H12-211 : HCIA Routing & Switching : Part 01
-
An administrator currently manages AR2200 devices in the network through a single password, however the company wishes to introduce another two administrators and provide unique user credentials and privilege levels for telnet access to the network devices.
What action can be taken? (Choose three)
- Configure three users under the AAA-view, and assign each a different password.
- The authentication mode must be changed to AAA.
- Each administrator must be assigned a privilege level.
- A public IP address must be assigned to each user for telnet access
-
Which of the following authentication methods are supported for Telnet users? (Choose three)
- Password authentication
- AAA local authentication
- MD5 authentication
- No authentication
-
On Huawei AR G3 Series routers, which authentication modes does AAA support? (Choose all that apply.)
- None
- Local
- Radius
- 802.1X
-
Refer to the configuration output. RTA has been configured using AAA as shown, and associated with the “huawei” domain. For users in the huawei domain, which authentication-scheme will be used?

H12-211 HCIA Routing & Switching Part 01 Q04 001 - au1
- au2
- au1 will be used. When au1 is deleted, users will use au2
- au2 will be used. When au2 is deleted, users will use au1
-
A user accesses a server supporting AAA, for which the authorization mode on the AAA server has been configured using the command “authorization-mode hwtacacs if-authenticated”.
Which of the following statements regarding this command are true? (Choose three).
- If the hwtacacs server fails to respond, the user will be authenticated using local authentication.
- If the hwtacacs server fails to respond, the user will be authenticated using remote authentication.
- If the hwtacacs server fails to respond, the user will bypass authentication.
- The hwtacacs server will authorize the user.
-
Which of the following descriptions regarding eSight is not correct?
- eSight is used to monitor and manage enterprise networks.
- eSight supports only Huawei devices.
- eSight supports WLAN management and monitoring of hotspot coverage.
- eSight supports the backup of configuration files and network traffic analysis.
-
What of the following statements is correct regarding access control list types and ranges?
- A basic ACL value ranges from 1000-2999
- An advanced ACL value ranges from 3000-4000
- A layer 2 ACL value ranges from 4000-4999
- An interface ACL value ranges 1000-2000
-
Which of the following parameters is not used by Advanced ACL?
- Source interface
- Destination port number
- Protocol number
- Time-range
-
Refer to the configuration output. Which of the following statements regarding ACL 2001 is correct?

H12-211 HCIA Routing & Switching Part 01 Q09 002 - Packets from network 10.0.1.0/24 network will be denied.
- Packets from network 10.0.1.0/24 network will be permitted.
- Packets destined for network 10.0.1.0/24 will be denied.
- Packets destined for network 10.0.1.0/24 will be permitted.
-
Refer to the configuration output. A network administrator configured the ACL on router RTA, as shown.

H12-211 HCIA Routing & Switching Part 01 Q10 003 Which of the following statements regarding the rule order are correct? (Choose two).
- The rule-number of the first rule is 1
- The rule-number of the first rule is 5
- The rule-number of the second rule is 2
- The rule-number of the second rule is 10
-
Following a failure of services in the network, an administrator discovered that the configuration in one of the enterprise routers had been changed.
What actions can be taken by the administrator to prevent further changes? (Choose three)
- The administrator should limit access by setting the login privilege of users to 0.
- The administrator should configure AAA to manage user authorization on the router.
- The administrator should configure an ACL to allow only the administrator to manage the router.
- The administrator should configure port-security on the router.
-
Refer to the configuration output. Which of the following statements is correct regarding the configuration of the ACL on RTA?

H12-211 HCIA Routing & Switching Part 01 Q12 004 - Packets from network 20.1.1.0/24 network will be denied.
- Packets from network 20.1.1.0/24 network will be permitted.
- Packets destined for network 20.1.1.0/24 will be denied.
- Packets destined for network 20.1.1.0/24 will be permitted.
-
Refer to the configuration output. Which of the following statements are correct regarding the configuration of the ACL on RTA? (Choose two).

H12-211 HCIA Routing & Switching Part 01 Q13 005 - Packets from network 172.16.1.1/32 will be denied.
- Packets from network 172.16.1.0/24 will be denied.
- Packets from network 172.17.1.0/24 will be denied.
- Packets from network 172.18.0.0/16 will be denied.
-
The network administrator wants to improve the performance of network transmission, what steps can the administrator take? (Choose two)
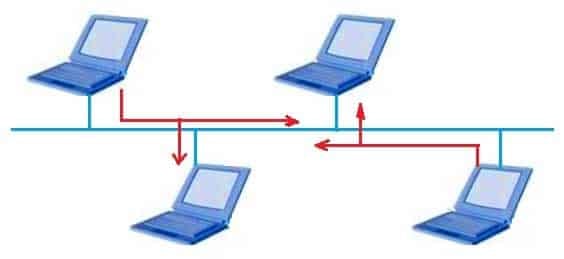
H12-211 HCIA Routing & Switching Part 01 Q14 006 - Change the work mode to full duplex of each end station.
- Link the end stations together using a switch.
- Change the work mode to half duplex of each end station.
- Link the end stations together using a hub.
-
On Huawei switch, which of the following commands can be used to set port duplex mode as “auto negotiation”? (Choose two)
- duplex negotiation auto
- duplex auto-negotiation
- duplex auto
- undo duplex
-
The network administrator wishes to transmit data between two end stations. The network interface cards of both devices operates at 100Mbps however one supports half duplex while the other uses full duplex mode.
What will occur as a result?
- The end stations cannot communicate.
- The end stations can communicate, but data may be lost during transmission of large amounts of traffic.
- The end stations will operate normally
- The end stations can communicate, but speed is different during transmission of large amounts of traffic.
-
An Ethernet port can work one of three duplex modes, whereas an Optical Ethernet port only supports one single mode.
Which of the following represents this mode?
- Full-duplex
- Half-duplex
- Auto-negotiation
- Simplex
-
While inspecting packets in the network, a network administrator discovers a frame with the destination MAC address of 01-00-5E-A0-B1-C3.
What can the administrator determine from this?
- The MAC address is a unicast address.
- The MAC address is a broadcast address
- The MAC address is a multicast address.
- The MAC address is incorrect.
-
According to OSI reference model, which layer is responsible for end to end error checking and flow control?
- Physical layer
- Data link layer
- Network layer
- Transport layer
-
Which of the following mechanisms are used for flow control? (Choose three)
- Acknowledgement
- Buffering
- Source quench messages
- Windowing
Subscribe
0 Comments
Newest