N10-007 : CompTIA Network+ : Part 24
N10-007 : CompTIA Network+ : Part 24
NS – Modules 20 – 22
-
A company’s web-based application has a database that is set up for high availability in case of a failure. Which of the following is necessary to achieve this type of setup?
- A virtual IP pointing to the active DB
- A static IP pointing to the passive DB
- A private IP pointing to the web front end
- A private IP pointing to the web proxy
-
A network technician is creating a diagram of network termination points in the building. The technician diagrammed the core network room and now needs to diagram the auxiliary network closets. Which of the following is the technician MOST likely going to add to the diagram?
- IDF
- MDF
- VRF
- TDM
-
A network technician has installed multiple new lightweight access points across the network. Which of the following devices should the technician use to manage the new access points?
- Wireless controller
- SSH
- DHCP server
- Content filter
- WiFi analyzer
-
Management is concerned there is excessive traffic on the network. A network technician wants to run a quick port scan to see any systems that have open ports. Which of the following tools should be used to do this?
-
tcpdump
-
dig
-
nmap -
netstat
-
-
A network technician receives the following command output from a Linux-based machine:
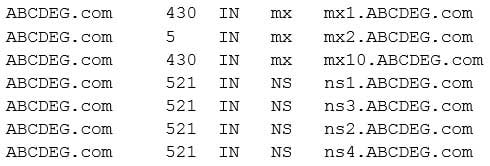
N10-007 Part 24 Q05 025 Which of the following commands did the network technician run?
-
iptables –f ABCDEG.com
-
dig –t ANY ABCDEG.com -
NMAP –t ABCDEG.com
-
netstat –a ACDEG.com
-
-
Allowing data to be centrally stored and accessed by multiple devices on an isolated subnet is BEST understood as:
- NAS
- iSCSI
- SAN
- FCoE
-
During a weekend event, several people reported they were unable to get onto the wireless network. On Monday, the technician could not find a problem. Which of the following is the MOST likely cause?
- Cross talk
- Overcapacity
- Channel overlap
- Wrong passphrase
-
After deployment of a second network link to load balance the network traffic, the quality of voice calls degrades. The network administrator discovers the voice packets are arriving at uneven intervals that cannot be handled by the voice application buffer. Which of the following actions will improve the quality of the voice calls?
- Control the attenuation of the non-voice traffic across the network links
- Control the latency of traffic across the network links
- Control the EMI of the multimedia traffic across the network links
- Control the jitter of the affected traffic across the network links
-
Which of the following can a network administrator use to access a network switch using standard AAA configurations?
- TACACS+
- Single sign-on
- LDAP
- Local authentication
-
A network technician receives a switch that is configured to support VLANs on its ports. At which of the following layers is this switch operating?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
-
Which of the following protocols is used to transport outgoing mail across networks?
- POP
- SMTP
- IMAP
- LDAP
-
Management at a company wants to increase the bandwidth available to users after receiving several complaints. A technician reports to management that 50% of the company bandwidth is being utilized by wireless devices outside the company’s property. Given budget constraints, which of the following solutions should the technician propose to management?
- Have the ISP double the bandwidth
- Move from WPA2 to WEP
- Enable WPA and change the SSID
- Configure geofencing
-
To increase speed and availability, a high-traffic web application was split into three servers recently and moved behind a load balancer. Which of the following should be configured on the load balancer to allow for a single destination?
- SIP
- PAT
- NAT
- VIP
-
A network technician is reading a network diagram and looking for the edge router. Which of the following is MOST likely the symbol used for the router?
- A circle with four outward arrows
- A rectangle with two horizontal arrows
- A square with two circular arrows
- A triangle with three outward arrows
-
Which of the following would a network technician MOST likely connect to power wireless access points in drop ceilings?
- Powerline extender
- Ethernet-over-power adapter
- Power-over-Ethernet switch
- Power distribution unit
- Ethernet power controller
-
A network technician needs to monitor the traffic going to a mission-critical server in the datacenter. Which of the following is the BEST method to perform this?
- Use port mirroring
- Install an inline tap
- Periodically view the server logs
- Configure port aggregation
-
A network engineer at a large company is restricting Internet browsing on the corporate WAN to only business-related external websites. Which of the following is the BEST solution to achieve this goal while avoiding the need to configure this restriction on each PC?
- Web application firewall
- Content filter
- IPS
- VPN concentrator
-
Which of the following types of attacks is characterized by encrypting data and locking out a user from access to certain data within a workstation?
- Ransomware
- Phishing
- DDoS
- Social engineering
- Spoofing
-
The process of searching for open or weakly secured wireless networks in a geographic area is known as:
- phishing.
- social engineering.
- war driving.
- an evil twin.
-
A request is made to open an additional port on a firewall. The request is approved, and the port is opened. Which of the following BEST describes this process?
- Standard operating procedure
- Process management
- Project management
- Change management