CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 20
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 20
-
Users have reported that an internally developed web application is acting erratically, and the response output is inconsistent. The issue began after a web application dependency patch was applied to improve security. Which of the following would be the MOST appropriate tool to help identify the issue?
- Fuzzer
- SCAP scanner
- Vulnerability scanner
- HTTP interceptor
-
A developer has executed code for a website that allows users to search for employees’ phone numbers by last name. The query string sent by the browser is as follows:
http://www.companywebsite.com/search.php?q=SMITH
The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement NEXT to prevent XSS? (Choose two.)
- Sanitization library
- Secure cookies
- TLS encryption
- Input serialization
- Output encoding
- PUT form submission
-
A secure facility has a server room that currently is controlled by a simple lock and key, and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators’ smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are:
– It cannot be invasive to the end user.
– It must be utilized as a second factor.
– Information sharing must be avoided.
– It must have a low false acceptance rate.
Which of the following BEST meets the criteria?
- Facial recognition
- Swipe pattern
- Fingerprint scanning
- Complex passcode
- Token card
-
An employee decides to log into an authorized system. The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
- Memory leak
- Race condition
- Smurf
- Resource exhaustion
-
A small firm’s newly created website has several design flaws. The developer created the website to be fully compatible with ActiveX scripts in order to use various digital certificates and trusting certificate authorities. However, vulnerability testing indicates sandboxes were enabled, which restricts the code’s access to resources within the user’s computer. Which of the following is the MOST likely cause of the error?
- The developer inadvertently used Java applets
- The developer established a corporate account with a non-reputable certification authority
- The developer used fuzzy logic to determine how the web browser would respond once ports 80 and 443 were both open
- The developer did not consider that mobile code would be transmitted across the network
-
An organization based in the United States is planning to expand its operations into the European market later in the year. Legal counsel is exploring the additional requirements that must be established as a result of the expansion. The BEST course of action would be to:
- revise the employee provisioning and deprovisioning procedures
- complete a quantitative risk assessment
- draft a memorandum of understanding
- complete a security questionnaire focused on data privacy
-
Several days after deploying an MDM for smartphone control, an organization began noticing anomalous behavior across the enterprise. Security analysts observed the following:
– Unauthorized certificate issuance
– Access to mutually authenticated resources utilizing valid but unauthorized certificates
– Granted access to internal resources via the SSL VPNTo address the immediate problem, security analysts revoked the erroneous certificates. Which of the following describes the MOST likely root cause of the problem and offers a solution?
- The VPN and web resources are configured with too weak a cipher suite and should be rekeyed to support AES 256 in GCM and ECC for digital signatures and key exchange.
- A managed mobile device is rooted, exposing its keystore, and the MDM should be reconfigured to wipe these devices and disallow access to corporate resources.
- SCEP is configured insecurely, which should be enabled for device onboarding against a PKI for mobile-exclusive use.
- The CA is configured to sign any received CSR from mobile users and should be reconfigured to permit CSR signings only from domain administrators.
-
Confidential information related to Application A, Application B, and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:
Group Name: product-updates-application-a Members: administrator, app-support, dev-ops, jdoe, jsmith, mpeters
Group Name: pending-bug-fixes-application-a Members: administrator, app-support, dev-ops, jsmith, jdoe, mpeters, rwilliams
Group Name: inflight-updates-application-b Members: app-support, dev-ops, jdoe, nbrown, jsmith
Group Name: PoC-project-x Members: dev-support, product-mgt, jsmith, nbrown, rwilliams
Which of the following actions should the IR team take FIRST?
- Remove all members from the distribution groups immediately
- Place the mailbox for jsmith on legal hold
- Implement a proxy server on the network to inspect all outbound SMTP traffic for the DevOps group
- Install DLP software on all developer laptops to prevent data from leaving the network
-
A security analyst receives an email from a peer that includes a sample of code from a piece of malware found in an application running in the organization’s staging environment. During the incident response process, it is determined the code was introduced into the environment as a result of a compromised laptop being used to harvest credentials and access the organization’s code repository. While the laptop itself was not used to access the code repository, an attacker was able to leverage the harvested credentials from another system in the development environment to bypass the ACLs limiting access to the repositories. Which of the following controls MOST likely would have interrupted the kill chain in this attack?
- IP whitelisting on the perimeter firewall
- MFA for developer access
- Dynamic analysis scans in the production environment
- Blue team engagement in peer-review activities
- Time-based restrictions on developer access to code repositories
-
A SaaS provider decides to offer data storage as a service. For simplicity, the company wants to make the service available over industry standard APIs, routable over the public Internet. Which of the following controls offers the MOST protection to the company and its customer’s information?
- Detailed application logging
- Use of non-standard ports
- Web application firewall
- Multifactor authentication
-
A new employee is plugged into the network on a BYOD machine but cannot access the network. Which of the following must be configured so the employee can connect to the network?
- Port security
- Firewall
- Remote access
- VPN
-
After analyzing code, two developers at a company bring these samples to the security operations manager:

CAS-003 Part 20 Q12 098 Which of the following would BEST solve these coding problems?
- Use a privileged access management system
- Prompt the administrator for the password
- Use salted hashes with PBKDF2
- Increase the complexity and length of the password
-
A researcher is working to identify what appears to be a new variant of an existing piece of malware commonly used in ransomware attacks. While it is not identical to the malware previously evaluated, it has a number of similarities including language, payload, and algorithms. Which of the following would help the researcher safely compare the code base of the two variants?
- Virtualized sandbox
- Vulnerability scanner
- Software-defined network
- HTTP interceptor
-
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created:
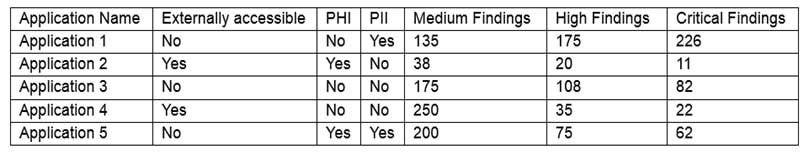
CAS-003 Part 20 Q14 099 The findings are then categorized according to the following chart:
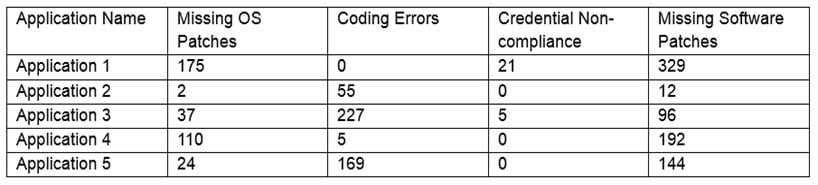
CAS-003 Part 20 Q14 100 Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Choose two.)
- Place a WAF in line with Application 2
- Move Application 3 to a secure VLAN and require employees to use a jump server for access
- Apply the missing OS and software patches to the server hosting Application 4
- Use network segmentation and ACLs to control access to Application 5
- Implement an IDS/IPS on the same network segment as Application 3
- Install a FIM on the server hosting Application 4
- Enforce Group Policy password complexity rules on the server hosting Application 1
-
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
- Internal data integrity standards and outsourcing contracts and partnerships
- Data ownership, internal data classification, and risk profiling of outsourcers
- Company audit functions, cross-boarding jurisdictional challenges, and export controls
- Data privacy regulations, data sovereignty, and third-party providers
-
A company wants to implement a cloud-based security solution that will sinkhole malicious DNS requests. The security administrator has implemented technical controls to direct DNS requests to the cloud servers but wants to extend the solution to all managed and unmanaged endpoints that may have user-defined DNS manual settings. Which of the following should the security administrator implement to ensure the solution will protect all connected devices?
-
Implement firewall ACLs as follows: PERMIT UDP ANY CLOUD_SERVER EQ 53 DENY UDP ANY ANY EQ 53
- Implement NAT as follows:
CAS-003 Part 20 Q16 101 -
Implement DHCP options as follows: DHCP DNS1: CLOUD_SERVER1 DHCP DNS2: CLOUD_SERVER2
-
Implement policy routing as follows: 100 PERMIT UDP ANY ANY ANY 53 200 PERMIT UDP PAT_POOL ANY CLOUD_SERVER 53 IP ROUTE_MAP 200 200
-
-
A systems administrator recently conducted a vulnerability scan of the intranet. Subsequently, the organization was successfully attacked by an adversary. Which of the following is the MOST likely explanation for why the organization’s network was compromised?
- There was a false positive since the network was fully patched
- The systems administrator did not perform a full system scan
- The systems administrator performed a credentialed scan
- The vulnerability database was not updated
-
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrator captures an attempted authentication and discovers the following being presented by the user’s VPN client:
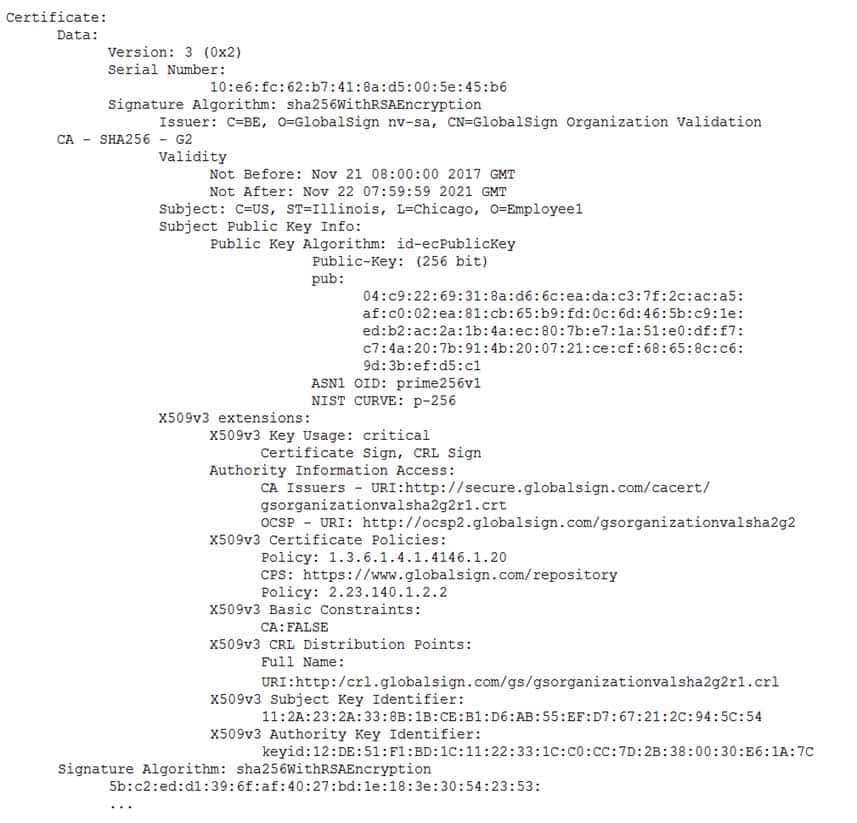
CAS-003 Part 20 Q18 102 Which of the following BEST describes the reason the user is unable to connect to the VPN service?
- The user’s certificate is not signed by the VPN service provider
- The user’s certificate has been compromised and should be revoked
- The user’s certificate was not created for VPN use
- The user’s certificate was created using insecure encryption algorithms
-
A large, multinational company currently has two separate databases. One is used for ERP, while the second is used for CRM. To consolidate services and infrastructure, it is proposed to combine the databases. The company’s compliance manager is asked to review the proposal and is concerned about this integration. Which of the following would pose the MOST concern to the compliance manager?
- The attack surface of the combined database is lower than the previous separate systems, so there likely are wasted resources on additional security controls that will not be needed.
- There are specific regulatory requirements the company might be violating by combining these two types of services into one shared platform.
- By consolidating services in this manner, there is an increased risk posed to the organization due to the number of resources required to manage the larger data pool.
- Auditing the combined database structure will require more short-term resources, as the new system will need to be learned by the auditing team to ensure all security controls are in place.
-
The Chief Executive Officer (CEO) of a company has considered implementing a cost-saving measure that might result in new risk to the company. When deciding whether to implement this measure, which of the following would be the BEST course of action to manage the organization’s risk?
- Present the detailed risk resulting from the change to the company’s board of directors
- Pilot new mitigations that cost less than the total amount saved by the change
- Modify policies and standards to discourage future changes that increase risk
- Capture the risk in a prioritized register that is shared routinely with the CEO