CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 03
CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 03
-
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not capable of escaping the virtual machines and pivoting to other networks.
To BEST mitigate this risk, the analyst should use __________.
- an 802.11ac wireless bridge to create an air gap.
- a managed switch to segment the lab into a separate VLAN.
- a firewall to isolate the lab network from all other networks.
- an unmanaged switch to segment the environments from one another.
-
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organization’s financial assets.
Which of the following is the BEST example of the level of sophistication this threat actor is using?
- Social media accounts attributed to the threat actor
- Custom malware attributed to the threat actor from prior attacks
- Email addresses and phone numbers tied to the threat actor
- Network assets used in previous attacks attributed to the threat actor
- IP addresses used by the threat actor for command and control
-
Bootloader malware was recently discovered on several company workstations. All the workstations run Windows and are current models with UEFI capability.
Which of the following UEFI settings is the MOST likely cause of the infections?
- Compatibility mode
- Secure boot mode
- Native mode
- Fast boot mode
-
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives:
– Reduce the number of potential findings by the auditors.
– Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations.
– Prevent the external-facing web infrastructure used by other teams from coming into scope.
– Limit the amount of exposure the company will face if the systems used by the payment-processing team are compromised.Which of the following would be the MOST effective way for the security team to meet these objectives?
- Limit the permissions to prevent other employees from accessing data owned by the business unit.
- Segment the servers and systems used by the business unit from the rest of the network.
- Deploy patches to all servers and workstations across the entire organization.
- Implement full-disk encryption on the laptops used by employees of the payment-processing team.
-
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period:
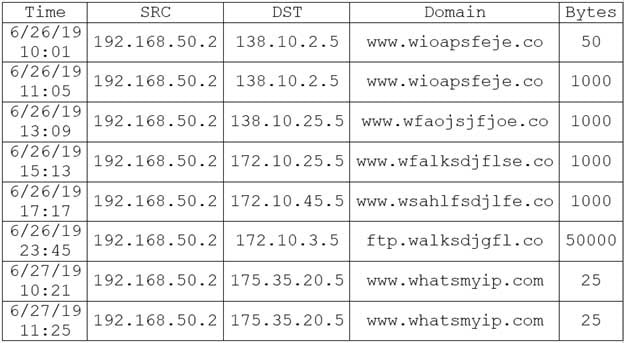
CS0-002 Part 03 Q05 010 To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
- DST 138.10.2.5.
- DST 138.10.25.5.
- DST 172.10.3.5.
- DST 172.10.45.5.
- DST 175.35.20.5.
-
For machine learning to be applied effectively toward security analysis automation, it requires __________.
- relevant training data.
- a threat feed API.
- a multicore, multiprocessor system.
- anomalous traffic signatures.
-
A large amount of confidential data was leaked during a recent security breach. As part of a forensic investigation, the security team needs to identify the various types of traffic that were captured between two compromised devices.
Which of the following should be used to identify the traffic?
- Carving
- Disk imaging
- Packet analysis
- Memory dump
- Hashing
-
Which of the following sets of attributes BEST illustrates the characteristics of an insider threat from a security perspective?
- Unauthorized, unintentional, benign
- Unauthorized, intentional, malicious
- Authorized, intentional, malicious
- Authorized, unintentional, benign
-
A security analyst has observed several incidents within an organization that are affecting one specific piece of hardware on the network. Further investigation reveals the equipment vendor previously released a patch.
Which of the following is the MOST appropriate threat classification for these incidents?
- Known threat
- Zero day
- Unknown threat
- Advanced persistent threat
-
An incident responder successfully acquired application binaries off a mobile device for later forensic analysis.
Which of the following should the analyst do NEXT?
- Decompile each binary to derive the source code.
- Perform a factory reset on the affected mobile device.
- Compute SHA-256 hashes for each binary.
- Encrypt the binaries using an authenticated AES-256 mode of operation.
- Inspect the permissions manifests within each application.
-
A security analyst needs to reduce the overall attack surface.
Which of the following infrastructure changes should the analyst recommend?
- Implement a honeypot.
- Air gap sensitive systems.
- Increase the network segmentation.
- Implement a cloud-based architecture.
-
A security analyst is reviewing the following log from an email security service.
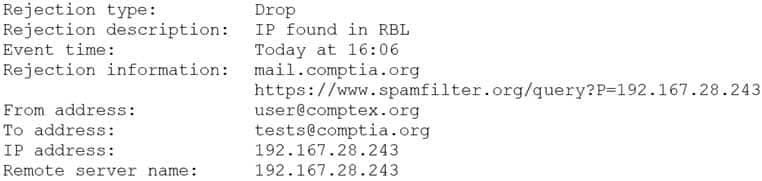
CS0-002 Part 03 Q12 011 Which of the following BEST describes the reason why the email was blocked?
- The To address is invalid.
- The email originated from the www.spamfilter.org URL.
- The IP address and the remote server name are the same.
- The IP address was blacklisted.
- The From address is invalid.
-
A user’s computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
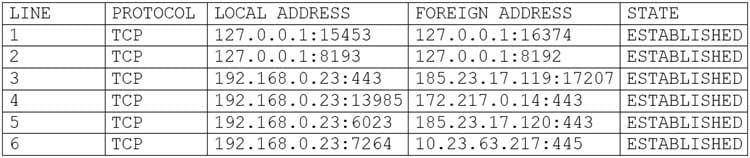
CS0-002 Part 03 Q13 012 Which of the following lines indicates the computer may be compromised?
- Line 1
- Line 2
- Line 3
- Line 4
- Line 5
- Line 6
-
As part of an exercise set up by the information security officer, the IT staff must move some of the network systems to an off-site facility and redeploy them for testing. All staff members must ensure their respective systems can power back up and match their gold image. If they find any inconsistencies, they must formally document the information.
Which of the following BEST describes this test?
- Walk through
- Full interruption
- Simulation
- Parallel
-
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful authentication, the user is then redirected back to the original page. Some users have reported receiving phishing emails with a link that takes them to the application login page but then redirects to a fake login page after successful authentication.
Which of the following will remediate this software vulnerability?
- Enforce unique session IDs for the application.
- Deploy a WAF in front of the web application.
- Check for and enforce the proper domain for the redirect.
- Use a parameterized query to check the credentials.
- Implement email filtering with anti-phishing protection.
-
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too much access to customer data. Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO’s concern?
- DLP
- Encryption
- Test data
- NDA
-
A company was recently awarded several large government contracts and wants to determine its current risk from one specific APT.
Which of the following threat modeling methodologies would be the MOST appropriate to use during this analysis?
- Attack vectors
- Adversary capability
- Diamond Model of Intrusion Analysis
- Kill chain
- Total attack surface
-
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having outdated antivirus signatures. The analyst observes the following plugin output:
Antivirus is installed on the remote host: Installation path: C:\Program Files\AVProduct\Win32\ Product Engine: 14.12.101 Engine Version: 3.5.71 Scanner does not currently have information about AVProduct version 3.5.71. It may no longer be supported. The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor’s website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
- This is a false positive, and the scanning plugin needs to be updated by the vendor.
- This is a true negative, and the new computers have the correct version of the software.
- This is a true positive, and the new computers were imaged with an old version of the software.
- This is a false negative, and the new computers need to be updated by the desktop team.
-
A SIEM solution alerts a security analyst of a high number of login attempts against the company’s webmail portal. The analyst determines the login attempts used credentials from a past data breach.
Which of the following is the BEST mitigation to prevent unauthorized access?
- Single sign-on
- Mandatory access control
- Multifactor authentication
- Federation
- Privileged access management
-
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
- The use of infrastructure-as-code capabilities leads to an increased attack surface.
- Patching the underlying application server becomes the responsibility of the client.
- The application is unable to use encryption at the database level.
- Insecure application programming interfaces can lead to data compromise.