202-450 : LPIC-2 Exam 202 : Part 04
202-450 : LPIC-2 Exam 202 : Part 04
-
Which of the following services belongs to NFSv4 and does not exist in NFSv3?
-
rpc.idmapd -
rpc.statd
-
nfsd
-
rpc.mountd
Explanation:
Reference: https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/5/html/deployment_guide/ch-nfs
-
-
Which of the following actions synchronizes UNIX passwords with the Samba passwords when the encrypted Samba password is changed using smbpasswd?
- There are no actions to accomplish this since is not possible.
- Run
netvampregularly, to convert the passwords. - Run
winbind –sync,to synchronize the passwords. -
Addunix password sync = yes to smb.conf - Add
smb unix password = sync to smb.conf
Explanation:Reference: https://www.oreilly.com/openbook/samba/book/ch06_04.html -
In order to join a file server to the Active Directory domain
intra.example.com,the followingsmb.confhas been created: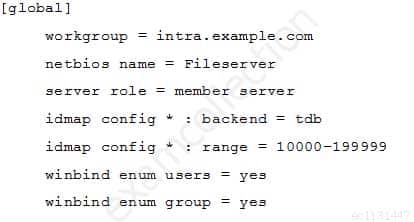
202-450 LPIC-2 Exam 202 Part 04 Q03 023 The command net ads join raises an error and the server is not joined to the domain. What should be done to successfully join the domain?
- Change
server role to ad member serverto join an Active Directory domain instead of an NT4 domain. - Add
realm = intra.example.comto the smb.conf and change workgroup to the domain’s netbios workgroup name. - Manually create a machine account in the Active Directory domain and specify the machine account’s name with –U when starting
net ads join. - Remove the winbind enum users and winbind enum groups since winbind is incompatible with Active Directory domains.
- Remove all
idmapconfiguration stanzas since the id mapping is defined globally in an Active Directory domain and cannot be changed on a member server.
- Change
-
FILL BLANK
In order to export /usr and /bin via NFSv4, /exports was created and contains working bind mounts to /usr
and /bin. The following lines are added to /etc/exports on the NFC server: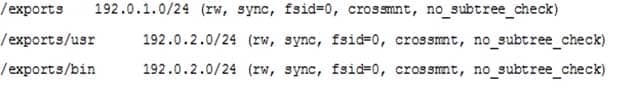
202-450 LPIC-2 Exam 202 Part 04 Q04 024 After running
mount -t nfsv4 server:/ /mntof an NFC-Client, it is observed that /mnt contains the content of the server’s /usr directory instead of the content of the NFSv4 foot folder.
Which option in
/etc/exportshas to be changed or removed in order to make the NFSv4 root folder appear when mounting the highest level of the server? (Specify ONLY the option name without any values or parameters.)-
mount
-
-
What does the samba-tool testparm command confirm regarding the Samba configuration?
- The configuration loads successfully.
- The service operates as expected.
- The Samba services are started automatically when the system boots.
- The netfilter configuration on the Samba server does not block any access to the services defined in the configuration.
- All running Samba processes use the most recent configuration version.
Explanation:Reference: https://www.samba.org/samba/docs/current/man-html/testparm.1.html -
Select the Samba option below that should be used if the main intention is to setup a guest printer service?
-
security = cups
-
security = ldap
-
security = pam
-
security = share -
security = printing
-
-
The Samba configuration file contains the following lines:
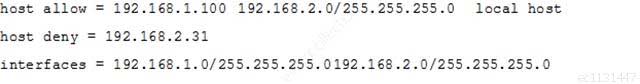
202-450 LPIC-2 Exam 202 Part 04 Q07 025 A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server.
Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
-
host allow = 192.168.1.1-255
-
host allow = 192.168.1.100 192.168.2.200 localhost
-
host deny = 192.168.1.100/255.255.255.0 192.168.2.31 localhost
-
host deny = 192.168.2.200/255.255.255.0 192.168.2.31 localhost -
host allow = 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0 localhost
-
-
FILL BLANK
What command displays NFC kernel statistics? (Specify ONLY the command without any path or parameters.)
-
nfsstat
Explanation:Reference: https://www.systutorials.com/docs/linux/man/8-nfsstat/ -
-
Which keyword is used in the Squid configuration to define networks and times used to limit access to the service?
- acl
- allow
- http_allow
- permit
Explanation:Reference: https://www.tecmint.com/configure-squid-server-in-linux/ -
The following Apache HTTPD configuration has been set up to create a virtual host available at www.example.com and www2.example.com:
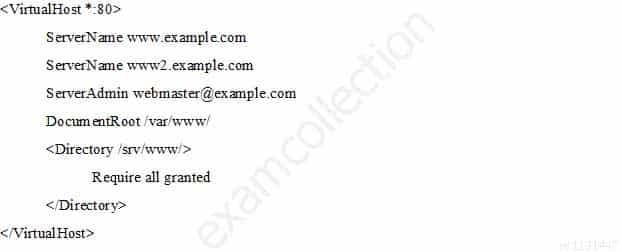
202-450 LPIC-2 Exam 202 Part 04 Q10 026 Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
- The configuration must be split into two
VirtualHostsections since each virtual host may only have one name. - The port mentioned in opening
VirtualHosttag has to be appended to theServerNamedeclaration’s values. - Both virtual host names have to be placed as comma separated values in one
ServerNamedeclaration. - Both virtual host names have to be mentioned in the opening
VirtualHosttag. - Only one Server name declaration may exist, but additional names can be declared in
ServerAliasoptions.
- The configuration must be split into two
-
Given the following Squid configuration excerpt:
cache_dir ufs /var/spool/squid3/ 1024 16 256
Which of the following directories will exist directly within the directory:
/var/spool/squid3/?(Choose two.)-
0F -
A0
-
0b -
FF
-
00
-
-
Which of the following statements are true regarding Server Name Indication (SNI)? (Choose two.)
- It supports transparent failover of TLS sessions from one web server to another.
- It allows multiple SSL/TLS secured virtual HTTP hosts to coexist on the same IP address.
- It enables HTTP servers to update the DNS of their virtual hosts’ names using the X 509 certificates of the virtual hosts.
- It provides a list of available virtual hosts to the client during the TLS handshake.
- It submits the host name of the requested URL during the TLS handshake.
-
Which Apache HTTPD configuration directive specifies the RSA private key that was used in the generation of the SSL certificate for the server?
- SSLCertificateKeyFile
- SSLKeyFile
- SSLPrivateKeyFile
- SSLRSAKeyFile
Explanation:Reference: https://httpd.apache.org/docs/2.4/ssl/ssl_faq.html#aboutcerts -
There is a restricted area in a site hosted by Apache HTTPD, which requires users to authenticate against the file
/srv/www/security/sitepasswd.Which command is used to CHANGE the password of existing users, without losing data, when Basic authentication is being used?
-
htpasswd –c /srv/www/security/sitepasswd user -
htpasswd /srv/www/security/sitepasswd user
-
htpasswd –n /srv/www/security/sitepasswd user
-
htpasswd –D /srv/www/security/sitepasswd user
Explanation:Reference: https://httpd.apache.org/docs/2.4/howto/auth.html -
-
Which Apache HTTPD configuration directive is used to specify the method of authentication, e.g. None or Basic?
-
AuthUser
-
AllowedAuthUser
-
AuthType -
AllowAuth
Explanation:Reference: https://httpd.apache.org/docs/2.4/howto/auth.html -
-
Which of the following are logging directives in Apache HTTPD? (Choose two.)
-
TransferLog -
CustomLog -
ErrorLog
-
ServerLog
-
VHostLog
Explanation:Reference: http://httpd.apache.org/docs/current/mod/mod_log_config.html -
-
Which option within a Nginx server configuration section defines the file system path from which the content of the server is retrieved?
-
location
-
htdocs
-
DocumentRoot
-
root -
base_dir
Explanation:Reference: http://nginx.org/en/docs/beginners_guide.html -
-
With Nginx, which of the following directives is used to proxy requests to a FastCGI application?
-
fastcgi_pass -
fastcgi_proxy
-
proxy_fastcgi
-
proxy_fastcgi_pass
-
fastcgi_forward
-
-
Which of the following information has to be submitted to a certification authority in order to request a web server certificate?
- The web server’s private key.
- The IP address of the web server.
- The list of ciphers supported by the web server.
- The web server’s SSL configuration file.
- The certificate signing request.
Explanation:Reference: https://help.ubuntu.com/lts/serverguide/certificates-and-security.html.en -
For what purpose is TCP/IP stack fingerprinting used by nmap?
- It is used to determine the remote operating system.
- It is used to filter out responses from specific servers.
- It is used to identify duplicate responses from the same remote server.
- It is used to masquerade the responses of remote servers.
- It is used to uniquely identify servers on the network for forensics.
Explanation:Reference: https://nmap.org/nmap-fingerprinting-old.html