N10-007 : CompTIA Network+ : Part 25
N10-007 : CompTIA Network+ : Part 25
NS – Modules 20 – 22
-
A network technician notices that switches of the same model have different commands and security features while administering them. Which of the following hardening techniques should the technician perform on a regular schedule to ensure all switches have the same features and security functionality?
- Change the default credentials.
- Verify the firmware file hash.
- Disable unused switchports.
- Apply patches and updates.
-
A network administrator has deployed a secure wireless network that authenticates using Active Directory network credentials so individual users are uniquely identified when connected to the WLAN. Which of the following wireless technologies has the administrator configured?
- WEP
- EAP-PEAP
- PSK
- CCMP-AES
-
A SAN serves out storage to a company’s virtual environment and provides low-level disk access. The company wants to use its existing IP network and equipment to access the virtual disks. Which of the following network connection types would BEST accomplish this task?
- InfiniBand
- iSCSI
- Fibre Channel
- CIFS
-
When using a network monitoring system, a network technician notices that a switch returns many object identifiers that do not have descriptions. Which of the following should be imported into the monitoring system to describe these object identifiers?
- SNMPv3
- SIEM
- MIB
- SYSLOG
-
A company hires some temporary workers. On day one, the temporary employees report they are unable to connect to the network. A network technician uses a packet analysis tool and finds that many clients are continuously sending out requests for an IP address, but many of them are not receiving a response. Which of the following could be the cause of this issue?
- Exhausted DHCP scope
- Untrusted SSL certificates
- Duplicate MAC addresses
- Incorrect firewall settings
-
A network administrator is responding to a help desk ticket, which states an unknown wireless access point is broadcasting in a specific area. Upon investigation, the administrator finds that a user brought a wireless access point from home and plugged it into the corporate network. This resulted in an attacker using the unsecured wireless LAN to gain access to the network. Which of the following should the network administrator have done to BEST prevent this problem?
- Changed the default credentials on the network switches
- Installed a Layer 7 firewall
- Implemented port security
- Disabled unnecessary services on the network switches
-
A user no longer has access to network resources after a recent office move, but all other users in the building are able to connect at 100MB connections. After further investigation, a network technician notices the following information:
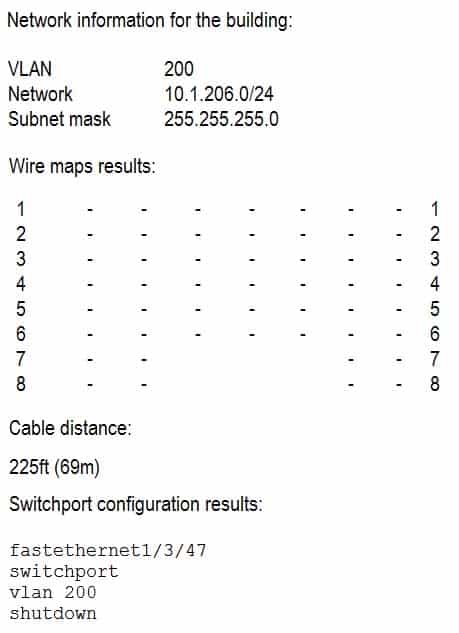
N10-007 Part 25 Q07 026 Which of the following is causing the network connection issues?
- Open/short pins
- VLAN mismatch
- Distance limitation
- Crosstalk
- Port configuration
-
A small team is overloaded with requests for database resources. The Chief Information Officer (CIO) is concerned the company does not have the resources to deploy and manage these additional services efficiently. Which of the following types of cloud services would be the MOST effective?
- PaaS
- IaaS
- BaaS
- SaaS
-
Which of the following should be performed on a regular basis to prevent unauthorized access to a company network? (Choose two.)
- Packet analysis
- Reviewing baselines
- Vulnerability scanning
- Patch management
- Log archiving
-
A network technician receives a report that the company’s intranet web server is not responding. The technician verifies successful connectivity to the server via the ping and tracert commands. The technician also verifies the routers and switches are online and operational, and then runs Telnet to port 80 and receives a response. Which of the following troubleshooting steps should the technician perform NEXT?
- Establish a plan to reset the company router.
- Escalate the issue to the server administrator.
- Duplicate the issue and continue testing.
- Report that an issue was not identified.
-
Which of the following ports are used for electronic mail protocols? (Choose three.)
- 23
- 25
- 110
- 123
- 143
- 161
- 389
- 443
-
A technician needs to connect two routers using copper cables. Which of the following cables would utilize both the TIA/EIA 568a and TIA/EIA 568b standards?
- Cat5 crossover
- Cat5e straight-through
- Cat5e rollover
- Cat6 console
- Cat6a straight-through
-
The engineering department wants to bring a legacy computer online to test a failed component. When patching the device into the switch, there are no link lights or connectivity. The legacy computer can ping its loopback address successfully. Another device can connect to that same port without issues. Which of the following should the network technician check NEXT? (Choose two.)
- Speed setting on the switch
- Duplex requirements
- Firmware version
- Protocols the legacy computer supports
- Network card drivers
- VLAN settings
-
A user in the marketing department reports the email server is down. The user has not received email for more than 24 hours. Which of the following should the network technician do to investigate this issue?
- Question other users in the marketing department to see if they are also having connectivity issues.
- Reboot the email server and verify connectivity once it is up again.
- Check the router and firewall to see if ACLs or firmware have changed in the last 24 hours.
- Check for network connectivity on the user’s PC and reinstall the email client.
-
A network technician has provisioned a new Linux instance in a public cloud provider’s IaaS environment. The technician did not install a graphical user interface. The technician wants to connect to the server’s public IP address securely to start a console session. Which of the following remote access methods should the technician use?
- SSH
- Telnet
- VNC
- RDP
-
A network administrator is reviewing the following output from a switch:
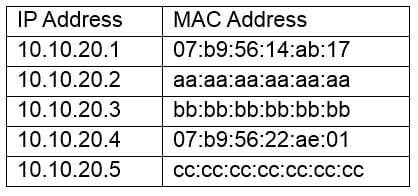
N10-007 Part 25 Q16 027 Which of the following attacks has occurred on the switch?
- DNS poisoning
- ARP poisoning
- VLAN hopping
- MAC address spoofing
-
A user does not have access to network services but has Internet access. The technician notices the computer has an IP address of 192.168.1.144 when the network is 10.10.10.0. Which of the following is MOST likely the issue?
- Rogue DHCP server
- Duplicate IP addresses
- Incorrect gateway
- Server permission changes
-
A technician is trying to identify the cause of an issue several wireless users are experiencing at an office. The office is in a square-shaped building, with four 802.11b WAPs with omnidirectional antennas located in the four corners of the building. Users near the center of the building report sporadic issues connecting to resources. The technician checks the signal strength in the middle of the building and determines it is adequate. Which of the following is causing the reported issue?
- The antenna types are incorrect, and unidirectional should be used.
- MAC filtering has not been updated.
- There is channel overlap of the access points.
- The power levels are set too low on the WAPs.
-
A network technician is performing an initial configuration of a new network switch. Per company policy, the only authorized manner for remotely administering the switch is through a command line. Which of the following protocols should the technician disable to adhere to the company policy?
- HTTP
- Telnet
- SSH
- TFTP
-
A network technician is troubleshooting a connectivity issue with Joe, a user. Joe has reported that when he attempts to RDP to machine1 (192.168.21.21) by name, he is connected to machine3 (192.168.21.23). When the network technician runs the command nslookup machine1, it returns the IP address 192.168.21.23; but when the ping –a 192.168.21.23 command is run, the results return the hostname machine3. Which of the following DNS records should be updated to allow RDP connections to machine1 by hostname?
- A
- SRV
- PTR
- TXT