| Explanation & Hints:
Place the options in the following order:
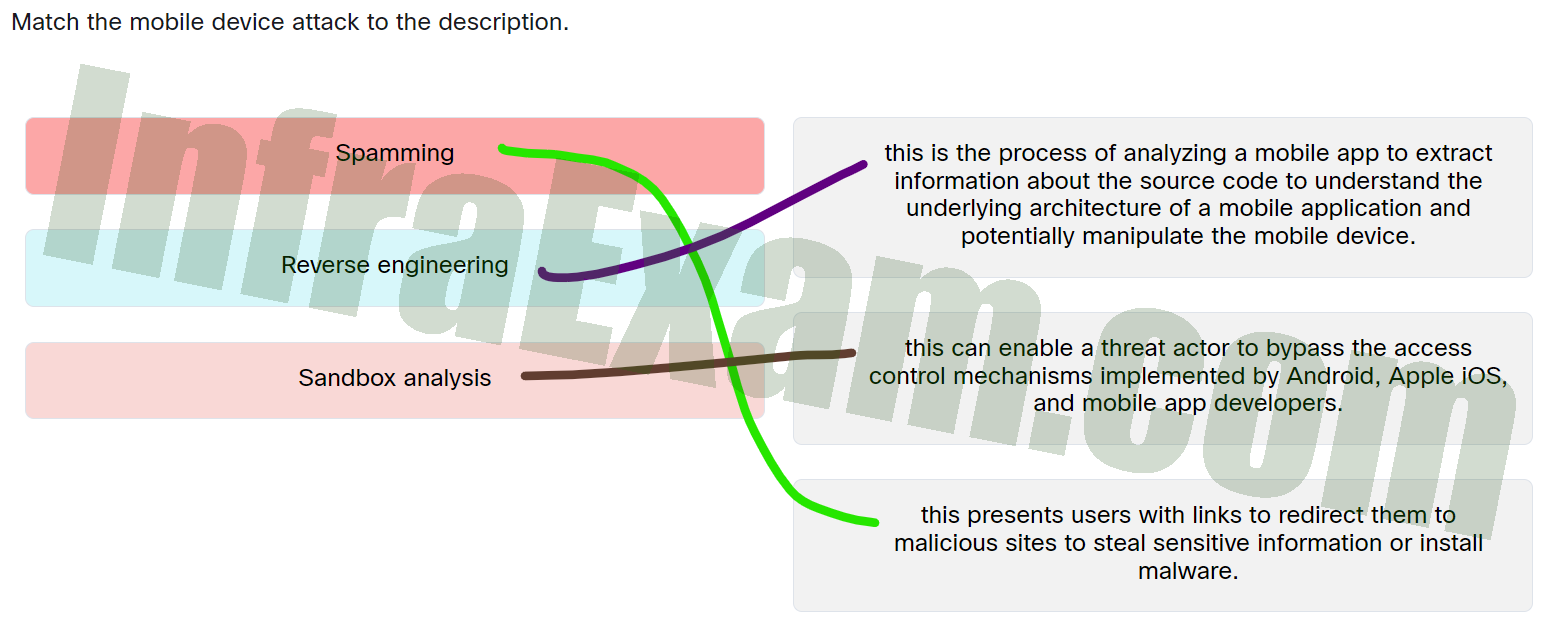
| Sandbox analysis |
This can enable a threat actor to bypass the access control mechanisms implemented by Android, Apple iOS, and mobile app developers. |
| Spamming |
This presents users with links to redirect them to malicious sites to steal sensitive information or install malware. |
| Reverse engineering |
This is the process of analyzing a mobile app to extract information about the source code to understand the underlying architecture of a mobile application and potentially manipulate the mobile device. |
|