CISSP : Certified Information Systems Security Professional : Part 22
CISSP : Certified Information Systems Security Professional : Part 22
-
In the Software Development Life Cycle (SDLC), maintaining accurate hardware and software inventories is a critical part of
- systems integration.
- risk management.
- quality assurance.
- change management.
-
As a best practice, the Security Assessment Report (SAR) should include which of the following sections?
- Data classification policy
- Software and hardware inventory
- Remediation recommendations
- Names of participants
-
The application of a security patch to a product previously validate at Common Criteria (CC) Evaluation Assurance Level (EAL) 4 would
- require an update of the Protection Profile (PP).
- require recertification.
- retain its current EAL rating.
- reduce the product to EAL 3.
-
Which of the following media sanitization techniques is MOST likely to be effective for an organization using public cloud services?
- Low-level formatting
- Secure-grade overwrite erasure
- Cryptographic erasure
- Drive degaussing
-
What type of wireless network attack BEST describes an Electromagnetic Pulse (EMP) attack?
- Radio Frequency (RF) attack
- Denial of Service (DoS) attack
- Data modification attack
- Application-layer attack
-
DRAG DROP
Match the types of e-authentication tokens to their description.
Drag each e-authentication token on the left to its corresponding description on the right.
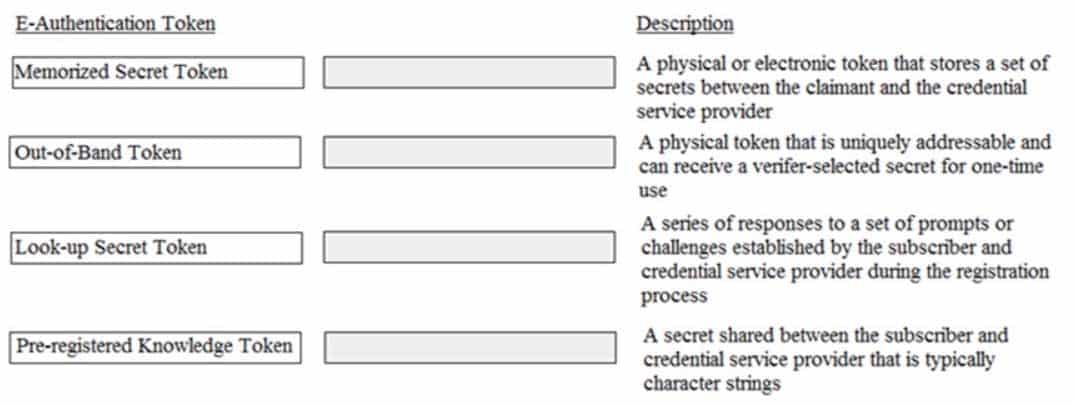
CISSP Certified Information Systems Security Professional Part 22 Q06 006 Question 
CISSP Certified Information Systems Security Professional Part 22 Q06 006 Answer -
Which of the following is a remote access protocol that uses a static authentication?
- Point-to-Point Tunneling Protocol (PPTP)
- Routing Information Protocol (RIP)
- Password Authentication Protocol (PAP)
- Challenge Handshake Authentication Protocol (CHAP)
-
Which of the following sets of controls should allow an investigation if an attack is not blocked by preventive controls or detected by monitoring?
- Logging and audit trail controls to enable forensic analysis
- Security incident response lessons learned procedures
- Security event alert triage done by analysts using a Security Information and Event Management (SIEM) system
- Transactional controls focused on fraud prevention
-
Determining outage costs caused by a disaster can BEST be measured by the
- cost of redundant systems and backups.
- cost to recover from an outage.
- overall long-term impact of the outage.
- revenue lost during the outage.
-
Which of the following is considered a secure coding practice?
- Use concurrent access for shared variables and resources
- Use checksums to verify the integrity of libraries
- Use new code for common tasks
- Use dynamic execution functions to pass user supplied data
-
As part of the security assessment plan, the security professional has been asked to use a negative testing strategy on a new website. Which of the following actions would be performed?
- Use a web scanner to scan for vulnerabilities within the website.
- Perform a code review to ensure that the database references are properly addressed.
- Establish a secure connection to the web server to validate that only the approved ports are open.
- Enter only numbers in the web form and verify that the website prompts the user to enter a valid input.
-
Who has the PRIMARY responsibility to ensure that security objectives are aligned with organization goals?
- Senior management
- Information security department
- Audit committee
- All users
-
Which of the following alarm systems is recommended to detect intrusions through windows in a high-noise, occupied environment?
- Acoustic sensor
- Motion sensor
- Shock sensor
- Photoelectric sensor
-
Which of the following is the MOST effective practice in managing user accounts when an employee is terminated?
- Implement processes for automated removal of access for terminated employees.
- Delete employee network and system IDs upon termination.
- Manually remove terminated employee user-access to all systems and applications.
- Disable terminated employee network ID to remove all access.
-
Which of the following is the MOST important part of an awareness and training plan to prepare employees for emergency situations?
- Having emergency contacts established for the general employee population to get information
- Conducting business continuity and disaster recovery training for those who have a direct role in the recovery
- Designing business continuity and disaster recovery training programs for different audiences
- Publishing a corporate business continuity and disaster recovery plan on the corporate website
-
What is the process of removing sensitive data from a system or storage device with the intent that the data cannot be reconstructed by any known technique?
- Purging
- Encryption
- Destruction
- Clearing
-
Which one of the following considerations has the LEAST impact when considering transmission security?
- Network availability
- Node locations
- Network bandwidth
- Data integrity
-
The security accreditation task of the System Development Life Cycle (SDLC) process is completed at the end of which phase?
- System acquisition and development
- System operations and maintenance
- System initiation
- System implementation
-
DRAG DROP
Drag the following Security Engineering terms on the left to the BEST definition on the right.
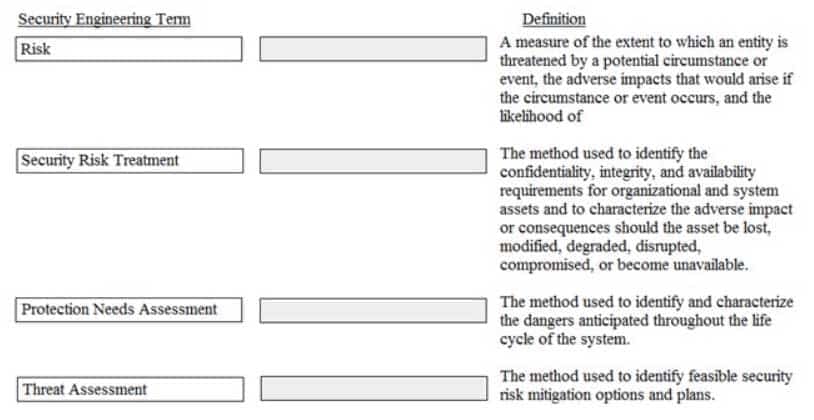
CISSP Certified Information Systems Security Professional Part 22 Q19 007 Question 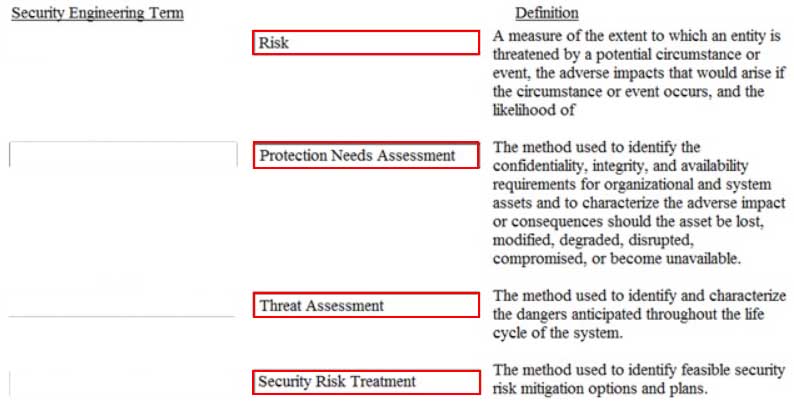
CISSP Certified Information Systems Security Professional Part 22 Q19 007 Answer -
Which of the following is the BEST reason for the use of security metrics?
- They ensure that the organization meets its security objectives.
- They provide an appropriate framework for Information Technology (IT) governance.
- They speed up the process of quantitative risk assessment.
- They quantify the effectiveness of security processes.