98-367 : Security Fundamentals : Part 03
98-367 : Security Fundamentals : Part 03
-
What does implementing Windows Server Update Services (WSUS) allow a company to manage?
- Shared private encryption key updates
- Updates to Group Policy Objects
- Active Directory server replication
- Windows updates for workstations and servers
-
The purpose of Microsoft Baseline Security Analyzer is to:
- List system vulnerabilities.
- Apply all current patches to a server.
- Set permissions to a default level.
- Correct a company’s security state.
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
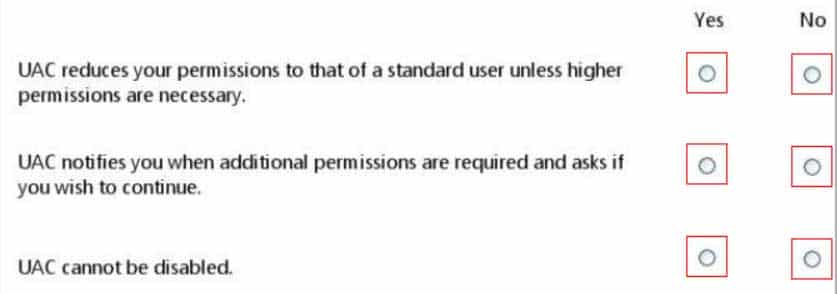
98-367 Part 03 Q03 016 Question 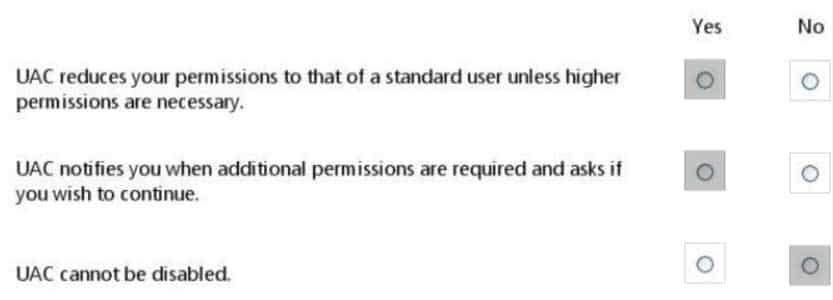
98-367 Part 03 Q03 016 Answer -
The Graphic Design Institute hires you to help them set up a server for their 20-person team.
As a general practice of hardening the server, you start by performing which two tasks? (Choose two.)
- Disable the guest account.
- Rename the admin account.
- Remove the account lockout policy.
- Format partitions with FAT32.
-
What are two attributes that an email message may contain that should cause a user to question whether the message is a phishing attempt? (Choose two.)
- An image contained in the message
- Spelling and grammar errors
- Threats of losing service
- Use of bold and italics
-
Keeping a server updated:
- Maximizes network efficiency
- Fixes security holes
- Speeds up folder access
- Synchronizes the server
-
Before you deploy Network Access Protection (NAP), you must install:
- Internet Information Server (IIS)
- Network Policy Server (NPS)
- Active Directory Federation Services
- Windows Update Service
-
What is a common method for password collection?
- Email attachments
- Back door intrusions
- SQL Injection
- Network sniffers
-
Which provides the highest level of security in a firewall?
- Stateful inspection
- Outbound packet filters
- Stateless inspection
- Inbound packet filters
-
The primary method of authentication in an SSL connection is passwords.
To answer, choose the option “No change is needed” if the underlined text is correct. If the underlined text is not correct, choose the correct answer.
- No change is needed
- Certificates
- IPsec
- Biometrics
-
You are setting up Remote Desktop on your computer. Your computer is a member of a domain.
Your firewall configuration is shown in the following image:
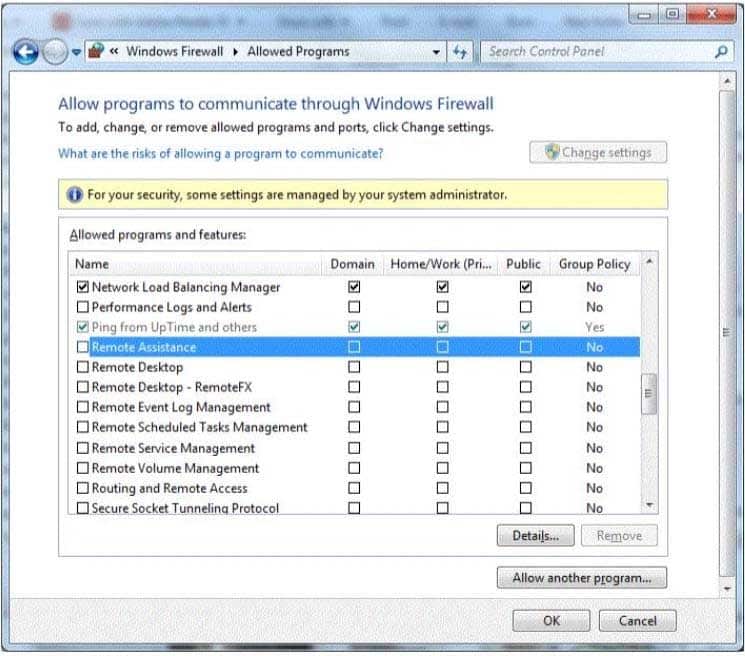
98-367 Part 03 Q11 017 You need to allow Remote Desktop to be able to get through your firewall for users on your company’s network.
Which settings should you enable?
- Remote Assistance: Home/Work (Private)
- Remote Desktop: Public
- Remote Desktop: Home/Work (Private)
- Remote Assistance: Domain
-
You are trying to connect to an FTP server on the Internet from a computer in a school lab. You cannot get a connection. You try on another computer with the same results. The computers in the lab are able to browse the Internet.
You are able to connect to this FTP server from home.
What could be blocking the connection to the server?
- A layer-2 switch
- A wireless access point
- A firewall
- A layer-2 hub
-
What does NAT do?
- It encrypts and authenticates IP packets.
- It provides caching and reduces network traffic.
- It translates public IP addresses to private addresses and vice versa.
- It analyzes incoming and outgoing traffic packets.
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 03 Q14 018 Question 
98-367 Part 03 Q14 018 Answer -
The default password length for a Windows Server domain controller is:
- 0
- 5
- 7
- 14
-
HOTSPOT
Your supervisor asks you to review file permission settings on the application.bat file.You need to report which file system the file is on and the type of permission the file has.
You review the application Properties dialog box shown in the following image:
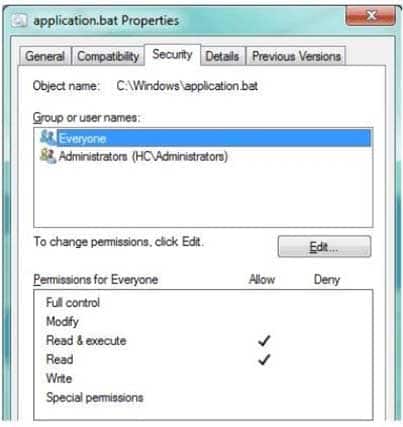
98-367 Part 03 Q16 019 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
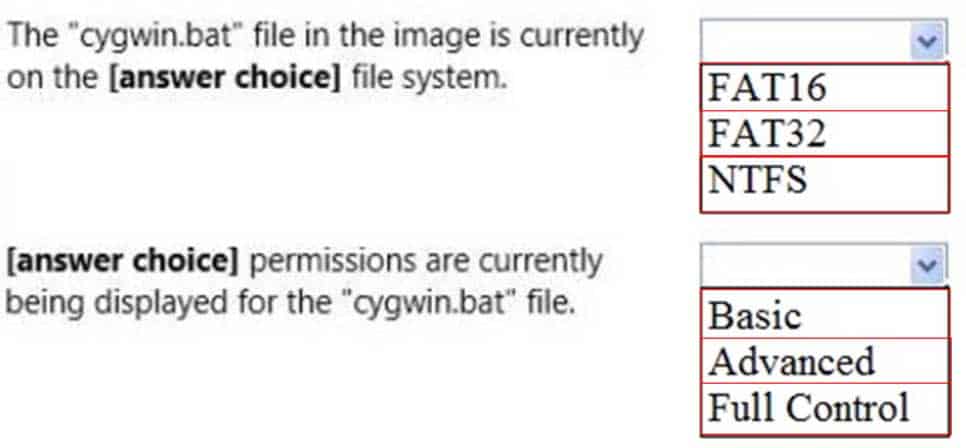
98-367 Part 03 Q16 020 Question 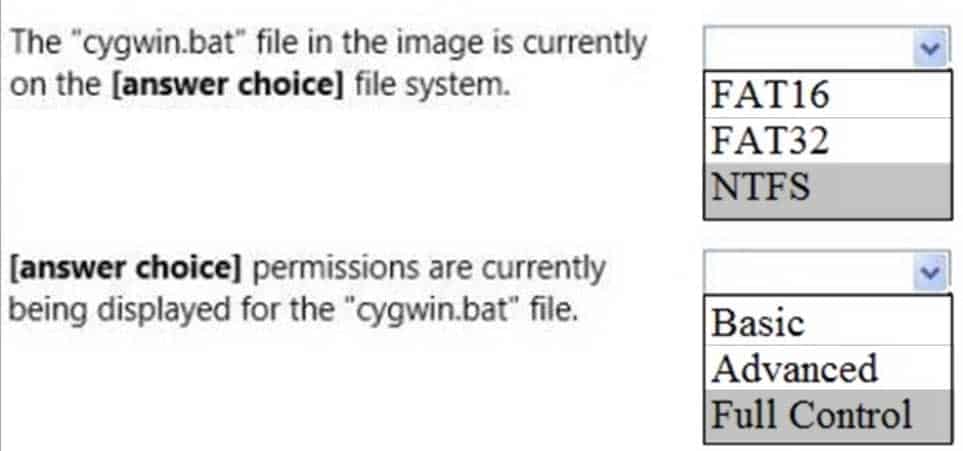
98-367 Part 03 Q16 020 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 03 Q17 021 Question 
98-367 Part 03 Q17 021 Answer -
You create a web server for your school. When users visit your site, they get a certificate error that says your site is not trusted.
What should you do to fix this problem?
- Install a certificate from a trusted Certificate Authority (CA).
- Use a digital signature.
- Generate a certificate request.
- Enable Public Keys on your website.
-
What is an example of non-propagating malicious code?
- A back door
- A hoax
- A Trojan horse
- A worm
-
A brute force attack:
- Uses response filtering
- Tries all possible password variations
- Uses the strongest possible algorithms
- Targets all the ports