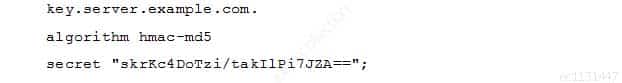202-450 : LPIC-2 Exam 202 : Part 05
202-450 : LPIC-2 Exam 202 : Part 05
-
To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
-
AllowForwarding
-
ForwardingAllow
-
XllForwardingAllow
-
XllForwarding
Explanation:
Reference: https://help.ubuntu.com/community/SSH/OpenSSH/Configuring
-
-
What is the standard port used by OpenVPN?
- 1723
- 4500
- 500
- 1194
Explanation:Reference: https://openvpn.net/archive/openvpn-users/2006-04/msg00355.html -
FILL BLANK
What option in the
sshdconfiguration file instructssshdto permit only specific user names to log in to a system? (Specify ONLY the option name without any values.)-
sshd_config
Explanation:Reference: https://www.ssh.com/ssh/sshd_config/ -
-
Using its standard configuration, how does fail2ban block offending SSH clients?
- By rejecting connections due to its role as a proxy in front of SSHD.
- By modifying and adjusting the SSHD configuration.
- By creating and maintaining netfilter rules.
- By creating null routes that drop any answer packets sent to the client.
- By modifying and adjusting the TCP Wrapper configuration for SSHD.
Explanation:Reference: https://www.digitalocean.com/community/tutorials/how-to-protect-ssh-with-fail2ban-on-centos-7 -
Which FTP names are recognized as anonymous users in vsftp when the option anonymous_enable is set to yes in the configuration files? (Choose two.)
-
anonymous -
ftp - In the described configuration, any username which neither belongs to an existing user nor has another special meaning is treated as anonymous user.
-
nobody
-
guest
Explanation:Reference: http://vsftpd.beasts.org/vsftpd_conf.html#lbAE -
-
Which of the following commands can be used to connect and interact with remote TCP network services? (Choose two.)
-
nettalk
-
nc -
telnet -
cat
-
netmap
-
-
To which destination will a route appear in the Linux routing table after activating IPv6 on a router’s network interface, even when no global IPv6 addresses have been assigned to the interface?
- fe80::/10
- 0::/128
- 0::/0
- fe80::/64
- 2000::/3
-
In order to prevent all anonymous FTP users from listing uploaded file names, what security precaution can be taken when creating an upload directory?
- The directory must not have the execute permission set.
- The directory must not have the read permission set.
- The directory must not have the read or execute permission set.
- The directory must not have the write permission set.
- The directory must not contain other directories.
-
Which command is used to administer IPv6 netfilter rules?
- iptables
- iptablesv6
- iptables6
- ip6tables
- ipv6tables
Explanation:Reference: https://www.centos.org/docs/5/html/5.1/Deployment_Guide/s1-ip6tables.html -
Which netfilter table contains built-in chains called INPUT, OUTPUT and FORWARD?
-
ipconn
-
filter -
nat
-
default
-
masq
Explanation:Reference: http://shorewall.org/NetfilterOverview.html -
-
After running ssh-keygen and accepting the default values, which of the following files are changed or created? (Choose two.)
- ~/.ssh/id_rsa.key
- ~/.ssh/id_rsa.pub
- ~/.ssh/id_rsa.prv
- ~/.ssh/id_rsa.crt
- ~/.ssh/id_rsa
Explanation:Reference: https://www.ssh.com/ssh/keygen/ -
Which of the following OpenVPN configuration options makes OpenVPN forward network packets between VPN clients itself instead of passing the packets on to the Linux host which runs the OpenVPN server for further processing?
-
inter-client-traffic
-
client-to-client -
client-router
-
client-pass
-
grant-client-traffic
-
-
Which of these tools provides DNS information in the following format?
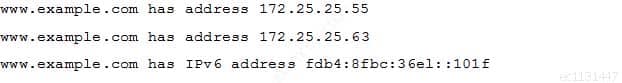
202-450 LPIC-2 Exam 202 Part 05 Q13 027 -
dig
-
nslookup
-
host -
named-checkconf
-
named-checkzone
-
-
Which rdnc sub command can be used in conjunction with the name of a zone in order to make BIND reread the content of the specific zone file without reloading other zones as well?
-
lookup -
reload
-
fileupdate -
reread
-
zoneupdate
-
-
A zone file contains the following lines:
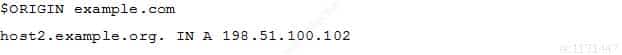
202-450 LPIC-2 Exam 202 Part 05 Q15 028 and is included in the BIND configuration using this configuration stanza:

202-450 LPIC-2 Exam 202 Part 05 Q15 029 Which problem is contained in this configuration?
- The
zonestatement is the BIND configuration must contain thecross-zone-datayes; statement. - The zone cannon contain records for a name which is outside the zone’s hierarchy.
- The
$ORIGINdeclaration cannot be used in zone files that are included for a specific zone name in the BIND configuration. - An A record cannot contain an IPv4 address because its value is supposed to be a reverse DNS name.
- Names of records in a zone file cannot be fully qualified domain names.
- The
-
Which of the following DNS record types is used for reverse DNS queries?
-
CNAME
-
IN
-
PTR -
REV
-
RIN
Explanation:Reference: http://help.dnsmadeeasy.com/managed-dns/dns-record-types/ptr-record/ -
-
FILL BLANK
According to the configuration below, what is the full e-mail address of the administrator for this domain?
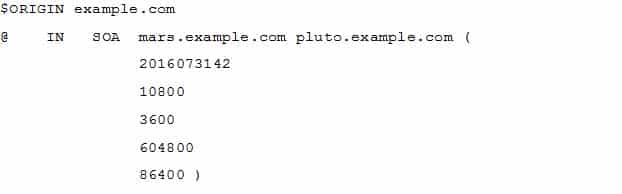
202-450 LPIC-2 Exam 202 Part 05 Q17 030 -
admin@mars.example.com
-
-
What is the purpose of DANE?
- Verify the integrity of name information retrieved via DNS.
- Allow secure dynamic DNS updates.
- Invalidate name information stored on caching name servers to speed up DNS updates.
- Discover which servers within a DNS domain offer a specific service.
- Provide a way to verify the association of X 509 certificates to DNS host names.
Explanation:Reference: https://wiki.archlinux.org/index.php/DANE -
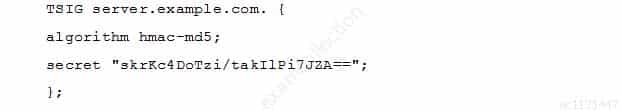
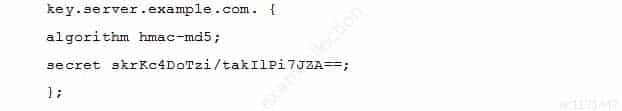
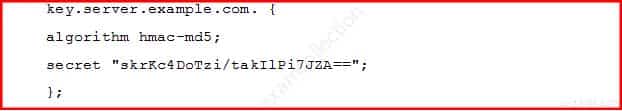
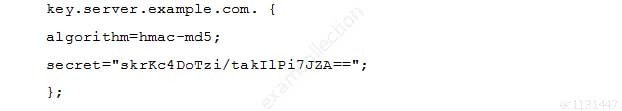
A BIND server should be upgraded to use TSIG. Which configuration parameters should be added if the server should use the algorithm hmac-md5 and the key skrKc4DoTzi/takIlPi7JZA==?
-
Which option in
named.confspecifies which host are permitted to ask for domain name information from the server?-
allowed-hosts
-
accept-query
-
permit-query
-
allow-query -
query-group
-