98-366 : Networking Fundamentals : Part 07
98-366 : Networking Fundamentals : Part 07
-
HOTSPOT
You are configuring a wireless network with the Wireless Network Properties that are shown in the following image:
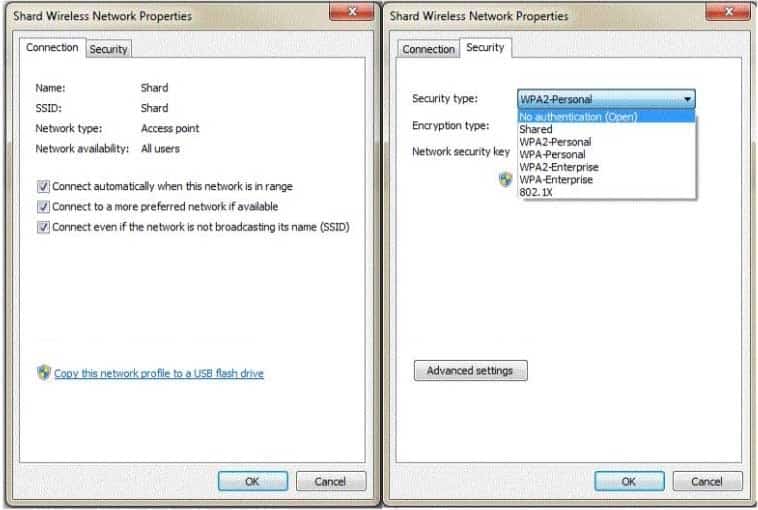
98-366 Part 07 Q01 031 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
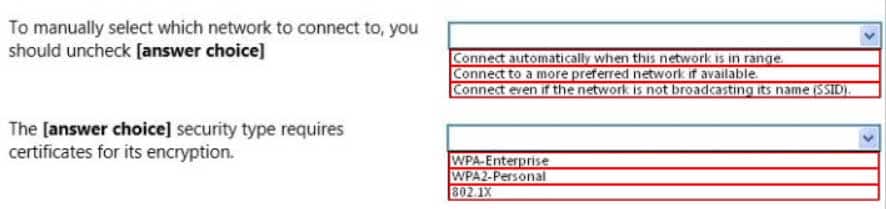
98-366 Part 07 Q01 032 Question 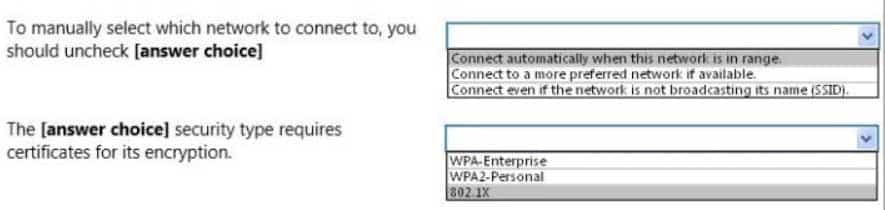
98-366 Part 07 Q01 032 Answer Explanation:* Connect automatically when this network is in range
If you want to have a network in the list, but don’t want Windows to connect to it automatically, you can open up the properties from the Manage Wireless Networks dialog, and then uncheck the box for “Connect automatically when this network is in range”.
* 802.1x
This deployment scenario requires server certificates for each NPS server that performs 802.1X authentication. -
This question requires that you evaluate the underlined text to determine if it is correct.
“A/anvirtual private network (VPN)” protects a network’s perimeter by monitoring traffic as it enters and leaves.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- Extranet
- Firewall
- Intranet
- No change is needed
Explanation:A firewall is software or hardware that checks information coming from the Internet or a network, and then either blocks it or allows it to pass through to your computer, depending on your firewall settings.
-
This question requires that you evaluate the underlined text to determine if it is correct.
The loopback address of your computer is “127.0.0.1”.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- 10.0.1.1
- 169.254.0.5
- 192168.1.1
- No change is needed
Explanation:127.0.0.1 is the IPv4 loopback address.
-
You run the ipconfig command. The output is shown in the following image:
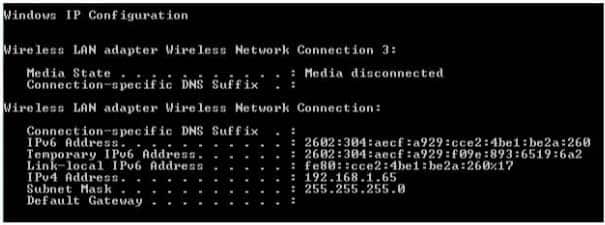
98-366 Part 07 Q04 033 From these settings, you can tell that the computer:
- Will have limited Internet access
- Will have full Internet access
- Will not be able to access the Internet
- Will not be able to access the local network
-
Which IEEE 802.11 Wi-Fi networking standard requires dual antennas so it can run in all of its supported frequencies?
- 802.11a
- 802.11b
- 802.11g
- 802.11n
Explanation:IEEE 802.11n-2009, commonly shortened to 802.11n, is a wireless networking standard that uses multiple antennas to increase data rates.
-
What is the bit rate for a North American T3 circuit?
- 6.312 Mbit/s
- 44.736 Mbit/s
- 274.176 Mbit/s
- 400.352 Mbit/s
Explanation:Data Rates. DS3/T3 = 44.7 Mbps
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-366 Part 07 Q07 034 Question 
98-366 Part 07 Q07 034 Answer Explanation:* Dynamic Routing. A router with dynamically configured routing tables is known as a dynamic router. Dynamic routing consists of routing tables that are built and maintained automatically through an ongoing communication between routers.
* Most of the dominant routing algorithms are dynamic routing algorithms, which adjust to changing network circumstances by analyzing incoming routing update messages. If the message indicates that a network change has occurred, the routing software recalculates routes and sends out new routing update messages. These messages permeate the network, stimulating routers to rerun their algorithms and change their routing tables accordingly.
* When there are multiple routes to the same destination, a router must have a mechanism for calculating the best path. A metric is a variable assigned to routes as a means of ranking them from best to worst or from most preferred to least preferred. -
Which feature of Category 5e STP cable reduces external interference?
- Crosstalk
- Shielding
- Length
- Twisting
Explanation:Twisted pair cabling is a type of wiring in which two conductors of a single circuit are twisted together for the purposes of canceling out electromagnetic interference (EMI) from external sources.
-
What are three advantages of VLANs? (Choose three.)
- They can logically address packets by using IP.
- They require a router to connect to VLANs on another switch.
- They compartmentalize a network and isolate traffic.
- They are efficient because a single switch can implement only a single VLAN.
- They act as though they are on the same LAN regardless of physical location.
Explanation:VLANs provide the following advantages:
* (E) VLANs enable logical grouping of end-stations that are physically dispersed on a network. …
* VLANs reduce the need to have routers deployed on a network to contain broadcast traffic. …
* (C) Confinement of broadcast domains on a network significantly reduces traffic.
By confining the broadcast domains, end-stations on a VLAN are prevented from listening to or receiving broadcasts not intended for them.
* (B) If a router is not connected between the VLANs, the end-stations of a VLAN cannot communicate with the end-stations of the other VLANs. -
DRAG DROP
Match the OSI layer to its corresponding description.To answer, drag the appropriate OSI layer from the column on the left to its description on the right. Each OSI layer may be used once, more than once, or not at all. Each correct match is worth one point.
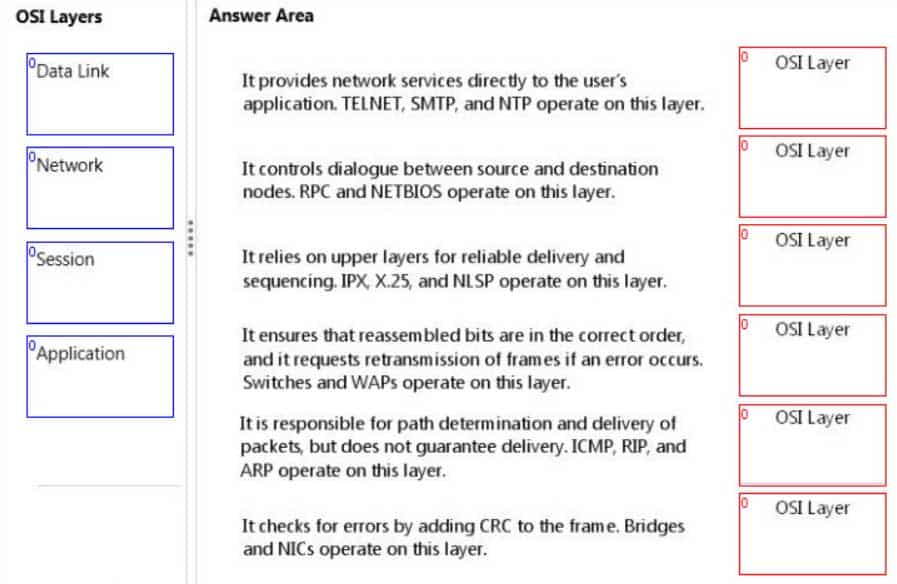
98-366 Part 07 Q10 035 Question 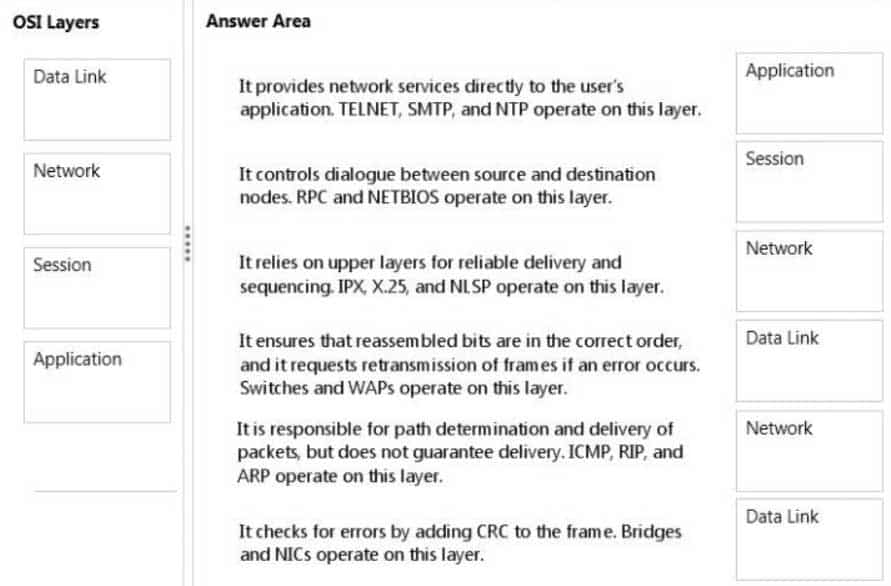
98-366 Part 07 Q10 035 Answer Explanation:* (1) Application layer protocols include:
Remote login to hosts: Telnet
File transfer: File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP)
Electronic mail transport: Simple Mail Transfer Protocol (SMTP)
NTP, Network Time Protocol
* (2) Session Layer
Session-layer services are commonly used in application environments that make use of remote procedure calls (RPCs).
NetBios is also a session layer protocol.
* (3) Network Layer
The network layer is responsible for packet forwarding including routing through intermediate routers.
Network Layer protocols include IPX (Internetwork Packet Exchange).
/ X.25 is one of the oldest packet-switched services available. It was developed before the OSI Reference Model. The protocol suite is designed as three conceptual layers, which correspond closely to the lower three layers of the seven-layer OSI model. It also supports functionality not found in the OSI network layer.
/ NetWare Link Services Protocol (NLSP) is a routing protocol for Internetwork Packet Exchange (IPX).
* (4) Data link layer
WAPs (Wireless access points) and wwitches operate on the data link layer.
* (5) Network layer
Network layer protocols include ICMP (Internet Control Message Protocol), RIP (Routing Information Protocol), and ARP (Address Resolution Protocol).
* (6) Data link layer
the data link layer is responsible for media access control, flow control and error checking.
Bridges and network cards are on the data link layer. -
HOTSPOT
You receive a call from a family member who is unable to connect to a game server.You learn that the server’s IP is 172.16.2.11.
To help, you ping the server and receive the information shown in the following image:
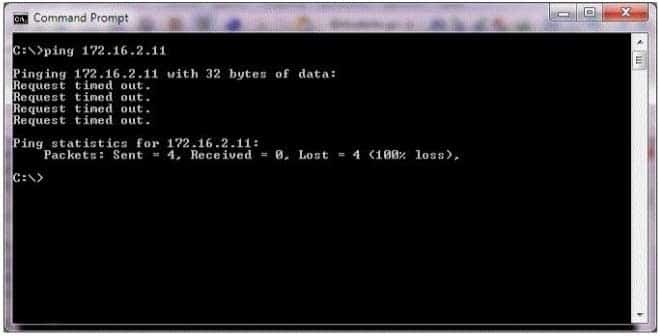
98-366 Part 07 Q11 036 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
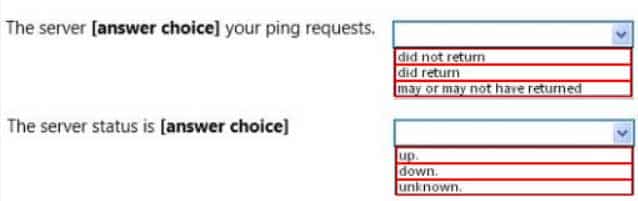
98-366 Part 07 Q11 037 Question 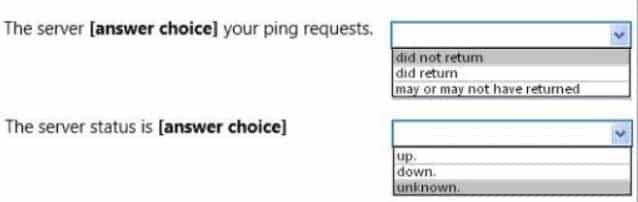
98-366 Part 07 Q11 037 Answer Explanation:* Received = 0 means that that the ping request did not return any answers.
* Request timed out.
This message indicates that no Echo Reply messages were received within the default time of 1 second. This can be due to many different causes; the most common include network congestion, failure of the ARP request, packet filtering, routing error, or a silent discard.So we cannot know if the server is down or not.
-
DRAG DROP
Match each address type to its appropriate range.
To answer, drag the appropriate address type from the column on the left to its range on the right. Each address type may be used once, more than once, or not at all. Each correct match is worth one point.
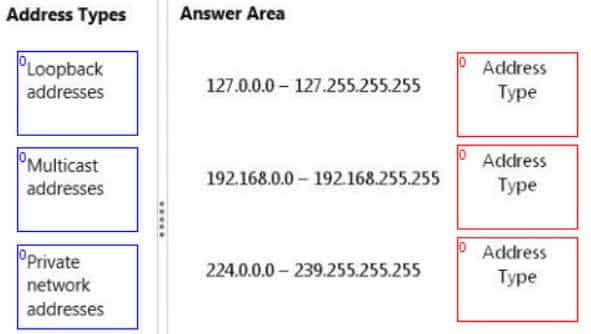
98-366 Part 07 Q12 038 Question 
98-366 Part 07 Q12 038 Answer -
For which two reasons should you use IPsec between computers? (Choose two.)
- Data compression
- Data integrity
- Data redundancy
- Data confidentiality
Explanation:IPSEC (Internet Protocol Security) is a security protocol that provides encryption and authentication over the Internet. IPSEC supports network-level data integrity, data confidentiality, data origin authentication, and replay protection.
-
This question requires that you evaluate the underlined text to determine if it is correct.
Every router today is “TCP/IP” enabled, which is an industry-standard protocol that you use on the Internet and for local addressing.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- HTTP
- FTP
- SNMP
- No change is needed
-
You are home for vacation, and a family member wants your help to purchase and install network cable for a home office.
The cable needs to support at least 300 Mbps.
What is the least expensive option that meets this requirement?
- Cat3
- CAT5
- Cat5e
- Cat6
Explanation:Cat5e cables support up to 1000BASE-T (Gigabit Ethernet).
Incorrect:
not cat5: Max speed is 100Mbps
not Cat6: 20% higher cost than Cat 5e. -
This question requires that you evaluate the underlined text to determine if it is correct.
“WEP” wireless encryption is the most susceptible to interception and decryption.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct
- WPA-AES
- WPA2
- WPA-PSK
- No change is needed
Explanation:Several weaknesses have been discovered using WEP encryption that allows an attacker using readily available software to crack the key within minutes.
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
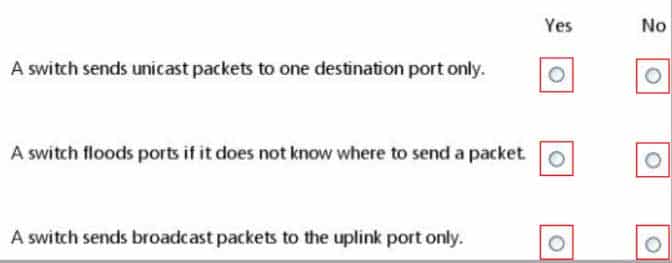
98-366 Part 07 Q17 039 Question 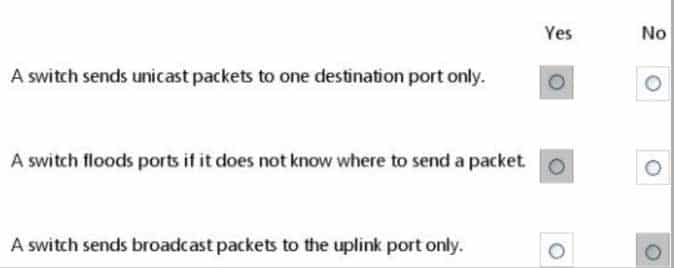
98-366 Part 07 Q17 039 Answer Explanation:* Yes. Unicast
Unicast is a one-to one connection between the client and the server.* Yes. No.
As part of the learning process, a switch will flood (broadcast) the single frame out all of its other ports when it cannot find the destination MAC address in the switch’s lookup table. -
What is an example of a network device that associates a network address with a port?
- Switch
- Router
- Hub
- DSL modem
Explanation:A router is a Layer 3 gateway device, meaning that it connects two or more networks and that the router operates at the network layer of the OSI model.
Incorrect:
not switch: Any switch that provides this ‘basic’ functionality, operates at the 2nd OSI layer also known as the Datalink Layer.
not hub: A network hub, or a repeater, is a simple network device that does not manage any of the traffic coming through it. Any packet entering a port is flooded out or “repeated” on every other port, except for the port of entry. -
Which wireless communication problem is caused by electromagnetic waves?
- Fading
- Attenuation
- Interference
- Diffraction
Explanation:Because the air is shared by all transmitters, transmissions by any device at the same frequency as an access point’s radio can cause interference. Because 802.11 wireless networks operate in unlicensed bands used by many technologies, such as microwave ovens, video surveillance cameras, cordless phones, they are subject to interference.
-
An Action Center alert recommends that you enable Windows Firewall.
After enabling the firewall, you can no longer access websites.
Which two TCP ports should you add exceptions for on the firewall? (Choose two.)
- Port 21
- Port 23
- Port 25
- Port 80
- Port 443
Explanation:Port 80: HTTP
Port 443: HTTPS