98-366 : Networking Fundamentals : Part 05
98-366 : Networking Fundamentals : Part 05
-
Tracert is used to:
- Manage routing tables dynamically.
- Manage session-oriented connections between nodes.
- Report the route taken by packets across an IP network.
- Report the shortest route between different networks.
Explanation:In computing, traceroute (treacert) is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network.
-
In which OSI layer does routing occur?
- Transport
- Network
- Data Link
- Physical
Explanation:In the seven-layer OSI model of computer networking, the network layer is layer 3. The network layer is responsible for packet forwarding including routing through intermediate routers.
-
What type of record does DNS use to find a mail service?
- Service (SRV) DNS record
- Canonical (CNAME) DNS record
- Mail Exchanger (MX) DNS record
- Host (A) DNS record
Explanation:A mail exchanger record (MX record) is a type of resource record in the Domain Name System that specifies a mail server responsible for accepting email messages on behalf of a recipient’s domain, and a preference value used to prioritize mail delivery if multiple mail servers are available. The set of MX records of a domain name specifies how email should be routed with the Simple Mail Transfer Protocol (SMTP).
-
The default gateway address identifies the:
- Device that will connect the computer to the local network.
- Device that will connect the computer to a remote network.
- Server that will provide name services for the computer.
- Server that will authenticate the user of the computer.
Explanation:A default gateway is the node on the computer network that the network software uses when an IP address does not match any other routes in the routing table.
In home computing configurations, an ISP often provides a physical device which both connects local hardware to the Internet and serves as a gateway. -
How many bits are there in an Internet Protocol version 6 (IPv6) address?
- 32
- 64
- 128
- 256
Explanation:IPv6 uses a 128-bit address, allowing 2**128, or approximately 3.4×10**38 addresses, or more than 7.9×10**28 times as many as IPv4, which uses 32-bit addresses
-
Which of the following is a public IP address?
- 10.156.89.1
- 68.24.78.221
- 172.16.152.48
- 192.168.25.101
Explanation:Incorrect:
The private address space specified in RFC 1918 is defined by the following three address blocks:
not D: 192.168.0.0/16
The 192.168.0.0/16 private network can be interpreted either as a block of 256 class C network IDs or as a 16-bit assignable address space (16 host bits) that can be used for any subnetting scheme within the private organization. The 192.168.0.0/16 private network allows the following range of valid IP addresses: 192.168.0.1 to 192.168.255.254.Not A:
10.0.0.0/8
The 10.0.0.0/8 private network is a class A network ID that allows the following range of valid IP addresses: 10.0.0.1 to 10.255.255.254. The 10.0.0.0/8 private network has 24 host bits that can be used for any subnetting scheme within the private organization.Not C:
172.16.0.0/12
The 172.16.0.0/12 private network can be interpreted either as a block of 16 class B network IDs or as a 20-bit assignable address space (20 host bits) that can be used for any subnetting scheme within the private organization. The 172.16.0.0/12 private network allows the following range of valid IP addresses: 172.16.0.1 to 172.31.255.254. -
What is the minimum cabling requirement for a 100BaseTX network?
- Category 3 UTP cable
- Category 5 UTP cable
- Category 6 UTP cable
- Multimode fiber cable
Explanation:100BASE-TX is the predominant form of Fast Ethernet, and runs over two wire-pairs inside a category 5 or above cable.
100BASE-TX and 1000BASE-T were both designed to require a minimum of Category 5 cable and also specify a maximum cable length of 100 meters. Category 5 cable has since been deprecated and new installations use Category 5e.
-
Internet Key Exchange (IKE) is responsible for which two functions? (Choose two.)
- Establishing network speed parameters
- Verifying the client’s patch level
- Negotiating algorithms to use
- Exchanging key information
Explanation:Internet Key Exchange (IKE) negotiates the IPSec security associations (SAs). This process requires that the IPSec systems first authenticate themselves to each other and establish ISAKMP (IKE) shared keys.
In phase 1 of this process, IKE creates an authenticated, secure channel between the two IKE peers, called the IKE security association. The Diffie-Hellman key agreement is always performed in this phase.
In phase 2, IKE negotiates the IPSec security associations and generates the required key material for IPSec. The sender offers one or more transform sets that are used to specify an allowed combination of transforms with their respective settings. The sender also indicates the data flow to which the transform set is to be applied. The sender must offer at least one transform set. The receiver then sends back a single transform set, which indicates the mutually agreed-upon transforms and algorithms for this particular IPSec session.
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-366 Part 05 Q09 006 Question 
98-366 Part 05 Q09 006 Answer Explanation:Since the leftmost three bits are reserved as “001” for Global unicast IPv6 addresses, the range of Global Unicast Addresses available now are from 2000 to 3FFF.
21DA is a global unicast prefix. -
HOTSPOT
You are trying to access a music sharing service on the Internet. The service is located at the IP address 173.194.75.105. You are experiencing problems connecting.You run a trace route to the server and receive the output shown in the following image:
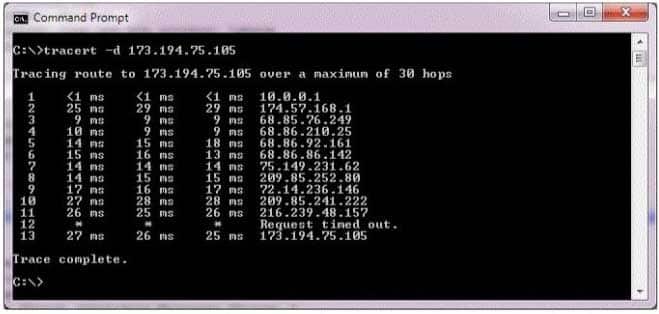
98-366 Part 05 Q10 007 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.

98-366 Part 05 Q10 008 Question 
98-366 Part 05 Q10 008 Answer Explanation:* traceroute (tracert) outputs the list of traversed routers in simple text format, together with timing information
* Q: How is it possible for traceroute to timeout, yet the site will load fine in a browser?
If a router along the way decides to not send the ICMP error message, you will get a timeout at that point in the traceroute.The router may pass on normal traffic, thus allowing your TCP-based http request to complete, but it may silently drop ICMP requests or errors, leaving your local traceroute process waiting and then timing out on that stop.
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-366 Part 05 Q11 009 Question 
98-366 Part 05 Q11 009 Answer Explanation: Sometimes you will want to create a tunnel without encryption. The IPSEC protocols provide two ways to do this -
This question requires that you evaluate the underlined text to determine if it is correct.
The process of replicating a zone file to multiple DNS servers is called “zone replication”.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.- Zone transfer
- Zone synchronization
- Start of authority
- No change is needed
Explanation:DNS zone transfer, also sometimes known by the inducing DNS query type AXFR, is a type of DNS transaction. It is one of the many mechanisms available for administrators to replicate DNS databases across a set of DNS servers
-
DRAG DROP
Match each IP address to its corresponding IPv4 address class.To answer, drag the appropriate IP address from the column on the left to its IPv4 address class on the right. Each IP address may be used once, more than once, or not at all. Each correct match is worth one point.
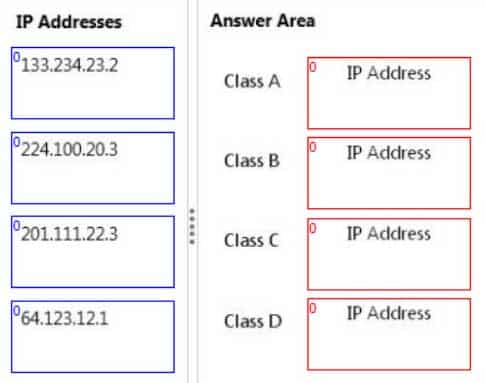
98-366 Part 05 Q13 010 Question 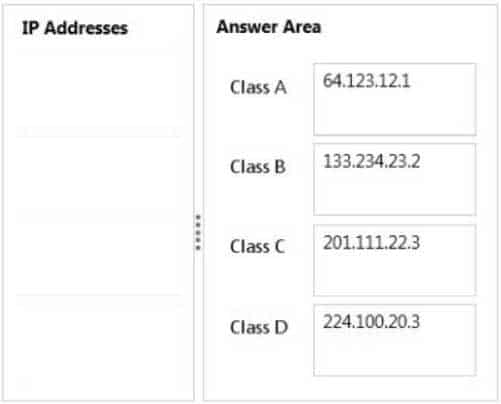
98-366 Part 05 Q13 010 Answer Explanation:Class A: 0.0.0.0 – 127.255.255.255
Class B: 128.0.0.0 – 191.255.255.255
Class C: 192.0.0.0 – 223.255.255.25
Class D: 224.0.0.0 – 239.255.255.255 -
Which DNS record type specifies the host that is the authority for a given domain?
- NS
- MX
- CNAME
- SOA
Explanation:The start of authority (SOA) resource record indicates the name of origin for the zone and contains the name of the server that is the primary source for information about the zone. It also indicates other basic properties of the zone.
-
DRAG DROP
Match each protocol to its description.To answer, drag the appropriate protocol from the column on the left to its description on the right. Each protocol may be used once, more than once, or not at all. Each correct match is worth one point.
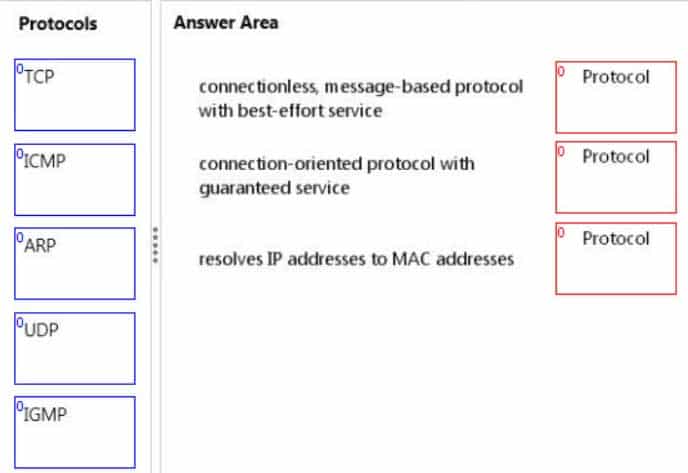
98-366 Part 05 Q15 012 Question 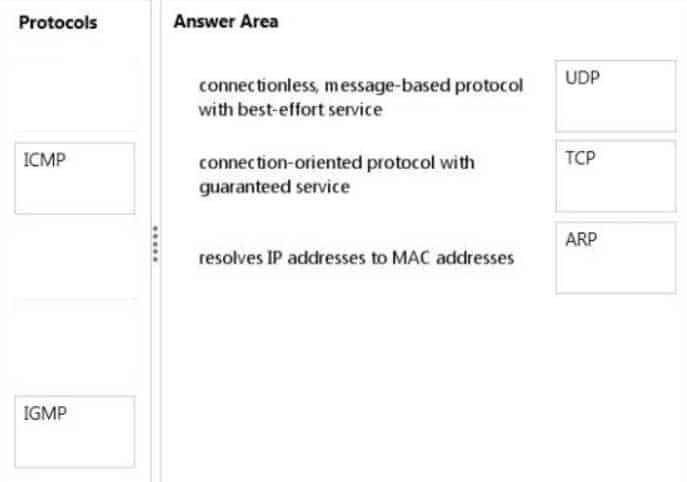
98-366 Part 05 Q15 012 Answer Explanation:* UDP uses a simple connectionless transmission model with a minimum of protocol mechanism. User datagram protocol (UDP) provides a thinner abstraction layer which only error-checks the datagrams.
Note: Best-effort delivery describes a network service in which the network does not provide any guarantees that data is delivered or that a user is given a guaranteed quality of service level or a certain priority.
* Transmission control protocol (TCP) provides a guaranteed delivery of an octet stream between a pair of hosts to the above layer, internally splitting the stream into packets and resending these when lost or corrupted.
* Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address (MAC address) that is recognized in the local network. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-366 Part 05 Q16 013 Question 
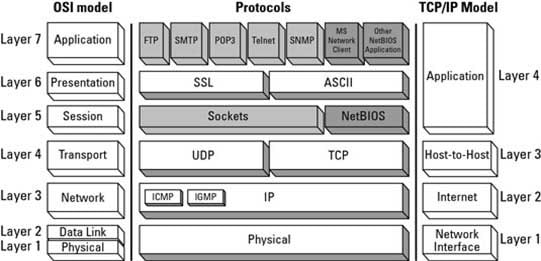
98-366 Part 05 Q16 013 Answer Explanation:* Yes, the TCP/IP four layers corresponds to the OSI model’s seven layers.
* No, the TCP/IP application layer corresponds to only the three top OSI Layers.
* Yes, TCP transport (host-to-host in diagram below) and Internet layers corresponds to layer 3 and layer 4 in the OSI model.Illustration:
-
This question requires that you evaluate the underlined text to determine if it is correct.
All session data is “encrypted between all machines” while using telnet.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- Not encrypted
- Encrypted between any Windows machines
- Encrypted only to any non-Windows machines
- No change is needed
Explanation:Telnet, by default, does not encrypt any data sent over the connection (including passwords), and so it is often practical to eavesdrop on the communications and use the password later for malicious purposes; anybody who has access to a router, switch, hub or gateway located on the network between the two hosts where Telnet is being used can intercept the packets passing by and obtain login, password and whatever else is typed with a packet analyzer.
-
Which protocol is a transport layer protocol?
- FTP
- IP
- UDP
- ASCII
Explanation:Transport layer protocols include: UDP, TCP
-
This question requires that you evaluate the underlined text to determine if it is correct.
IPv4 multicast addresses range from “192.168.0.0 to 192.168.255.255”.Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- 127.0.0.0 to 127.255.255.255
- 172.16.0.0 to 172.31.255.255
- 224.0.0.0 to 239.255.255.255
- No change is needed
Explanation:Class D is multicast.
Class A: 0.0.0.0 – 127.255.255.255
Class B: 128.0.0.0 – 191.255.255.255
Class C: 192.0.0.0 – 223.255.255.25
Class D: 224.0.0.0 – 239.255.255.255 -
This question requires that you evaluate the underlined text to determine if it is correct.
The four IEEE standards, 802.11a, b, g, and n, are collectively known as “mobile ad hoc” networks.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- WiMAX
- Bluetooth
- WiFi
- No change is needed
Explanation:IEEE 802.11 is a set of media access control (MAC) and physical layer (PHY) specifications for implementing wireless local area network (WLAN) computer communication in the 2.4, 3.6, 5, and 60 GHz frequency bands. They are created and maintained by the IEEE LAN/MAN Standards Committee (IEEE 802). The base version of the standard was released in 1997, and has had subsequent amendments. The standard and amendments provide the basis for wireless network products using the Wi-Fi brand.