98-367 : Security Fundamentals : Part 07
98-367 : Security Fundamentals : Part 07
-
Your password is 1Vu*cI!8sT.
Which attack method is your password vulnerable to?
- Rainbow table
- Brute force
- Spidering
- Dictionary
-
You have a Windows 7 desktop computer, and you create a Standard User account for your roommate so that he can use the desktop from time to time. Your roommate has forgotten his password.
Which two actions can you take to reset the password? (Choose two.)
- Use your password reset disk.
- Use your administrator account.
- Boot into Safe Mode with your roommate’s account.
- From your roommate’s account press CTRL+ALT+DELETE, and then click Change a password.
-
You have two servers that run Windows Server. All drives on both servers are formatted by using NTFS.
You move a file from one server to the other server. The file’s permissions in the new location will:
- Enable full access to the everyone group
- Restrict access to the Administrators group
- Inherit the destination folder’s permissions
- Retain the original folder’s permissions
Explanation:
You can modify how Windows Explorer handles permissions when objects are copied or moved to another NTFS volume. When you copy or move an object to another volume, the object inherits the permissions of its new folder. -
HOTSPOT
You are setting up BitLocker on a new computer.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Note: For each correct selection is worth one point.
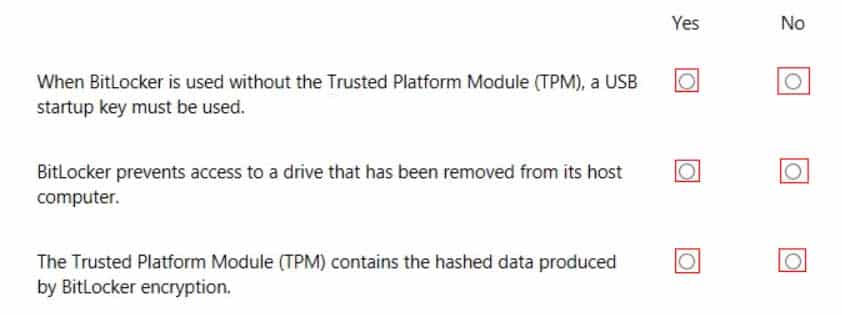
98-367 Part 07 Q04 034 Question 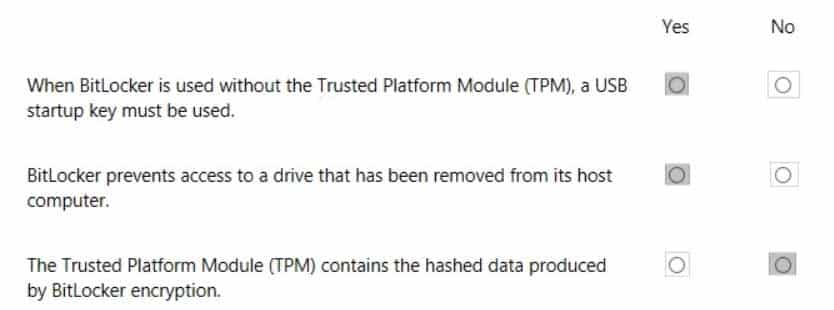
98-367 Part 07 Q04 034 Answer -
You need to be able to gather information about a running program.
Which type of auditing should you implement?
- directory services
- object access
- logon events
- process tracking
-
The purpose of Windows Server Update Services (WSUS) is to:
- manage the deployment of patches to company servers
- provide alerts and reports on system vulnerabilities
- set permissions to the minimum level necessary for each function
- update licensing for Windows servers
-
A process by which DNS zone data is obtained by an attacker is referred to as:
- spoofing
- footprinting
- phishing
- Denial of Service
-
DRAG DROP
Certain potentially harmful file types should be filtered as attachments of incoming email messages.
Match the file extension that should be filtered with its description.
Instructions: To answer, drag the appropriate file extension from the column on the left to its description on the right. Each file extension may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Note: For each correct selection is worth one point.
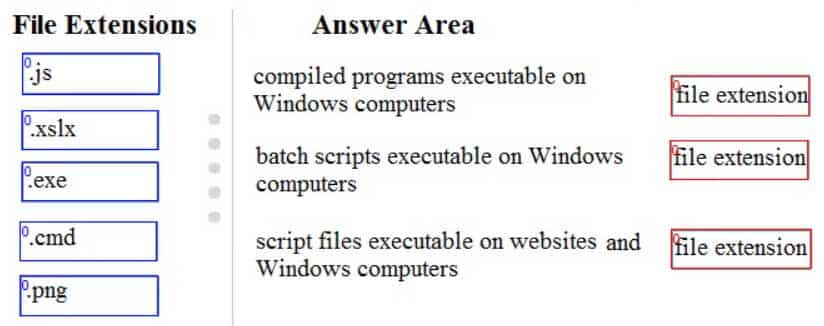
98-367 Part 07 Q08 035 Question 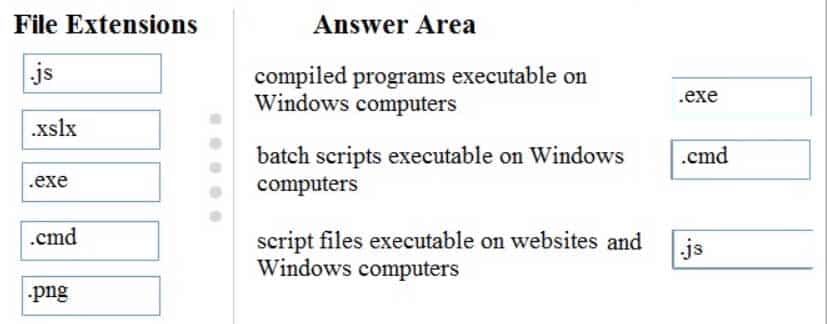
98-367 Part 07 Q08 035 Answer -
Media Access Control (MAC) filtering enables you to:
- limit access to a network based on the client computer’s network adapter.
- set access permissions to a shared folder.
- prevent communications between specific IP addresses.
- restrict communications to a specific website.
-
What are two examples of physical site security? (Choose two.)
- keeping machines in locked offices
- sending backups to a remote location
- enforcing multi-factor authentication
- using BitLocker encryption on drives
-
You are using the Microsoft Edge browser to connect to a web server that hosts a test version of a web application. You receive the following message:
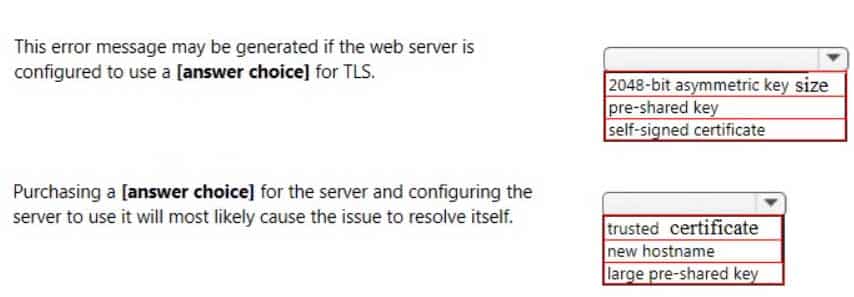
98-367 Part 07 Q11 036 Instructions: Use the drop-down menus to select the answer choice that completes each statement based on the information.
98-367 Part 07 Q11 037 Question 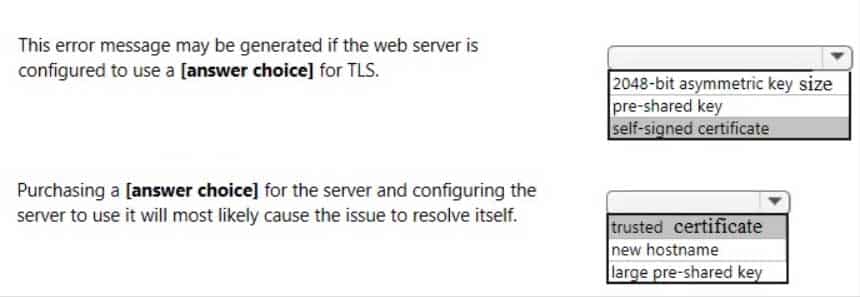
98-367 Part 07 Q11 037 Answer -
You need to hide internal IP addresses from the Internet while maintaining client access to the Internet.
What should you implement?
- Port forwarding
- Secure Sockets Layer (SSL)
- Access Control Lists
- Network Address Translation (NAT)
-
A malicious user who intercepts and modifies communications is known as a:
- red hat hacker
- white hat hacker
- network sniffer
- man-in-the-middle
-
You have an application that uses IPsec to secure communications between an Internet client and a server on the internal network.
To which network security service must the IPsec client connect?
- SFTP
- SSH
- VPN
- RADIUS
-
You want to prevent external users from acquiring information about your network. You should implement a:
- router
- layer-3 switch
- firewall
- proxy server
-
What are three examples of factors required for multi-factor authentication? (Choose three.)
- a username
- a smart card
- a fingerprint
- a password challenge question
- a pin number
-
HOTSPOT
You are helping your classmates with their password settings.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
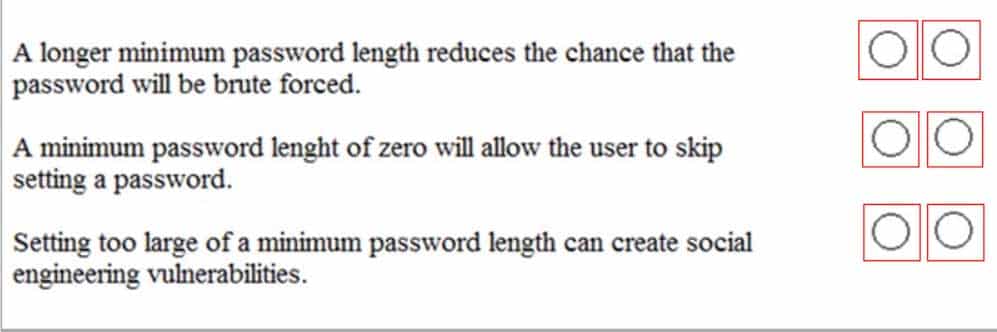
98-367 Part 07 Q17 038 Question 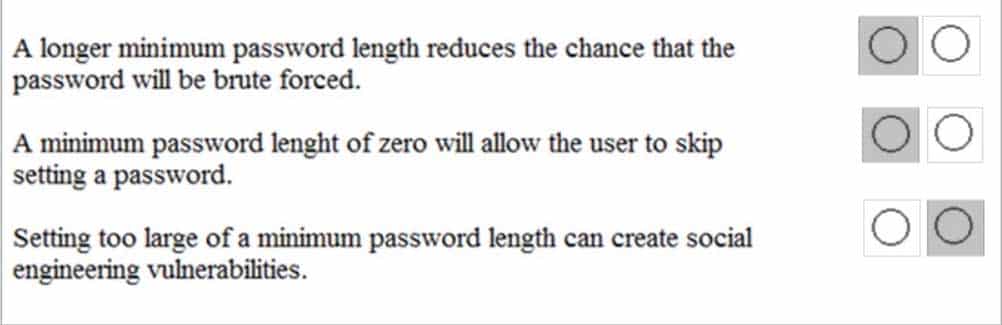
98-367 Part 07 Q17 038 Answer -
What displays a user’s level of access to a particular file or folder on the server?
- The Resultant Set of Policy
- the object’s Advanced Attributes
- the object’s Effective Permissions
- the client computer’s registry
-
You are trying to enable BitLocker on your father’s computer.
What is the purpose of the Trusted Platform Module (TPM) when it is used by BitLocker?
- to store an encrypted file allocation table for the protected drive
- to provide a co-processor that encrypts/decrypts data
- to verify the integrity of the early boot components
- to store the hashed data produced by BitLocker encryption
-
Which type of password attack attempts to guess passwords by using a list of common passwords?
- Keylogger
- brute force
- man-in-the-middle
- dictionary