98-367 : Security Fundamentals : Part 09
98-367 : Security Fundamentals : Part 09
-
HOTSPOT
You are configuring the network settings of computers in your school’s computer lab.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
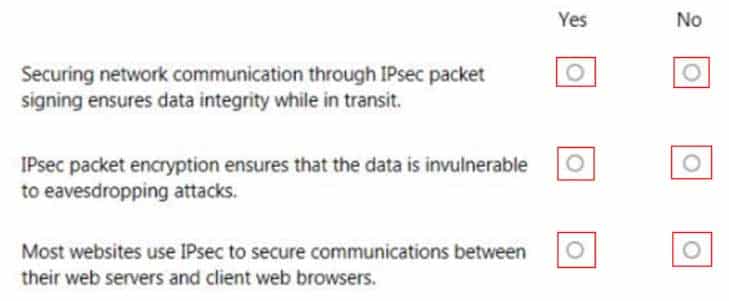
98-367 Part 09 Q01 041 Question 
98-367 Part 09 Q01 041 Answer Explanation:
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over an Internet Protocol network. -
The process of creating a barrier between domain members and non-domain members by using IPsec policies is referred to as:
- server filtering
- domain filtering
- domain isolation
- server isolation
-
Which networking protocol provides centralized authentication, authorization, and accounting?
- HTTPS
- OpenID
- SMTP
- RADIUS
Explanation:
OpenID is an open standard and decentralized authentication protocol. -
This question requires that you evaluate the underlined text to determine if it is correct.
Malware is any kind of unwanted software that is installed without your consent.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice that makes the statement correct.
- Trojans are
- Worms are
- Viruses are
- No change is needed
-
A Virtual Private Network (VPN) is a/an:
- Intrusion Prevention System that filters unauthorized communications in the enterprise network
- virtual communication method that stores data transmitted in a private environment
- tunnel that prevents information that passes through it from being modified or stolen
- perimeter network that contains secure virtual servers
-
Your anti-spam program is blocking emails from a particular sender. Your company needs to receive emails from this sender.
What should you do?
- Accept RSS feeds from their domain
- List the sender’s email address in DNS
- Add the email addresses to the whitelist
- Reconfigure the SMS Gateway
-
DRAG DROP
Match the authentication protocol with its description.
Instructions: To answer, drag the appropriate authentication protocol from the column on the left to its description on the right. Each authentication protocol may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
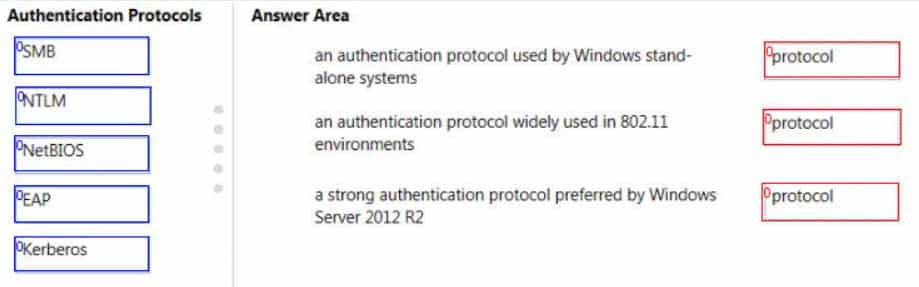
98-367 Part 09 Q07 042 Question 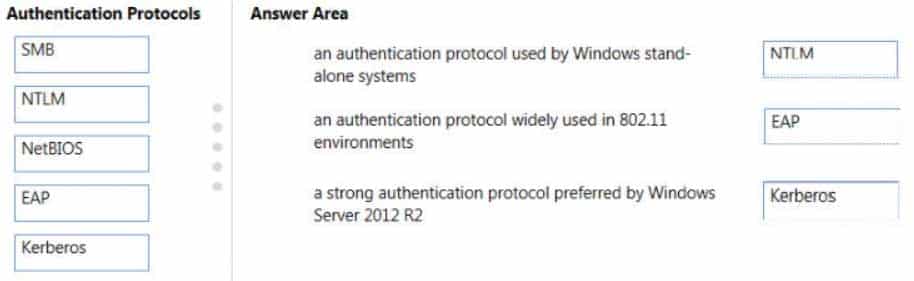
98-367 Part 09 Q07 042 Answer -
You need to give a standard user permission to run a program as an administrator.
How should you set up the program shortcut to accomplish this?
- in a different Compatibility Mode
- by utilizing RunAs
- in a separate memory space
- by using a smart card