CISSP : Certified Information Systems Security Professional : Part 16
CISSP : Certified Information Systems Security Professional : Part 16
-
A continuous information security monitoring program can BEST reduce risk through which of the following?
- Collecting security events and correlating them to identify anomalies
- Facilitating system-wide visibility into the activities of critical user accounts
- Encompassing people, process, and technology
- Logging both scheduled and unscheduled system changes
-
What would be the MOST cost effective solution for a Disaster Recovery (DR) site given that the organization’s systems cannot be unavailable for more than 24 hours?
- Warm site
- Hot site
- Mirror site
- Cold site
-
Who is accountable for the information within an Information System (IS)?
- Security manager
- System owner
- Data owner
- Data processor
-
It is MOST important to perform which of the following to minimize potential impact when implementing a new vulnerability scanning tool in a production environment?
- Negotiate schedule with the Information Technology (IT) operation’s team
- Log vulnerability summary reports to a secured server
- Enable scanning during off-peak hours
- Establish access for Information Technology (IT) management
-
A Security Operations Center (SOC) receives an incident response notification on a server with an active intruder who has planted a backdoor. Initial notifications are sent and communications are established.
What MUST be considered or evaluated before performing the next step?
- Notifying law enforcement is crucial before hashing the contents of the server hard drive
- Identifying who executed the incident is more important than how the incident happened
- Removing the server from the network may prevent catching the intruder
- Copying the contents of the hard drive to another storage device may damage the evidence
-
Due to system constraints, a group of system administrators must share a high-level access set of credentials.
Which of the following would be MOST appropriate to implement?
- Increased console lockout times for failed logon attempts
- Reduce the group in size
- A credential check-out process for a per-use basis
- Full logging on affected systems
-
Which of the following is the MOST efficient mechanism to account for all staff during a speedy non-emergency evacuation from a large security facility?
- Large mantrap where groups of individuals leaving are identified using facial recognition technology
- Radio Frequency Identification (RFID) sensors worn by each employee scanned by sensors at each exit door
- Emergency exits with push bars with coordinates at each exit checking off the individual against a predefined list
- Card-activated turnstile where individuals are validated upon exit
-
What does electronic vaulting accomplish?
- It protects critical files.
- It ensures the fault tolerance of Redundant Array of Independent Disks (RAID) systems
- It stripes all database records
- It automates the Disaster Recovery Process (DRP)
-
Who would be the BEST person to approve an organizations information security policy?
- Chief Information Officer (CIO)
- Chief Information Security Officer (CISO)
- Chief internal auditor
- Chief Executive Officer (CEO)
-
A security analyst for a large financial institution is reviewing network traffic related to an incident. The analyst determines the traffic is irrelevant to the investigation but in the process of the review, the analyst also finds that an applications data, which included full credit card cardholder data, is transferred in clear text between the server and user’s desktop. The analyst knows this violates the Payment Card Industry Data Security Standard (PCI-DSS). Which of the following is the analyst’s next step?
- Send the log file co-workers for peer review
- Include the full network traffic logs in the incident report
- Follow organizational processes to alert the proper teams to address the issue.
- Ignore data as it is outside the scope of the investigation and the analyst’s role.
-
An Information Technology (IT) professional attends a cybersecurity seminar on current incident response methodologies.
What code of ethics canon is being observed?
- Provide diligent and competent service to principals
- Protect society, the commonwealth, and the infrastructure
- Advance and protect the profession
- Act honorable, honesty, justly, responsibly, and legally
-
An organization adopts a new firewall hardening standard. How can the security professional verify that the technical staff correct implemented the new standard?
- Perform a compliance review
- Perform a penetration test
- Train the technical staff
- Survey the technical staff
-
What is the MAIN purpose of a change management policy?
- To assure management that changes to the Information Technology (IT) infrastructure are necessary
- To identify the changes that may be made to the Information Technology (IT) infrastructure
- To verify that changes to the Information Technology (IT) infrastructure are approved
- To determine the necessary for implementing modifications to the Information Technology (IT) infrastructure
-
DRAG DROP
Match the functional roles in an external audit to their responsibilities.
Drag each role on the left to its corresponding responsibility on the right.
CISSP Certified Information Systems Security Professional Part 16 Q14 003 Question 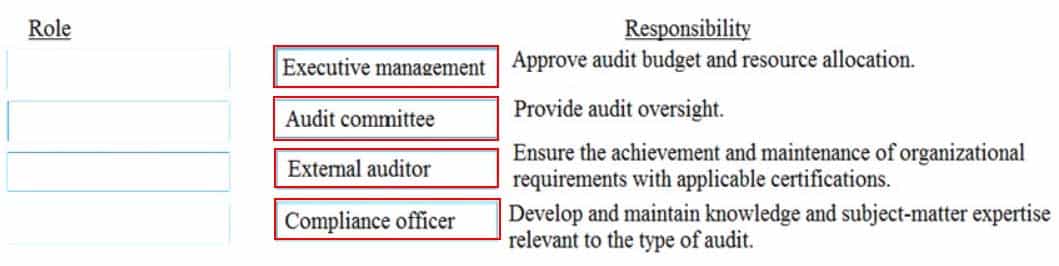
CISSP Certified Information Systems Security Professional Part 16 Q14 003 Answer -
Who is responsible for the protection of information when it is shared with or provided to other organizations?
- Systems owner
- Authorizing Official (AO)
- Information owner
- Security officer
-
Which of the following is the MOST challenging issue in apprehending cyber criminals?
- They often use sophisticated method to commit a crime.
- It is often hard to collect and maintain integrity of digital evidence.
- The crime is often committed from a different jurisdiction.
- There is often no physical evidence involved.
-
What is the BEST way to correlate large volumes of disparate data sources in a Security Operations Center (SOC) environment?
- Implement Intrusion Detection System (IDS)
- Implement a Security Information and Event Management (SIEM) system
- Hire a team of analysts to consolidate data and generate reports
- Outsource the management of the SOC
-
Which of the following factors is a PRIMARY reason to drive changes in an Information Security Continuous Monitoring (ISCM) strategy?
- Testing and Evaluation (TE) personnel changes
- Changes to core missions or business processes
- Increased Cross-Site Request Forgery (CSRF) attacks
- Changes in Service Organization Control (SOC) 2 reporting requirements
-
In fault-tolerant systems, what do rollback capabilities permit?
- Identifying the error that caused the problem
- Isolating the error that caused the problem
- Allowing the system to run in a reduced manner
- Restoring the system to a previous functional state
-
During a Disaster Recovery (DR) simulation, it is discovered that the shared recovery site lacks adequate data restoration capabilities to support the implementation of multiple plans simultaneously.
What would be impacted by this fact if left unchanged?
- Recovery Point Objective (RPO)
- Recovery Time Objective (RTO)
- Business Impact Analysis (BIA)
- Return on Investment (ROI)