CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 04
CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 04
-
Because some clients have reported unauthorized activity on their accounts, a security analyst is reviewing network packet captures from the company’s API server. A portion of a capture file is shown below:
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.s/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/"> <request+xmlns:a="http://schemas.somesite.org"+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"></s:Body></s:Envelope> 192.168.1.22 - - api.somesite.com 200 0 1006 1001 0 192.168.1.22
POST /services/v1_0/Public/Members.svc/soap <<a:Password>Password123</a:Password><a:ResetPasswordToken+i:nil="true"/> <a:ShouldImpersonatedAuthenticationBePopulated+i:nil="true"/><a:Username>somebody@companyname.com</a:Username></request></Login></s:Body></s:Envelope> 192.168.5.66 - - api.somesite.com 200 0 11558 1712 2024 192.168.4.89
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/"> <a:IPAddress>516.7.446.605</a:IPAddress><a:ZipCode+i:nil="true"/></request></GetIPLocation></s:Body></s:Envelope> 192.168.1.22 - - api.somesite.com 200 0 1003 1011 307 192.168.1.22
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><IsLoggedIn+xmlns="http://tempuri.org/"> <request+xmlns:a="http://schemas.datacontract.org/2004/07/somesite.web+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"><a:Authentication> <a:ApiToken>kmL4krg2CwwWBan5BReGv5Djb7syxXTNKcWFuSjd</a:ApiToken><a:ImpersonateUserId>0</a:ImpersonateUserId><a:LocationId>161222</a:LocationId> <a:NetworkId>4</a:NetworkId><a:ProviderId>''1=1</a:ProviderId><a:UserId>13026046</a:UserId></a:Authentication></request></IsLoggedIn></s:Body></s:Envelope> 192.168.5.66 - - api.somesite.com 200 0 1378 1209 48 192.168.4.89
Which of the following MOST likely explains how the clients’ accounts were compromised?
- The clients’ authentication tokens were impersonated and replayed.
- The clients’ usernames and passwords were transmitted in cleartext.
- An XSS scripting attack was carried out on the server.
- A SQL injection attack was carried out on the server.
-
A monthly job to install approved vendor software updates and hot fixes recently stopped working. The security team performed a vulnerability scan, which identified several hosts as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and exposures (CVE) database.
Which of the following should the security team do NEXT to resolve the critical findings in the most effective manner? (Choose two.)
- Patch the required hosts with the correct updates and hot fixes, and rescan them for vulnerabilities.
- Remove the servers reported to have high and medium vulnerabilities.
- Tag the computers with critical findings as a business risk acceptance.
- Manually patch the computers on the network, as recommended on the CVE website.
- Harden the hosts on the network, as recommended by the NIST framework.
- Resolve the monthly job issues and test them before applying them to the production network.
-
A development team is testing a new application release. The team needs to import existing client PHI data records from the production environment to the test environment to test accuracy and functionality.
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
- Deidentification
- Encoding
- Encryption
- Watermarking
-
A network attack that is exploiting a vulnerability in the SNMP is detected.
Which of the following should the cybersecurity analyst do FIRST?
- Apply the required patches to remediate the vulnerability.
- Escalate the incident to senior management for guidance.
- Disable all privileged user accounts on the network.
- Temporarily block the attacking IP address.
-
An organization is moving its infrastructure to the cloud in an effort to meet the budget and reduce staffing requirements. The organization has three environments: development, testing, and production. These environments have interdependencies but must remain relatively segmented.
Which of the following methods would BEST secure the company’s infrastructure and be the simplest to manage and maintain?
- Create three separate cloud accounts for each environment. Configure account peering and security rules to allow access to and from each environment.
- Create one cloud account with one VPC for all environments. Purchase a virtual firewall and create granular security rules.
- Create one cloud account and three separate VPCs for each environment. Create security rules to allow access to and from each environment.
- Create three separate cloud accounts for each environment and a single core account for network services. Route all traffic through the core account.
-
A pharmaceutical company’s marketing team wants to send out notifications about new products to alert users of recalls and newly discovered adverse drug reactions. The team plans to use the names and mailing addresses that users have provided.
Which of the following data privacy standards does this violate?
- Purpose limitation
- Sovereignty
- Data minimization
- Retention
-
A user receives a potentially malicious email that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review.
Which of the following commands would MOST likely indicate if the email is malicious?
-
sha256sum ~/Desktop/file.pdf -
file ~/Desktop/file.pdf
-
strings ~/Desktop/file.pdf | grep "<script"
-
cat < ~/Desktop/file.pdf | grep -i .exe
-
-
A development team signed a contract that requires access to an on-premises physical server. Access must be restricted to authorized users only and cannot be connected to the Internet.
Which of the following solutions would meet this requirement?
- Establish a hosted SSO.
- Implement a CASB.
- Virtualize the server.
- Air gap the server.
-
SIMULATION
You are a cybersecurity analyst tasked with interpreting scan data from Company A’s servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company’s hardening guidelines indicate the following:
• TLS 1.2 is the only version of TLS running.
• Apache 2.4.18 or greater should be used.
• Only default ports should be used.INSTRUCTIONS
Using the supplied data, record the status of compliance with the company’s guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.

CS0-002 Part 04 Q09 013 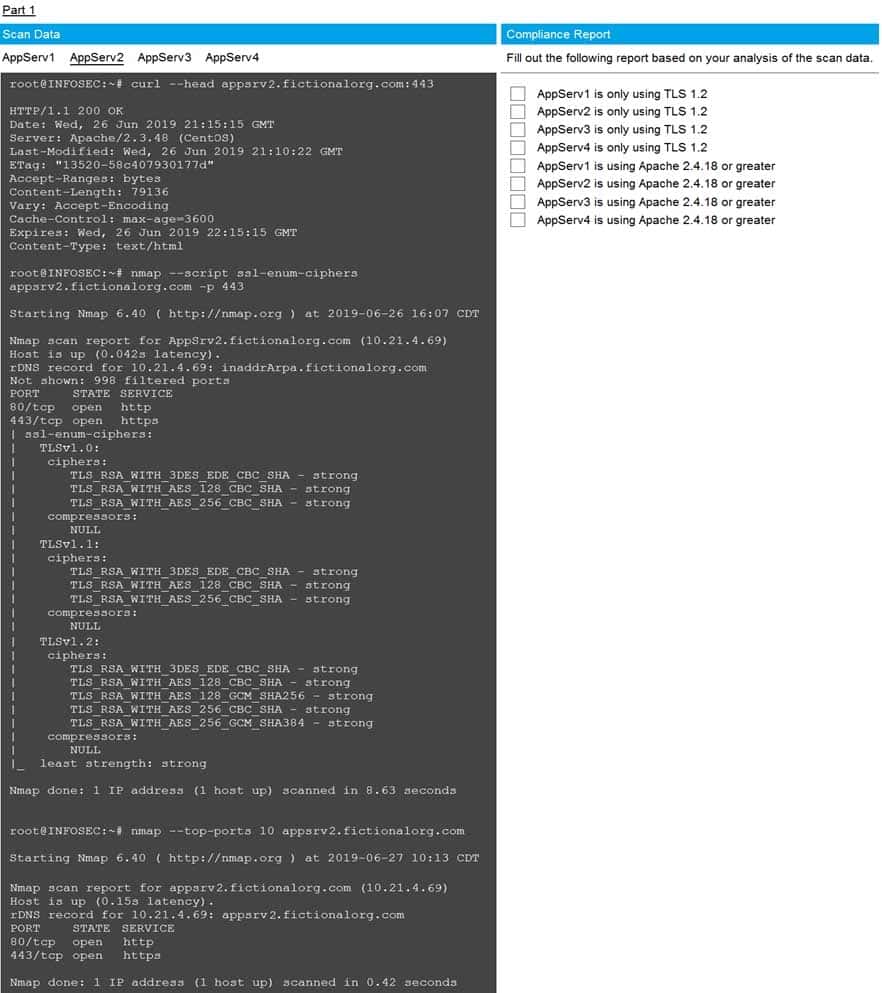
CS0-002 Part 04 Q09 014 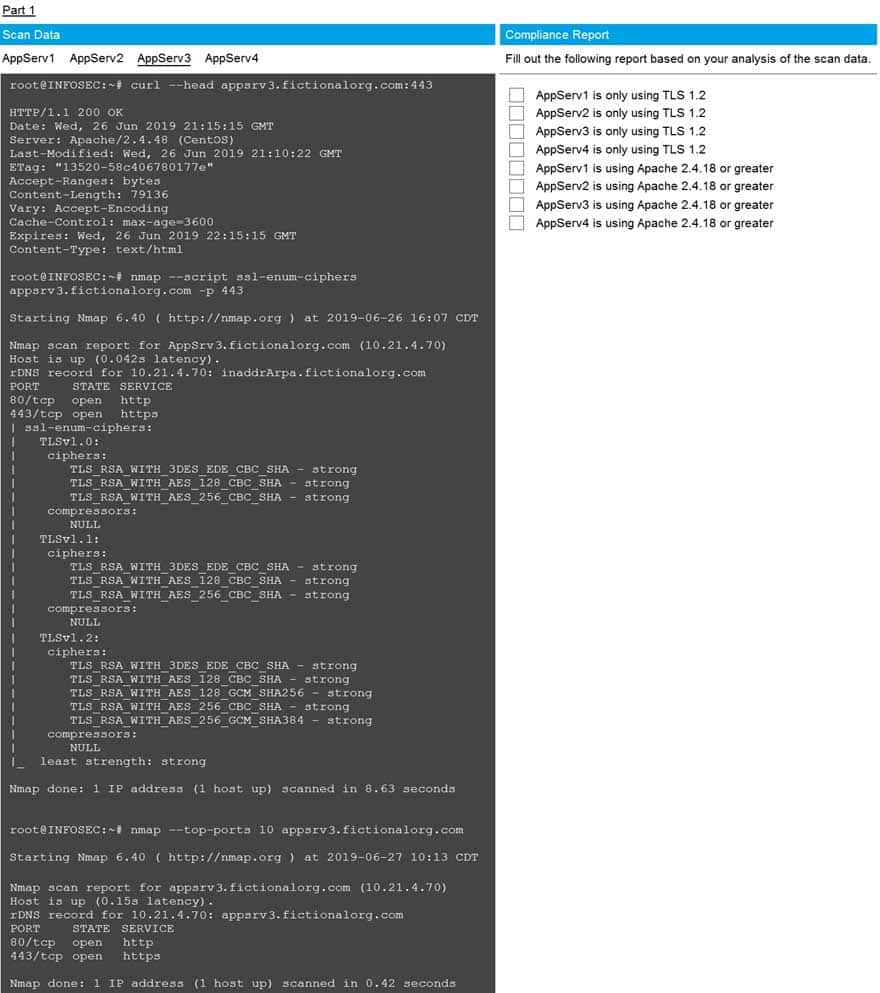
CS0-002 Part 04 Q09 015 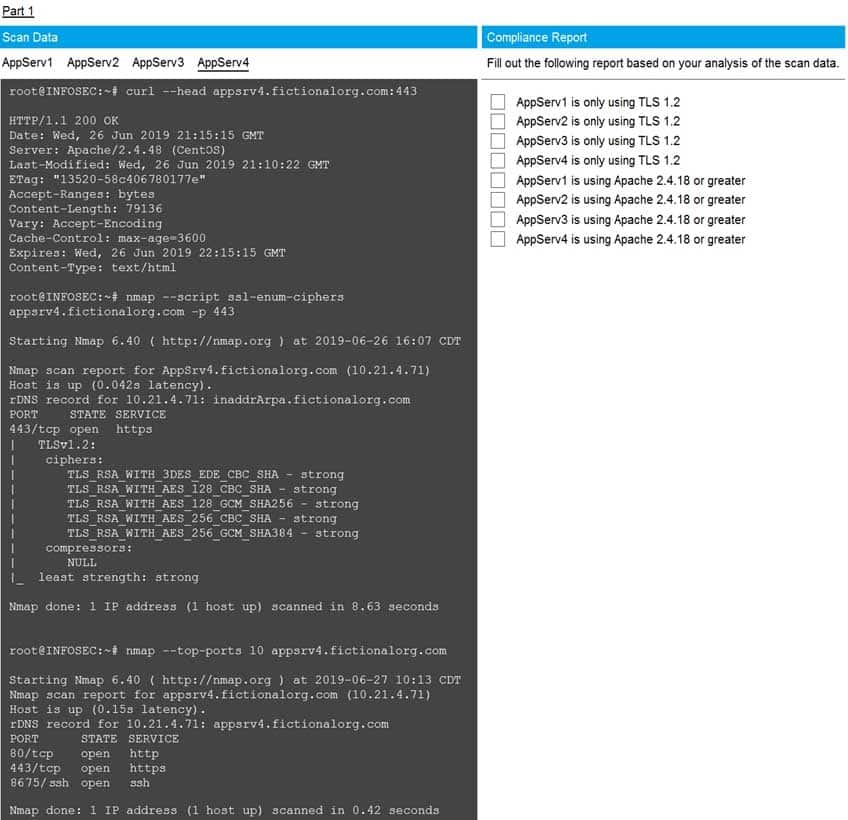
CS0-002 Part 04 Q09 016 
CS0-002 Part 04 Q09 017 - See explanation below.
Explanation:
Part 1 Answer:
Check on the following:
AppServ1 is only using TLS.1.2
AppServ4 is only using TLS.1.2
AppServ1 is using Apache 2.4.18 or greater
AppServ3 is using Apache 2.4.18 or greater
AppServ4 is using Apache 2.4.18 or greater
Part 2 answer:
Recommendation:
Recommendation is to disable TLS v1.1 on AppServ2 and AppServ3. Also upgrade AppServ2 Apache to version 2.4.48 from its current version of 2.3.48
-
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
-
nmap –sA –O <system> -noping
-
nmap –sT –O <system> -P0
-
nmap –sS –O <system> -P0 -
nmap –sQ –O <system> -P0
-
-
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team’s NEXT step during the detection phase of this response process?
- Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
- Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
- Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
- Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
-
While analyzing logs from a WAF, a cybersecurity analyst finds the following:
“GET /form.php?id=463225%2b%2575%256e%2569%256f%256e%2b%2573%2574%2box3133333731,1223,1224&name=&state=IL”
Which of the following BEST describes what the analyst has found?
- This is an encrypted GET HTTP request
- A packet is being used to bypass the WAF
- This is an encrypted packet
- This is an encoded WAF bypass
-
A company’s marketing emails are either being found in a spam folder or not being delivered at all. The security analyst investigates the issue and discovers the emails in question are being sent on behalf of the company by a third party, mail.marketing.com. Below is the existing SPF record:
v=spf1 a mx -all
Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
-
v=spf1 a mx redirect:mail.marketing.com ?all
-
v=spf1 a mx include:mail.marketing.com -all
-
v=spf1 a mx +all
-
v=spf1 a mx include:mail.marketing.com ~all
-
-
A security analyst is reviewing the following web server log:
GET %2f..%2f..%2f.. %2f.. %2f.. %2f.. %2f../etc/passwd
Which of the following BEST describes the issue?
- Directory traversal exploit
- Cross-site scripting
- SQL injection
- Cross-site request forgery
-
A hybrid control is one that:
- is implemented differently on individual systems
- is implemented at the enterprise and system levels
- has operational and technical components
- authenticates using passwords and hardware tokens
-
After a breach involving the exfiltration of a large amount of sensitive data, a security analyst is reviewing the following firewall logs to determine how the breach occurred:
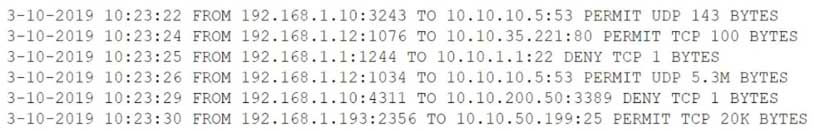
CS0-002 Part 04 Q16 018 Which of the following IP addresses does the analyst need to investigate further?
- 192.168.1.1
- 192.168.1.10
- 192.168.1.12
- 192.168.1.193
-
A cybersecurity analyst is supporting an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
- Requirements analysis and collection planning
- Containment and eradication
- Recovery and post-incident review
- Indicator enrichment and research pivoting
-
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
- web servers on private networks
- HVAC control systems
- smartphones
- firewalls and UTM devices
-
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:

CS0-002 Part 04 Q19 019 Which of the following should the analyst review to find out how the data was exfiltrated?
- Monday’s logs
- Tuesday’s logs
- Wednesday’s logs
- Thursday’s logs
-
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- It automatically performs remedial configuration changes to enterprise security services
- It enables standard checklist and vulnerability analysis expressions for automation
- It establishes a continuous integration environment for software development operations
- It provides validation of suspected system vulnerabilities through workflow orchestration