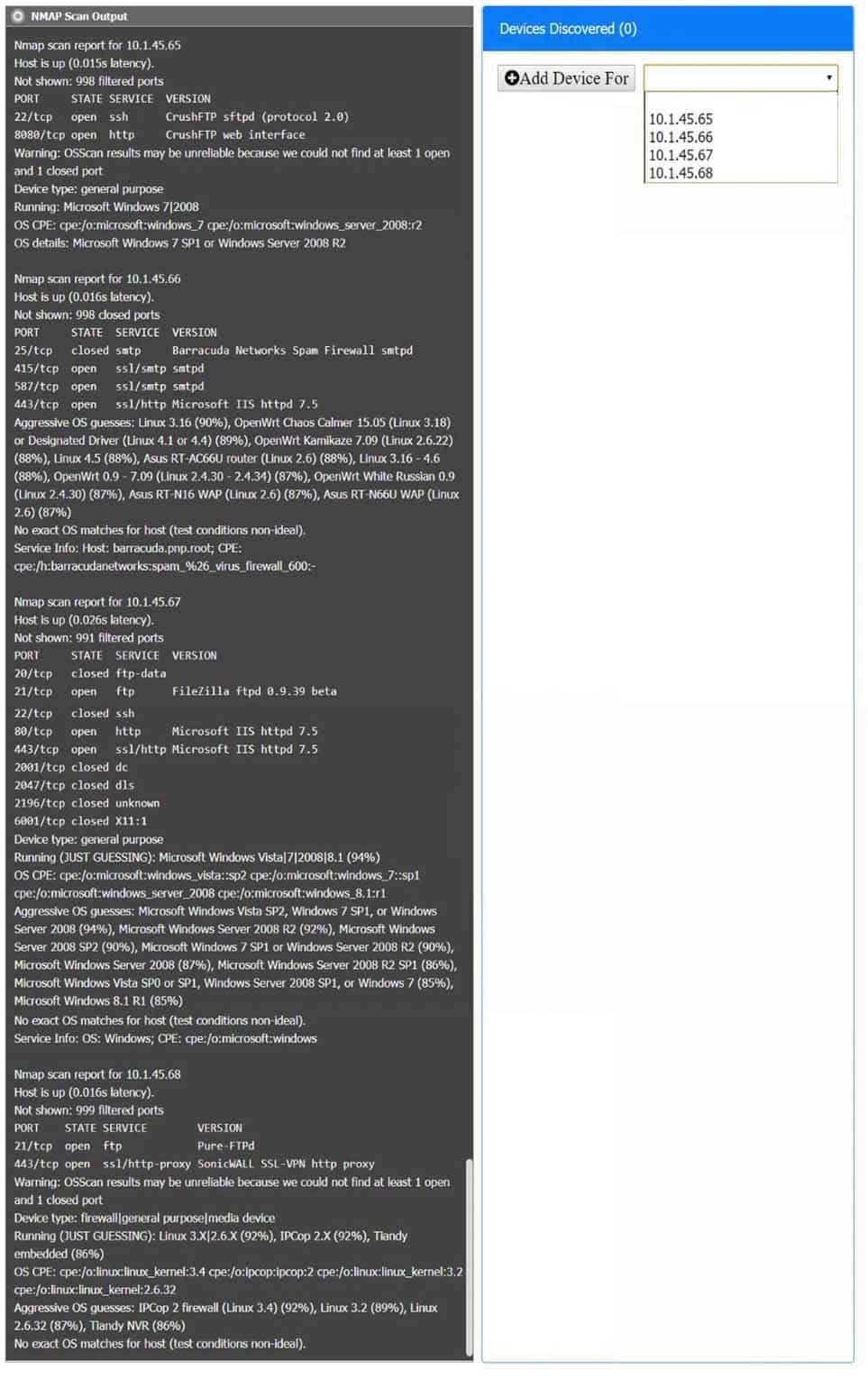
CAS-003 Part 19 Q10 096 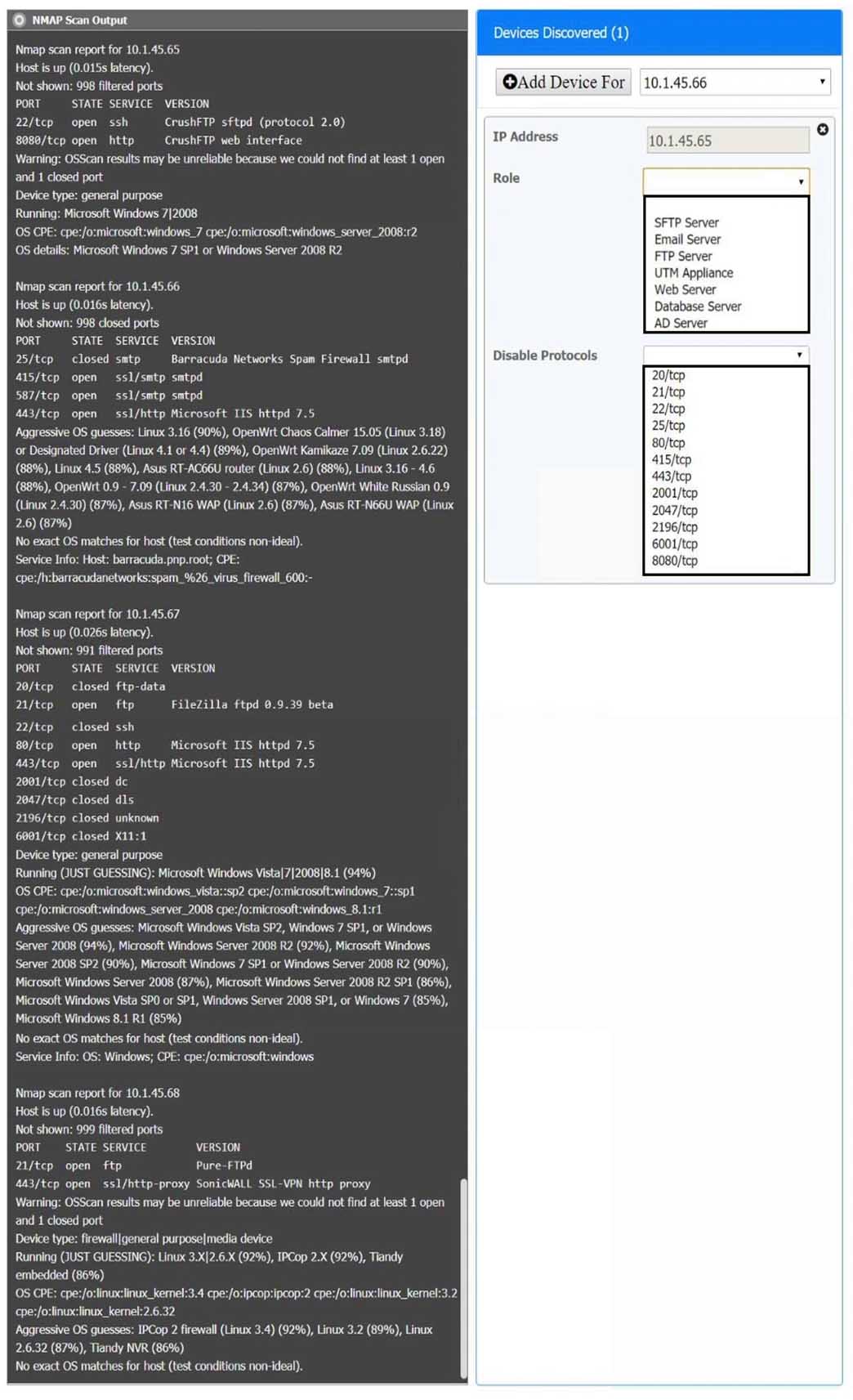
CAS-003 Part 19 Q10 097 - For correct answers: see the explanation below
Explanation:
10.1.45.65 – FTP Server – Disable 8080
10.1.45.66 – Email Serve – Disable 25 and 415
10.1.45.67 – Web Server – Disable 21, 80
10.1.45.68 – UTM Appliance – Disable 21 -
A company has made it a spending priority to implement security architectures that will be resilient during an attack. Recent incidents have involved attackers leveraging latent vulnerabilities in cryptographic implementations and VPN concentrators to be able to compromise sensitive information. Patches have been slowly released for these emergent vulnerabilities, leaving weeks to months of exposed and vulnerable attack surface. Which of the following approaches would be BEST to increase enterprise resilience during similar future attacks?
- Implement appliances and software from diverse manufacturers
- Segment remote VPN users logically from the production LAN
- Maximize open-source software to benefit from swifter patch releases
- Upgrade the cryptographic ciphers used on the VPN concentrators
-
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation-states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
- Software vendor threat reports
- White papers
- Security blogs
- Threat data subscription
-
A security consultant is conducting a penetration test against a customer enterprise that comprises local hosts and cloud-based servers. The hosting service employs a multitenancy model with elastic provisioning to meet customer demand. The customer runs multiple virtualized servers on each provisioned cloud host. The security consultant is able to obtain multiple sets of administrator credentials without penetrating the customer network. Which of the following is the MOST likely risk the tester exploited?
- Data-at-rest encryption misconfiguration and repeated key usage
- Offline attacks against the cloud security broker service
- The ability to scrape data remnants in a multitenancy environment
- VM escape attacks against the customer network hypervisors
-
An application has been through a peer review and regression testing and is prepared for release. A security engineer is asked to analyze an application binary to look for potential vulnerabilities prior to wide release. After thoroughly analyzing the application, the engineer informs the developer it should include additional input sanitation in the application to prevent overflows. Which of the following tools did the security engineer MOST likely use to determine this recommendation?
- Fuzzer
- HTTP interceptor
- Vulnerability scanner
- SCAP scanner
-
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
- Isolate all of the PHI on its own VLAN and keep it segregated at Layer 2
- Take an MD5 hash of the server
- Delete all PHI from the network until the legal department is consulted
- Consult the legal department to determine the legal requirements
-
Users of a newly deployed VoIP solution report multiple instances of dropped or garbled calls. Thirty users connect to the primary site via a site-to-site VPN, and the primary site supplies a dial tone to all satellite locations. The network engineer who installed the equipment copied the configuration from a site that has two users on a low bandwidth DSL connection. Which of the following is MOST likely to restore telephone availability at the 30-user site?
- Disable Layer 2 encryption on the site-to-site VPNs throughout the company
- Provision new firewalls at all sites to enable QoS management of VoIP traffic
- Enable point-to-point tunneling for all VoIP traffic at the new site
- Configure QoS settings to support the larger bandwidth available
- Prioritize ICMP and TCP traffic over UDP traffic using QoS
-
A manufacturing company’s security engineer is concerned a remote actor may be able to access the ICS that is used to monitor the factory lines. The security engineer recently proposed some techniques to reduce the attack surface of the ICS to the Chief Information Security Officer (CISO). Which of the following would BEST track the reductions to show the CISO the engineer’s plan is successful during each phase?
- Conducting tabletop exercises to evaluate system risk
- Contracting a third-party auditor after the project is finished
- Performing pre- and post-implementation penetration tests
- Running frequent vulnerability scans during the project
-
A software development firm wants to validate the use of standard libraries as part of the software development process. Each developer performs unit testing prior to committing changes to the code repository. Which of the following activities would be BEST to perform after a commit but before the creation of a branch?
- Static analysis
- Heuristic analysis
- Dynamic analysis
- Web application vulnerability scanning
- Penetration testing
-
A development team releases updates to an application regularly. The application is compiled with several standard, open-source security products that require a minimum version for compatibility. During the security review portion of the development cycle, which of the following should be done to minimize possible application vulnerabilities?
- The developers should require an exact version of the open-source security products, preventing the introduction of new vulnerabilities.
- The application development team should move to an Agile development approach to identify security concerns faster.
- The change logs for the third-party libraries should be reviewed for security patches, which may need to be included in the release
- The application should eliminate the use of open-source libraries and products to prevent known vulnerabilities from being included
-
An organization’s mobile device inventory recently provided notification that a zero-day vulnerability was identified in the code used to control the baseband of the devices. The device manufacturer is expediting a patch, but the rollout will take several months.
Additionally, several mobile users recently returned from an overseas trip and report their phones now contain unknown applications, slowing device performance. Users have been unable to uninstall these applications, which persist after wiping the devices. Which of the following MOST likely occurred and provides mitigation until the patches are released?
- Unauthentic firmware was installed; disable OTA updates and carrier roaming via MDM
- Users opened a spear-phishing email; disable third-party application stores and validate all signed code prior to execution
- An attacker downloaded monitoring applications; perform a full factory reset of the affected devices
- Users received an improperly encoded emergency broadcast message, leading to an integrity loss condition; disable emergency broadcast messages