SSCP : System Security Certified Practitioner (SSCP) : Part 38
SSCP : System Security Certified Practitioner (SSCP) : Part 38
-
Which of the following logical access exposures INVOLVES CHANGING data before, or as it is entered into the computer?
- Salami techniques
- Salami techniques
- Trojan horses
- Viruses
Explanation:
It involves changing data before , or as it is entered into the computer or in other words , it refers to the alteration of the existing data.
The other answers are incorrect because :
Salami techniques : A salami attack is the one in which an attacker commits several small crimes with the hope that the overall larger crime will go unnoticed.
Trojan horses: A Trojan Horse is a program that is disguised as another program.
Viruses:A Virus is a small application , or a string of code , that infects applications.Reference: Shon Harris , AIO v3
Chapter – 11: Application and System Development, Page : 875-880
Chapter – 10: Law, Investigation and Ethics , Page : 758-759 -
When a biometric system is used, which error type deals with the possibility of GRANTING access to impostors who should be REJECTED?
- Type I error
- Type II error
- Type III error
- Crossover error
Explanation:When the biometric system accepts impostors who should have been rejected , it is called a Type II error or False Acceptance Rate or False Accept Rate.
Biometrics verifies an individual’s identity by analyzing a unique personal attribute or behavior, which is one of the most effective and accurate methods of verifying identification.
Biometrics is a very sophisticated technology; thus, it is much more expensive and complex than the other types of identity verification processes. A biometric system can make authentication decisions based on an individual’s behavior, as in signature dynamics, but these can change over time and possibly be forged.
Biometric systems that base authentication decisions on physical attributes (iris, retina, fingerprint) provide more accuracy, because physical attributes typically don’t change much, absent some disfiguring injury, and are harder to impersonate.
When a biometric system rejects an authorized individual, it is called a Type I error (False Rejection Rate (FRR) or False Reject Rate (FRR)).
When the system accepts impostors who should be rejected, it is called a Type II error (False Acceptance Rate (FAR) or False Accept Rate (FAR)). Type II errors are the most dangerous and thus the most important to avoid.
The goal is to obtain low numbers for each type of error, but When comparing different biometric systems, many different variables are used, but one of the most important metrics is the crossover error rate (CER).
The accuracy of any biometric method is measured in terms of Failed Acceptance Rate (FAR) and Failed Rejection Rate (FRR). Both are expressed as percentages. The FAR is the rate at which attempts by unauthorized users are incorrectly accepted as valid. The FRR is just the opposite. It measures the rate at which authorized users are denied access.
The relationship between FRR (Type I) and FAR (Type II) is depicted in the graphic below . As one rate increases, the other decreases. The Cross-over Error Rate (CER) is sometimes considered a good indicator of the overall accuracy of a biometric system. This is the point at which the FRR and the FAR have the same value. Solutions with a lower CER are typically more accurate.
See graphic below from Biometria showing this relationship. The Cross-over Error Rate (CER) is also called the Equal Error Rate (EER), the two are synonymous.
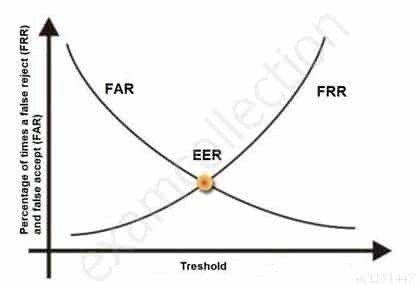
SSCP System Security Certified Practitioner (SSCP) Part 38 Q02 040 Cross Over Error Rate
The other answers are incorrect:
Type I error is also called as False Rejection Rate where a valid user is rejected by the system.
Type III error : there is no such error type in biometric system.Crossover error rate stated in percentage , represents the point at which false rejection equals the false acceptance rate.
Reference(s) used for this question:
http://www.biometria.sk/en/principles-of-biometrics.html
and
Shon Harris, CISSP All In One (AIO), 6th Edition , Chapter 3, Access Control, Page 188-189
and
Tech Republic, Reduce Multi_Factor Authentication Cost -
Which of the following is the LEAST user accepted biometric device?
- Fingerprint
- Iris scan
- Retina scan
- Voice verification
Explanation:The biometric device that is least user accepted is the retina scan, where a system scans the blood-vessel pattern on the backside of the eyeball. When using this device, an individual has to place their eye up to a device, and may require a puff of air to be blown into the eye. The iris scan only needs for an individual to glance at a camera that could be placed above a door.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, Chapter 4: Access Control (page 131). -
Which of the following is the WEAKEST authentication mechanism?
- Passphrases
- Passwords
- One-time passwords
- Token devices
Explanation:Most of the time users usually choose passwords which can be guessed , hence passwords is the BEST answer out of the choices listed above.
The following answers are incorrect because :
Passphrases is incorrect as it is more secure than a password because it is longer.
One-time passwords is incorrect as the name states , it is good for only once and cannot be reused.
Token devices is incorrect as this is also a password generator and is an one time password mechanism.Reference : Shon Harris AIO v3 , Chapter-4 : Access Control , Page : 139 , 142.
-
Which of the following statements pertaining to biometrics is FALSE?
- User can be authenticated based on behavior.
- User can be authenticated based on unique physical attributes.
- User can be authenticated by what he knows.
- A biometric system’s accuracy is determined by its crossover error rate (CER).
Explanation:As this is not a characteristic of Biometrics this is the rigth choice for this question. This is one of the three basic way authentication can be performed and it is not related to Biometrics. Example of something you know would be a password or PIN for example.
Please make a note of the negative ‘FALSE’ within the question. This question may seem tricky to some of you but you would be amazed at how many people cannot deal with negative questions. There will be a few negative questions within the real exam, just like this one the keyword NOT or FALSE will be in Uppercase to clearly indicate that it is negative.
Biometrics verifies an individual’s identity by analyzing a unique personal attribute or behavior, which is one of the most effective and accurate methods of performing authentication (one to one matching) or identification (a one to many matching).
A biometric system scans an attribute or behavior of a person and compares it to a template store within an authentication server datbase, such template would be created in an earlier enrollment process. Because this system inspects the grooves of a person’s fingerprint, the pattern of someone’s retina, or the pitches of someone’s voice, it has to be extremely sensitive.
The system must perform accurate and repeatable measurements of anatomical or physiological characteristics. This type of sensitivity can easily cause false positives or false negatives. The system must be calibrated so that these false positives and false negatives occur infrequently and the results are as accurate as possible.
There are two types of failures in biometric identification:
False Rejection also called False Rejection Rate (FRR) — The system fail to recognize a legitimate user. While it could be argued that this has the effect of keeping the protected area extra secure, it is an intolerable frustration to legitimate users who are refused access because the scanner does not recognize them.
False Acceptance or False Acceptance Rate (FAR) — This is an erroneous recognition, either by confusing one user with another or by accepting an imposter as a legitimate user.
Physiological Examples:
Unique Physical Attributes:
Fingerprint (Most commonly accepted)
Hand Geometry
Retina Scan (Most accurate but most intrusive)
Iris Scan
Vascular ScanBehavioral Examples:
Repeated Actions
Keystroke Dynamics
(Dwell time (the time a key is pressed) and Flight time (the time between “key up” and the next “key down”).
Signature Dynamics
(Stroke and pressure points)EXAM TIP:
Retina scan devices are the most accurate but also the most invasive biometrics system available today. The continuity of the retinal pattern throughout life and the difficulty in fooling such a device also make it a great long-term, high-security option. Unfortunately, the cost of the proprietary hardware as well the stigma of users thinking it is potentially harmful to the eye makes retinal scanning a bad fit for most situations.Remember for the exam that fingerprints are the most commonly accepted type of biometrics system.
The other answers are incorrect:
‘Users can be authenticated based on behavior.’ is incorrect as this choice is TRUE as it pertains to BIOMETRICS.
Biometrics systems makes use of unique physical characteristics or behavior of users.‘User can be authenticated based on unique physical attributes.’ is also incorrect as this choice is also TRUE as it pertains to BIOMETRICS. Biometrics systems makes use of unique physical characteristics or behavior of users.
‘A biometric system’s accuracy is determined by its crossover error rate (CER)’ is also incorrect as this is TRUE as it also pertains to BIOMETRICS. The CER is the point at which the false rejection rates and the false acceptance rates are equal. The smaller the value of the CER, the more accurate the system.
Reference(s) used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 25353-25356). Auerbach Publications. Kindle Edition.
and
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 25297-25303). Auerbach Publications. Kindle Edition. -
Which of the following biometric devices offers the LOWEST CER?
- Keystroke dynamics
- Voice verification
- Iris scan
- Fingerprint
Explanation:From most effective (lowest CER) to least effective (highest CER) are:
Iris scan, fingerprint, voice verification, keystroke dynamics.
Reference : Shon Harris Aio v3 , Chapter-4 : Access Control , Page : 131
Also see: http://www.sans.org/reading_room/whitepapers/authentication/biometric-selection-body-parts-online_139 -
Which of the following is most appropriate to notify an external user that session monitoring is being conducted?
- Logon Banners
- Wall poster
- Employee Handbook
- Written agreement
Explanation:Banners at the log-on time should be used to notify external users of any monitoring that is being conducted. A good banner will give you a better legal stand and also makes it obvious the user was warned about who should access the system and if it is an unauthorized user then he is fully aware of trespassing.
This is a tricky question, the keyword in the question is External user.
There are two possible answers based on how the question is presented, this question could either apply to internal users or ANY anonymous user.
Internal users should always have a written agreement first, then logon banners serve as a constant reminder.
Anonymous users, such as those logging into a web site, ftp server or even a mail server; their only notification system is the use of a logon banner.References used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 50.
and
Shon Harris, CISSP All-in-one, 5th edition, pg 873 -
Which of the following pairings uses technology to enforce access control policies?
- Preventive/Administrative
- Preventive/Technical
- Preventive/Physical
- Detective/Administrative
Explanation:The preventive/technical pairing uses technology to enforce access control policies.
TECHNICAL CONTROLS
Technical security involves the use of safeguards incorporated in computer hardware, operations or applications software, communications hardware and software, and related devices. Technical controls are sometimes referred to as logical controls.Preventive Technical Controls
Preventive technical controls are used to prevent unauthorized personnel or programs from gaining remote access to computing resources. Examples of these controls include:Access control software.
Antivirus software.
Library control systems.
Passwords.
Smart cards.
Encryption.
Dial-up access control and callback systems.Preventive Physical Controls
Preventive physical controls are employed to prevent unauthorized personnel from entering computing facilities (i.e., locations housing computing resources, supporting utilities, computer hard copy, and input data media) and to help protect against natural disasters. Examples of these controls include:
Backup files and documentation.
Fences.
Security guards.
Badge systems.
Double door systems.
Locks and keys.
Backup power.
Biometric access controls.
Site selection.
Fire extinguishers.Preventive Administrative Controls
Preventive administrative controls are personnel-oriented techniques for controlling people’s behavior to ensure the confidentiality, integrity, and availability of computing data and programs. Examples of preventive administrative controls include:
Security awareness and technical training.
Separation of duties.
Procedures for recruiting and terminating employees.
Security policies and procedures.
Supervision.
Disaster recovery, contingency, and emergency plans.
User registration for computer access.Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 34.
-
Which of the following is most relevant to determining the maximum effective cost of access control?
- the value of information that is protected
- management’s perceptions regarding data importance
- budget planning related to base versus incremental spending.
- the cost to replace lost data
Explanation:The cost of access control must be commensurate with the value of the information that is being protected.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 49. -
Which of the following is NOT a factor related to Access Control?
- integrity
- authenticity
- confidentiality
- availability
Explanation:These factors cover the integrity, confidentiality, and availability components of information system security.
Integrity is important in access control as it relates to ensuring only authorized subjects can make changes to objects.
Authenticity is different from authentication. Authenticity pertains to something being authentic, not necessarily having a direct correlation to access control.
Confidentiality is pertinent to access control in that the access to sensitive information is controlled to protect confidentiality.
vailability is protected by access controls in that if an attacket attempts to disrupt availability they would first need access.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 49.
-
Access Control techniques do not include which of the following?
- Rule-Based Access Controls
- Role-Based Access Control
- Mandatory Access Control
- Random Number Based Access Control
Explanation:Which of the following statements relating to the Bell-LaPadula security model is FALSE (assuming the Strong Star property is not being used) ? -
Which of the following statements relating to the Bell-LaPadula security model is FALSE (assuming the Strong Star property is not being used) ?
- A subject is not allowed to read up.
- The property restriction can be escaped by temporarily downgrading a high level subject.
- A subject is not allowed to read down.
- It is restricted to confidentiality.
Explanation:It is not a property of Bell LaPadula model.
The other answers are incorrect because:
A subject is not allowed to read up is a property of the ‘simple security rule’ of Bell LaPadula model.
The property restriction can be escaped by temporarily downgrading a high level subject can be escaped by temporarily downgrading a high level subject or by identifying a set of trusted objects which are permitted to violate the property as long as it is not in the middle of an operation.
It is restricted to confidentiality as it is a state machine model that enforces the confidentiality aspects of access control.
Reference: Shon Harris AIO v3 , Chapter-5 : Security Models and Architecture , Page:279-282 -
Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining influence over the behavior, use, and content of a system. It does not permit management to:
- specify what users can do
- specify which resources they can access
- specify how to restrain hackers
- specify what operations they can perform on a system.
Explanation:Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining influence over the behavior, use, and content of a system. It permits management to specify what users can do, which resources they can access, and what operations they can perform on a system. Specifying HOW to restrain hackers is not directly linked to access control.
Source: DUPUIS, Clement, Access Control Systems and Methodology, Version 1, May 2002, CISSP Open Study Group Study Guide for Domain 1, Page 12. -
Access Control techniques do not include which of the following choices?
- Relevant Access Controls
- Discretionary Access Control
- Mandatory Access Control
- Lattice Based Access Control
Explanation:Access Control Techniques
Discretionary Access Control
Mandatory Access Control
Lattice Based Access Control
Rule-Based Access Control
Role-Based Access Control
Source: DUPUIS, Clement, Access Control Systems and Methodology, Version 1, May 2002, CISSP Open Study Group Study Guide for Domain 1, Page 13. -
Which of the following statements pertaining to access control is false?
- Users should only access data on a need-to-know basis.
- If access is not explicitly denied, it should be implicitly allowed.
- Access rights should be granted based on the level of trust a company has on a subject.
- Roles can be an efficient way to assign rights to a type of user who performs certain tasks.
Explanation:Access control mechanisms should default to no access to provide the necessary level of security and ensure that no security holes go unnoticed. If access is not explicitly allowed, it should be implicitly denied.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, Chapter 4: Access Control (page 143). -
How are memory cards and smart cards different?
- Memory cards normally hold more memory than smart cards
- Smart cards provide a two-factor authentication whereas memory cards don’t
- Memory cards have no processing power
- Only smart cards can be used for ATM cards
Explanation:The main difference between memory cards and smart cards is their capacity to process information. A memory card holds information but cannot process information. A smart card holds information and has the necessary hardware and software to actually process that information.
A memory card holds a user’s authentication information, so that this user needs only type in a user ID or PIN and presents the memory card to the system. If the entered information and the stored information match and are approved by an authentication service, the user is successfully authenticated.
A common example of a memory card is a swipe card used to provide entry to a building. The user enters a PIN and swipes the memory card through a card reader. If this is the correct combination, the reader flashes green and the individual can open the door and enter the building.
Memory cards can also be used with computers, but they require a reader to process the information. The reader adds cost to the process, especially when one is needed for every computer. Additionally, the overhead of PIN and card generation adds additional overhead and complexity to the whole authentication process. However, a memory card provides a more secure authentication method than using only a password because the attacker would need to obtain the card and know the correct PIN.
Administrators and management need to weigh the costs and benefits of a memory card implementation as well as the security needs of the organization to determine if it is the right authentication mechanism for their environment.
One of the most prevalent weaknesses of memory cards is that data stored on the card are not protected. Unencrypted data on the card (or stored on the magnetic strip) can be extracted or copied. Unlike a smart card, where security controls and logic are embedded in the integrated circuit, memory cards do not employ an inherent mechanism to protect the data from exposure.
Very little trust can be associated with confidentiality and integrity of information on the memory cards.The following answers are incorrect:
“Smart cards provide two-factor authentication whereas memory cards don’t” is incorrect. This is not necessarily true. A memory card can be combined with a pin or password to offer two factors authentication where something you have and something you know are used for factors.
“Memory cards normally hold more memory than smart cards” is incorrect. While a memory card may or may not have more memory than a smart card, this is certainly not the best answer to the question.
“Only smart cards can be used for ATM cards” is incorrect. This depends on the decisions made by the particular institution and is not the best answer to the question.
Reference(s) used for this question:
Shon Harris, CISSP All In One, 6th edition , Access Control, Page 199 and also for people using the Kindle edition of the book you can look at Locations 4647-4650.
Schneiter, Andrew (2013-04-15). Official (ISC)2 Guide to the CISSP CBK, Third Edition : Access Control ((ISC)2 Press) (Kindle Locations 2124-2139). Auerbach Publications. Kindle Edition. -
Why do buffer overflows happen? What is the main cause?
- Because buffers can only hold so much data
- Because of improper parameter checking within the application
- Because they are an easy weakness to exploit
- Because of insufficient system memory
Explanation:Buffer Overflow attack takes advantage of improper parameter checking within the application. This is the classic form of buffer overflow and occurs because the programmer accepts whatever input the user supplies without checking to make sure that the length of the input is less than the size of the buffer in the program.
The buffer overflow problem is one of the oldest and most common problems in software development and programming, dating back to the introduction of interactive computing. It can result when a program fills up the assigned buffer of memory with more data than its buffer can hold. When the program begins to write beyond the end of the buffer, the program’s execution path can be changed, or data can be written into areas used by the operating system itself. This can lead to the insertion of malicious code that can be used to gain administrative privileges on the program or system.
As explained by Gaurab, it can become very complex. At the time of input even if you are checking the length of the input, it has to be check against the buffer size. Consider a case where entry point of data is stored in Buffer1 of Application1 and then you copy it to Buffer2 within Application2 later on, if you are just checking the length of data against Buffer1, it will not ensure that it will not cause a buffer overflow in Buffer2 of Application2.
A bit of reassurance from the ISC2 book about level of Coding Knowledge needed for the exam:
It should be noted that the CISSP is not required to be an expert programmer or know the inner workings of developing application software code, like the FORTRAN programming language, or how to develop Web applet code using Java. It is not even necessary that the CISSP know detailed security-specific coding practices such as the major divisions of buffer overflow exploits or the reason for preferring str(n)cpy to strcpy in the C language (although all such knowledge is, of course, helpful). Because the CISSP may be the person responsible for ensuring that security is included in such developments, the CISSP should know the basic procedures and concepts involved during the design and development of software programming. That is, in order for the CISSP to monitor the software development process and verify that security is included, the CISSP must understand the fundamental concepts of programming developments and the security strengths and weaknesses of various application development processes.The following are incorrect answers:
“Because buffers can only hold so much data” is incorrect. This is certainly true but is not the best answer because the finite size of the buffer is not the problem — the problem is that the programmer did not check the size of the input before moving it into the buffer.“Because they are an easy weakness to exploit” is incorrect. This answer is sometimes true but is not the best answer because the root cause of the buffer overflow is that the programmer did not check the size of the user input.
“Because of insufficient system memory” is incorrect. This is irrelevant to the occurrence of a buffer overflow.
Reference(s) used for this question:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 13319-13323). Auerbach Publications. Kindle Edition. -
Which access control model is best suited in an environment where a high security level is required and where it is desired that only the administrator grants access control?
- DAC
- MAC
- Access control matrix
- TACACS
Explanation:MAC provides high security by regulating access based on the clearance of individual users and sensitivity labels for each object. Clearance levels and sensitivity levels cannot be modified by individual users — for example, user Joe (SECRET clearance) cannot reclassify the “Presidential Doughnut Recipe” from “SECRET” to “CONFIDENTIAL” so that his friend Jane (CONFIDENTIAL clearance) can read it. The administrator is ultimately responsible for configuring this protection in accordance with security policy and directives from the Data Owner.
DAC is incorrect. In DAC, the data owner is responsible for controlling access to the object.
Access control matrix is incorrect. The access control matrix is a way of thinking about the access control needed by a population of subjects to a population of objects. This access control can be applied using rules, ACL’s, capability tables, etc.
TACACS is incorrect. TACACS is a tool for performing user authentication.
References:
CBK, p. 187, Domain 2: Access Control.
AIO3, Chapter 4, Access Control. -
Which access control model provides upper and lower bounds of access capabilities for a subject?
- Role-based access control
- Lattice-based access control
- Biba access control
- Content-dependent access control
Explanation:In the lattice model, users are assigned security clearences and the data is classified. Access decisions are made based on the clearence of the user and the classification of the object. Lattice-based access control is an essential ingredient of formal security models such as Bell-LaPadula, Biba, Chinese Wall, etc.
The bounds concept comes from the formal definition of a lattice as a “partially ordered set for which every pair of elements has a greatest lower bound and a least upper bound.” To see the application, consider a file classified as “SECRET” and a user Joe with a security clearence of “TOP SECRET.” Under Bell-LaPadula, Joe’s “least upper bound” access to the file is “READ” and his least lower bound is “NO WRITE” (star property).
Role-based access control is incorrect. Under RBAC, the access is controlled by the permissions assigned to a role and the specific role assigned to the user.
Biba access control is incorrect. The Biba integrity model is based on a lattice structure but the context of the question disqualiifes it as the best answer.
Content-dependent access control is incorrect. In content dependent access control, the actual content of the information determines access as enforced by the arbiter.
References:
CBK, pp. 324-325.
AIO3, pp. 291-293. See aprticularly Figure 5-19 on p. 293 for an illustration of bounds in action. -
Which security model introduces access to objects only through programs?
- The Biba model
- The Bell-LaPadula model
- The Clark-Wilson model
- The information flow model
Explanation:In the Clark-Wilson model, the subject no longer has direct access to objects but instead must access them through programs (well -formed transactions).
The Clark–Wilson integrity model provides a foundation for specifying and analyzing an integrity policy for a computing system.The model is primarily concerned with formalizing the notion of information integrity. Information integrity is maintained by preventing corruption of data items in a system due to either error or malicious intent. An integrity policy describes how the data items in the system should be kept valid from one state of the system to the next and specifies the capabilities of various principals in the system. The model defines enforcement rules and certification rules.
Clark–Wilson is more clearly applicable to business and industry processes in which the integrity of the information content is paramount at any level of classification.
Integrity goals of Clark–Wilson model:
Prevent unauthorized users from making modification (Only this one is addressed by the Biba model).
Separation of duties prevents authorized users from making improper modifications.
Well formed transactions: maintain internal and external consistency i.e. it is a series of operations that are carried out to transfer the data from one consistent state to the other.The following are incorrect answers:
The Biba model is incorrect. The Biba model is concerned with integrity and controls access to objects based on a comparison of the security level of the subject to that of the object.
The Bell-LaPdaula model is incorrect. The Bell-LaPaula model is concerned with confidentiality and controls access to objects based on a comparison of the clearence level of the subject to the classification level of the object.
The information flow model is incorrect. The information flow model uses a lattice where objects are labelled with security classes and information can flow either upward or at the same level. It is similar in framework to the Bell-LaPadula model.
References:
ISC2 Official Study Guide, Pages 325 – 327
AIO3, pp. 284 – 287
AIOv4 Security Architecture and Design (pages 338 – 342)
AIOv5 Security Architecture and Design (pages 341 – 344)
Wikipedia at: https://en.wikipedia.org/wiki/Clark-Wilson_model