N10-007 : CompTIA Network+ : Part 29
N10-007 : CompTIA Network+ : Part 29
NS – Modules 20 – 22
-
HOTSPOT
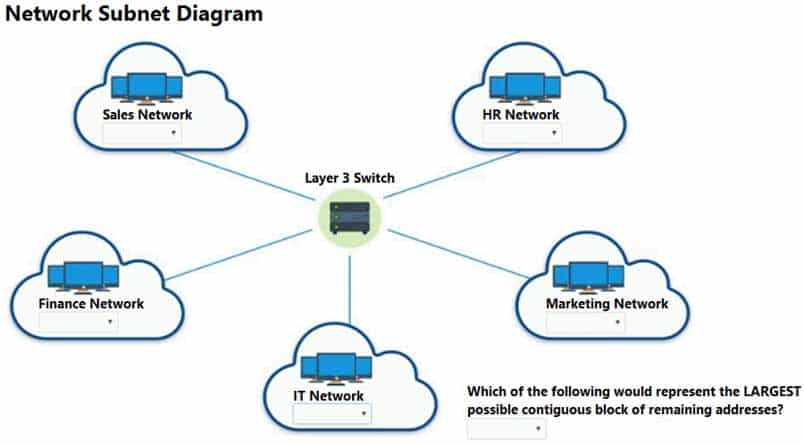
Corporate headquarters provided your office a portion of their class B subnet to use at a new office location.
Range Given: 172.30.232.0/24
– Sales 57 devices
– HR 23 devices
– IT 12 devices
– Finance 32 devices
– Marketing 9 devicesINSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
N10-007 Part 29 Q01 029 
N10-007 Part 29 Q01 030 Question 
N10-007 Part 29 Q01 030 Answer Explanation:
Sales network – /26 – This will provide up to 62 usable IP addresses (64-2 for subnet and broadcast IP)
HR network – /27 – This will provide for up to 30usable IP’s (32-2)
IT – /28 – This will provide for up to 14 usable IP’s (16-2)
Finance – /26 – Note that a /27 is 32 IP addresses but 2 of those are reserved for the network and broadcast IP’s and can’t be used for hosts.
Marketing – /28
If we add up how many IP blocks are used that is 64+32+16+64+16=192.
A /24 contains 256 IP addresses, so 256-192=64.
So the last unused box should be a /26, which equates to 64 addresses -
SIMULATION
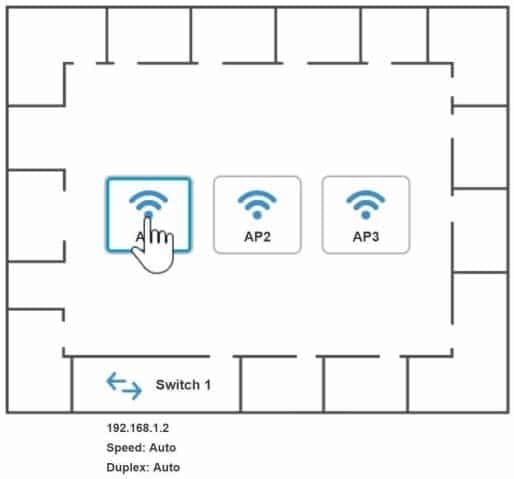
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other.
The subnet the Access Points and switch are on should only support 30 devices maximum.
The Access Points should be configured to only support TKIP clients at a maximum speed.INSTRUCTIONS
Click on the devices to review their information and adjust the settings of the APs to meet the given requirements.
If any time you would like to bring back the initial state of the simulation, please click the Reset All button.
N10-007 Part 29 Q02 031 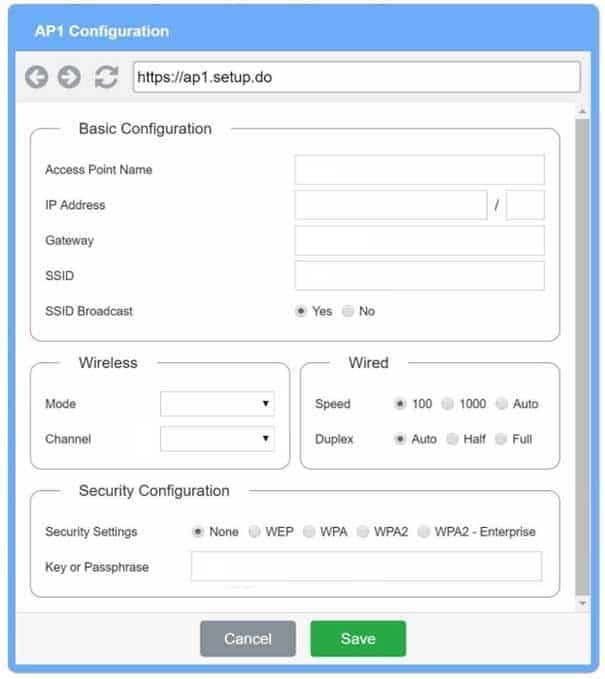
N10-007 Part 29 Q02 032 
N10-007 Part 29 Q02 033 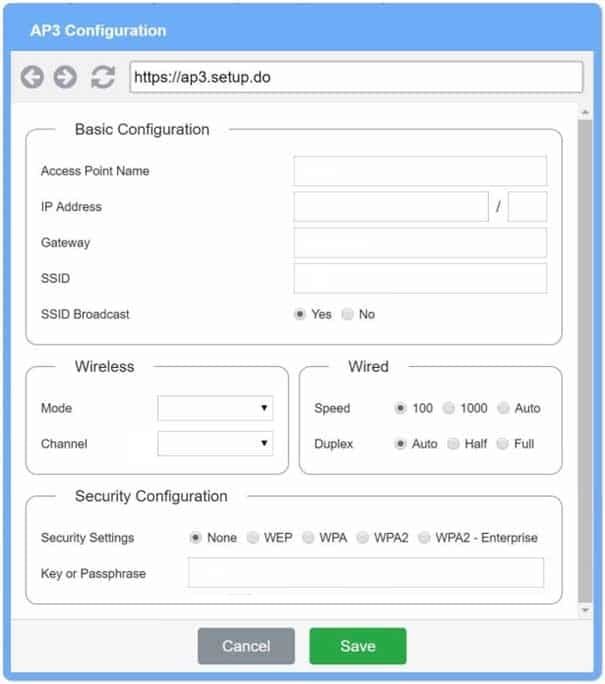
N10-007 Part 29 Q02 034 - See explanation below.
Explanation:
On the first exhibit, the layout should be as followsAccess Point Name AP1
IP Address 192.168.1.3
Gateway 192.168.1.2
SSID corpnet
SSID Broadcast yesMode G
Channel 1Speed Auto
Duplex AutoWPA
Passphrase S3cr3t!Exhibit 2 as follows
Access Point Name AP2
IP Address 192.168.1.4
Gateway 192.168.1.2
SSID corpnet
SSID Broadcast yesMode G
Channel 6Speed Auto
Duplex AutoWPA
Passphrase S3cr3t!Exhibit 3 as follows
Access Point Name AP3
IP Address 192.168.1.5
Gateway 192.168.1.2
SSID corpnet
SSID Broadcast yesMode G
Channel 11Speed Auto
Duplex AutoWPA
Passphrase S3cr3t!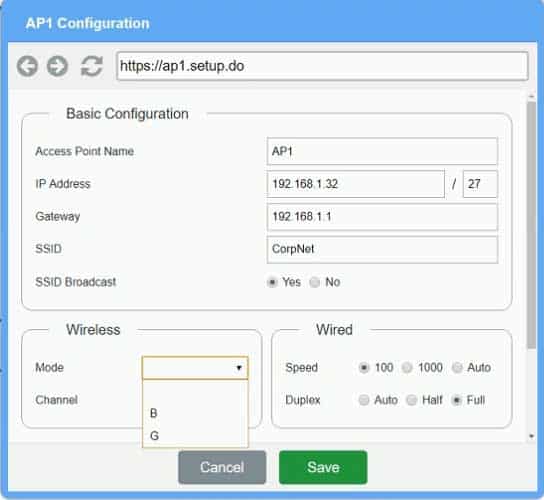
N10-007 Part 29 Q02 035 
N10-007 Part 29 Q02 036 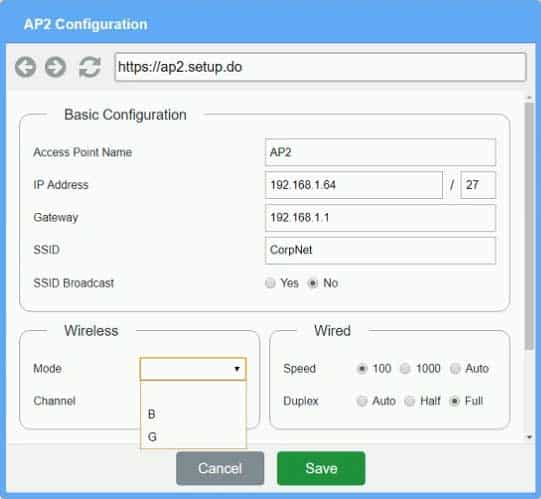
N10-007 Part 29 Q02 037 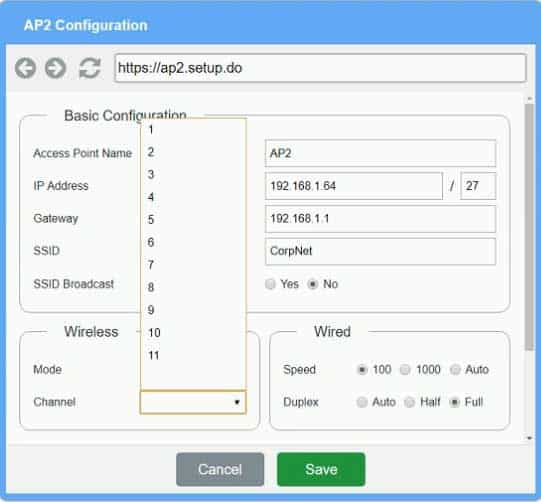
N10-007 Part 29 Q02 038 
N10-007 Part 29 Q02 039 
N10-007 Part 29 Q02 040 -
SIMULATION
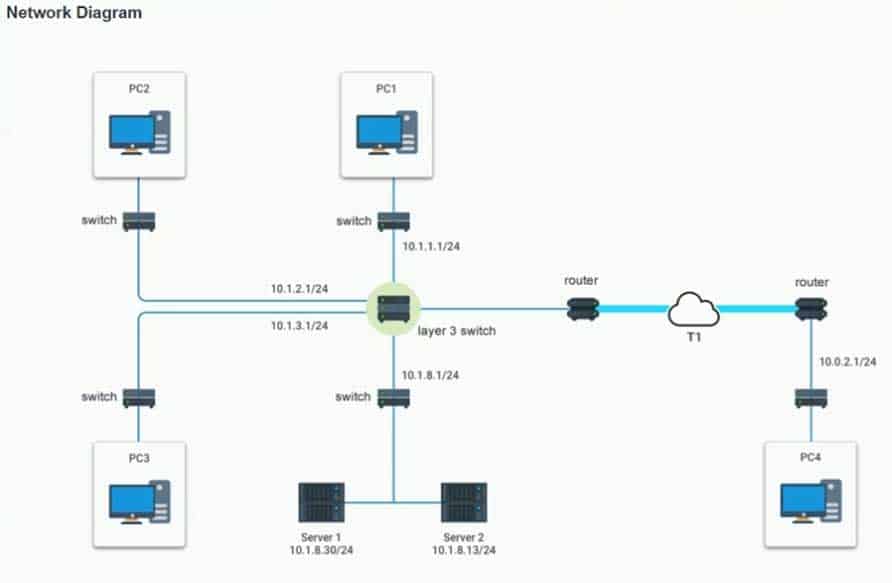
After recent changes to the pictured network, several users are unable to access the servers. Only PC1, PC2, PC3, and PC4 are clickable and will give you access to the command prompt and the adapter configuration tabs.
INSTRUCTIONS
Verify the settings by using the command prompt, after making any system changes.
Next, restore connectivity by making the appropriate changes to the infrastructure.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
N10-007 Part 29 Q03 041 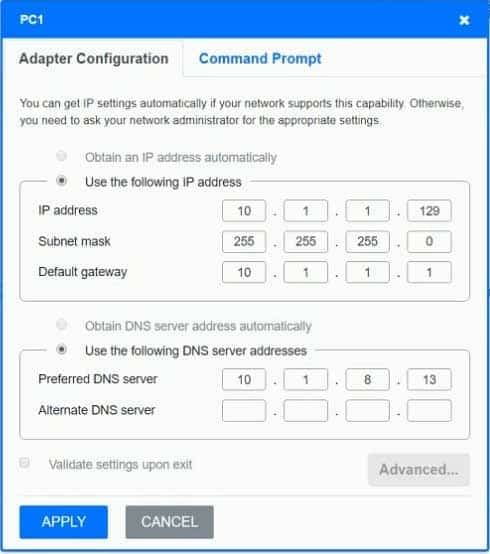
N10-007 Part 29 Q03 042 
N10-007 Part 29 Q03 043 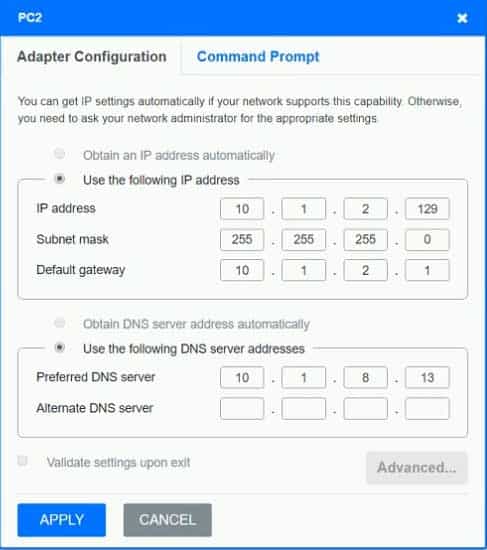
N10-007 Part 29 Q03 044 
N10-007 Part 29 Q03 045 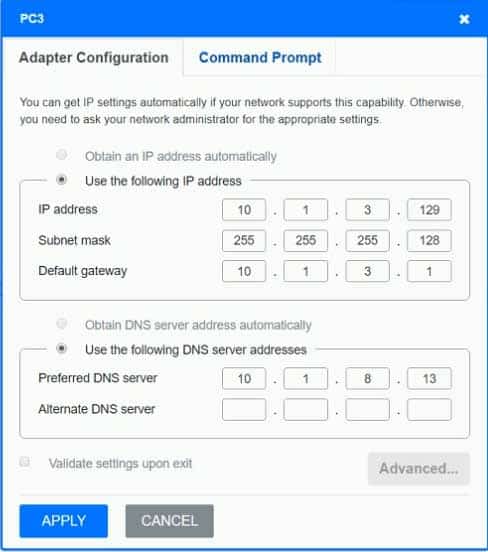
N10-007 Part 29 Q03 046 
N10-007 Part 29 Q03 047 
N10-007 Part 29 Q03 048 
N10-007 Part 29 Q03 049 - See explanation below.
Explanation:
On PC3, change the subnet mask to 255.255.255.0. When it is set to 255.255.255.128, then the PC with a .129 address will not be on the same subnet as the default gateway which is .1 On PC4, change the default gateway to 10.0.2.1. It has been incorrectly set as 10.1.2.1. -
While reviewing switch logs, a network analyst notices many failed logon attempts followed by a successful logon from an unknown IP address. Which of the following hardening techniques should be utilized to prevent unauthorized access?
- Avoiding common passwords
- File hashing
- Disabling unused IP ports
- Using secure protocols
Explanation:
On PC3, change the subnet mask to 255.255.255.0. When it is set to 255.255.255.128, then the PC with a .129 address will not be on the same subnet as the default gateway which is .1 On PC4, change the default gateway to 10.0.2.1. It has been incorrectly set as 10.1.2.1. -
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
- WPA2
- EAP-FAST
- MAC filtering
- 802.1X
-
Which of the following routing conventions is known as a link-state protocol?
- RIP
- BGP
- EIGRP
- OSPF
-
A technician is making the population of routers more secure. Which of the following are the BEST options for making authentication more secure? (Choose two.)
- Add a login banner.
- Disable unused services.
- Upgrade the firmware.
- Disable Telnet.
- Implement AAA.
- Disable SSH.
-
A technician is installing six PCs and six VoIP telephones on a small office LAN. The VoIP telephones require QoS to be configured for proper operation. The customer router does not have QoS capability. Which of the following network devices should the technician purchase and install at this office?
- Managed PoE switch
- Load balancer
- Layer 3 switch
- Unmanaged PoE switch
-
A network administrator has signed up for service with a new ISP. The administrator was given the IP address of 172.17.10.254/30 to use on the external interface of the Internet-facing router. However, the network administrator cannot reach the Internet using that address. Which of the following is the MOST likely explanation?
- The address provided by the ISP has a mask that is too small to be used and needs a larger mask.
- The address provided by the ISP is a private IP address space and is not routable on the Internet.
- The address provided by the ISP is the wrong one; they should be using 172.17.10.252/30.
- The address provided by the ISP is part of the reserved loopback address space and cannot be used.
-
A company deploys many workers in the field who remotely access files from a server at headquarters. Leadership is concerned about the risks posed when field workers update these files from unsecured networks. Which of the following policy changes can the company make to MOST improve the confidentiality of connections when connecting remotely? (Choose two.)
- Implement SSL VPN connections from the remote devices to headquarters.
- Change file access protocols from SFTP to FTP on the remote devices.
- Utilize HTTPS to access the company intranet from remote devices.
- Configure WPA2 on the wireless networks at headquarters.
- Configure IMAP over port 143 for email access on remote devices.
-
A manufacturing company has signed an agreement with another company to collaborate on an upcoming project. Both companies require secure and persistent access to resources on each other’s networks. Which of the following remote access technologies should the companies implement to satisfy their requirements?
- Out-of-band management
- Site-to-site VPN
- DMZ networks
- SFTP site
-
A security administrator wants to implement the ability to prevent an unauthorized user from tailgating into the office building. Which of the following should be implemented?
- Badge reader
- Bluetooth reader
- Cipher lock
- Mantrap
-
Joe, a technician, was able to copy data at a site with no network equipment between two new laptops, featuring gigabit Ethernet ports, by using a regular straight-through patch cable. Joe then unsuccessfully tried to accomplish the same thing at a different site from his laptop with a gigabit Ethernet port to an older customer unit, which had a 10/100 network port. Which of the following is the cause of this?
- The customer’s laptop does not support auto-MDIX.
- Joe’s laptop does not support auto-MDIX.
- Straight-through patch cables are prone to crosstalk.
- The customer’s laptop NIC does not support full duplex.
-
A network engineer has connected the storefront with the maintenance shed on the other side of a golf course using 802.11 wireless bridges and omnidirectional antennas. However, the signal strength is too weak. Which of the following is the MOST efficient and cost-effective solution to solve the issue?
- Replace the omnidirectional antennas with unidirectional antennas.
- Put protective enclosures around the omnidirectional antennas to prevent damage from golf balls.
- Replace the 802.11 wireless standard and use GSM instead.
- Replace the wireless bridges with wireless routers.
-
Which of the following would block access to an untagged port when connected to a Layer 2 device?
- BPDU guard
- Spanning tree
- Flood guard
- Root guard
-
Which of the following OSI layers contains the LLC function?
- Network
- Data link
- Session
- Transport
-
Which of the following BEST describes the RADIUS authentication service protocol?
- A protocol that sends passwords to the authentication server
- A protocol that sends encrypted tickets from the authentication server
- A protocol that sends X.500 service requests to the authentication server
- A protocol that sends configuration information from the authentication server
-
A company needs a secure way to provide building blueprints to an engineering partner frequently. The Chief Information Officer (CIO) states that a secure protocol must be used for transfer, and the partner needs to initiate a secure connection to the company’s router. Which of the following would BEST meet the requirements? (Choose two.)
- Site-to-site VPN
- Client-to-site VPN
- RDP
- SSH
- SFTP
- Captive portal
-
A network technician is installing a new PTZ camera for the security department. The camera is capable of being powered via the Ethernet cable, but it is not powering on. The network technician has tested the cable and received positive results. Which of the following is MOST likely the issue?
- The camera requires PoE+, but the switch is delivering only PoE.
- A straight-through cable is being used, but the camera requires a crossover cable.
- The camera is configured for the wrong segmented network.
- The cable has a bad pinout and needs to be reterminated.
-
A network technician attempts to limit access to a wireless network by using WPA2 and a pre-shared key; however, employees have been sharing this key with others. Which of the following methods should the technician configure on the wireless access point to ensure only corporate systems can connect using the least amount of effort?
- RADIUS
- EAP-TLS
- Port security
- MAC filtering