98-367 : Security Fundamentals : Part 04
98-367 : Security Fundamentals : Part 04
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 04 Q01 022 Question 
98-367 Part 04 Q01 022 Answer -
Humongous Insurance is an online healthcare insurance company. During an annual security audit a security firm tests the strength of the company’s password policy and suggests that Humongous Insurance implement password history policy.
What is the likely reason that the security firm suggests this?
- Past passwords were easily cracked by the brute force method.
- Past passwords of users contained dictionary words.
- Previous password breaches involved use of past passwords.
- Past passwords lacked complexity and special characters.
-
The WPA2 PreShared Key (PSK) is created by using a passphrase (password) and salting it with the WPS PIN.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Service Set Identifier (SSID)
- Admin password
- WEP key
- No change is needed
-
What are three major attack vectors that a social engineering hacker may use? (Choose three.)
- Telephone
- Reverse social engineering
- Waste management
- Honey pot systems
- Firewall interface
-
Which two security settings can be controlled by using group policy? (Choose two.)
- Password complexity
- Access to the Run… command
- Automatic file locking
- Encrypted access from a smart phone
-
Cookies impact security by enabling: (Choose two.)
- Storage of Web site passwords.
- Higher security Web site protections.
- Secure Sockets Layer (SSL).
- Web sites to track browsing habits.
-
To keep third-party content providers from tracking your movements on the web, enable InPrivate Browsing.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- InPrivate Filtering
- SmartScreen Filter
- Compatibility Mode
- No change is needed
-
Which enables access to all of the logged-in user’s capabilities on a computer?
- Java applets
- ActiveX controls
- Active Server Pages (ASP)
- Microsoft Silverlight
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
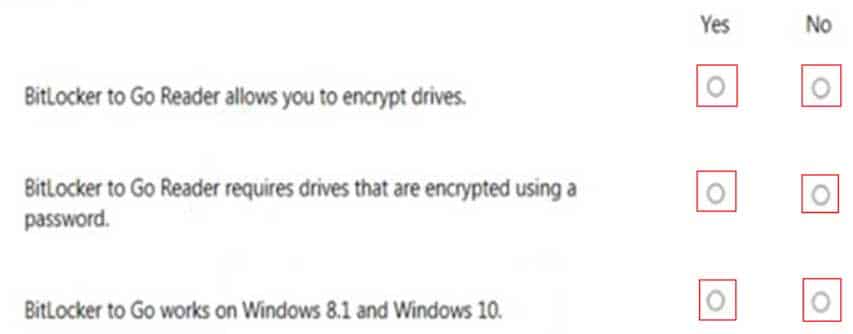
98-367 Part 04 Q09 023 Question 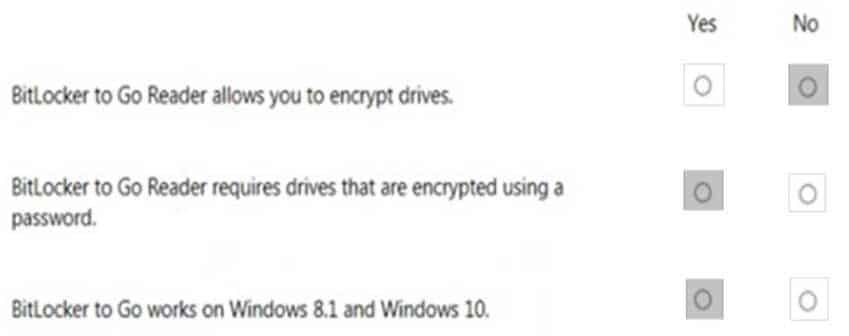
98-367 Part 04 Q09 023 Answer -
You need to install a domain controller in a branch office. You also need to secure the information on the domain controller. You will be unable to physically secure the server.
Which should you implement?
- Read-Only Domain Controller
- Point-to-Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP)
- Server Core Domain Controller
Explanation:
A read-only domain controller (RODC) is a new type of domain controller in the Windows Server® 2008 operating system. With an RODC, organizations can easily deploy a domain controller in locations where physical security cannot be guaranteed. An RODC hosts read-only partitions of the Active Directory® Domain Services (AD DS) database. -
E-mail spoofing:
- Forwards e-mail messages to all contacts
- Copies e-mail messages sent from a specific user
- Obscures the true e-mail sender
- Modifies e-mail routing logs
-
What is the primary advantage of using Active Directory Integrated Zones?
- Zone encryption
- Password protection
- Non-repudiation
- Secure replication
-
Which two are included in an enterprise antivirus program? (Choose two.)
- Attack surface scanning
- On-demand scanning
- Packet scanning
- Scheduled scanning
-
Phishing is an attempt to:
- Obtain information by posing as a trustworthy entity.
- Limit access to e-mail systems by authorized users.
- Steal data through the use of network intrusion.
- Corrupt e-mail databases through the use of viruses.
Explanation:
Phishing is the act of attempting to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication. -
Humongous Insurance needs to set up a domain controller in a branch office. Unfortunately, the server cannot be sufficiently secured from access by employees in that office, so the company is installing a Primary Domain Controller.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Read-Only Domain Controller
- Backup Domain Controller
- Active Directory Server
- No change is needed.
-
Where should you lock up the backup tapes for your servers?
- The server room
- A filing cabinet
- The tape library
- An offsite fire safe
Explanation:
Backup tapes should be stored off site, preferably in a fire safe, so that the data is available should a fire, flood, or other disaster affect the location were the servers are. -
Which is a special folder permission?
- Read
- Modify
- Write
- Delete
-
When conducting a security audit the first step is to:
- Inventory the company’s technology assets
- Install auditing software on your servers
- Set up the system logs to audit security events
- Set up a virus quarantine area
-
You are an intern at Litware, Inc. Your manager asks you to make password guess attempts harder by limiting login attempts on company computers.
What should you do?
- Enforce password sniffing.
- Enforce password history.
- Make password complexity requirements higher.
- Implement account lockout policy.
-
You need to grant a set of users write access to a file on a network share. You should add the users to:
- A security group
- The Authenticated Users group
- The Everyone group
- A distribution group