N10-007 : CompTIA Network+ : Part 12
N10-007 : CompTIA Network+ : Part 12
NS – Modules 20 – 22
-
A technician is replacing a failed SOHO router for a customer who has an existing switch, cable modem, and static IP address. The user has a web server that faces the Internet so users can visit and leave comments. Which of the following BEST describes the correct configuration for this customer’s requirements?
- The modem is placed in bridge mode, the router is placed behind the modem, and the web server is placed behind the router.
- The router is placed in bridge mode, the modem is placed behind the router, and the web server is placed behind the modem.
- The web server is placed in bridge mode, the router is placed behind the web server, and the modem is placed behind the router.
- The switch is placed in bridge mode, the modem is placed behind the router, and the router is placed behind the modem.
-
A network technician is attempting to troubleshoot a connectivity issue. The issue is only reported during the evening hours, and only a single workstation loses connectivity. Which of the following is the MOST likely cause of the issue?
- The router has a time-based ACL, applied for the network segment.
- A light source is creating EMI interference, affecting the UTP cabling.
- Nightly backups are consuming excessive bandwidth.
- The user has violated the AUP, and Internet access has been restricted.
-
A network administrator is redesigning network security after an attack. During the attack, an attacker used open cubicle locations to attach devices to the network. The administrator wants to be able to monitor future attacks in a safe environment and determine the method of attack. Which of the following should the administrator do to BEST meet this requirement?
- Create a VLAN for the unused ports and create a honeyspot on the VLAN.
- Install a BPDU guard on switchports and enable STP.
- Create a DMZ for public servers and secure a segment for the internal network.
- Install antivirus software and set an ACL on the servers.
-
A company has just refreshed the hardware in its datacenter with new 10G Ethernet switches. A technician wishes to set up a new storage area network but must use existing infrastructure. Which of the following storage standards should the technician use?
- iSCSI
- Fibre Channel
- NAS
- InfiniBand
-
A network technician needs to install a new access switch. After installing the new switch, the technician begins to move connections from the old switch to the new switch. The old switch used a GBIC with SC connectors, and the new switch uses an SFP with LC connectors. After connecting the SC connector to the SC-to-LC adapter and plugging it into the switch, the link does not come up as expected. Which of the following should a network technician perform NEXT?
- Replace SFP with a new one.
- Fall back to the old switch.
- Transpose the fiber pairs.
- Replace multimode with single-mode cable.
-
A network technician is installing a new SOHO branch office that requires the use of a DOCSIS-compatible modem. The modem needs to be connected to the ISP’s network at the demarc. Which of the following cable types should be used?
- UTP
- Multimode
- Coaxial
- Serial
-
A technician needs to order cable that meets 10GBaseT and fire safety requirements for an installation between a drop ceiling and a standard ceiling. Which of the following should the technician order to ensure compliance with the requirements?
- PVC Cat 5
- Plenum Cat 5e
- Plenum Cat 6a
- PVC Cat 7
-
Which of the following physical security devices is used to detect unauthorized server room access?
- Access badge
- Biometrics
- Smart card
- Video surveillance
-
A network technician recently installed a new server on a network. The technician must ensure the server does not have any unnecessary services running. The IP address of the server is 204.211.38.50. Which of the following commands would allow the technician to make this determination?
-
nmap -
pathping
-
route
-
nslookup
-
-
Joe, an employee at a large regional bank, wants to receive company email on his personal smartphone and tablet. To authenticate on the mail server, he must first install a custom security application on those mobile devices. Which of the following policies would BEST enforce this requirement?
- Incident response policy
- BYOD policy
- DLP policy
- Remote access policy
-
A technician is allocating the IP address space needed for a new remote office. This office will contain the engineering staff with six employees and the digital marketing staff with 55 employees. The technician has decided to allocate the 192.168.1.0/24 block to the remote office. The engineering staff has been allocated the 192.168.1.64/29 subnet. Using the LEAST amount of space possible, which of the following would be the last usable IP address in the engineering subnet?
- 192.168.1.62
- 192.168.1.63
- 192.168.1.70
- 192.168.1.71
-
An administrator is troubleshooting a user’s intermittent wireless connectivity issue. Other users across the hallway can connect and use the wireless network properly. Upon inspection of the connection details, the administrator finds the following:
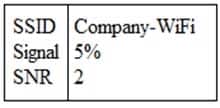
N10-007 Part 12 Q12 019 Which of the following is MOST likely the cause of the poor wireless connection?
- Channel overlap
- Overcapacity
- Incorrect antenna type
- Latency
-
A VoIP system will require 23 concurrent voice channels and one signaling channel. Which of the following types of WAN service would provide the BEST connectivity to the PSTN?
- PRI
- BRI
- E1/E3
- DSL
-
A network administrator is going to be performing a major upgrade to the network. Which of the following should the administrator use in case of a failure?
- Baseline report
- Vulnerability report
- Rollback plan
- Business continuity plan
-
A web application is unable to authenticate customers so they can access their bills. The server administrator has tested the LDAP query but is not receiving results. Which of the following is the NEXT step the server administrator should take to correct the problem?
- Check port 636 to see if it is being blocked.
- Change service port 636 to port 389.
- Restart the web server.
- Verify the browser is using port 443.
-
Which of the following is networking stand-alone hardware that will permit any WiFi-compliant device to connect to a wired network?
- Wireless hub
- Wireless firewall
- Wireless access point
- Wireless bridge
-
Which of the following devices are MOST often responsible for 802.1q tagging? (Choose two.)
- Switch
- Router
- IDS
- Hub
- IPS
- Network tap
-
A network technician is installing a new wireless network in a small office. Due to environmental concerns, the customer wants the network to run exclusively on the 5GHz frequency. Which of the following wireless technologies should the technician install to BEST meet this requirement? (Choose two.)
- 802.11ac
- 802.11b
- 802.11g
- 802.11n
- Bluetooth
- Z-Wave
-
Which of the following concepts would BEST describe when a company chooses to use a third-party vendor to host and administer a critical application?
- SaaS
- IaaS
- PaaS
- CASB
-
A content filter is set to analyze XML and JSON that users access from the Internet. At which of the following layers is this analysis taking place?
- 1
- 3
- 5
- 7
- 6