98-367 : Security Fundamentals : Part 02
98-367 : Security Fundamentals : Part 02
-
The Windows Firewall protects computers from unauthorized network connections.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Email viruses
- Phishing scams
- Unencrypted network access
- No change is needed
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 02 Q02 009 Question 
98-367 Part 02 Q02 009 Answer -
Coho Winery wants to increase their web presence and hires you to set up a new web server. Coho already has servers for their business and would like to avoid purchasing a new one.
Which server is best to use as a web server, considering the security and performance concerns?
- SQL Server
- File Server
- Domain Controller
- Application Server
-
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Malware
- Spoofed mail
- Spam
- No change is needed.
-
The client computers on your network are stable and do not need any new features.
Which is a benefit of applying operating system updates to these clients?
- Keep the software licensed
- Keep the server ports available
- Update the hardware firewall
- Close existing vulnerabilities
-
Which password attack uses all possible alpha numeric combinations?
- Social engineering
- Brute force attack
- Dictionary attack
- Rainbow table attack
-
A digitally signed e-mail message:
- Validates the recipient
- Validates the sender
- Is encrypted
- Is virus-free
Explanation:
By digitally signing a message, you apply your unique digital mark to the message. The digital signature includes your certificate and public key. This information proves to the recipient that you signed the contents of the message and not an imposter, and that the contents have not been altered in transit. -
HOTSPOT
You are preparing a local audit policy for your workstation. No auditing is enabled.The settings of your policy are shown in the following image:
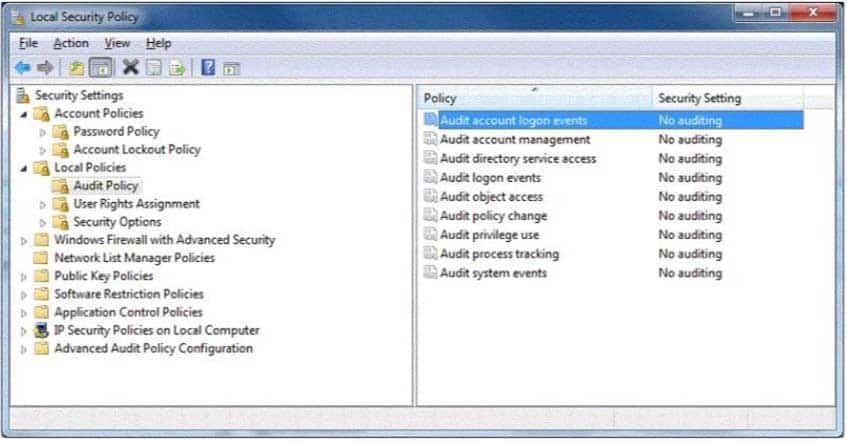
98-367 Part 02 Q08 010 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
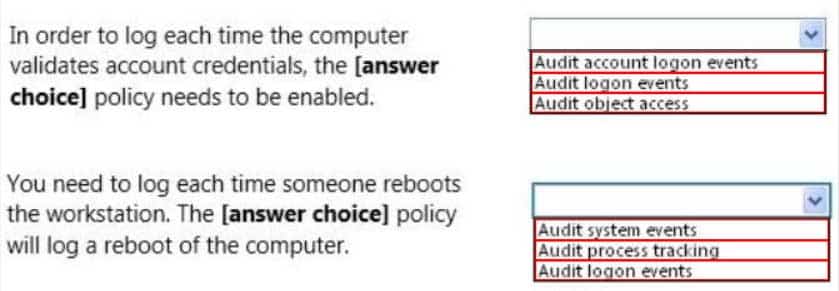
98-367 Part 02 Q08 011 Question 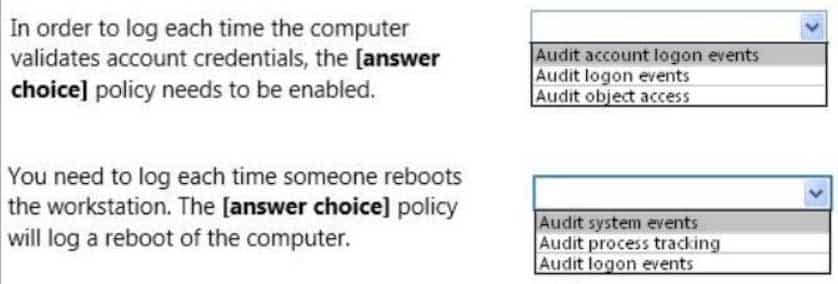
98-367 Part 02 Q08 011 Answer Explanation:
Dozens of events can be audited in Windows. The events fall into several categories:
– Audit account logon events – audit each instance of a user logging on to or logging off from another computer in which this computer is used to validate the account. This event category is applicable to domain controllers only since DC’s are used to validate accounts in domains.
– Audit account management – audit each event of account management on a computer. Examples of account maintenance include password changes, user account and group modifications.
– Audit directory service access – audit the event of a user accessing an Active Directory object that has its own system access control list (SACL) specified.
– Audit logon events – audit each instance of a user logging on to or logging off from a computer. Note that this is different than the ‘Audit account login events’ category. This tracks the logon event to a specific server. The former tracks which domain controller authenticated the user.
– Audit object access – audit the event of a user accessing an object that has its own system access control list (SACL) specified. Examples of objects are files, folders, registry keys, printers, etc.
– Audit policy change – audit every incident of a change to user rights assignment policies, audit policies, or trust policies.
– Audit privilege use – audit each instance of a user exercising a user right.
– Audit process tracking – audit detailed tracking information for events such as program activation, process exit, handle duplication, and indirect object access.
– Audit system events – audit when a user restarts or shuts down the computer or when an event occurs that affects either the system security or the security log. -
HOTSPOT
You are at school and logged in to a Windows 7 computer using a standard user account.You need to change some of the properties of a desktop icon for an assignment. Your instructor provides you with an administrator username and password and asks you to do two tasks.
When you open the Need Admin Access Properties window, you see the following image:
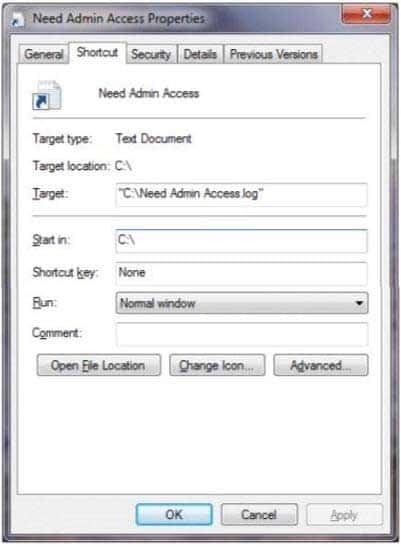
98-367 Part 02 Q09 012 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
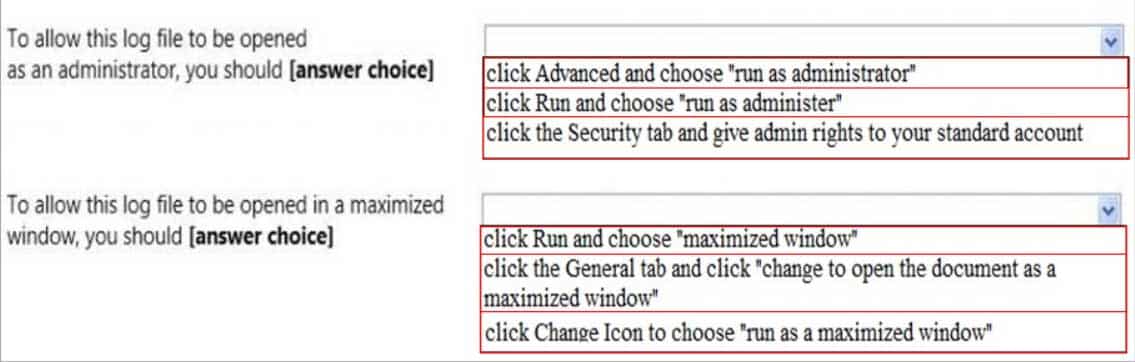
98-367 Part 02 Q09 013 Question 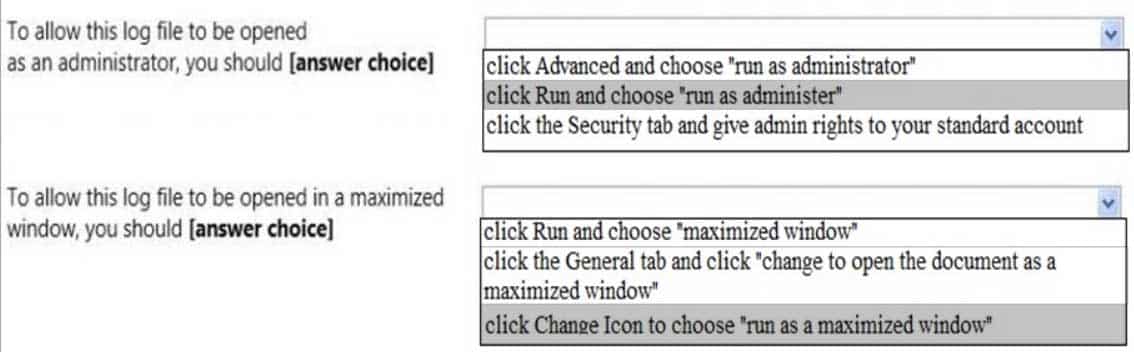
98-367 Part 02 Q09 013 Answer -
Passwords that contain recognizable words are vulnerable to a:
- Denial of Service attack
- Hashing attack
- Dictionary attack
- Replay attack
Explanation:
A dictionary attack is a method of breaking into a password-protected computer or server by systematically entering every word in a dictionary as a password. A dictionary attack can also be used in an attempt to find the key necessary to decrypt an encrypted message or document.Dictionary attacks work because many computer users and businesses insist on using ordinary words as passwords. Dictionary attacks are rarely successful against systems that employ multiple-word phrases, and unsuccessful against systems that employ random combinations of uppercase and lowercase letters mixed up with numerals.
-
Account lockout policies are used to prevent which type of security attack?
- Brute force attacks
- Users sharing passwords
- Social engineering
- Passwords being reused immediately
-
What is the standard or basic collection of NTFS permissions?
- Read and execute, read, write, full control, modify, list folder contents
- Change permissions, read permissions, write permissions
- Read attributes, list folder/read data, traverse folder/execute file
- Create files/write data, create folders/append data, take ownership
-
Which is the minimum requirement to create BitLocker-To-Go media on a client computer?
- Windows XP Professional Service Pack 3
- Windows Vista Enterprise Edition
- Windows 7 Enterprise Edition
- Windows 2000 Professional Service Pack 4
-
Which enables you to change the permissions on a folder?
- Take ownership
- Extended attributes
- Auditing
- Modify
-
A group of users has access to Folder A and all of its contents. You need to prevent some of the users from accessing a subfolder inside Folder A.
What should you do first?
- Disable folder sharing
- Hide the folder
- Change the owner
- Block inheritance
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 02 Q16 014 Question 
98-367 Part 02 Q16 014 Answer Explanation:
Biometric devices, such as finger scanners consist of a reader or scanning device, Software that converts the scanned information into digital form and compares match points, and a database that stores the biometric data for comparison. To prevent identity theft, biometric data is usually encrypted when it is gathered. -
What are three examples of two-factor authentication? (Choose three.)
- A fingerprint and a pattern
- A password and a smart card
- A username and a password
- A password and a pin number
- A pin number and a debit card
Explanation:
At minimum two-factor authentication requires two out of three regulatory-approved authentication variables such as:
– Something you know (like the PIN on your bank card or email password).
– Something you have (the physical bank card or a authenticator token).
– Something you are (biometrics like your finger print or iris pattern). -
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 02 Q18 015 Question 
98-367 Part 02 Q18 015 Answer -
You need to limit the programs that can run on client computers to a specific list.
Which technology should you implement?
- Windows Security Center
- Security Accounts Manager
- System Configuration Utility
- AppLocker group policies
-
The purpose of User Account Control (UAC) is to:
- Encrypt the user’s account
- Limit the privileges of software
- Secure your data from corruption
- Facilitate Internet filtering
Explanation:
User Account Control (UAC) is a technology and security infrastructure introduced with Microsoft’s Windows machines. It aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an administrator authorizes an increase or elevation. In this way, only applications trusted by the user may receive administrative privileges, and malware should be kept from compromising the operating system.