N10-007 : CompTIA Network+ : Part 38
N10-007 : CompTIA Network+ : Part 38
NS – Modules 20 – 22
-
A technician receives a report that Joe, an existing user, is unable to access the network. Joe confirms that he had full access the previous day. The change log is reviewed, and there have been no changes on Joe’s computer or any network changes in the last week. The technician moves the connection to an adjacent location on the switch, and Joe is able to access the network. Which of the following is the MOST likely cause of this issue?
- Incorrect pin-out
- Bad port
- Transceiver mismatch
- Incorrect cable type
-
A network administrator plans to install network connectivity at a new remote office location. The administrator is concerned about how to troubleshoot network connectivity issues and reconfigure the remote router. The technician should use __________.
- an SD card with a backup configuration.
- a TFTP server on the main network for backup configurations.
- a modem using POTS.
- a second Ethernet interface for remote access.
-
A consultant is designing a new network for a company that will be hosting its own email and web servers. The company wants to ensure there are separate devices to protect the internal network from the DMZ and the DMZ from the Internet. Which of the following would provide this protection?
- The installation of a firewall with multiple interfaces for the Internet to the DMZ and the LAN.
- The in-line installation of two firewalls to divide the Internet to the DMZ and the DMZ to the LAN.
- The installation of two switches to divide the Internet from the LAN and the LAN to the DMZ.
- The installation of a switch from the Internet to the DMZ and a firewall between the DMZ and the LAN.
-
Which of the following BEST explains why a network engineer would use a wireless mesh network when connecting sensors to a sensor gateway?
- It creates various paths to a particular destination.
- It increases the overall throughput of the links connecting the devices.
- It provides redundancy if the sensor network experiences broad wireless interference.
- It allows autonomous communication if the sensor network goes down.
-
A network technician is assisting a user who cannot connect to a wireless connection. The user is connecting to the correct SSID and has the correct pre-shared key. The technician verifies the WAP is working, and other clients are connected to it from the same location. Which of the following should the technician investigate?
- Channel overlap
- Wireless frequency
- AP power levels
- Encryption type
-
A network administrator has been directed to present the network alerts from the past week to the company’s executive staff. Which of the following will provide the BEST collection and presentation of this data?
- A port scan printout
- A consolidated report of various network devices
- A report from the SIEM tool
- A report from a vulnerability scan done yesterday
-
As part of a new datacenter upgrade project, the security manager has asked for additional physical security to prevent asset theft. Which of the following technologies should be implemented?
- Video surveillance
- Motion detection alarms
- Asset tracking tags
- Locks on devices
-
HOTSPOT
Workstations are unable to access the Internet after a recent power outage. Configure the appropriate devices to ensure All workstations have Internet connectivity.
Instructions
All ports can be enabled (fill) or disabled (no fill).
If at any time you wiuld like to bring back the initial state of the simulation, please click the Reset All button.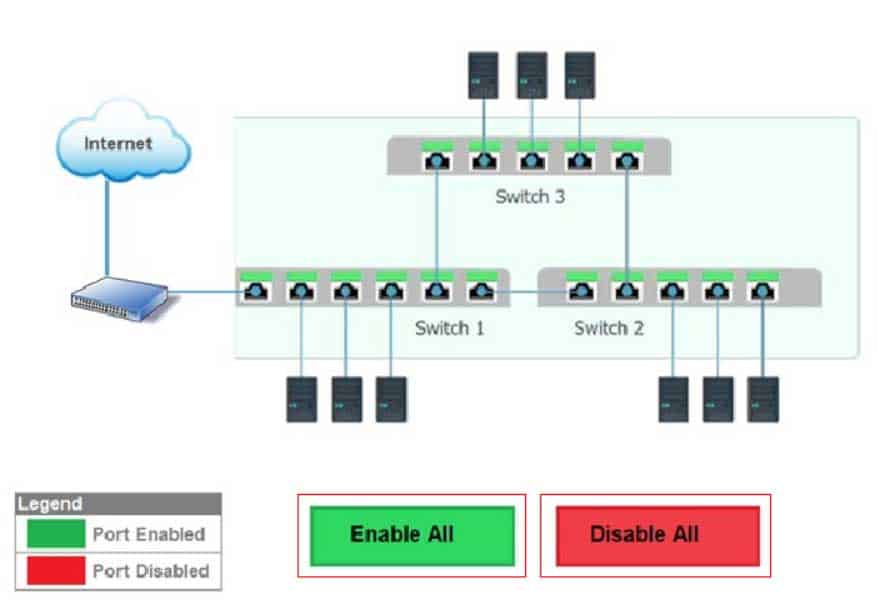
N10-007 Part 38 Q08 053 Question 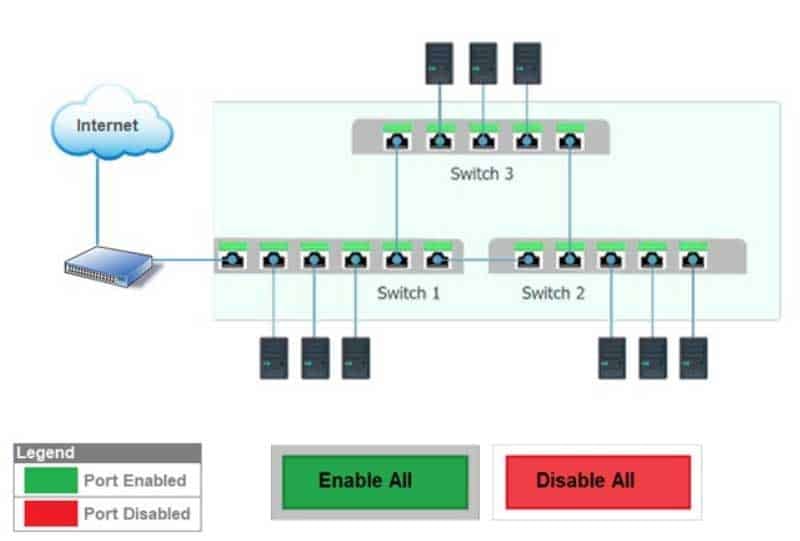
N10-007 Part 38 Q08 053 Answer