98-367 : Security Fundamentals : Part 05
98-367 : Security Fundamentals : Part 05
-
The certificate of a secure public Web server on the Internet should be:
- Issued by a public certificate authority (CA)
- Signed by using a 4096-bit key
- Signed by using a 1024-bit key
- Issued by an enterprise certificate authority (CA)
-
Setting a minimum password age restricts when users can:
- Request a password reset
- Change their passwords
- Log on by using their passwords
- Set their own password expiration
Explanation:
Configure the minimum password age to be more than 0 if you want Enforce password history to be effective. Without a minimum password age, users can cycle through passwords repeatedly until they get to an old favorite. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
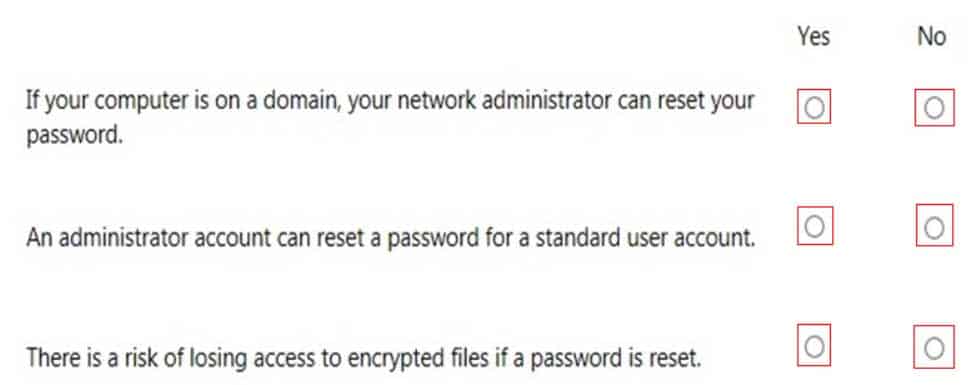
98-367 Part 05 Q03 024 Question 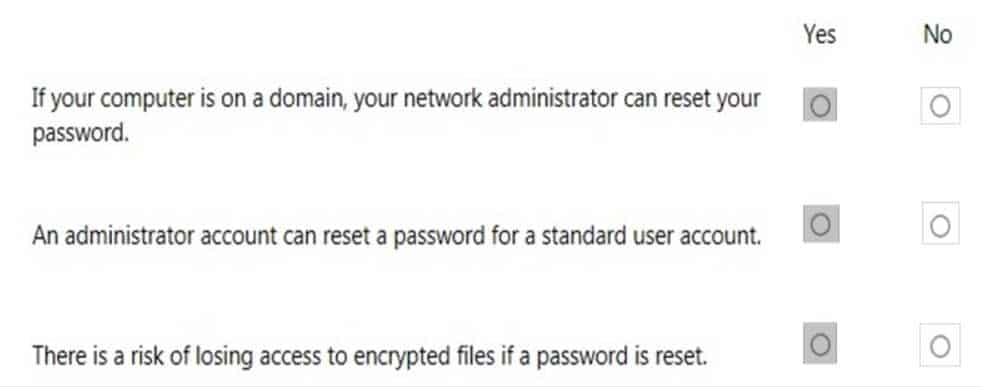
98-367 Part 05 Q03 024 Answer -
Basic security questions used to reset a password are susceptible to:
- Hashing
- Social engineering
- Network sniffing
- Trojan horses
-
You suspect a user’s computer is infected by a virus.
What should you do first?
- Restart the computer in safe mode
- Replace the computer’s hard disk drive
- Disconnect the computer from the network
- Install antivirus software on the computer
-
You create a new file in a folder that has inheritance enabled.
By default, the new file:
- Takes the permissions of the parent folder
- Does not take any permissions
- Takes the permissions of other folders in the same directory
- Takes the permissions of other files in the same directory
-
Password history policies are used to prevent:
- Brute force attacks
- Users from sharing passwords
- Social engineering
- Passwords from being reused immediately
Explanation:
This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. The value must be between 0 and 24 passwords.
This policy enables administrators to enhance security by ensuring that old passwords are not reused continually. -
HOTSPOT
You are preparing an audit policy for the workstations at Contoso, Ltd. Currently, no advanced auditing is enabled. The workstations are not members of the domain.The settings of your Advanced Audit Policy Configuration are shown in the following image:
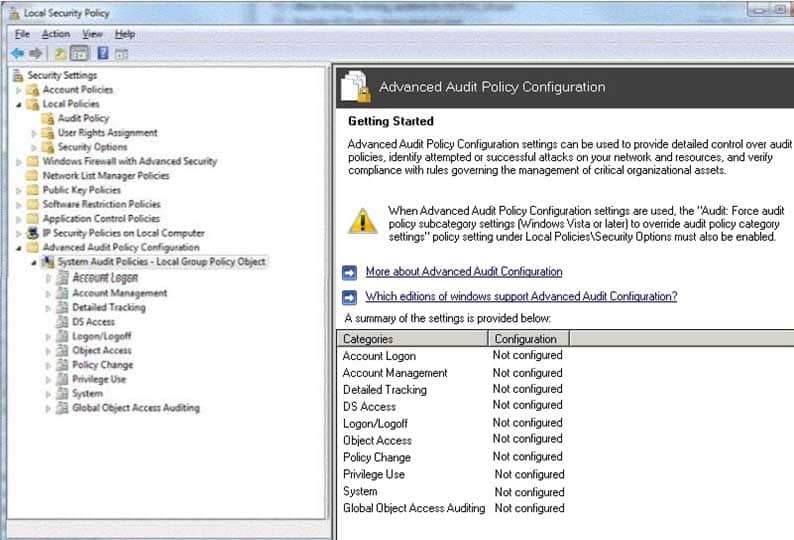
98-367 Part 05 Q08 025 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
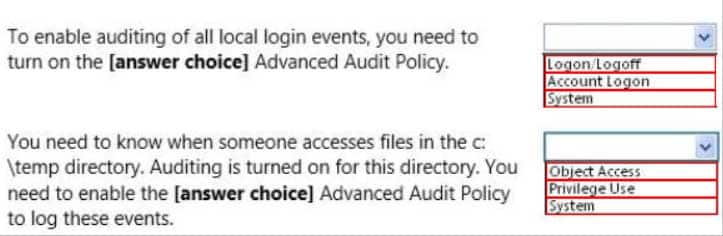
98-367 Part 05 Q08 026 Question 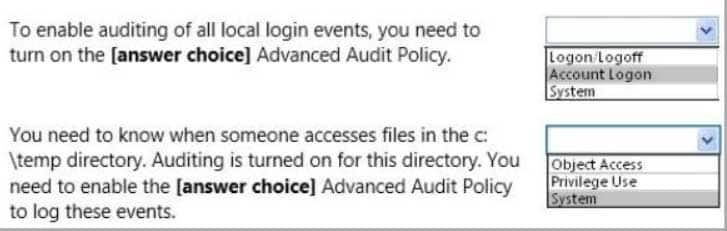
98-367 Part 05 Q08 026 Answer -
The Active Directory controls, enforces, and assigns security policies and access rights for all users.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- NTFS permissions
- User Account Control
- Registry
- No change is needed
-
Creating MD5 hash for files is an example of ensuring what?
- Confidentiality
- Availability
- Least privilege
- Integrity
Explanation:
The MD5 message-digest algorithm is a widely used cryptographic hash function producing a 128-bit (16-byte) hash value, typically expressed in text format as a 32 digit hexadecimal number. MD5 has been utilized in a wide variety of cryptographic applications, and is also commonly used to verify data integrity. -
Which three elements does HTTPS encrypt? (Choose three.)
- Browser cookies
- Server IP address
- Port numbers
- Website URL
- Login information
-
The company that you work for wants to set up a secure network, but they do not have any servers.
Which three security methods require the use of a server? (Choose three.)
- 802.1x
- WPA2 Personal
- WPA2 Enterprise
- RADIUS
- 802.11ac
-
Shredding documents helps prevent:
- Man-in-the-middle attacks
- Social engineering
- File corruption
- Remote code execution
- Social networking
-
Dumpster diving refers to a physical threat that a hacker might use to look for information about a computer network.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Phishing
- Malware
- Reverse Social engineering
- No change is needed
-
An attorney hires you to increase the wireless network security for the law firm’s office. The office has a very basic network, with just a modem and a router.
Which of these security modes offers the highest security?
- WPA-Personal
- WEP
- WPA2-Personal
- WPA-Enterprise
-
HOTSPOT
An employee where you work is unable to access the company message board in Internet Explorer.You review her Internet Options dialog box, as shown in the following image:
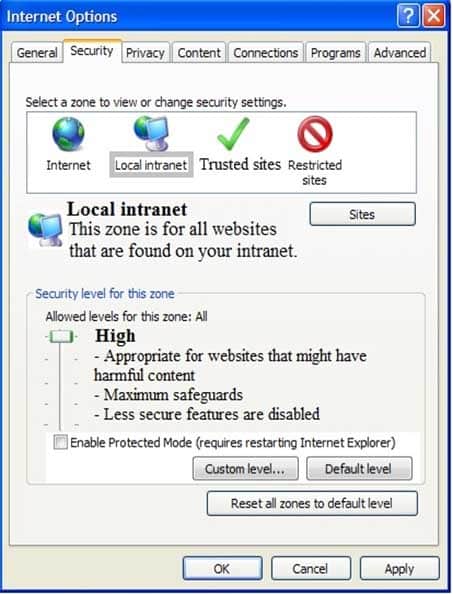
98-367 Part 05 Q16 027 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.

98-367 Part 05 Q16 028 Question 
98-367 Part 05 Q16 028 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-367 Part 05 Q17 029 Question 
98-367 Part 05 Q17 029 Answer -
HOTSPOT
Alice and Bob are exchanging messages with each other. Chuck modifies the messages sent between Alice and Bob as shown in the following image:
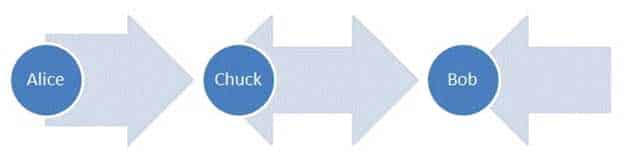
98-367 Part 05 Q18 030 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
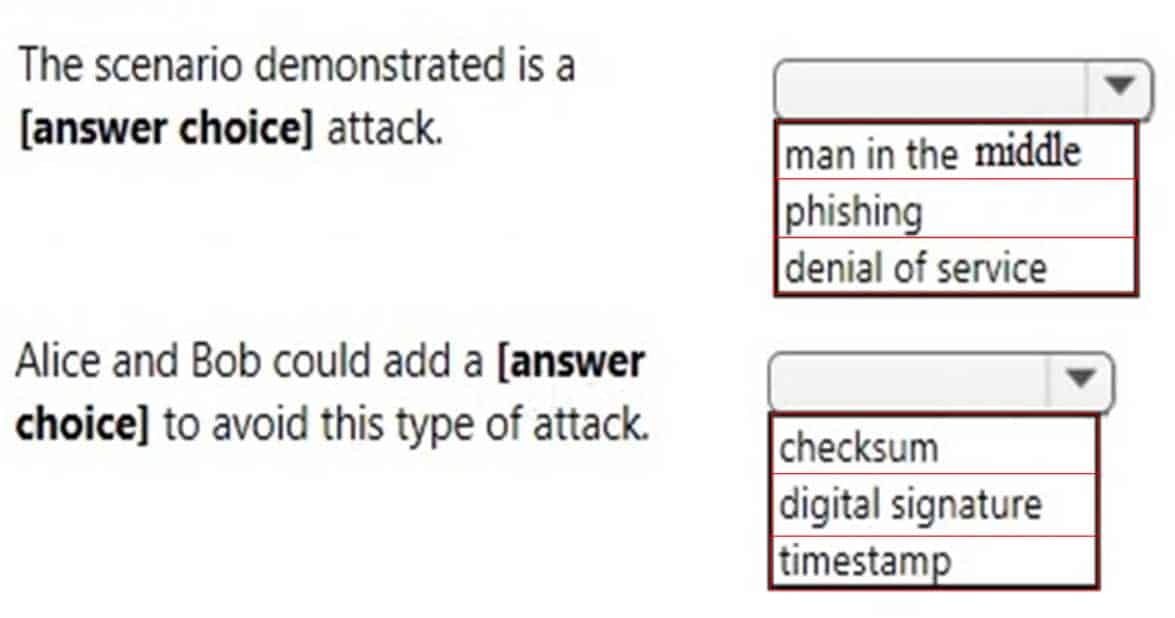
98-367 Part 05 Q18 031 Question 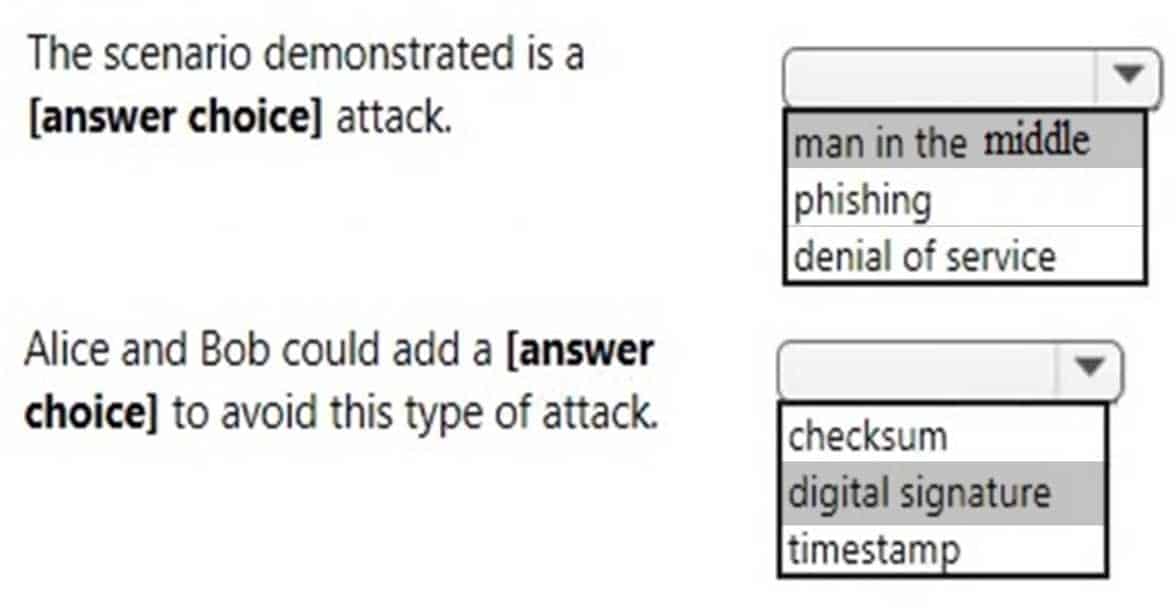
98-367 Part 05 Q18 031 Answer Explanation:
The usual way to prevent the man-in-the-middle attack is to use a public key cryptosystem capable of providing digital signatures. For set up, the parties must know each others public keys in advance. After the shared secret has been generated, the parties send digital signatures of it to each other. The man-in-the-middle can attempt to forge these signatures, but fails because he cannot fake the signatures. -
Which type of firewall allows for inspection of all characteristics of a packet?
- NAT
- Stateful
- Stateless
- Windows Defender
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
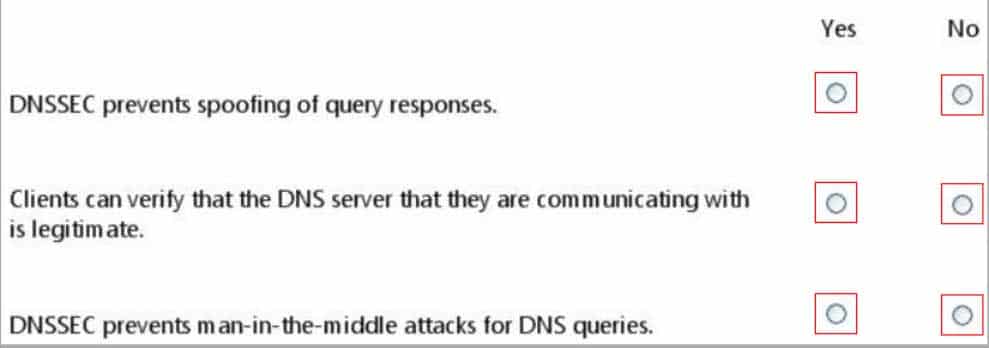
98-367 Part 05 Q20 032 Question 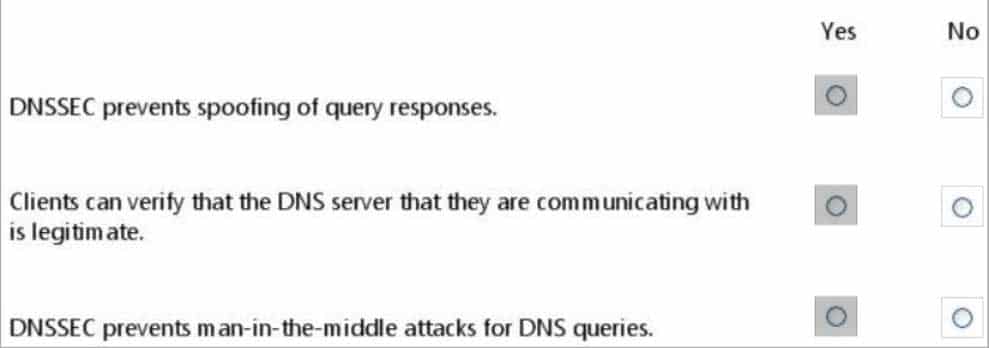
98-367 Part 05 Q20 032 Answer