CISSP : Certified Information Systems Security Professional : Part 27
CISSP : Certified Information Systems Security Professional : Part 27
-
Why might a network administrator choose distributed virtual switches instead of stand-alone switches for network segmentation?
- To standardize on a single vendor
- To ensure isolation of management traffic
- To maximize data plane efficiency
- To reduce the risk of configuration errors
-
DRAG DROP
Match the following generic software testing methods with their major focus and objective.
Drag each testing method next to its corresponding set of testing objectives.
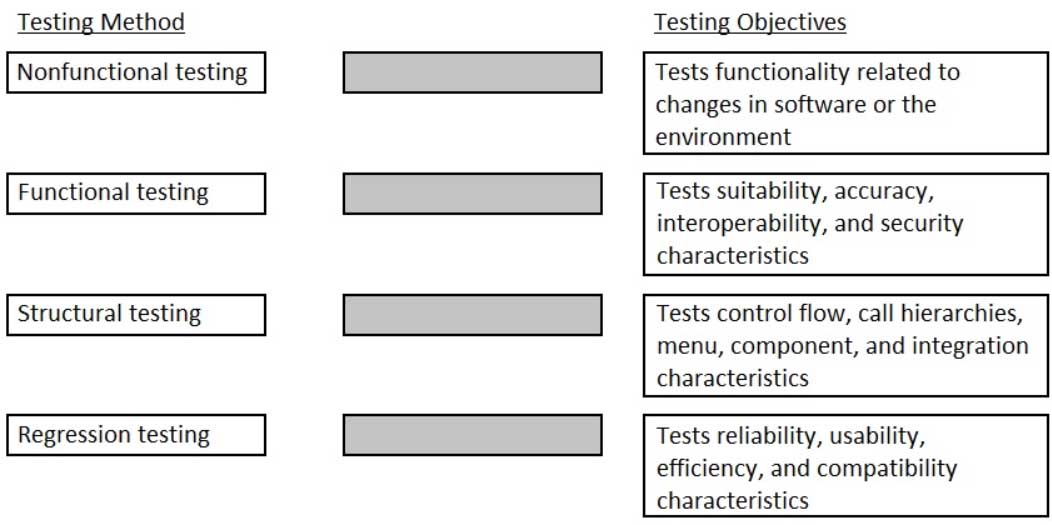
CISSP Certified Information Systems Security Professional Part 27 Q02 008 Question 
CISSP Certified Information Systems Security Professional Part 27 Q02 008 Answer Explanation:Reference:
https://www.tutorialride.com/software-testing/software-test-types.htm -
Which of the following is the BEST reason to apply patches manually instead of automated patch management?
- The cost required to install patches will be reduced.
- The time during which systems will remain vulnerable to an exploit will be decreased.
- The target systems reside within isolated networks.
- The ability to cover large geographic areas is increased.
-
When should the software Quality Assurance (QA) team feel confident that testing is complete?
- When release criteria are met
- When the time allocated for testing the software is met
- When senior management approves the test results
- When the software has zero security vulnerabilities
-
A system administration office desires to implement the following rules:
– An administrator that is designated as a skill level 3, with 5 years of experience, is allowed to perform system backups, upgrades, and local administration.
– An administrator that is designated as a skill level 5, with 10 years of experience, is permitted to perform all actions related to system administration.Which of the following access control methods MUST be implemented to achieve this goal?
- Discretionary Access Control (DAC)
- Role Based Access Control (RBAC)
- Mandatory Access Control (MAC)
- Attribute Based Access Control (ABAC)
-
Which of the following MUST a security policy include to be effective within an organization?
- A list of all standards that apply to the policy
- Owner information and date of last revision
- Disciplinary measures for non-compliance
- Strong statements that clearly define the problem
-
What is the MOST efficient way to verify the integrity of database backups?
- Test restores on a regular basis.
- Restore every file in the system to check its health.
- Use checksum as part of the backup operation to make sure that no corruption has occurred.
- Run DBCC CHECKDB on a regular basis to check the logical and physical integrity of the database objects.
-
What information will BEST assist security and financial analysts in determining if a security control is cost effective to mitigate a vulnerability?
- Annualized Loss Expectancy (ALE) and the cost of the control
- Single Loss Expectancy (SLE) and the cost of the control
- Annual Rate of Occurrence (ARO) and the cost of the control
- Exposure Factor (EF) and the cost of the control
-
Which of the following are the FIRST two steps to securing employees from threats involving workplace violence and acts of terrorism?
- Physical barriers impeding unauthorized access and security guards at each entrance
- Physical barriers and the ability to identify people as they enter the workplace
- Security guards and metal detectors posted at each entrance
- Metal detectors and the ability to identify people as they enter the workplace
-
Which step of the Risk Management Framework (RMF) identifies the initial set of baseline security controls?
- Selection
- Monitoring
- Implementation
- Assessment
Explanation:Reference: https://csrc.nist.gov/projects/risk-management/risk-management-framework-(RMF)-Overview -
How can an attacker exploit a stack overflow to execute arbitrary code?
- Modify a function’s return address.
- Move the stack pointer
- Substitute elements in the stack.
- Alter the address of the stack.
-
What is the MAIN reason for having a developer sign a Non-Disclosure Agreement (NDA)?
- Signing the NDA always gives consent to the developer to access tools and privileged company information to do their work.
- Signing the NDA allows the developer to use their developed coding methods.
- Signing the NDA protects confidential, technical, or Intellectual Property (IP) from disclosure to others.
- Signing the NDA is legally binding for up to one year of employment.
-
Which of the following provides for the STRONGEST protection of data confidentiality in a Wi-Fi environment?
- Wi-Fi Protected Access (WPA) + Temporal Key Integrity Protocol (TKIP)
- Wi-Fi Protected Access 2 (WPA2) + Advanced Encryption Standard (AES)
- Wi-Fi Protected Access 2 (WPA2) + Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP)
- Wired Equivalent Privacy (WEP) + Advanced Encryption Standard (AES)
-
What is a consideration when determining the potential impact an organization faces in the event of the loss of confidentiality of Personally Identifiable Information (PII)?
- Quantity
- Availability
- Quality
- Criticality
Explanation:Reference: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-122.pdf -
A security practitioner has just been assigned to address an ongoing Denial of Service (DoS) attack against the company’s network, which includes an e-commerce web site. The strategy has to include defenses for any size of attack without rendering the company network unusable. Which of the following should be a PRIMARY concern when addressing this issue?
- Deal with end user education and training.
- Pay more for a dedicated path to the Internet.
- Allow legitimate connections while blocking malicious connections.
- Ensure the web sites are properly backed up on a daily basis.
-
A security team member was selected as a member of a Change Control Board (CCB) for an organization. Which of the following is one of their responsibilities?
- Approving or disapproving the change
- Determining the impact of the change
- Carrying out the requested change
- Logging the change
-
Which action is MOST effective for controlling risk and minimizing maintenance costs in the software supply chain?
- Selecting redundant suppliers
- Selecting suppliers based on business requirements
- Selecting fewer, more reliable suppliers
- Selecting software suppliers with the fewest known vulnerabilities
-
A group of organizations follows the same access standards and practices. One manages the verification and due diligence processes for the others. For a user to access a resource from one of the organizations, a check is made to see if that user has been certified. Which Federated Identity Management (FIM) process is this an example of?
- One-time authentication
- Web based access management
- Cross-certification model
- Bridge model
-
A data owner determines the appropriate job-based access for an employee to perform their duties. Which type of access control is this?
- Discretionary Access Control (DAC)
- Non-discretionary access control
- Mandatory Access Control (MAC)
- Role-based access control (RBAC)
Explanation:Reference: https://searchsecurity.techtarget.com/definition/role-based-access-control-RBAC -
The process of “salting” a password is designed to increase the difficulty of cracking which of the following?
-
- Specific password
- Password hash function
- Password algorithm
- Maximum password length
Explanation:Reference: https://auth0.com/blog/adding-salt-to-hashing-a-better-way-to-store-passwords/