102-500 : LPI Level 1 : Part 05
102-500 : LPI Level 1 : Part 05
-
What information related to a user account is modified using the chage command?
- Default ownership for new files
- Group membership
- Set of commands available to the user
- Password expiry information
- Default permissions for new files
-
Which command is used to set restrictions on the size of a core file that is created for a user when a program crashes?
coreedquotaquotaulimitktrace
-
How do shadow passwords improve the password security in comparison to standard no-shadow password?
- Regular users do not have access to the password hashes of shadow passwords.
- Every shadow password is valid for 45 days and must be changed afterwards.
- The system’s host key is used to encrypt all shadow passwords.
- Shadow passwords are always combined with a public key that has to match the user’s private key.
- Shadow passwords are stored in plain text and can be checked for weak passwords.
-
After editing the TCP wrapper configuration to grant specific hosts access to a service, when do these changes become effective?
- The new configuration becomes effective after restarting the respective service.
- The new configuration becomes effective at the next system reboot.
- The new configuration becomes effective when the last established connection to the service is closed.
- The new configuration becomes effective after restarting the tcpd service.
- The new configuration becomes effective immediately for all new connections.
-
What is true regarding public and private SSH keys? (Choose two.)
- For each user account, there is exactly one key pair that can be used to log into that account.
- The private key must never be revealed to anyone.
- Several different public keys may be generated for the same private key.
- To maintain the private key’s confidentiality, the SSH key pair must be created by its owner.
- To allow remote logins, the user’s private key must be copied to the remote server.
-
Which of the following commands finds all files owned by root that have the SetUID bit set?
-
find / -user root -perm -4000 -
find / -user 0 -mode +s
-
find / -owner root -setuid
-
find / -owner 0 -permbits 0x100000000
-
find / --filter uid=1 --filter pers=u+s
-
-
FILL BLANK
What command is used to add OpenSSH private keys to a running ssh-agent instance? (Specify the command name only without any path.)
ssh-add
-
FILL BLANK
Which directory holds configuration files for xinetd services? (Specify the full path to the directory.)
/etc/xinetd.d/
-
Which mechanism does
sshuse to interact with the SSH agent?- Connecting to port 2222 which is used by the system-wide SSH agent.
- Using the fixed socket
.ssh-agent/ipc. - Creating an alias replacing
sshwith calls tossh-agent. - Starting
ssh-agentas a child process for each ssh invocation. - Evaluating environment variables such as
SSH_AUTH_SOCK.
-
FILL BLANK
Which parameter of the ssh command specifies the location of the private key used for login attempts? (Specify only the option name without any values or parameters.)
ssh-keygen
-
Which of the following is true about IPv6?
- IPv6 no longer supports broadcast addresses.
- With IPv6, the TCP port numbers of most services have changed.
- IPv4 addresses can be used without any change with IPv6.
- IPv6 no longer supports multicast addresses.
- For IPv6, UDP and TCP have been replaced by the Rapid Transmission Protocol RTP.
-
What is true about the following command?
nmcli device wifi connect WIFIoI- NetworkManager opens a new public hotspot with the
SSID WIFIoI. - NetworkManager creates an unconfigured new virtual network interface named
WIFIoI. - NetworkManager creates a new wifi connection
WIFIoIand activates it. - NetworkManager returns an error in case the connection
WIFIoIdoes not exist. - NetworkManager returns an error because
WIFIoIis an invalid wifi device.
- NetworkManager opens a new public hotspot with the
-
Which of the commands below might have produced the following output?
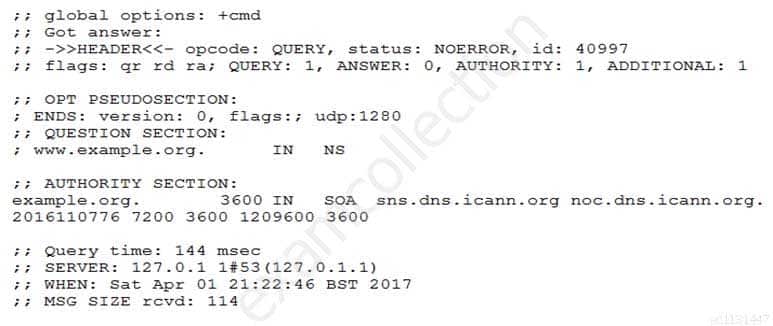
102-500 LPI Level 1 Part 05 Q13 001 - dig -t mx www.example.org
- dig www.example.org
- dig -t ns www.example.org
- dig -t a www.example.org
- dig -t soa www.example.org
-
FILL BLANK
Which parameter is missing in the command
ip link set ____ dev eth0
to activate the previously inactive network interface eth0? (Specify the parameter only without any command, path or additional options.)
-
up
-
-
Which of the following states can NetworkManager show regarding the system’s network connectivity? (Choose two.)
-
up
-
portal -
full -
login-required
-
firewalled
-
-
Which of the following are valid host addresses for the subnet 203.0.113.64/28? (Choose two.)
- 203.0.113.64
- 203.0.113.78
- 203.0.113.65
- 203.0.113.80
- 203.0.113.81
-
Which of the following keywords can be used in the file
/etc/resolv/conf?(Choose two.)-
substitute
-
lookup
-
search -
nameserver -
method
-
-
How does the ping command work by default?
- Is sends an ICMP Echo Request to a remote host and waits to receive an ICMP Echo Response in return.
- It sends an ARP request to a remote host and waits to receive an ARP response in return.
- It sends a TCP SYN packet to a remote host and waits to receive an TCP ACK response in return.
- Is sends a broadcast packet to all hosts on the net and waits to receive, among others, a response from the target system.
- It sends a UDP packet to port 0 of the remote host and waits to receive a UDP error response in return.
-
Which of the following commands display the number of bytes transmitted and received via the eth0 network interface? (Choose two.)
-
route -v via eth0
-
ip stats show dev eth0
-
netstat -s -i eth0 -
ifconfig eth0 -
ip -s link show eth0
-
-
Given the following routing table:
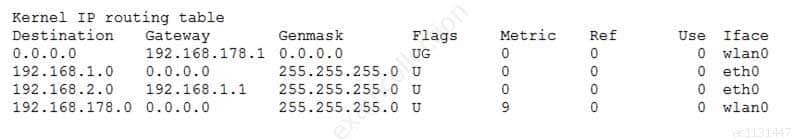
102-500 LPI Level 1 Part 05 Q20 002 How would an outgoing packet to the destination 192.168.2.150 be handled?
- It would be passed to the default router 192.168.178.1 on wlan0.
- It would be directly transmitted on the device eth0.
- It would be passed to the default router 255.255.255.0 on eth0.
- It would be passed to the router 192.168.1.1 on eth0.
- It would be directly transmitted on the device wlan0.