N10-007 : CompTIA Network+ : Part 09
N10-007 : CompTIA Network+ : Part 09
NS – Modules 20 – 22
-
A technician is sent to a remote office to set up a device to connect to the Internet. The company standards document requires stateful inspection. Which of the following should the technician install?
- Router
- Multiplayer switch
- Firewall
- Bridge
-
A technician is assigned to secure a basic wireless network. Which of the following authentication protocols should the technician use to perform this task? (Choose two.)
- RDP
- SNMP
- WPA2
- EAP
- SSL
-
A technician is investigating the cause of a network outage. Which of the following documents should be checked to rule out configuration issues?
- Change management records
- Inventory management
- Network log files
- Logical diagrams
-
A junior network technician receives a help desk ticket from an end user who is having trouble accessing a web application that was working the previous day. After talking with the end user and gathering information about the issue, which of the following would be the most likely course of action for the technician to perform NEXT?
- Establish a theory of probable cause.
- Escalate the ticket to a senior technician.
- Implement the solution.
- Document the findings and outcomes.
-
A system administrator receives reports from users of odd behavior in regard to a recently installed server. While reviewing the server network configuration, the systems administrator does both a forward and a reverse DNS lookup on the host, along with the network adapter configuration.
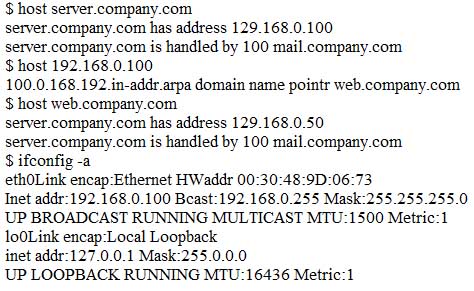
N10-007 Part 09 Q05 018 Which of the following is the problem identified in the output above?
- There is no reverse DNS entry for this host.
- The server IP address is incorrectly configured.
- The DNS lookup entry is incorrectly configured.
- The reverse DNS entry is pointing to a different host.
-
A network technician at a small office upgrades the LAN switch. After the upgrade, a user reports being unable to access network resources. When the technician checks the switchport, the LED light is not lit. Which of the following should the technician check FIRST?
- The device is using the correct cable type.
- The switchport is functioning properly.
- The device is connected to the switch.
- The switch is connected to the router.
-
A network administrator wants to employ a username and password authentication system for guest WiFi. Which of the following is the BEST option to provide this type of authentication?
- Port security
- MAC filtering
- Network access control
- Captive portal
-
A technician is responsible for configuring a new firewall. The hardware team has already installed, powered, and connected the system. Which of the following types of documentation should the technician utilize to complete the task?
- Rack diagram
- IDF/MDF documentation
- Network performance baseline
- Logical and physical diagrams
-
Which of the following storage network technologies inherently leverages block-level storage?
- NAS
- SAN
- FCoE
- iSCSI
- FTP
-
Which of the following networking devices operates at Layer1?
- Router
- Firewall
- Hub
- Bridge
-
A disgruntled employee decides to leak critical information about a company’s new product. The employee places keyloggers on the department’s computers, allowing the information to be sent out to the Internet. Which of the following attacks is occurring?
- Man-in-the-middle
- Logic bomb
- Insider threat
- Social engineering
-
A network technician needs to set up an access method for Ann, a manager, to work from home. Ann needs to locally mapped corporate resources to perform her job. Which of the following would provide secure access to the corporate resources?
- Utilize an SSH connection to the corporate server.
- Use TFTP to transfer files to corporate resources.
- Allow RDP through an external firewall.
- Connect utilizing client-to-site VPN.
-
Which of the following DNS record types is an alias?
- CNAME
- PTR
- NS
- SRV
-
A recently constructed building makes use of glass and natural light. Users in the building are reporting poor cellular connectivity and speeds. Which of the following is MOST likely the cause?
- Absorption
- Channel overlap
- Reflection
- Frequency mismatch
-
A network technician is working on a new switch implementation to expand the network. Which of the following is the BEST option to ensure the implementation goes according to business requirements?
- AUP
- NDA
- SOP
- SLA
-
A technician is utilizing SNMPv3 to monitor network statistics. Which of the following actions would occur immediately of a server’s utilization spikes above the prescribed value?
- A trap message is sent via UDP to the monitoring workstation.
- The SET function pushes an alert to the MIB database.
- The object identifier is modified and reported during the next monitoring cycle.
- A response message is sent from the agent to the manager.
-
In which of the following scenarios should a technician use a cross-over cable to provide connectivity?
- PC to switch
- Switch to AP
- Router to switch
- Router to modem
- PC to PC
-
802.11n clients currently have no way to connect to the network. Which of the following devices should be implemented to let the clients connect?
- Router
- Range extender
- VoIP endpoint
- Access point
-
A network technician is setting up a new router. Since it is exposed to the public, which of the following are the BEST steps the technician should take when setting up this device? (Choose two.)
- Disable unnecessary services.
- Use private IP addresses.
- Allow remote management access.
- Disable the console port.
- Enable encryption.
- Upgrade to the latest firmware.
-
A network technician is configuring user access to a VPN concentrator and has been advised to use a protocol that supports encryption over UDP. Which of the following protocols has the technician MOST likely configured for client use?
- TFTP
- DTLS
- DNS
- SNMP