CISSP : Certified Information Systems Security Professional : Part 21
CISSP : Certified Information Systems Security Professional : Part 21
-
Reciprocal backup site agreements are considered to be
- a better alternative than the use of warm sites.
- difficult to test for complex systems.
- easy to implement for similar types of organizations.
- easy to test and implement for complex systems.
-
In which identity management process is the subject’s identity established?
- Trust
- Provisioning
- Authorization
- Enrollment
-
In order to assure authenticity, which of the following are required?
- Confidentiality and authentication
- Confidentiality and integrity
- Authentication and non-repudiation
- Integrity and non-repudiation
-
At which layer of the Open Systems Interconnect (OSI) model are the source and destination address for a datagram handled?
- Transport Layer
- Data-Link Layer
- Network Layer
- Application Layer
-
An organization regularly conducts its own penetration tests. Which of the following scenarios MUST be covered for the test to be effective?
- Third-party vendor with access to the system
- System administrator access compromised
- Internal attacker with access to the system
- Internal user accidentally accessing data
-
A company was ranked as high in the following National Institute of Standards and Technology (NIST) functions: Protect, Detect, Respond and Recover. However, a low maturity grade was attributed to the Identify function. In which of the following the controls categories does this company need to improve when analyzing its processes individually?
- Asset Management, Business Environment, Governance and Risk Assessment
- Access Control, Awareness and Training, Data Security and Maintenance
- Anomalies and Events, Security Continuous Monitoring and Detection Processes
- Recovery Planning, Improvements and Communications
-
What is the difference between media marking and media labeling?
- Media marking refers to the use of human-readable security attributes, while media labeling refers to the use of security attributes in internal data structures.
- Media labeling refers to the use of human-readable security attributes, while media marking refers to the use of security attributes in internal data structures.
- Media labeling refers to security attributes required by public policy/law, while media marking refers to security required by internal organizational policy.
- Media marking refers to security attributes required by public policy/law, while media labeling refers to security attributes required by internal organizational policy.
-
What balance MUST be considered when web application developers determine how informative application error messages should be constructed?
- Risk versus benefit
- Availability versus auditability
- Confidentiality versus integrity
- Performance versus user satisfaction
-
What operations role is responsible for protecting the enterprise from corrupt or contaminated media?
- Information security practitioner
- Information librarian
- Computer operator
- Network administrator
-
Which of the following is a characteristic of the initialization vector when using Data Encryption Standard (DES)?
- It must be known to both sender and receiver.
- It can be transmitted in the clear as a random number.
- It must be retained until the last block is transmitted.
- It can be used to encrypt and decrypt information.
-
DRAG DROP
Match the access control type to the example of the control type.
Drag each access control type net to its corresponding example.
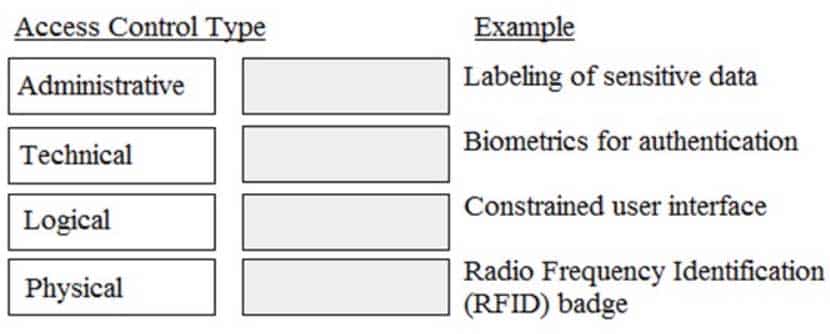
CISSP Certified Information Systems Security Professional Part 21 Q11 005 Question 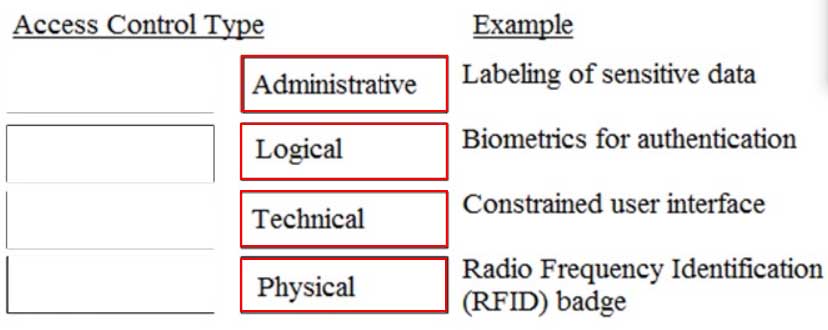
CISSP Certified Information Systems Security Professional Part 21 Q11 005 Answer -
In general, servers that are facing the Internet should be placed in a demilitarized zone (DMZ). What is MAIN purpose of the DMZ?
- Reduced risk to internal systems.
- Prepare the server for potential attacks.
- Mitigate the risk associated with the exposed server.
- Bypass the need for a firewall.
-
Network-based logging has which advantage over host-based logging when reviewing malicious activity about a victim machine?
- Addresses and protocols of network-based logs are analyzed.
- Host-based system logging has files stored in multiple locations.
- Properly handled network-based logs may be more reliable and valid.
- Network-based systems cannot capture users logging into the console.
-
Which of the following is the PRIMARY reason for employing physical security personnel at entry points in facilities where card access is in operation?
- To verify that only employees have access to the facility.
- To identify present hazards requiring remediation.
- To monitor staff movement throughout the facility.
- To provide a safe environment for employees.
-
Between which pair of Open System Interconnection (OSI) Reference Model layers are routers used as a communications device?
- Transport and Session
- Data-Link and Transport
- Network and Session
- Physical and Data-Link
-
Which type of security testing is being performed when an ethical hacker has no knowledge about the target system but the testing target is notified before the test?
- Reversal
- Gray box
- Blind
- White box
-
Which of the following countermeasures is the MOST effective in defending against a social engineering attack?
- Mandating security policy acceptance
- Changing individual behavior
- Evaluating security awareness training
- Filtering malicious e-mail content
-
Which of the following information MUST be provided for user account provisioning?
- Full name
- Unique identifier
- Security question
- Date of birth
-
Which of the following adds end-to-end security inside a Layer 2 Tunneling Protocol (L2TP) Internet Protocol Security (IPSec) connection?
- Temporal Key Integrity Protocol (TKIP)
- Secure Hash Algorithm (SHA)
- Secure Shell (SSH)
- Transport Layer Security (TLS)
-
A company has decided that they need to begin maintaining assets deployed in the enterprise. What approach should be followed to determine and maintain ownership information to bring the company into compliance?
- Enterprise asset management framework
- Asset baseline using commercial off the shelf software
- Asset ownership database using domain login records
- A script to report active user logins on assets