98-367 : Security Fundamentals : Part 08
98-367 : Security Fundamentals : Part 08
-
Malicious software designed to collect personally identifiable information is referred to as :
- spyware
- a cookie
- a network sniffer
- freeware
-
Kerberos prevents:
- Denial of Service attacks
- spyware distribution
- file corruption
- replay attacks
-
You manage 50 Windows workstations in a computer lab. All workstations belong to the lab Active Directory domain.
You need to implement several audit policies on each workstation in the shortest time possible.
What should you do?
- Enable logging on each computer
- Create a domain Group Policy
- Turn on the Audit Policy on the domain controller
- Enable Audit object access
-
You have a Windows 2012 R2 Server. Security logging is enabled. You use this log for several audits of the server.
You need to make sure the log is not overwritten when it reaches its maximum log size.
What should you do?
- Copy logs regularly to a different location
- Maintain a backup of the log file
- Increase the log file size
- Enable archiving
-
The name of a particular wireless LAN that is broadcast on a network is referred to as a:
- MAC address
- Basis Service Set (BSS)
- Wireless Access Point (WAP)
- Service Set Identifier (SSID)
-
This question requires that you evaluate the underlined text to determine if it is correct.
An example of physical security for a laptop is a/an cable lock.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed.” If the statement is incorrect, select the answer choice that makes the statement correct.
- docking station
- fingerprint reader
- external USB drive
- No change is needed
-
DRAG DROP
Match the components of a secure website with their role in securing communication.
Instructions: To answer, drag the appropriate component from the column on the left to its role on the right. Each component may be used once, more than once or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
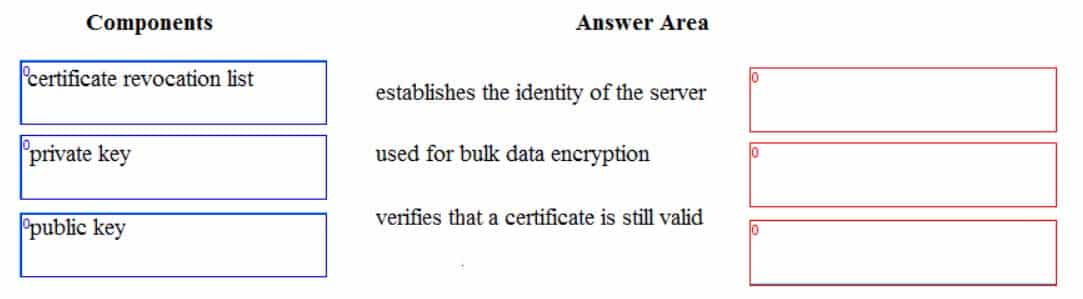
98-367 Part 08 Q07 039 Question 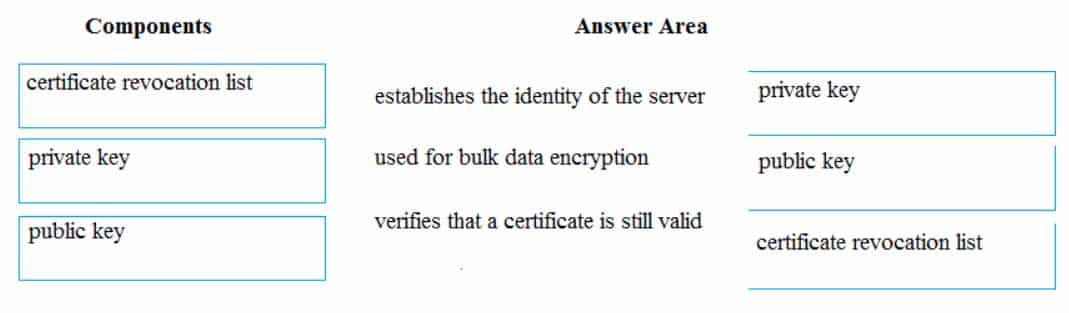
98-367 Part 08 Q07 039 Answer -
The reason for implementing Service Set IDentifier (SSID) masking is to:
- enforce a more secure password policy
- hide a wireless network name from unknown computers
- hide a network share from unauthorized users
- disable autologon
-
Email spoofing:
- obscures the true email sender
- copies email messages sent from a specific user
- modifies email routing logs
- forwards email messages to all contacts
-
This question requires that you evaluate the underlined text to determine if it is correct.
To determine which action, if any, to take on an inbound message, anti-spam and antivirus recipient filtering inspects the IP address of the remote server that is trying to send messages.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed.” If the statement is incorrect, select the answer choice that makes the statement correct.
- connection
- sender
- content
- No change is needed
-
What are two reasons to implement VLANs? (Choose two.)
- Manage traffic flow between the Internet and the network
- Create the most secure path between two hosts
- Enable grouping of hosts regardless of physical location
- Separate hosts on the same network
-
This question requires that you evaluate the underlined text to determine if it is correct.
Dedicated perimeter firewalls often provide a service named static packet filtering, which converts interval private addresses into an external Internet address.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed.” If the statement is incorrect, select the answer choice that makes the statement correct.
- Application Layer filtering
- Network Address Translation
- circuit-level inspection
- No change is needed
-
HOTSPOT
You are setting up the wireless network for your class.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
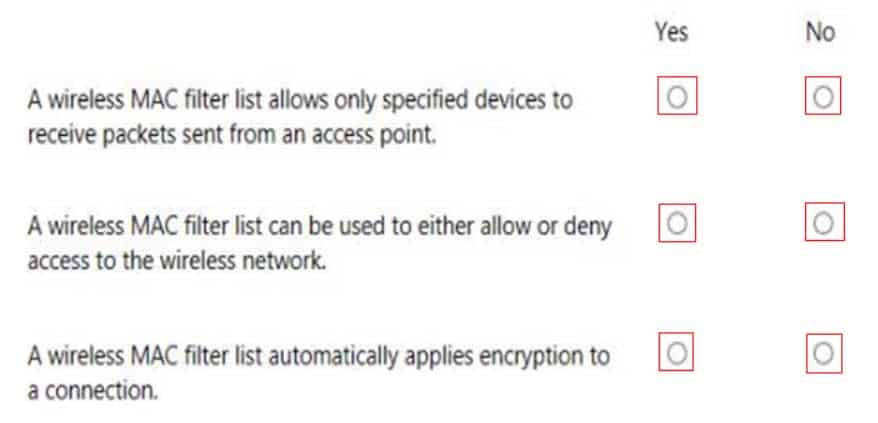
98-367 Part 08 Q13 040 Question 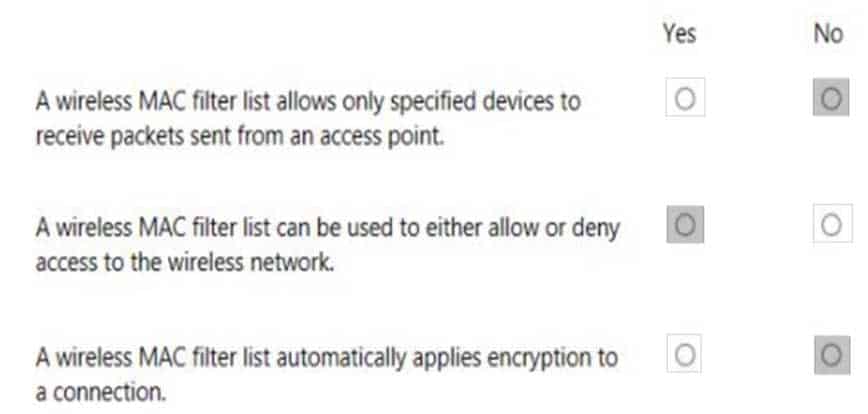
98-367 Part 08 Q13 040 Answer -
Installing uninterruptible power sources to your servers is an example of ensuring:
- integrity
- a backup strategy
- availability
- accessibility
-
Setting a database to run on a cluster of servers is an example of applying:
- accessibility
- availability
- confidentially
- integrity
-
What are three ways you can reduce the number of opportunities that attackers have to exploit potential weaknesses or vulnerabilities? (Choose three.)
- Employ layered defenses
- Elevate all accounts to administrator accounts
- Apply the principle of least privilege
- Employ content filtering for web browsers
- Restrict access to system services
-
You are a network administrator.
All computers run the Microsoft Edge browser.
You need to prevent web cookies from being saved.
What should you enforce?
- SmartScreen Filter
- InPrivate Browsing
- Antivirus protection
- Cross-Site Scripting Filter
-
Encrypting a hard disk is an example of ensuring:
- security be default
- confidentially
- integrity
- least privilege
-
You have a new computer and want to restrict other people from replacing the operating system.
Which action prevents a user from installing an alternate operating system by using physical media if the user has physical media if the user has physical access to the computer?
- installing drive-level encryption
- disabling removable devices and drives
- password protecting the computer BIOS
- removing the user from the administrators group
-
You have an application that communicates by using plain text. You want to secure communications between the application and a server at the network layer.
What should you implement?
- TLS
- SFTP
- SSH
- IPsec
Explanation:
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over an Internet Protocol network. It operates at the network (layer 3 in the OSI model)Incorrect Answers:
A, C: TLS and SSH are cryptographic protocols designed to provide communications security over a network. They operate at the application layer, or layer 7 of the OSI model.
B: SFTP provides file access, file transfer, and file management over a reliable data stream. It operates at the application layer, or layer 7 of the OSI model.