SSCP : System Security Certified Practitioner (SSCP) : Part 25
SSCP : System Security Certified Practitioner (SSCP) : Part 25
-
Which of the following was designed as a more fault-tolerant topology than Ethernet, and very resilient when properly implemented?
- Token Link.
- Token system.
- Token Ring.
- Duplicate ring.
Explanation:
Token Ring was designed to be a more fault-tolerant topology than Ethernet, and can be a very resilient topology when properly implemented.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 72. -
Which of the following is a token-passing scheme like token ring that also has a second ring that remains dormant until an error condition is detected on the primary ring?
- Fiber Distributed Data Interface (FDDI).
- Ethernet
- Fast Ethernet
- Broadband
Explanation:FDDI is a token-passing ring scheme like a token ring, yet it also has a second ring that remains dormant until an error condition is detected on the primary ring.
Fiber Distributed Data Interface (FDDI) provides a 100 Mbit/s optical standard for data transmission in a local area network that can extend in range up to 200 kilometers (124 miles). Although FDDI logical topology is a ring-based token network, it does not use the IEEE 802.5 token ring protocol as its basis; instead, its protocol is derived from the IEEE 802.4 token bus timed token protocol. In addition to covering large geographical areas, FDDI local area networks can support thousands of users. As a standard underlying medium it uses optical fiber, although it can use copper cable, in which case it may be refer to as CDDI (Copper Distributed Data Interface). FDDI offers both a Dual-Attached Station (DAS), counter-rotating token ring topology and a Single-Attached Station (SAS), token bus passing ring topology.
Ethernet is a family of frame-based computer networking technologies for local area networks (LANs). The name came from the physical concept of the ether. It defines a number of wiring and signaling standards for the Physical Layer of the OSI networking model as well as a common addressing format and Media Access Control at the Data Link Layer.
In computer networking, Fast Ethernet is a collective term for a number of Ethernet standards that carry traffic at the nominal rate of 100 Mbit/s, against the original Ethernet speed of 10 Mbit/s. Of the fast Ethernet standards 100BASE-TX is by far the most common and is supported by the vast majority of Ethernet hardware currently produced. Fast Ethernet was introduced in 1995 and remained the fastest version of Ethernet for three years before being superseded by gigabit Ethernet.
Broadband in data can refer to broadband networks or broadband Internet and may have the same meaning as above, so that data transmission over a fiber optic cable would be referred to as broadband as compared to a telephone modem operating at 56,000 bits per second. However, a worldwide standard for what level of bandwidth and network speeds actually constitute Broadband have not been determined.[1]
Broadband in data communications is frequently used in a more technical sense to refer to data transmission where multiple pieces of data are sent simultaneously to increase the effective rate of transmission, regardless of data signaling rate. In network engineering this term is used for methods where two or more signals share a medium.[Broadband Internet access, often shortened to just broadband, is a high data rate Internet access—typically contrasted with dial-up access using a 56k modem.
Dial-up modems are limited to a bitrate of less than 56 kbit/s (kilobits per second) and require the full use of a telephone line—whereas broadband technologies supply more than double this rate and generally without disrupting telephone use.
Source:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 72.also see:
http://en.wikipedia.org/ -
What is called an attack in which an attacker floods a system with connection requests but does not respond when the target system replies to those requests?
- Ping of death attack
- SYN attack
- Smurf attack
- Buffer overflow attack
Explanation:A SYN attack occurs when an attacker floods the target system’s small “in-process” queue with connection requests, but it does not respond when the target system replies to those requests. This causes the target system to “time out” while waiting for the proper response, which makes the system crash or become unusable. A buffer overflow attack occurs when a process receives much more data than expected. One common buffer overflow attack is the ping of death, where an attacker sends IP packets that exceed the maximum legal length (65535 octets). A smurf attack is an attack where the attacker spoofs the source IP address in an ICMP ECHO broadcast packet so it seems to have originated at the victim’s system, in order to flood it with REPLY packets.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 76). -
What type of attack involves IP spoofing, ICMP ECHO and a bounce site?
- IP spoofing attack
- Teardrop attack
- SYN attack
- Smurf attack
Explanation:A smurf attack occurs when an attacker sends a spoofed (IP spoofing) PING (ICMP ECHO) packet to the broadcast address of a large network (the bounce site). The modified packet containing the address of the target system, all devices on its local network respond with a ICMP REPLY to the target system, which is then saturated with those replies. An IP spoofing attack is used to convince a system that it is communication with a known entity that gives an intruder access. It involves modifying the source address of a packet for a trusted source’s address. A teardrop attack consists of modifying the length and fragmentation offset fields in sequential IP packets so the target system becomes confused and crashes after it receives contradictory instructions on how the fragments are offset on these packets. A SYN attack is when an attacker floods a system with connection requests but does not respond when the target system replies to those requests.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 76). -
What is a TFTP server most useful for?
- Transferring configurations to and from network devices.
- Transferring files to web servers.
- Terminal access to network devices.
- Terminal access to file servers.
Explanation:A Trivial File Transfer Protocol (TFTP) server can be used when configuring network devices to transfer configurations to and from network devices. Many networking devices now support TFTP.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 73). -
Which type of attack consists of modifying the length and fragmentation offset fields in sequential IP packets?
- Teardrop attack
- Smurf attack
- SYN attack
- Buffer overflow attack
Explanation:A teardrop attack consists of modifying the length and fragmentation offset fields in sequential IP packets so the target system becomes confused and crashes after it receives contradictory instructions on how the fragments are offset on these packets. A SYN attack is when an attacker floods a system with connection requests but does not respond when the target system replies to those requests. A smurf attack is an attack where the attacker spoofs the source IP address in an ICMP ECHO broadcast packet so it seems to have originated at the victim’s system, in order to flood it with REPLY packets. A buffer overflow attack occurs when a process receives much more data than expected.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 76). -
Which layer of the DoD TCP/IP Model ensures error-free delivery and packet sequencing?
- Internet layer
- Network access layer
- Host-to-host
- Application layer
Explanation:This layer of the DoD Model is also sometimes called Transport in some books but the proper name is Host-to-Host as per the RFC document.
The host-to-host layer provides for reliable end-to-end communications, ensures the data’s error-free delivery, handles the data’s packet sequencing, and maintains the data’s integrity.
It is comparable to the transport layer of the OSI model.
Reference(s) used for this question:
http://en.wikipedia.org/wiki/Internet_protocol_suite
and
http://technet.microsoft.com/en-us/library/cc786900%28v=ws.10%29.aspx
and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85). -
Which of the following is NOT a VPN communications protocol standard?
- Point-to-point tunnelling protocol (PPTP)
- Challenge Handshake Authentication Protocol (CHAP)
- Layer 2 tunnelling protocol (L2TP)
- IP Security
Explanation:CHAP is an authentication mechanism for point-to-point protocol connections that encrypt the user’s password. It is a protocol that uses a three-way handshake. The server sends the client a challenge, which includes a random value (a nonce) to thwart replay attacks. The client responds with a MD5 hash of the nonce and the password. The authentication is successful if the client’s response is the one that the server expected.
The VPN communication protocol standards listed above are PPTP, L2TP and IPSec.
PPTP and L2TP operate at the data link layer (layer 2) of the OSI model and enable only a single point-to-point connection per session.
The following are incorrect answers:
PPTP uses native PPP authentication and encryption services. Point-to-Point Tunneling Protocol (PPTP) is a VPN protocol that runs over other protocols. PPTP relies on generic routing encapsulation (GRE) to build the tunnel between the endpoints. After the user authenticates, typically with Microsoft Challenge Handshake Authentication Protocol version 2 (MSCHAPv2), a Point-to-Point Protocol (PPP) session creates a tunnel using GRE.
L2TP is a combination of PPTP and the earlier Layer 2 Forwarding protocol (L2F). Layer 2 Tunneling Protocol (L2TP) is a hybrid of Cisco’s Layer 2 Forwarding (L2F) and Microsoft’s PPTP. It allows callers over a serial line using PPP to connect over the Internet to a remote network. A dial-up user connects to his ISP’s L2TP access concentrator (LAC) with a PPP connection. The LAC encapsulates the PPP packets into L2TP and forwards it to the remote network’s layer 2 network server (LNS). At this point, the LNS authenticates the dial-up user. If authentication is successful, the dial-up user will have access to the remote network.
IPSec operates at the network layer (layer 3) and enables multiple simultaneous tunnels. IP Security (IPSec) is a suite of protocols for communicating securely with IP by providing mechanisms for authenticating and encryption. Implementation of IPSec is mandatory in IPv6, and many organizations are using it over IPv4. Further, IPSec can be implemented in two modes, one that is appropriate for end-to-end protection and one that safeguards traffic between networks.
Reference used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 7067-7071). Auerbach Publications. Kindle Edition.
and
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 6987-6990). Auerbach Publications. Kindle Edition. -
What layer of the OSI/ISO model does Point-to-point tunnelling protocol (PPTP) work at?
- Data link layer
- Transport layer
- Session layer
- Network layer
Explanation:PPTP operates at the data link layer (layer 2) of the OSI model and uses native PPP authentication and encryption services. Designed for individual client to server connections, it enables only a single point-to-point connection per session.
PPTP – Point-to-Point Tunneling Protocol – extends the Point to Point Protocol (PPP) standard for traditional dial-up networking. PPTP is best suited for the remote access applications of VPNs, but it also supports LAN internetworking.
PPTP operates at Layer 2 of the OSI model.Using PPTP
PPTP packages data within PPP packets, then encapsulates the PPP packets within IP packets (datagrams) for transmission through an Internet-based VPN tunnel. PPTP supports data encryption and compression of these packets. PPTP also uses a form of General Routing Encapsulation (GRE) to get data to and from its final destination.Reference(s) used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 95).
and
http://compnetworking.about.com/od/vpn/l/aa030103a.htm
and
http://technet.microsoft.com/en-us/library/cc768084.aspx -
Which type of firewall can be used to track connectionless protocols such as UDP and RPC?
- Stateful inspection firewalls
- Packet filtering firewalls
- Application level firewalls
- Circuit level firewalls
Explanation:Packets in a stateful inspection firewall are queued and then analyzed at all OSI layers, providing a more complete inspection of the data. By examining the state and context of the incoming data packets, it helps to track the protocols that are considered “connectionless”, such as UDP-based applications and Remote Procedure Calls (RPC).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 91). -
Which of the following is the most secure firewall implementation?
- Dual-homed host firewalls
- Screened-subnet firewalls
- Screened-host firewalls
- Packet-filtering firewalls
Explanation:One the most secure implementations of firewall architectures is the screened-subnet firewall. It employs two packet-filtering routers and a bastion host. Like a screened host firewall, this firewall supports both packet-filtering and proxy services.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 93). -
Which IPSec operational mode encrypts the entire data packet (including header and data) into an IPSec packet?
- Authentication mode
- Tunnel mode
- Transport mode
- Safe mode
Explanation:In tunnel mode, the entire packet is encrypted and encased into an IPSec packet.
In transport mode, only the datagram (payload) is encrypted, leaving the IP address visible within the IP header.
Authentication mode and safe mode are not defined IPSec operational modes.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 96).
-
Which of the following category of UTP cables is specified to be able to handle gigabit Ethernet (1 Gbps) according to the EIA/TIA-568-B standards?
- Category 5e UTP
- Category 2 UTP
- Category 3 UTP
- Category 1e UTP
Explanation:Categories 1 through 6 are based on the EIA/TIA-568-B standards.
On the newer wiring for LANs is CAT5e, an improved version of CAT5 which used to be outside of the standard, for more information on twisted pair, please see: twisted pair.
Category Cable Type Mhz Usage Speed
=============================================
CAT1 UTP Analog voice, Plain Old Telephone System (POTS)
CAT2 UTP 4 Mbps on Token Ring, also used on Arcnet networks
CAT3 UTP, ScTP, STP 16 MHz 10 Mbps
CAT4 UTP, ScTP, STP 20 MHz 16 Mbps on Token Ring Networks
CAT5 UTP, ScTP, STP 100 MHz 100 Mbps on ethernet, 155 Mbps on ATM
CAT5e UTP, ScTP, STP 100 MHz 1 Gbps (out of standard version, improved version of CAT5)
CAT6 UTP, ScTP, STP 250 MHz 10 Gbps
CAT7 ScTP, STP 600 M 100 GbpsCategory 6 has a minumum of 250 MHz of bandwidth. Allowing 10/100/1000 use with up to 100 meter cable length, along with 10GbE over shorter distances.
Category 6a or Augmented Category 6 has a minimum of 500 MHz of bandwidth. It is the newest standard and allows up to 10GbE with a length up to 100m.
Category 7 is a future cabling standard that should allow for up to 100GbE over 100 meters of cable. Expected availability is in 2013. It has not been approved as a cable standard, and anyone now selling you Cat. 7 cable is fooling you.
REFERENCES:
http://donutey.com/ethernet.php
http://en.wikipedia.org/wiki/TIA/EIA-568-B
http://en.wikipedia.org/wiki/Category_1_cable -
Which of the following statements pertaining to VPN protocol standards is false?
- L2TP is a combination of PPTP and L2F.
- L2TP and PPTP were designed for single point-to-point client to server communication.
- L2TP operates at the network layer.
- PPTP uses native PPP authentication and encryption services.
Explanation:L2TP and PPTP were both designed for individual client to server connections; they enable only a single point-to-point connection per session. Dial-up VPNs use L2TP often. Both L2TP and PPTP operate at the data link layer (layer 2) of the OSI model. PPTP uses native PPP authentication and encryption services and L2TP is a combination of PPTP and Layer 2 Forwarding protocol (L2F).
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 95).
-
Which OSI/ISO layer does a SOCKS server operate at?
- Session layer
- Transport layer
- Network layer
- Data link layer
Explanation:A SOCKS based server operates at the Session layer of the OSI model.
SOCKS is an Internet protocol that allows client-server applications to transparently use the services of a network firewall. SOCKS is an abbreviation for “SOCKetS”. As of Version 5 of SOCK, both UDP and TCP is supported.
One of the best known circuit-level proxies is SOCKS proxy server. The basic purpose of the protocol is to enable hosts on one side of a SOCKS server to gain access to hosts on the other side of a SOCKS Server, without requiring direct “IP-reachability”
The protocol was originally developed by David Koblas, a system administrator of MIPS Computer Systems. After MIPS was taken over by Silicon Graphics in 1992, Koblas presented a paper on SOCKS at that year’s Usenix Security Symposium and SOCKS became publicly available. The protocol was extended to version 4 by Ying-Da Lee of NEC.
SOCKS includes two components, the SOCKS server and the SOCKS client.
The SOCKS protocol performs four functions:
Making connection requests
Setting up proxy circuits
Relaying application data
Performing user authentication (optional)Source:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 96).
and
http://en.wikipedia.org/wiki/SOCKS
and
http://www.faqs.org/rfcs/rfc1928.html
and
The ISC2 OIG on page 619 -
Which of the following protocols is not implemented at the Internet layer of the TCP/IP protocol model?
- User datagram protocol (UDP)
- Internet protocol (IP)
- Internet Group Management Protocol (IGMP)
- Internet control message protocol (ICMP)
Explanation:The User Datagram Protocol (UDP) is implemented at the host-to-host transport layer, not at the internet layer.
Protocol at what layer?
Ensure you are familiar with both the OSI model and the DoD TCP/IP model as well. You need to know how to contrast the two side by side and what are the names being used on both side. Below you have a graphic showing the two and how things maps between the two as well as some of the most common protcolos found at each of the layers:
Protocols at what layers of the DoD TCP/IP model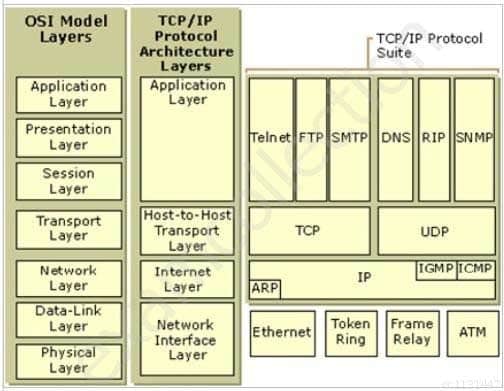
SSCP System Security Certified Practitioner (SSCP) Part 25 Q16 033 Graphic from http://technet.microsoft.com/en-us/library/cc958821.aspx
The following are incorrect answers:
All of the other protocols sit at the Internet Layer of the TCP/IP model.NOTE:
Some reference are calling the Transport layer on the DoD model Host-to-Host.Reference(s) used for this question:
Shon Harris, CISSP All In One (AIO), 6th edition , Telecommunication and Network Security, Page 518,534
and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85).
and
Microsoft Technet at http://technet.microsoft.com/en-us/library/cc958821.aspx -
Which protocol of the TCP/IP suite addresses reliable data transport?
- Transmission control protocol (TCP)
- User datagram protocol (UDP)
- Internet protocol (IP)
- Internet control message protocol (ICMP)
Explanation:TCP provides a full-duplex, connection-oriented, reliable, virtual circuit. It handles the sequencing and retransmission of lost packets.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85). -
Which layer of the TCP/IP protocol model would best correspond to the OSI/ISO model’s network layer?
- Network access layer
- Application layer
- Host-to-host transport layer
- Internet layer
Explanation:The Internet layer corresponds to the OSI’s network layer. It handles the routing of packets among multiple networks.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85). -
Which layer of the DoD TCP/IP model controls the communication flow between hosts?
- Internet layer
- Host-to-host transport layer
- Application layer
- Network access layer
Explanation:Whereas the host-to-host layer (equivalent to the OSI’s transport layer) provides end-to-end data delivery service, flow control, to the application layer.
The four layers in the DoD model, from top to bottom, are:
The Application Layer contains protocols that implement user-level functions, such as mail delivery, file transfer and remote login.
The Host-to-Host Layer handles connection rendez vous, flow control, retransmission of lost data, and other generic data flow management between hosts. The mutually exclusive TCP and UDP protocols are this layer’s most important members.
The Internet Layer is responsible for delivering data across a series of different physical networks that interconnect a source and destination machine. Routing protocols are most closely associated with this layer, as is the IP Protocol, the Internet’s fundamental protocol.
The Network Access Layer is responsible for delivering data over the particular hardware media in use. Different protocols are selected from this layer, depending on the type of physical network
The OSI model organizes communication services into seven groups called layers. The layers are as follows:Layer 7, The Application Layer: The application layer serves as a window for users and application processes to access network services. It handles issues such as network transparency, resource allocation, etc. This layer is not an application in itself, although some applications may perform application layer functions.
Layer 6, The Presentation Layer: The presentation layer serves as the data translator for a network. It is usually a part of an operating system and converts incoming and outgoing data from one presentation format to another. This layer is also known as syntax layer.
Layer 5, The Session Layer: The session layer establishes a communication session between processes running on different communication entities in a network and can support a message-mode data transfer. It deals with session and connection coordination.
Layer 4, The Transport Layer: The transport layer ensures that messages are delivered in the order in which they are sent and that there is no loss or duplication. It ensures complete data transfer. This layer provides an additional connection below the Session layer and assists with managing some data flow control between hosts. Data is divided into packets on the sending node, and the receiving node’s Transport layer reassembles the message from packets. This layer is also responsible for error checking to guarantee error-free data delivery, and requests a retransmission if necessary. It is also responsible for sending acknowledgments of successful transmissions back to the sending host. A number of protocols run at the Transport layer, including TCP, UDP, Sequenced Packet Exchange (SPX), and NWLink.
Layer 3, The Network Layer: The network layer controls the operation of the subnet. It determines the physical path that data takes on the basis of network conditions, priority of service, and other factors. The network layer is responsible for routing and forwarding data packets.
Layer 2, The Data-Link Layer: The data-link layer is responsible for error free transfer of data frames. This layer provides synchronization for the physical layer. ARP and RARP would be found at this layer.
Layer 1, The Physical Layer: The physical layer is responsible for packaging and transmitting data on the physical media. This layer conveys the bit stream through a network at the electrical and mechanical level.See a great flash animation on the subject at:
http://www.maris.com/content/applets/flash/comp/fa0301.swf
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 85).
Also: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 7: Telecommunications and Network Security (page 344). -
What protocol is used on the Local Area Network (LAN) to obtain an IP address from it’s known MAC address?
- Reverse address resolution protocol (RARP)
- Address resolution protocol (ARP)
- Data link layer
- Network address translation (NAT)
Explanation:The reverse address resolution protocol (RARP) sends out a packet including a MAC address and a request to be informed of the IP address that should be assigned to that MAC.
Diskless workstations do not have a full operating system but have just enough code to know how to boot up and broadcast for an IP address, and they may have a pointer to the server that holds the operating system. The diskless workstation knows its hardware address, so it broadcasts this information so that a listening server can assign it the correct IP address.
As with ARP, Reverse Address Resolution Protocol (RARP) frames go to all systems on the subnet, but only the RARP server responds. Once the RARP server receives this request, it looks in its table to see which IP address matches the broadcast hardware address. The server then sends a message that contains its IP address back to the requesting computer. The system now has an IP address and can function on the network.
The Bootstrap Protocol (BOOTP) was created after RARP to enhance the functionality that RARP provides for diskless workstations. The diskless workstation can receive its IP address, the name server address for future name resolutions, and the default gateway address from the BOOTP server. BOOTP usually provides more functionality to diskless workstations than does RARP.
The evolution of this protocol has unfolded as follows: RARP evolved into BOOTP, which evolved into DHCP.
The following are incorrect answers:
NAT is a tool that is used for masking true IP addresses by employing internal addresses.
ARP does the opposite of RARP, it finds the MAC address that maps with an existing IP address.
Data Link layer The Data Link layer is not a protocol; it is represented at layer 2 of the OSI model. In the TCP/IP model, the Data Link and Physical layers are combined into the Network Access layer, which is sometimes called the Link layer or the Network Interface layer.Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition, Telecommunications and Network Security, Page 584-585 and also 598. For Kindle users see Kindle Locations 12348-12357. McGraw-Hill.
and
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 87).