CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 21
CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 21
-
A security engineer is looking at a DNS server following a known incident. The engineer sees the following command as the most recent entry in the server’s shell history:
dd if=dev/sda of=/dev/sdb
Which of the following MOST likely occurred?
- A tape backup of the server was performed
- The drive was cloned for forensic analysis
- The hard drive was formatted after the incident
- The DNS log files were rolled daily as expected
-
Designing a system in which only information that is essential for a particular job task is allowed to be viewed can be accomplished successfully by using:
- mandatory vacations
- job rotations
- role-based access control
- discretionary access
- separation of duties
-
The information security manager of an e-commerce company receives an alert over the weekend that all the servers in a datacenter have gone offline. Upon discussing this situation with the facilities manager, the information security manager learns there was planned electrical maintenance. The information security manager is upset at not being part of the maintenance planning, as this could have resulted in a loss of:
- data confidentiality
- data security
- PCI compliance
- business availability
-
The Chief Executive Officer (CEO) of a small company decides to use cloud computing to host critical corporate data for protection from natural disasters. The recommended solution is to adopt the public cloud for its cost savings. If the CEO insists on adopting the public cloud model, which of the following would be the BEST advice?
- Ensure the cloud provider supports a secure virtual desktop infrastructure
- Ensure the colocation facility implements a robust DRP to help with business continuity planning
- Ensure the on-premises datacenter employs fault tolerance and load balancing capabilities
- Ensure the ISP is using a standard help-desk ticketing system to respond to any system outages
-
The Chief Financial Officer (CFO) of an organization wants the IT department to add the CFO’s account to the domain administrator group. The IT department thinks this is risky and wants support from the security manager before proceeding. Which of the following BEST supports the argument against providing the CFO with domain administrator access?
- Discretionary access control
- Separation of duties
- Data classification
- Mandatory access control
-
An attacker has been compromising banking institution targets across a regional area. The Chief Information Security Officer (CISO) at a local bank wants to detect and prevent an attack before the bank becomes a victim. Which of the following actions should the CISO take?
- Utilize cloud-based threat analytics to identify anomalous behavior in the company’s B2B and vendor traffic
- Purchase a CASB solution to identify and control access to cloud-based applications and services and integrate them with on-premises legacy security monitoring
- Instruct a security engineer to configure the IDS to consume threat intelligence feeds from an information-sharing association in the banking sector
- Attend and present at the regional banking association lobbying group meetings each month and facilitate a discussion on the topic
-
An organization is integrating an ICS and wants to ensure the system is cyber resilient. Unfortunately, many of the specialized components are legacy systems that cannot be patched. The existing enterprise consists of mission-critical systems that require 99.9% uptime. To assist in the appropriate design of the system given the constraints, which of the following MUST be assumed?
- Vulnerable components
- Operational impact due to attack
- Time critically of systems
- Presence of open-source software
-
A video-game developer has received reports of players who are cheating. All game players each have five capabilities that are ranked on a scale of 1 to 10 points, with 10 total points available for balance. Players can move these points between capabilities at any time. The programming logic is as follows:
– A player asks to move points from one capability to another.
– The source capability must have enough points to allow the move.
– The destination capability must not exceed 10 after the move.
– The move from source capability to destination capability is then completed.The time stamps of the game logs show each step of the transfer process takes about 900ms. However, the time stamps of the cheating players show capability transfers at the exact same time. The cheating players have 10 points in multiple capabilities. Which of the following is MOST likely being exploited to allow these capability transfers?
- TOC/TOU
- CSRF
- Memory leak
- XSS
- SQL injection
- Integer overflow
-
A security administrator receives reports that several workstations are unable to access resources within one network segment. A packet capture shows the segment is flooded with ICMPv6 traffic from the source fe80::21ae:4571:42ab:1fdd and for the destination ff02::1. Which of the following should the security administrator integrate into the network to help prevent this from occurring?
- Raise the dead peer detection interval to prevent the additional network chatter
- Deploy honeypots on the network segment to identify the sending machine
- Ensure routers will use route advertisement guards
- Deploy ARP spoofing prevention on routers and switches
-
A Chief Information Security Officer (CISO) has created a survey that will be distributed to managers of mission-critical functions across the organization. The survey requires the managers to determine how long their respective units can operate in the event of an extended IT outage before the organization suffers monetary losses from the outage. To which of the following is the survey question related? (Choose two.)
- Risk avoidance
- Business impact
- Risk assessment
- Recovery point objective
- Recovery time objective
- Mean time between failures
-
A security engineer discovers a PC may have been breached and accessed by an outside agent. The engineer wants to find out how this breach occurred before remediating the damage. Which of the following should the security engineer do FIRST to begin this investigation?
- Create an image of the hard drive
- Capture the incoming and outgoing network traffic
- Dump the contents of the RAM
- Parse the PC logs for information on the attacker
-
An internal penetration tester finds a legacy application that takes measurement input made in a text box and outputs a specific string of text related to industry requirements. There is no documentation about how this application works, and the source code has been lost. Which of the following would BEST allow the penetration tester to determine the input and output relationship?
- Running an automated fuzzer
- Constructing a known cipher text attack
- Attempting SQL injection commands
- Performing a full packet capture
- Using the application in a malware sandbox
-
A network service on a production system keeps crashing at random times. The systems administrator suspects a bug in the listener is causing the service to crash, resulting in a DoS. When the service crashes, a core dump is left in the /tmp directory. Which of the following tools can the systems administrator use to reproduce these symptoms?
- Fuzzer
- Vulnerability scanner
- Core dump analyzer
- Debugger
-
A company is deploying a DLP solution and scanning workstations and network drives for documents that contain potential PII and payment card data. The results of the first scan are as follows:
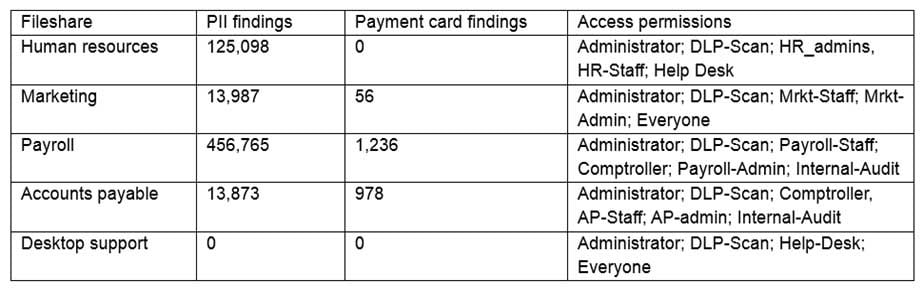
CAS-003 Part 21 Q14 103 The security team is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
- Move the files from the marketing share to a secured drive
- Search the metadata for each file to locate the file’s creator and transfer the files to the personal drive of the listed creator
- Configure the DLP tool to delete the files on the shared drives
- Remove the access for the internal audit group from the accounts payable and payroll shares
-
A hospital is using a functional magnetic resonance imaging (fMRI) scanner, which is controlled by a legacy desktop connected to the network. The manufacturer of the fMRI will not support patching of the legacy system. The legacy desktop needs to be network accessible on TCP port 445. A security administrator is concerned the legacy system will be vulnerable to exploits. Which of the following would be the BEST strategy to reduce the risk of an outage while still providing for security?
- Install HIDS and disable unused services
- Enable application whitelisting and disable SMB
- Segment the network and configure a controlled interface
- Apply only critical security patches for known vulnerabilities
-
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
- Penetration tests
- Vulnerability assessment
- Tabletop exercises
- Blue-team operations
-
While an employee is on vacation, suspicion arises that the employee has been involved in malicious activity on the network. The security engineer is concerned the investigation may need to continue after the employee returns to work. Given this concern, which of the following should the security engineer recommend to maintain the integrity of the investigation?
- Create archival copies of all documents and communications related to the employee
- Create a forensic image of network infrastructure devices
- Create an image file of the employee’s network drives and store it with hashes
- Install a keylogger to capture the employee’s communications and contacts
-
A company wants to secure a newly developed application that is used to access sensitive information and data from corporate resources. The application was developed by a third-party organization, and it is now being used heavily, despite lacking the following controls:
– Certificate pinning
– Tokenization
– Biometric authenticationThe company has already implemented the following controls:
– Full device encryption
– Screen lock
– Device password
– Remote wipeThe company wants to defend against interception of data attacks. Which of the following compensating controls should the company implement NEXT?
- Enforce the use of a VPN when using the newly developed application
- Implement a geofencing solution that disables the application according to company requirements
- Implement an out-of-band second factor to authenticate authorized users
- Install the application in a secure container requiring additional authentication controls
-
A product owner is reviewing the output of a web-application penetration test and has identified an application that is presenting sensitive information in cleartext on a page. Which of the following code snippets would be BEST to use to remediate the vulnerability?
-

CAS-003 Part 21 Q19 104 - <asp:TextBox ID=”txtACCT” TabIndex=”6” runat=”server” Width=”206px” MaxLength=”11” TextMode=”Password”></asp:TextBox>
-
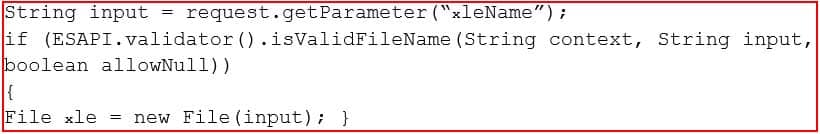
CAS-003 Part 21 Q19 105 - Query hqlQuery = session.createQuery(“select transaction from Accounts as orders where acct.id =?”);
List results = hqlQuery.setString(0,”122-ACC-988-QTWYTFDL”).list();
-
-
A company is concerned about disgruntled employees transferring its intellectual property data through covert channels. Which of the following tools would allow employees to write data into ICMP echo response packets?
- Thor
- Jack the Ripper
- Burp Suite
- Loki