CISSP : Certified Information Systems Security Professional : Part 14
CISSP : Certified Information Systems Security Professional : Part 14
-
Which of the following would BEST support effective testing of patch compatibility when patches are applied to an organization’s systems?
- Standardized configurations for devices
- Standardized patch testing equipment
- Automated system patching
- Management support for patching
-
An international medical organization with headquarters in the United States (US) and branches in France wants to test a drug in both countries. What is the organization allowed to do with the test subject’s data?
- Aggregate it into one database in the US
- Process it in the US, but store the information in France
- Share it with a third party
- Anonymize it and process it in the US
-
As part of an application penetration testing process, session hijacking can BEST be achieved by which of the following?
- Known-plaintext attack
- Denial of Service (DoS)
- Cookie manipulation
- Structured Query Language (SQL) injection
-
Assessing a third party’s risk by counting bugs in the code may not be the best measure of an attack surface within the supply chain.
Which of the following is LEAST associated with the attack surface?
- Input protocols
- Target processes
- Error messages
- Access rights
-
What are the steps of a risk assessment?
- identification, analysis, evaluation
- analysis, evaluation, mitigation
- classification, identification, risk management
- identification, evaluation, mitigation
-
After following the processes defined within the change management plan, a super user has upgraded a device within an Information system.
What step would be taken to ensure that the upgrade did NOT affect the network security posture?
- Conduct an Assessment and Authorization (A&A)
- Conduct a security impact analysis
- Review the results of the most recent vulnerability scan
- Conduct a gap analysis with the baseline configuration
-
DRAG DROP
What is the correct order of steps in an information security assessment?
Place the information security assessment steps on the left next to the numbered boxes on the right in the correct order.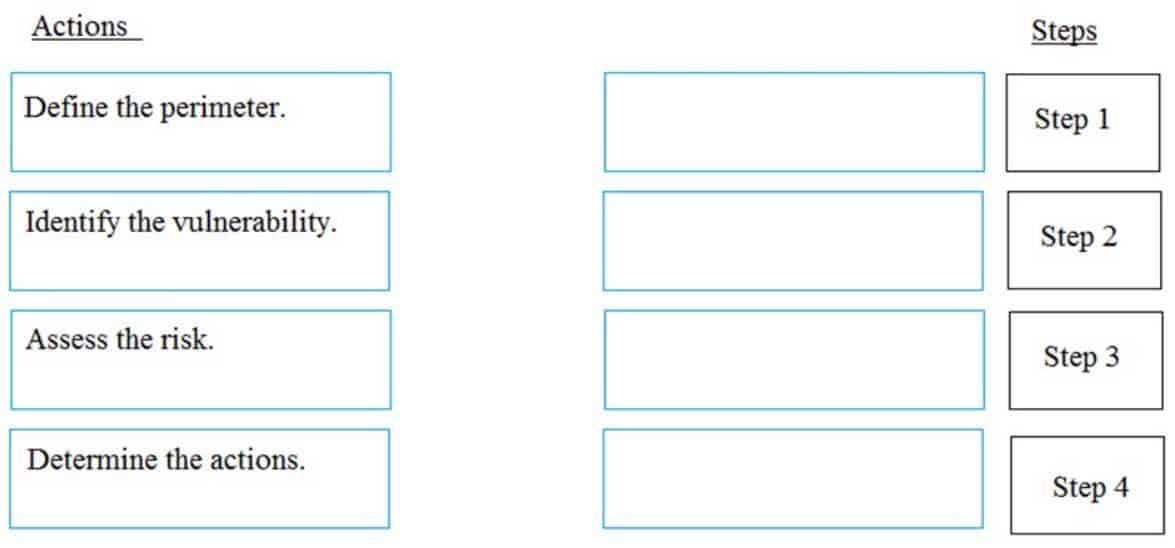
CISSP Certified Information Systems Security Professional Part 14 Q07 002 Question 
CISSP Certified Information Systems Security Professional Part 14 Q07 002 Answer -
What MUST each information owner do when a system contains data from multiple information owners?
- Provide input to the Information System (IS) owner regarding the security requirements of the data
- Review the Security Assessment report (SAR) for the Information System (IS) and authorize the IS to operate.
- Develop and maintain the System Security Plan (SSP) for the Information System (IS) containing the data
- Move the data to an Information System (IS) that does not contain data owned by other information owners
-
A vulnerability assessment report has been submitted to a client. The client indicates that one third of the hosts that were in scope are missing from the report.
In which phase of the assessment was this error MOST likely made?
- Enumeration
- Reporting
- Detection
- Discovery
-
Which of the following is a responsibility of the information owner?
- Ensure that users and personnel complete the required security training to access the Information System (IS)
- Defining proper access to the Information System (IS), including privileges or access rights
- Managing identification, implementation, and assessment of common security controls
- Ensuring the Information System (IS) is operated according to agreed upon security requirements
-
Which of the following explains why classifying data is an important step in performing a risk assessment?
- To provide a framework for developing good security metrics
- To justify the selection of costly security controls
- To classify the security controls sensitivity that helps scope the risk assessment
- To help determine the appropriate level of data security controls
-
Which of the following activities is MOST likely to be performed during a vulnerability assessment?
- Establish caller authentication procedures to verify the identities of users
- Analyze the environment by conducting interview sessions with relevant parties
- Document policy exceptions required to access systems in non-compliant areas
- Review professional credentials of the vulnerability assessment team or vendor
-
What is the PRIMARY objective of an application security assessment?
- Obtain information security management approval
- Maintain the integrity of the application
- Obtain feedback before implementation
- Identify vulnerabilities
-
Which of the following is an accurate statement when an assessment results in the discovery of vulnerabilities in a critical network component?
- There is little likelihood that the entire network is being placed at a significant risk of attack
- There is a low possibility that any adjacently connected components have been compromised by an attacker
- A second assessment should immediately be performed after all vulnerabilities are corrected
- The fact that every other host is sufficiently hardened does not change the fact that the network is placed at risk of attack
-
Following a penetration test, what should an organization do FIRST?
- Review all security policies and procedures
- Ensure staff is trained in security
- Determine if you need to conduct a full security assessment
- Evaluate the problems identified in the test result
-
An organization is outsourcing its payroll system and is requesting to conduct a full audit on the third-party Information Technology (IT) systems. During the due diligence process, the third party provides previous audit reports on its IT systems.
Which of the following MUST be considered by the organization in order for the audit reports to be acceptable?
- The audit reports have been issued in the last six months
- The audit assessment has been conducted by an independent assessor
- The audit assessment has been conducted by an international audit firm
- The audit reports have been signed by the third-party senior management
-
What requirement MUST be met during internal security audits to ensure that all information provided is expressed as an objective assessment without risk of retaliation?
- The auditor must be independent and report directly to the management
- The auditor must utilize automated tools to back their findings
- The auditor must work closely with both the Information Technology (IT) and security sections of an organization
- The auditor must perform manual reviews of systems and processes
-
A security engineer is designing a Customer Relationship Management (CRM) application for a third-party vendor. In which phase of the System Development Life Cycle (SDLC) will it be MOST beneficial to conduct a data sensitivity assessment?
- Development / Acquisition
- Initiation
- Enumeration
- Operation / Maintenance
-
Which of the following is the MOST effective preventative method to identify security flaws in software?
- Monitor performance in production environments
- Perform a structured code review
- Perform application penetration testing
- Use automated security vulnerability testing tools
-
Which of the following phases involves researching a target’s configuration from public sources when performing a penetration test?
- Information gathering
- Social engineering
- Target selection
- Traffic enumeration