CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 07
CS0-002 : CompTIA CySA+ Certification Exam (CS0-002) : Part 07
-
A web-based front end for a business intelligence application uses pass-through authentication to authenticate users. The application then uses a service account to perform queries and look up data in a database. A security analyst discovers employees are accessing data sets they have not been authorized to use. Which of the following will fix the cause of the issue?
- Change the security model to force the users to access the database as themselves
- Parameterize queries to prevent unauthorized SQL queries against the database
- Configure database security logging using syslog or a SIEM
- Enforce unique session IDs so users do not get a reused session ID
-
A company’s Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user’s activity session. Which of the following is the BEST technique to address the CISO’s concerns?
- Configure DLP to reject all changes to the files without pre-authorization. Monitor the files for unauthorized changes.
- Regularly use SHA-256 to hash the directory containing the sensitive information. Monitor the files for unauthorized changes.
- Place a legal hold on the files. Require authorized users to abide by a strict time context access policy. Monitor the files for unauthorized changes.
- Use Wireshark to scan all traffic to and from the directory. Monitor the files for unauthorized changes.
-
Which of the following secure coding techniques can be used to prevent cross-site request forgery attacks?
- Input validation
- Output encoding
- Parameterized queries
- Tokenization
-
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output.

CS0-002 Part 07 Q04 025 Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
- Port 22
- Port 135
- Port 445
- Port 3389
-
Which of the following technologies can be used to store digital certificates and is typically used in high-security implementations where integrity is paramount?
- HSM
- eFuse
- UEFI
- Self-encrypting drive
-
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability. Company policy prohibits using portable media or mobile storage. The security analyst is trying to determine which user caused the malware to get onto the system. Which of the following registry keys would MOST likely have this information?
-
HKEY_USERS\<user SID>\Software\Microsoft\Windows\CurrentVersion\Run
-
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
-
HKEY_USERS\<user SID>\Software\Microsoft\Windows\explorer\MountPoints2
-
HKEY_USERS\<user SID>\Software\Microsoft\Internet Explorer\Typed URLs
-
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\System\iusb3hub
-
-
Clients are unable to access a company’s API to obtain pricing data. An analyst discovers sources other than clients are scraping the API for data, which is causing the servers to exceed available resources. Which of the following would be BEST to protect the availability of the APIs?
- IP whitelisting
- Certificate-based authentication
- Virtual private network
- Web application firewall
-
A security analyst recently discovered two unauthorized hosts on the campus’s wireless network segment from a man-in-the-middle attack. The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices. Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
- Enable MAC filtering on the wireless router and suggest a stronger encryption for the wireless network
- Change the SSID, strengthen the passcode, and implement MAC filtering on the wireless router
- Enable MAC filtering on the wireless router and create a whitelist that allows devices on the network
- Conduct a wireless survey to determine if the wireless strength needs to be reduced
-
Given the Nmap request below:
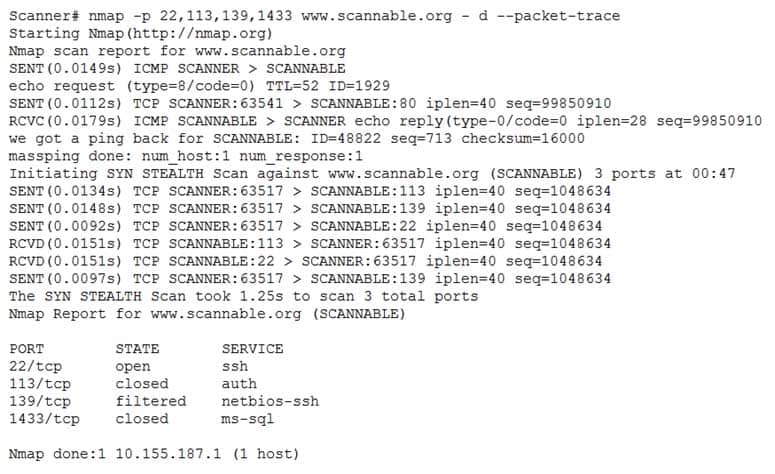
CS0-002 Part 07 Q09 026 Which of the following actions will an attacker be able to initiate directly against this host?
- Password sniffing
- ARP spoofing
- A brute-force attack
- An SQL injection
-
As part of an organization’s information security governance process, a Chief Information Security Officer (CISO) is working with the compliance officer to update policies to include statements related to new regulatory and legal requirements. Which of the following should be done to BEST ensure all employees are appropriately aware of changes to the policies?
- Conduct a risk assessment based on the controls defined in the newly revised policies
- Require all employees to attend updated security awareness training and sign an acknowledgement
- Post the policies on the organization’s intranet and provide copies of any revised policies to all active vendors
- Distribute revised copies of policies to employees and obtain a signed acknowledgement from them
-
During an investigation, an analyst discovers the following rule in an executive’s email client:
IF * TO <executive@anycompany.com> THEN mailto: <someaddress@domain.com> SELECT FROM ‘sent’ THEN DELETE FROM <executive@anycompany.com>
The executive is not aware of this rule. Which of the following should the analyst do FIRST to evaluate the potential impact of this security incident?
- Check the server logs to evaluate which emails were sent to <someaddress@domain.com>
- Use the SIEM to correlate logging events from the email server and the domain server
- Remove the rule from the email client and change the password
- Recommend that management implement SPF and DKIM
-
A critical server was compromised by malware, and all functionality was lost. Backups of this server were taken; however, management believes a logic bomb may have been injected by a rootkit. Which of the following should a security analyst perform to restore functionality quickly?
- Work backward, restoring each backup until the server is clean
- Restore the previous backup and scan with a live boot anti-malware scanner
- Stand up a new server and restore critical data from backups
- Offload the critical data to a new server and continue operations
-
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being used. Which of the following commands should the analyst use?
-
tcpdump –X dst port 21 -
ftp ftp.server –p 21
-
nmap –o ftp.server –p 21
-
telnet ftp.server 21
-
-
An incident response team is responding to a breach of multiple systems that contain PII and PHI. Disclosing the incident to external entities should be based on:
- the responder’s discretion
- the public relations policy
- the communication plan
- senior management’s guidance
-
A security is responding to an incident on a web server on the company network that is making a large number of outbound requests over DNS. Which of the following is the FIRST step the analyst should take to evaluate this potential indicator of compromise?
- Run an anti-malware scan on the system to detect and eradicate the current threat
- Start a network capture on the system to look into the DNS requests to validate command and control traffic
- Shut down the system to prevent further degradation of the company network
- Reimage the machine to remove the threat completely and get back to a normal running state
- Isolate the system on the network to ensure it cannot access other systems while evaluation is underway